Make PCI Compliance "Business as Usual"

Note: Nessus Cloud is now a part of Tenable.io Vulnerability Management. To learn more about this application and its latest capabilities, visit the Tenable.io Vulnerability Management web page.
If your organization transmits, processes, stores, or could impact the security of cardholder data, the Payment Card Industry Data Security Standard (PCI DSS) is the mandated framework of security controls and processes you must follow, and annual attestation is required. However, PCI compliance should not just be about passing an annual assessment. Adopting and maintaining a "business-as-usual," continuous PCI compliance monitoring approach is required to establish a foundation of true security that keeps criminal hackers away and cardholder data safe.
PCI DSS is established, yet still challenging
The PCI DSS is a mature standard with more than a decade of deployment and evolutionary updates. However, despite this maturity, consistently meeting the hundreds of security requirements specified in the PCI DSS standard continues to be a challenge for many organizations.
Version 3.2 of the Payment Card Industry Data Security Standard (PCI DSS), which the PCI Security Standards Council released on April 28, 2016, has six major goals defined by 12 requirements and more than 400+ sub-requirements. These specify a vast range of people, process, and technology controls that affect the security of cardholder data. To complicate things even further, sometimes the organization itself is responsible for performing an assessment and determining whether or not they believe they are meeting a requirement, while other times an external assessor is assessing the organization using his or her own interpretation of PCI requirements and the degree to which they are met. This makes it hard to know exactly what your organization's PCI compliance stance is at any given point in time.
According to the PCI Security Standards Council, for true protection of payment card information, you must not only meet, but also consistently maintain these security requirements as part of your business-as-usual activities.
PCI compliance isn’t a once-a-year project
The PCI DSS Version 3.0, released in November 2013, debuted the concept of making compliance business-as-usual in order to shift the mindset from a once-a-year project to a continuous effort. In Version 3.2 of the standard, there is a continued emphasis on the necessity of doing what the PCI DSS requires on an ongoing and continuous basis.
80% of companies that passed their annual assessment failed a subsequent interim assessment
According to the Verizon 2015 PCI Compliance Report (March 2015), “80% of companies that passed their annual assessment failed a subsequent interim assessment, which indicates that they’ve failed to sustain the security controls they put in place,” illustrating how easy it is to drift out of compliance. In order to truly protect cardholder data, you must start building a business-as-usual, continuous, sustainable PCI security program. Tenable can help.
Tenable enables business-as-usual PCI compliance
Tenable provides a continuous PCI DSS compliance monitoring solution you can use to create the strong, continuous security you need to effectively protect your cardholder data environment (CDE) and achieve business-as-usual PCI compliance.
Tenable supports PCI vulnerability scanning, but doesn’t stop there
Tenable is known as the creator of Nessus®, which is widely used to perform network vulnerability scans based on Requirement 11.2 of the PCI DSS. Requirement 11.2 focuses on vulnerability scanning, and includes three sub-requirements:
- Internal scanning (11.2.1)
- External scanning (11.2.2)
- Internal and external scanning after any significant change to the network (11.2.3), such as new system component installations, changes in network topology, firewall rule modifications, product upgrades, etc.
Service Providers and Merchants can use Tenable solutions to meet all PCI DSS 11.2 vulnerability scanning requirements:
- Internal scanning requirements: Use either Nessus, the world’s most widely deployed vulnerability scanner, Nessus Cloud, or SecurityCenter Continuous View™ (SecurityCenter CV™), which uses Nessus as its underlying scanner, to meet all PCI DSS 11.2.1 internal vulnerability scanning requirements, including requirements for internal scanning after significant change (11.2.3).
- External scanning requirements: Use Nessus Cloud, the Tenable Approved Scanning Vendor (ASV) service, to meet all PCI DSS 11.2.2 external scanning requirements, including quarterly external scan requirements.
Tenable support for PCI compliance also goes much deeper than simply internal and external vulnerability scanning support.
Tenable provides proactive, continuous PCI compliance monitoring
Tenable SecurityCenter CV, using Nessus as its underlying scanner, provides not only the internal vulnerability scanning support Service Providers and Merchants need for their PCI compliance program; it also includes additional capabilities that enable proactive and continuous monitoring of PCI security. These key capabilities help Service Providers and Merchants easily achieve continuous PCI compliance business-as-usual for their organizations.
