Mature your cyber hygiene with strong security policies
Poor security hygiene — such as open ports, lack of multifactor authentication (MFA) and unencrypted data — remains a top cause of breaches. Even with strong security policies in place, unauthorized or out-of-band changes can push assets out of compliance and increase risk.
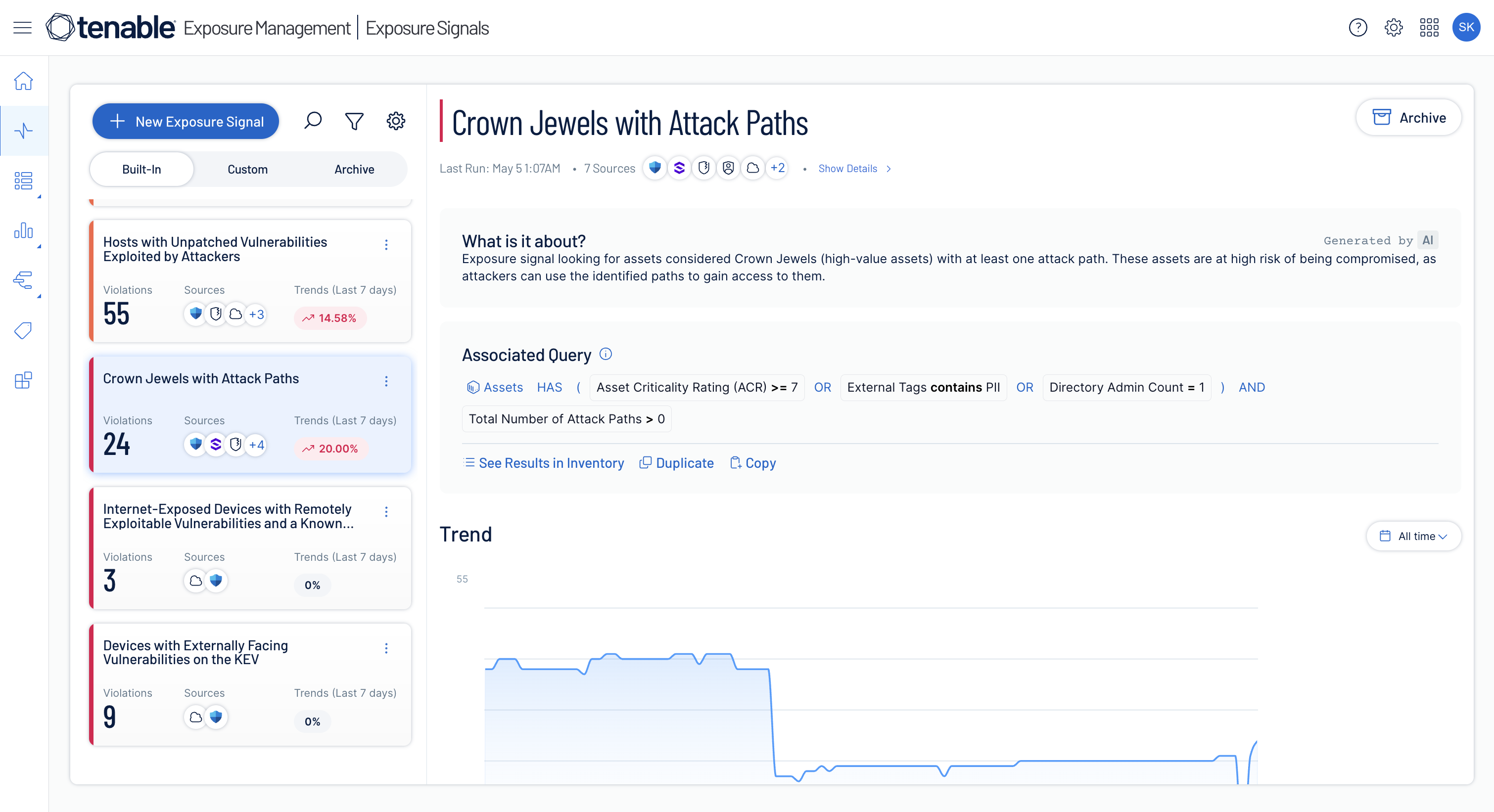
Maintain cyber hygiene with enforceable exposure policy
Identify toxic risk combinations to eliminate breach potential.
