Exposure management for federal government agencies
Minimize risk across IT, OT, and cloud and keep mission-critical workloads safe with exposure management for federal agencies.

Tenable Cloud Security now available through GSA OneGov
GSA and Tenable OneGov agreement provides Tenable Cloud Security FedRAMP at substantial cost savings for federal agencies.
Secure your agency’s mission with FedRAMP authorized exposure management from Tenable
Tenable One, Tenable Cloud Security, and Tenable Vulnerability Management are FedRAMP and GovRAMP authorized.

Support federal missions with Tenable
Build a preemptive cyber defense across your attack surface, covering legacy IT, cloud, OT, and identities. Reduce risk, streamline compliance, support zero trust initiatives, and defend mission-critical systems.
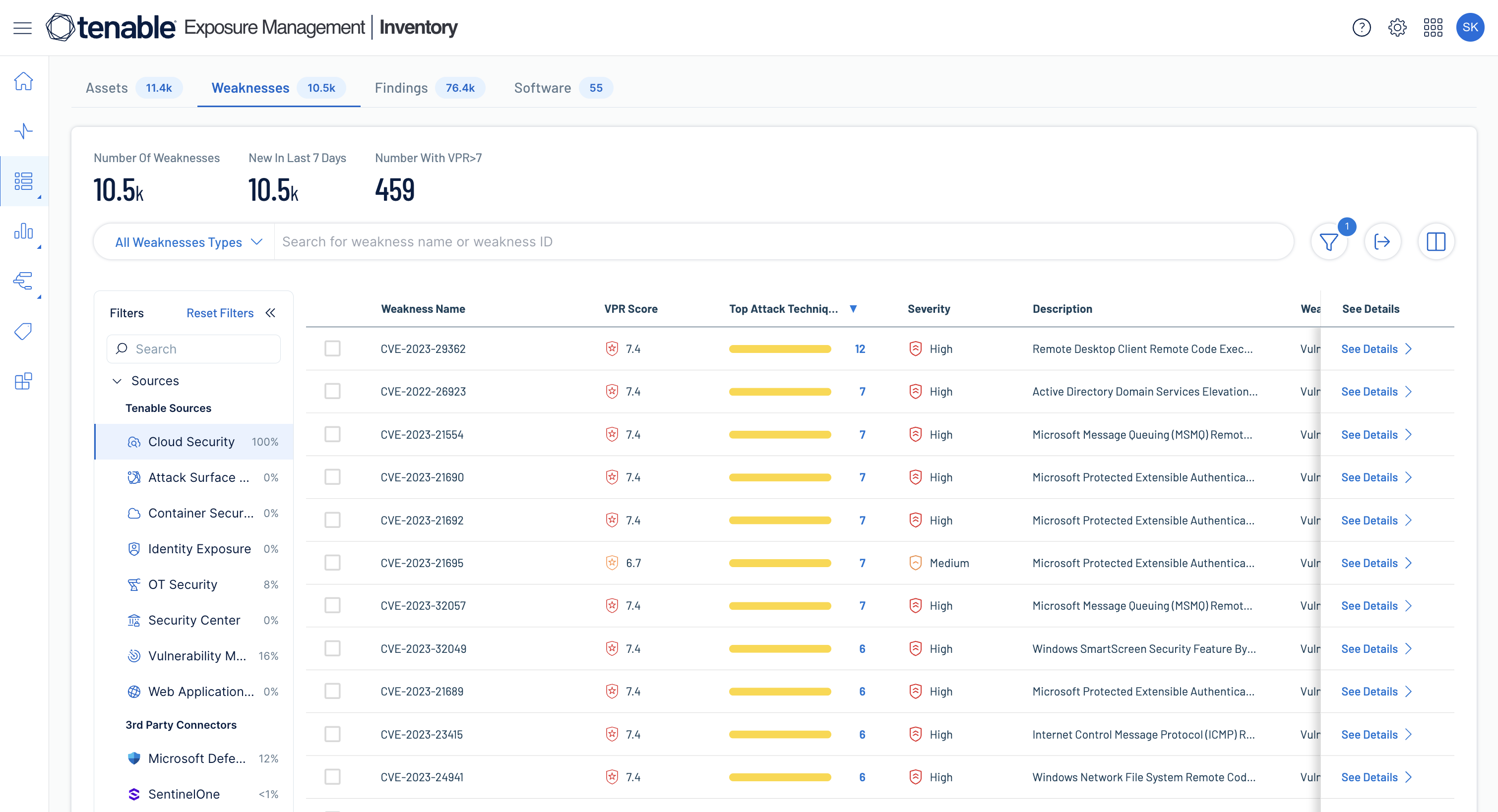
Gain a unified asset inventory and continuous assessment capabilities
Discover, inventory, and continuously assess every asset across IT, OT, multi-cloud, and identity systems — supporting EO 14028, Zero Trust architecture, and CDM requirements — so you can eliminate blind spots and close exposures before threat actors can exploit them.