These capabilities include:
- Continuous monitoring of more than 75% of PCI DSS technical controls, giving you a comprehensive, near real-time view into the status of your PCI compliance posture
- Support for centralized logging and monitoring PCI DSS requirements (10.5-10.6)
- Support for PCI DSS change detection requirements (11.5) using data collected from hosts and via continuous listening
- A centralized view that helps you identify threats and avoid data leakage by monitoring all devices within your cardholder data environment (CDE), including physical, virtual, mobile, and cloud, as well as traffic going into and out of the CDE
- A unique combination of active scanning, agent scanning, intelligent connectors, continuous listening and host data monitoring to help you quickly identify when you are drifting out of compliance so you can take immediate action
- Streamlined assessment, providing automated baseline creation, anomaly detection, continuous monitoring, and purpose-built PCI DSS Assurance Report Cards (ARCs), dashboards, and reports that make it easy for you to track and efficiently manage your entire PCI DSS security program from a central location
Security data collected by Tenable sensors is automatically fed into SecurityCenter CV, then displayed in the PCI dashboards and ARCs.
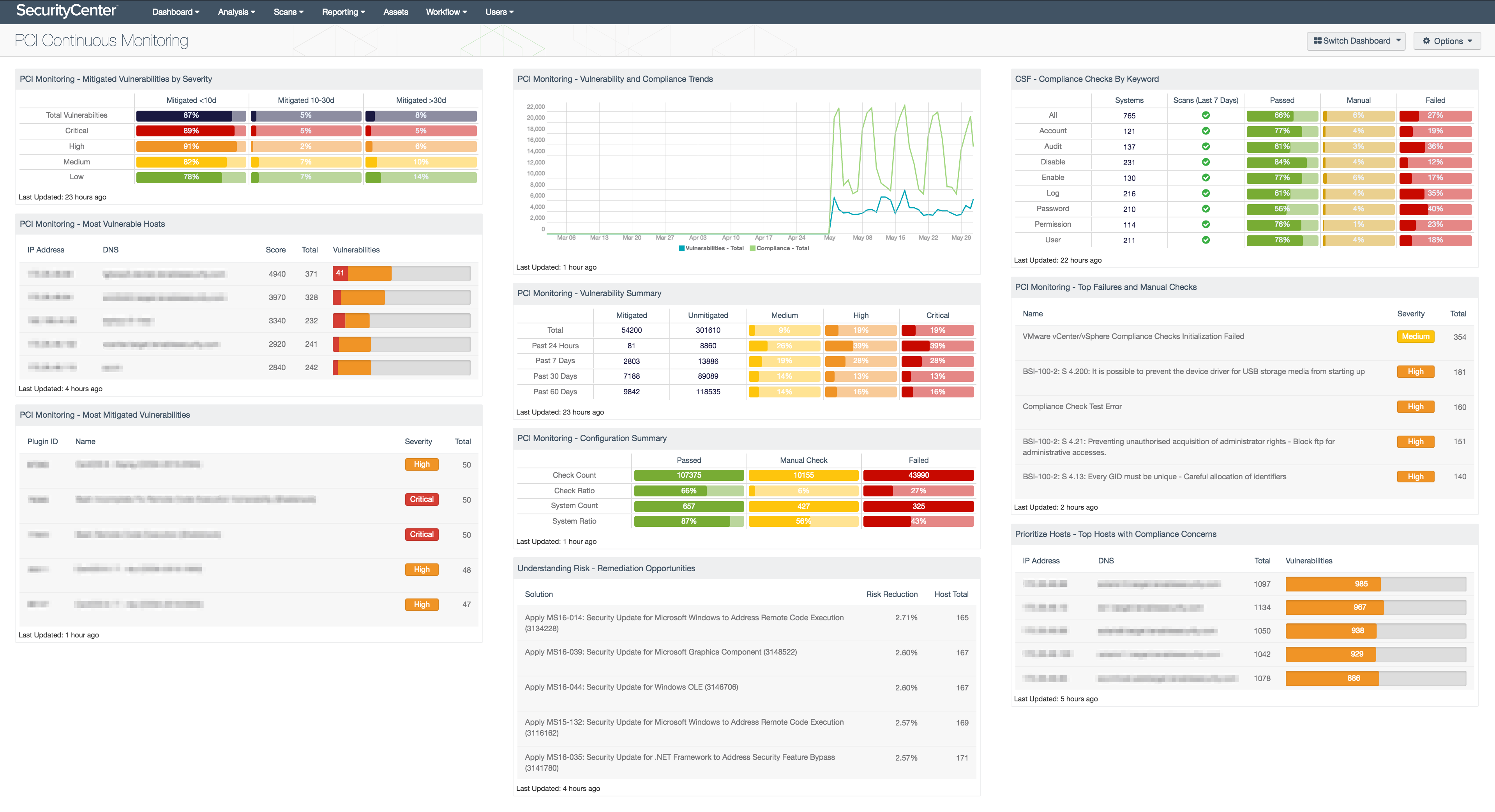
PCI dashboards for continuous compliance monitoring
Tenable PCI dashboards are centralized control panels used by security operations staff to monitor and react to security data in real-time.