Strengthen cyber hygiene with proactive exposure management
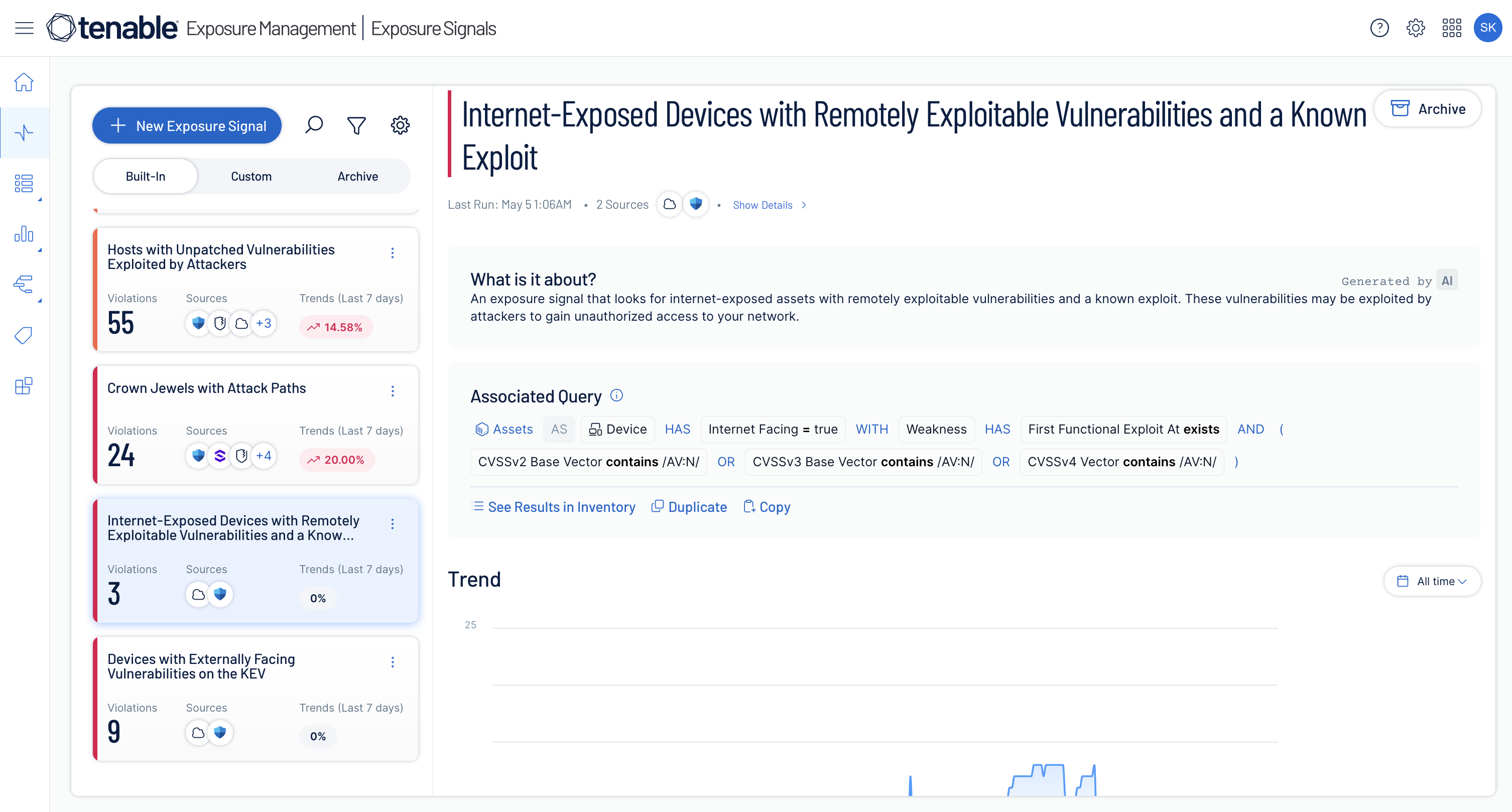
Define exposure policy your way
Leverage exposure context from Tenable and integrated third-party tools to apply prebuilt policies or create custom ones tailored to your organization's unique needs.