Read the eBookPrioritize exposures that matter
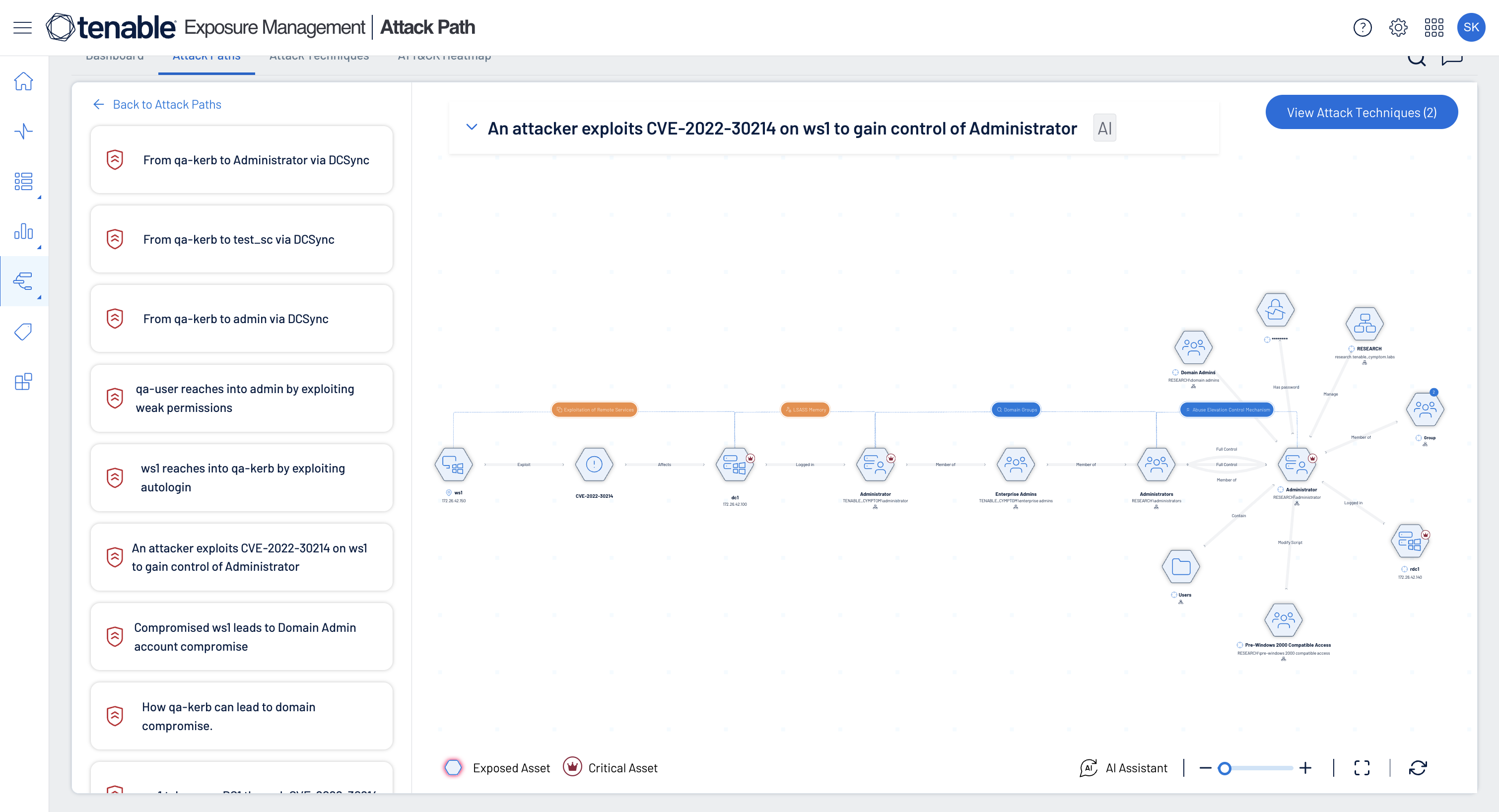
Standardize risk scoring across domains to pinpoint critical attack paths and toxic risk combinations, ensuring remediation efforts align with agency needs.