Dashboards enable continuous monitoring of critical PCI DSS controls
SecurityCenter CV includes 12 PCI-specific dashboards, along with one compliance summary, which includes both PCI as well as other standards and regulations which may also fall under your area of responsibility:
- PCI Access Control: Allows organizations to assess their level of adherence with PCI security requirements, focusing on access control
- PCI Asset Management: Provides security teams with detailed insight into their network and PCI security posture
- PCI Centralized Logging: Provides analysts with detailed insight into the log collection and events gathered across the organization
- PCI Configuration Audit: Presents extensive data about the configuration status of the network based on accepted industry configuration standards such as CIS
- PCI Continuous Monitoring: Presents extensive data about the vulnerability and configuration status of the network
- PCI Data Protection: Allows organizations to assess their level of adherence with PCI requirements, focusing on data protection
- PCI Monitoring Coverage: Allows organizations to assess their level of adherence with PCI requirements, focusing on monitoring coverage of vulnerability scanning
- PCI Network Mapping: Provides security teams with detailed insight into their network and cardholder data environment security posture
- PCI Network Security: Provides security teams with detailed insight into their organization and PCI compliance posture of the network
- PCI Quarterly Internal Vulnerability Scanning: Presents extensive data about the vulnerability status of the network
- PCI Scan Monitoring: Provides security teams with detailed insight into their organization and vulnerability management posture
- PCI Vulnerability Management Program: Enables organizations to assess their level of adherence with requirements found in the “Maintain a Vulnerability Management Program” section of the PCI DSS
- Compliance Summary: Provides several components for each of the compliance standards auditable by SecurityCenter CV (including PCI DSS)
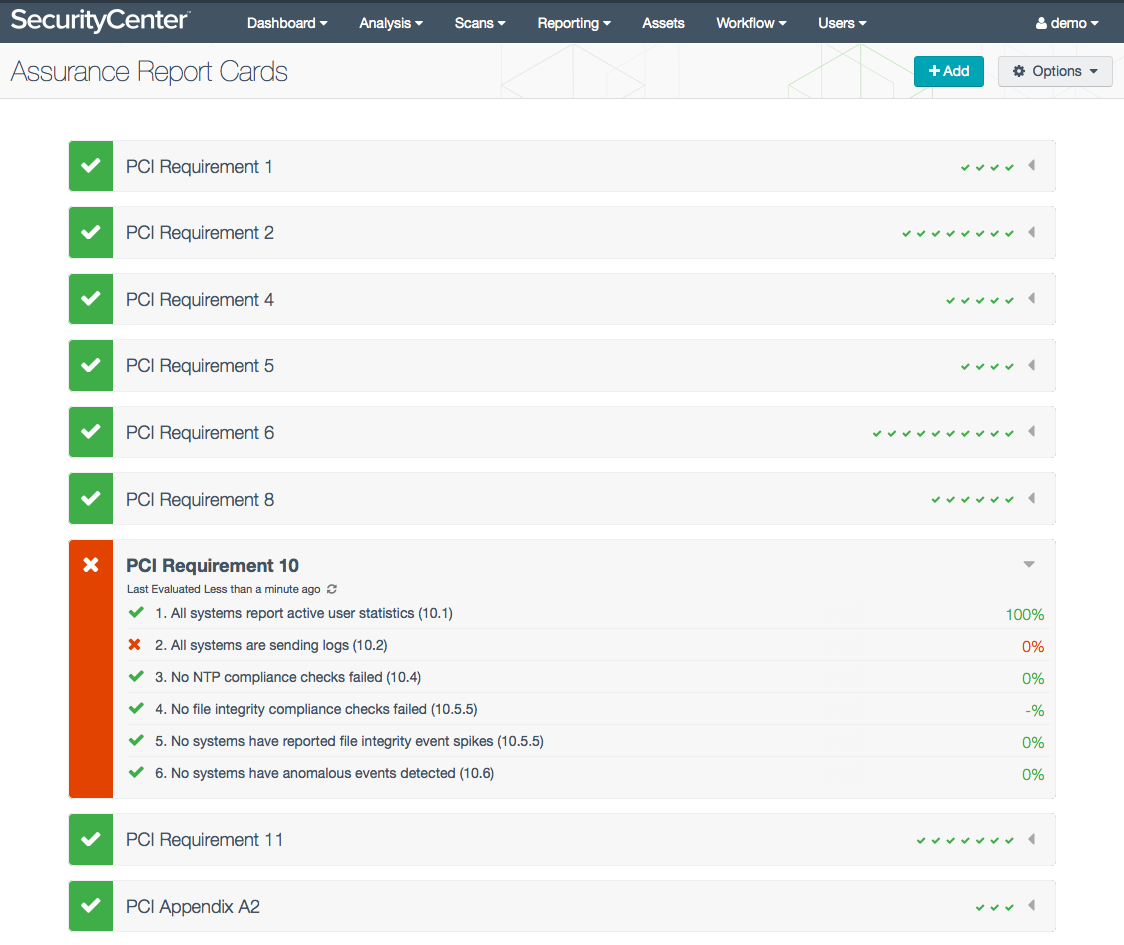
PCI Assurance Report Cards (ARCs) for continuous compliance monitoring
Tenable PCI ARCs provide security managers and executives with a business perspective, enabling you to show how your organization’s PCI DSS program is performing within the context of specific PCI requirements:
ARCs map to specific PCI requirements
Tenable provides nine PCI-specific ARCs in SecurityCenter CV:
- PCI Requirement 1: Analyzes policy statements related to the requirement: Secure the network border to protect cardholder data
- PCI Requirement 2: Analyzes policy statements related to the requirement: Harden systems to a consistent, documented, and secure standard based on recognized industry standards
- PCI Requirement 4: Analyzes policy statements related to the requirement: Encrypt cardholder data across open and public networks
- PCI Requirement 5: Analyzes policy statements related to the requirement: Defend the organization with anti-virus and anti-malware products
- PCI Requirement 6: Analyzes policy statements related to the requirement: Keep the organization safe with vulnerability management and use industry standard secure development practices
- PCI Requirement 8: Analyzes policy statements related to the requirement: Access to system components is identified and authenticated
- PCI Requirement 10: Analyzes policy statements related to the requirement: Network resources and all access to cardholder data is tracked and monitored
- PCI Requirement 11: Analyzes policy statements related to the requirement: Security systems and processes should be tested regularly
- PCI Appendix A2: Analyzes policy statements related to Appendix A2 requirement: Organizations using SSL and early versions of TLS must work toward upgrading to a strong cryptographic protocol
True PCI security requires a continuous business-as-usual approach to compliance
Achieving continuous business-as-usual PCI compliance is not easy, especially for large enterprise organizations with complex tool sets and security data sources. However, continuously maintaining the security of the cardholder data environment is critical, especially in this era of high profile payment card data breaches. Organizations responsible for securing cardholder data must shift from the mindset of passing a point-in-time audit to year-round continuous compliance and effective security, and Tenable can help.
For more information about the Tenable Continuous PCI DSS compliance monitoring solution, see the following resources:
- Solution Story: Make PCI Compliance Business as Usual
- Whitepaper: How to Enable Continuous PCI DSS Compliance Monitoring
- Infographic: PCI DSS Continuous Compliance Monitoring
- PCI
- Vulnerability Management