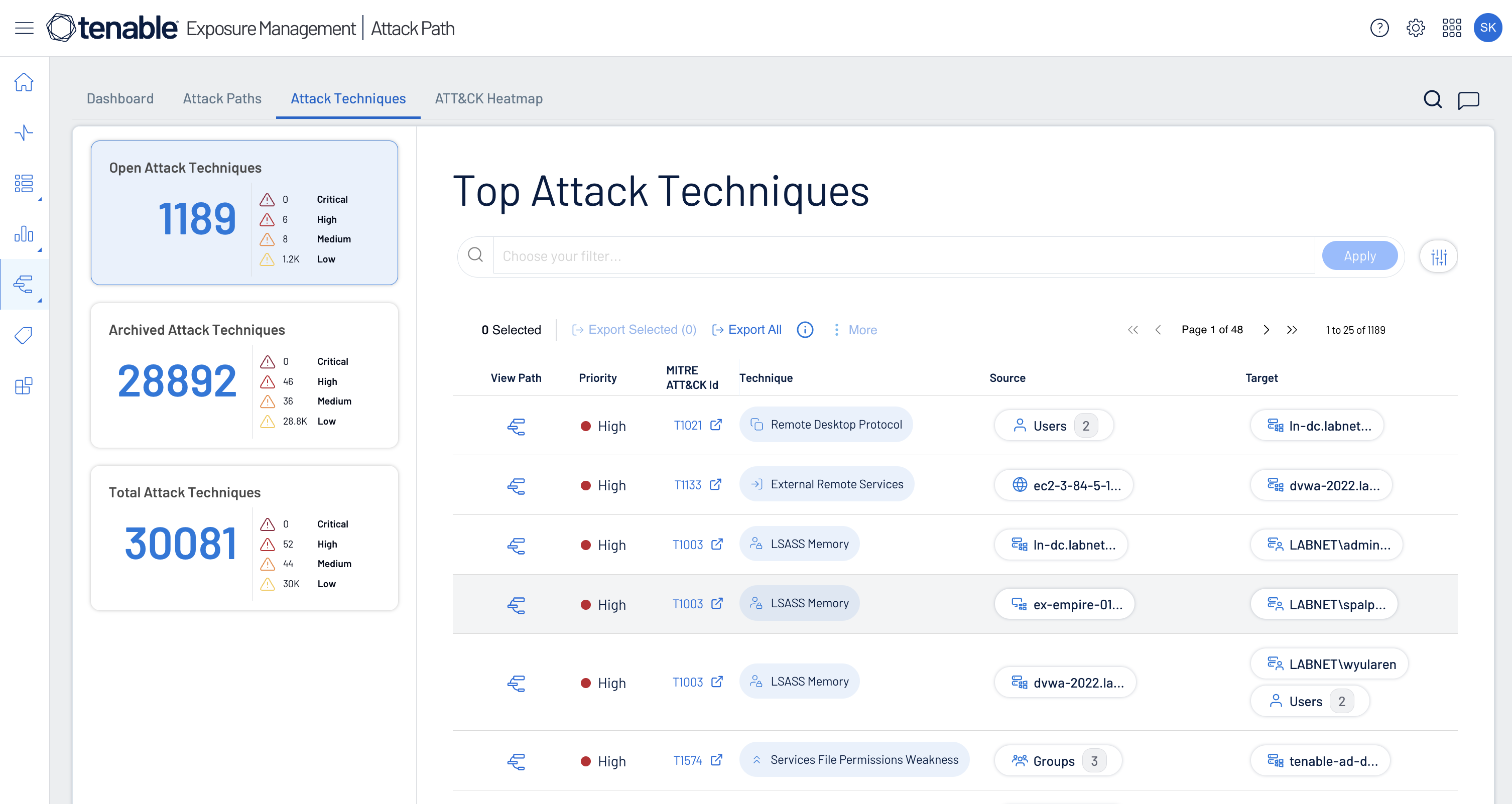
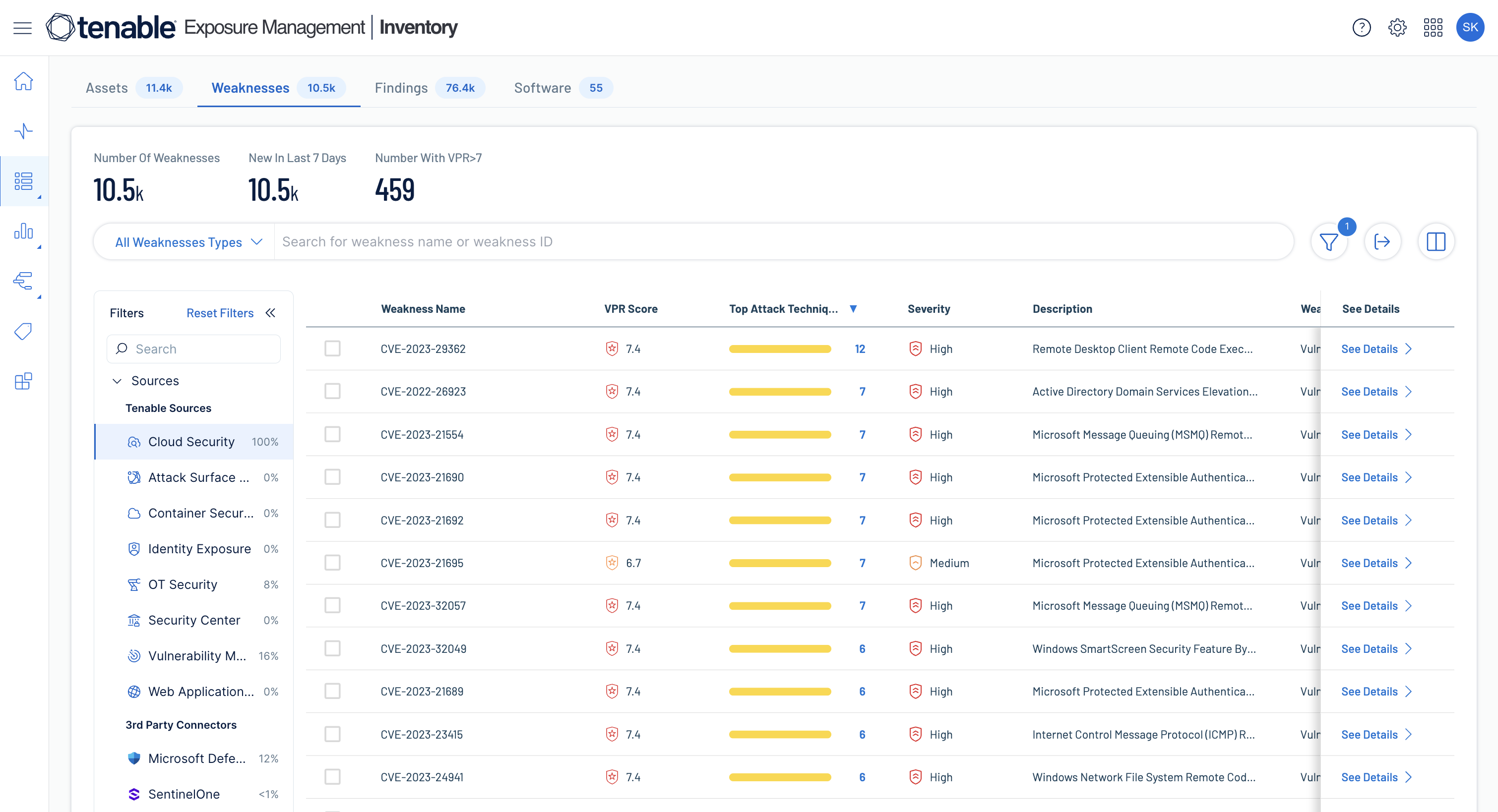