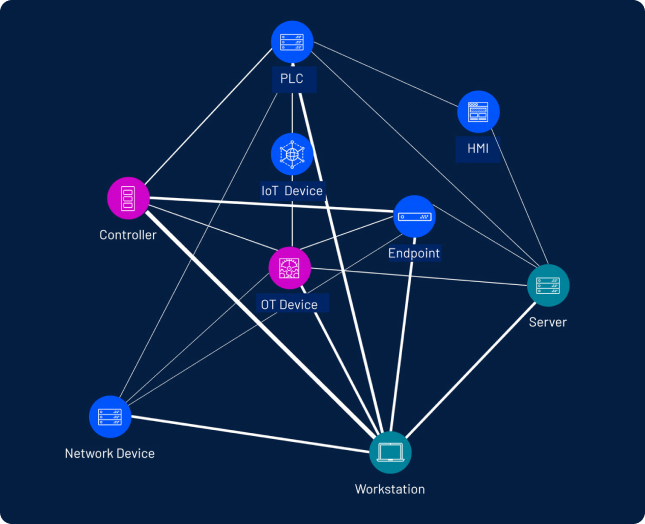
Safeguard critical infrastructure with unified IT/OT security
Secure legacy systems, remove operational silos, and detect exposures across OT and IT without disrupting operations.
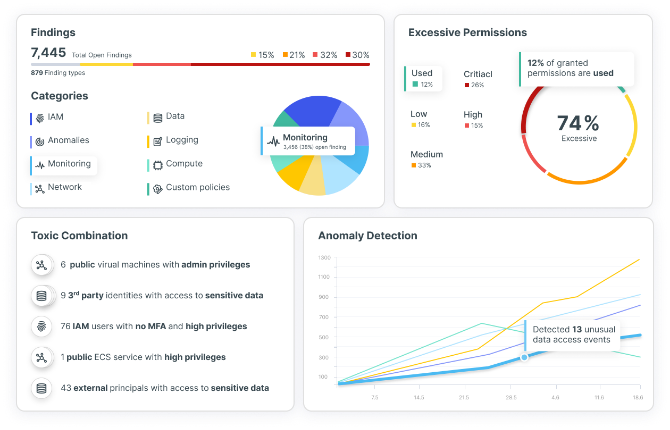
Secure federal cloud environments
Protect federal cloud environments with unified exposure management. Gain visibility across workloads, detect risks, prioritize vulnerabilities, maintain compliance, and modernize IT and DevOps pipelines safely.
Streamline federal compliance
Simplify compliance across IT, OT, and cloud with unified exposure management. Continuously monitor systems, map risks to NIST 800-53, RMF, DISA STIGs, CIS benchmarks, FISMA, zero trust mandates, and other standards. Generate audit-ready reports and reduce the effort to maintain regulatory adherence.
Department of Defense
selected platform
Tenable was selected by DISA to power the Assured Compliance Assessment Solution (ACAS) program, protecting all DoD networks with vulnerability assessment and management, contextual insight, risk assessment and configuration and compliance auditing.