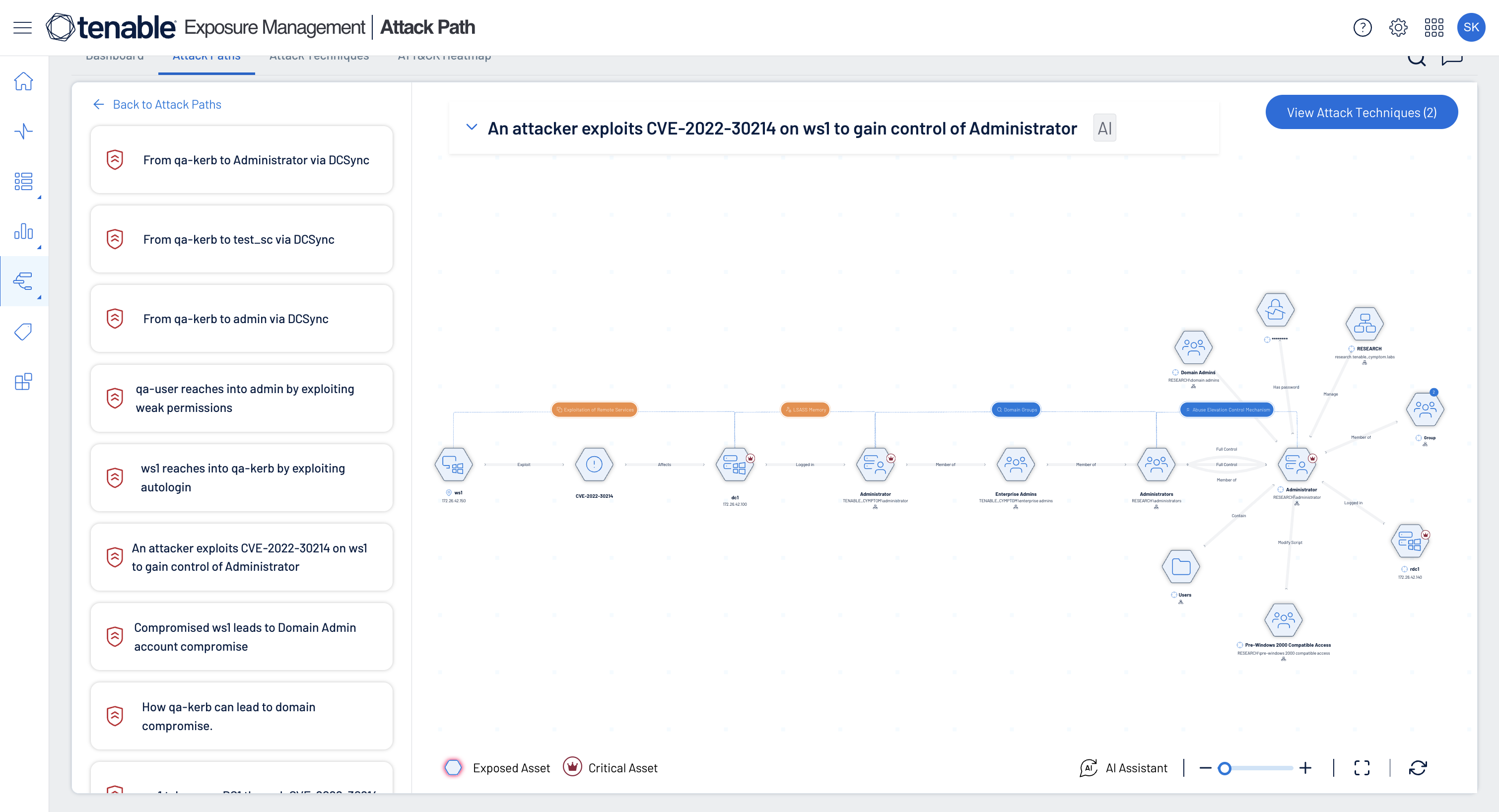
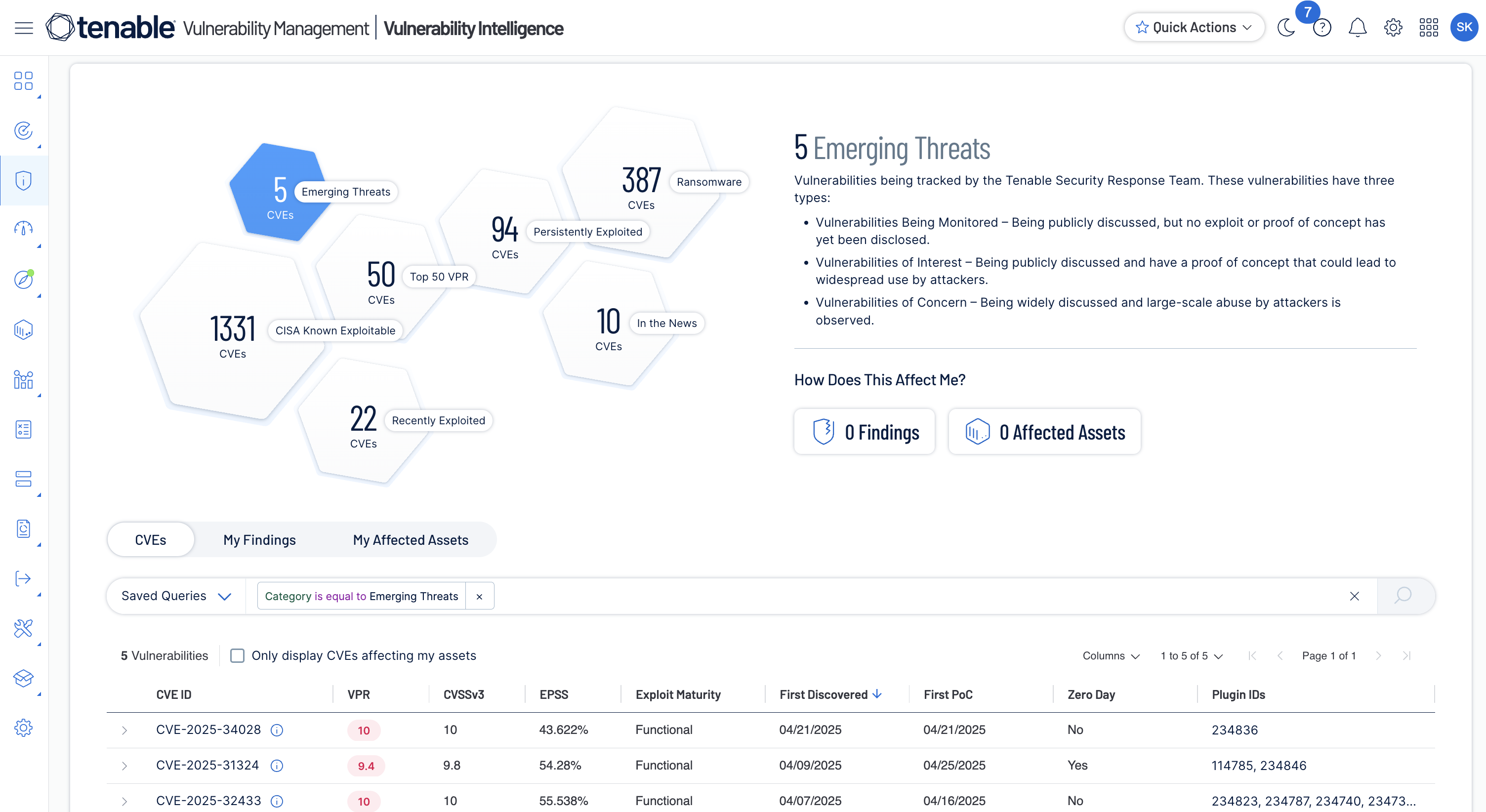