View the solution overview
How exposure management helps federal agencies address strategic priorities and cybersecurity challenges
| Strategic priority | How exposure management helps |
|---|---|
| Strengthen zero trust architecture | Exposure management delivers unified visibility across every asset, identity, and environment so agencies can validate trust continuously, enforce least-privilege access, and reduce attack paths with actionable, risk-driven insights. |
| Modernize legacy infrastructure and reduce technical debt | Exposure management continuously identifies outdated and high-risk systems, maps exposures to mission impact, and prioritizes what to fix first — helping agencies modernize with clarity and confidence. |
| Secure hybrid and multi-cloud environments | Exposure management provides complete discovery of cloud assets, configurations, workloads, and identities — helping agencies eliminate misconfigurations, strengthen cloud posture, and secure cloud modernization at scale. |
| Strengthen identity security and reduce privilege abuse | Exposure management reveals excessive entitlements, misconfigurations, and identity-based attack paths across cloud and on-prem environments so agencies can prevent lateral movement and harden access controls. |
| Protect operational technology (OT) and critical infrastructure | Exposure management gives agencies unified visibility into IT, OT, and ICS assets, identifies vulnerabilities and insecure configurations, and prioritizes remediation to reduce operational risk without disrupting mission systems. |
| Improve incident response and reduce dwell time | Exposure management pinpoints exploited assets, exposure chains, and high-risk weaknesses to accelerate investigation, containment, and response — reducing the impact on mission operations. |
| Achieve continuous compliance and reduce audit burden | Exposure management automates evidence collection and continuous monitoring, highlights control gaps, and streamlines reporting so agencies can maintain ATO readiness and meet federal mandates with less effort. |
| Support workforce efficiency and security tool consolidation | Exposure management consolidates siloed visibility, reduces manual analysis through automation, and helps teams focus on the exposures that matter most — improving efficiency without adding tool overload. |
Tenable Enclave Security
Purpose-build for the most secure federal environments
Built for classified, air-gapped, and FedRAMP High/IL5 environments, Tenable Enclave Security delivers scalable vulnerability management and container image scanning — purpose-built for isolated, mission-critical systems.
Federal agency trusted partner
Tenable has a deep understanding of federal government needs and a history of transforming networks and reducing risk to federal agencies.
Secure cloud, lower costs
Federal agencies can get Tenable Cloud Security via GSA OneGov, reducing spend and simplifying procurement. Learn more.
Strengthen zero trust and resilience
Map assets, prevent lateral movement, enforce least privilege, and reduce downtime from cyber attacks. Learn more.
Accelerate ATO and compliance
Streamline Authorization to Operate and meet requirements for NIST, FISMA, RMF, CIS, and more with audit-ready reporting.
FedRAMP authorized and cost effective
Use a single, government approved platform to consolidate tools, reduce costs, simplify reporting, and secure the entire attack surface.
Exposure management for federal government FAQ
-
What are the key benefits of Tenable for federal agencies?
-
As a longtime partner to federal agencies, Tenable can help your agency strengthen cybersecurity, reduce risk, and maintain compliance across IT, OT, and cloud environments. Key benefits include:
- Unified visibility: Get a complete, real-time inventory of assets, exposures, and risks across IT, OT, multi-cloud, web applications, and identity systems from one unified location.
- ATO acceleration: Streamline ATO processes with automated evidence mapped to NIST 800-53, DISA STIGs, CIS benchmarks, RMF, FISMA, CISA KEV, zero trust mandates, and more.
- FedRAMP authorization: Use cloud-native, government approved tools for secure deployments across federal environments.
- Support for Zero Trust: Map assets, detect lateral movement, enforce least privilege access, and coordinate incident response across domains.
- Exposure-based prioritization: Focus resources on the vulnerabilities that have the greatest impact to mission critical operations.
- Audit ready reporting: Generate standardized, agency-ready reports that clearly demonstrate compliance and risk reduction.
- Operational resilience: Reduce downtime and strengthen mission continuity by proactively managing cyber risk and exposure.
- Cost efficiency: Consolidate multiple security tools into a single platform for streamlined visibility, prioritization, reporting, and compliance efforts.
-
Why do agencies need exposure management now?
-
Federal networks are increasingly complex, with expanding attack surfaces across IT, OT, cloud, AI, and identities. Exposure management provides unified visibility, mission-focused prioritization, proactive risk reduction, OT/IT convergence, audit-ready reporting, and improved operational resilience to protect critical assets.
-
How does exposure management support regulatory compliance in federal agencies?
-
By continuously monitoring assets, identifying vulnerabilities, and providing actionable remediation guidance, exposure management helps agencies meet FISMA, NIST, and other regulatory requirements efficiently.
-
What business and cybersecurity outcomes can agencies expect from implementing exposure management?
-
Agencies can expect faster detection and remediation of exposures, improved operational resilience, reduced risk of breaches, and simplified compliance reporting, leading to both a stronger security posture and cost efficiencies.
-
How is exposure management different from traditional vulnerability management?