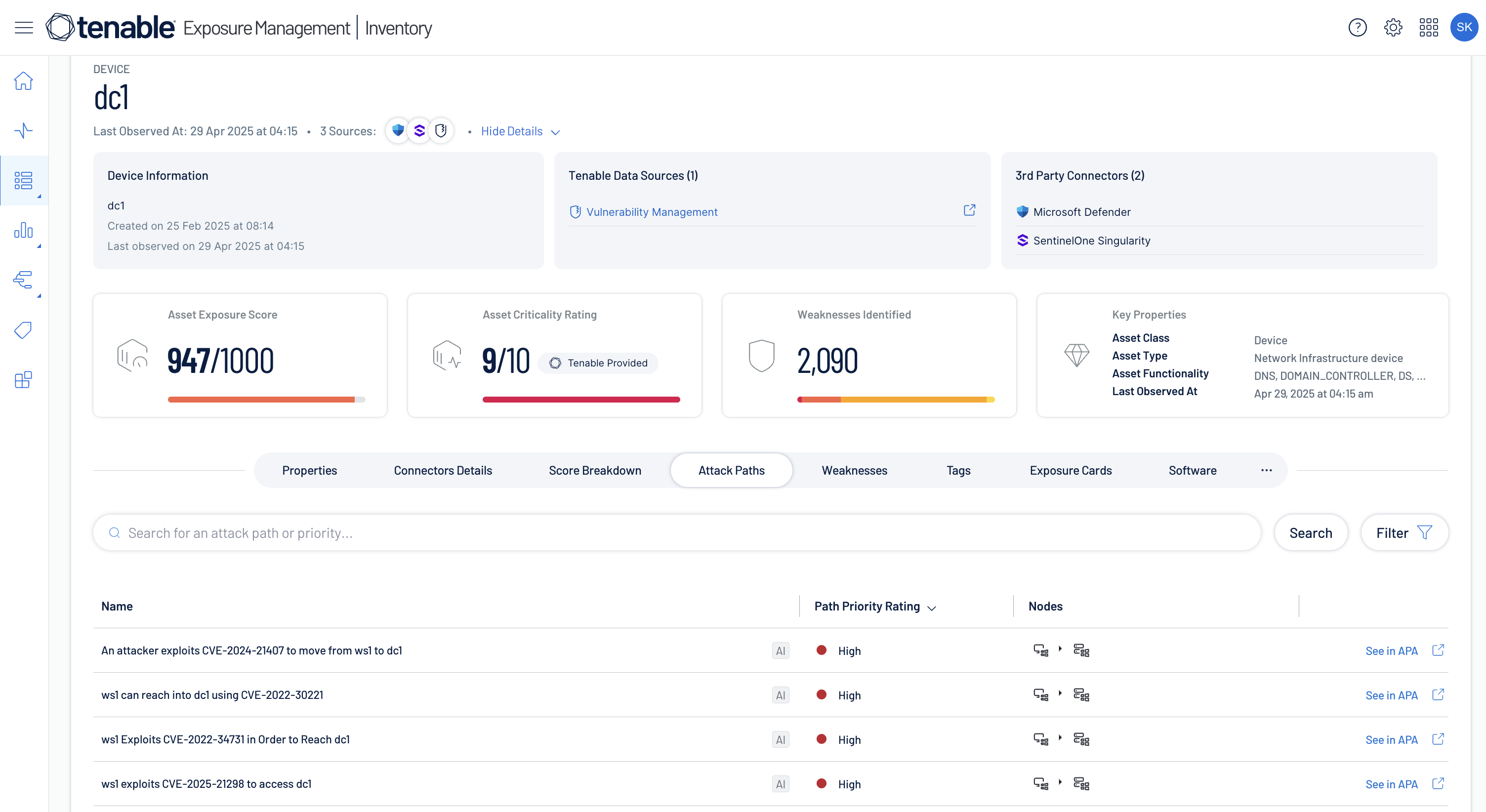
Uncover toxic risk combinations
Uncover and analyze hidden attack paths, define and track which risk combinations are important to you and view upcoming software end-of-life dates.