-
When comparing exposure management vs vulnerability management, the key difference is scope and context. Where vulnerability management identifies IT assets and prioritizes software vulnerabilities using standard industry models such as CVSS, exposure management goes farther. It performs asset discovery and aggregates asset and risk data from across the attack surface and existing tools. It correlates vulnerabilities, misconfigurations, and identity weaknesses into attack paths to provide a unified, contextual view of assets and exposure and to reveal how those toxic combinations of preventable security risks could impact critical systems or regulatory obligations. This enables federal agencies to prioritize what truly matters to business resilience and compliance.
-
How does Tenable support zero trust initiatives?
-
Tenable helps your agency implement a comprehensive zero trust strategy by providing unified visibility, continuous monitoring, and risk-based prioritization across IT, OT, and cloud environments. Your agencies can:
- Map all assets to understand exposure and risk.
- Get a common view of vulnerabilities, misconfigurations, exposures, and identity risks.
- Prevent lateral movement and privilege escalation across domains before it impacts mission systems.
- Enforce least privilege access and continuously verify identities.
- Prioritize vulnerabilities based on their potential impact on mission critical operations.
- Enable coordinated incident response that spans IT, OT, and cloud, reducing downtime and operational impact.
- Strengthen resilience against cyberattacks system failures or supply-chain disruptions.
- Apply network segmentation, micro-segmentation, and data protection policies to limit attack paths.
This approach ensures your agency continuously verifies, monitors, and protects all critical assets and identities while minimizing operational disruption and improving mission resilience.
-
What Tenable products are FedRAMP authorized?
-
Tenable is committed to supporting your federal agency with secure compliance solutions that help you reduce cyber risk. To support this mission, Tenable has a portfolio of FedRAMP moderate authorized platforms which include:
- Tenable One FedRAMP: A unified exposure management platform covering IT, OT, cloud, identity, and more.
- Tenable Cloud Security FedRAMP: A cloud native application protection platform (CNAPP) that provides continuous, unified protection for cloud environments, including workloads, infrastructure, applications, and identities.
- Tenable Vulnerability Management FedRAMP: Cloud-based asset discovery, vulnerability management, and vulnerability prioritization.
- Tenable Web Application Scanning FedRAMP: Cloud-based web application scanning.
Tenable is also in the process of obtaining FedRAMP high authorization for Tenable Cloud Security through our strategic partner UberEther. For more information on our FedRAMP solutions for your federal agency, read the solutions overview: Tenable for federal agencies.
-
Does Tenable protect cloud workloads and DevOps pipelines?
-
Yes. Through Tenable One FedRAMP and Tenable Cloud Security FedRAMP, Tenable secures the full cloud lifecycle — from code to runtime — helping your agency build, deploy, and operate workloads safely. It detects vulnerabilities, misconfigurations, and identity risks in cloud environments, integrates with CI/CD pipelines, and provides continuous visibility and risk-based prioritization for mission-critical operations.
-
Does Tenable cover both IT and OT environments?
-
Yes. Through FedRAMP authorized Tenable One, your agency can get visibility across IT, OT, and IoT environments. By securing IT and OT assets from a single platform, your agency can reduce blind spots, streamline risk management, and strengthen its overall cybersecurity posture across its entire infrastructure.
-
Are there cost savings benefits to using Tenable in federal agencies?
-
Yes. Tenable helps your agency reduce costs by consolidating multiple security tools into a single, unified platform that streamlines vulnerability and exposure management across IT, OT, cloud, and identities. By prioritizing remediation based on actual risk, Tenable helps your agency focus its resources where they matter most, reduce operational downtime, and simplify compliance reporting — saving time and money while strengthening your agency’s cybersecurity posture.
-
Is Tenable the ACAS solution provider?
-
Yes, Tenable is the core technology provider for the Assured Compliance Assessment Solution (ACAS). The ACAS program is managed by the Defense Information System Agency (DISA) and provides all DoD agencies with vulnerability management and compliance assessment. The technology powering ACAS is Tenable SecurityCenter. For more information please review the ACAS datasheet.
Related products
Related resources
See Tenable in action
Want to see how Tenable can help your team expose and close the priority cyber weaknesses that put your business at risk?
Complete this form for more information.
- Tenable Enclave Security
- Tenable Vulnerability Management
- Tenable Web App Scanning