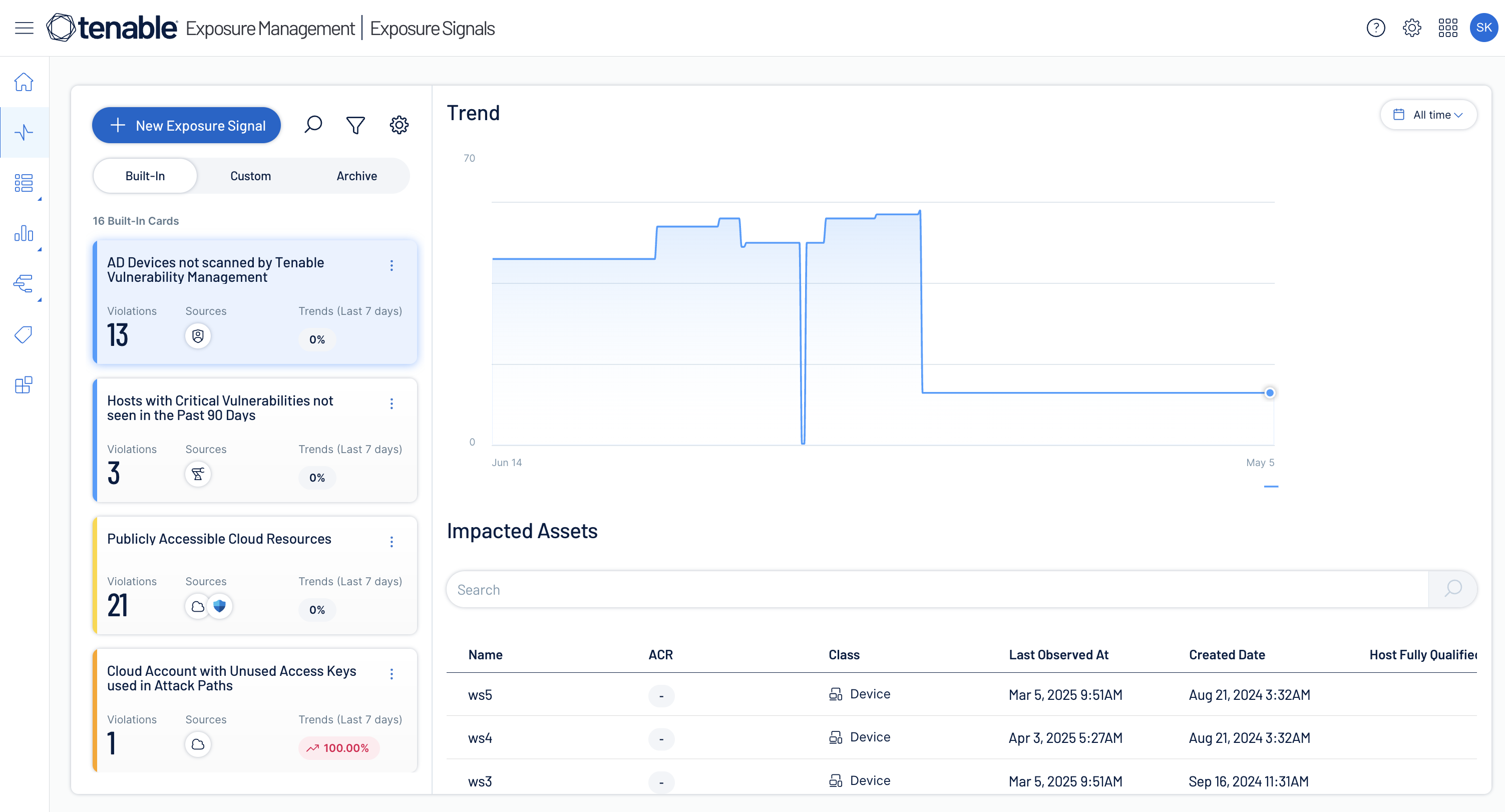
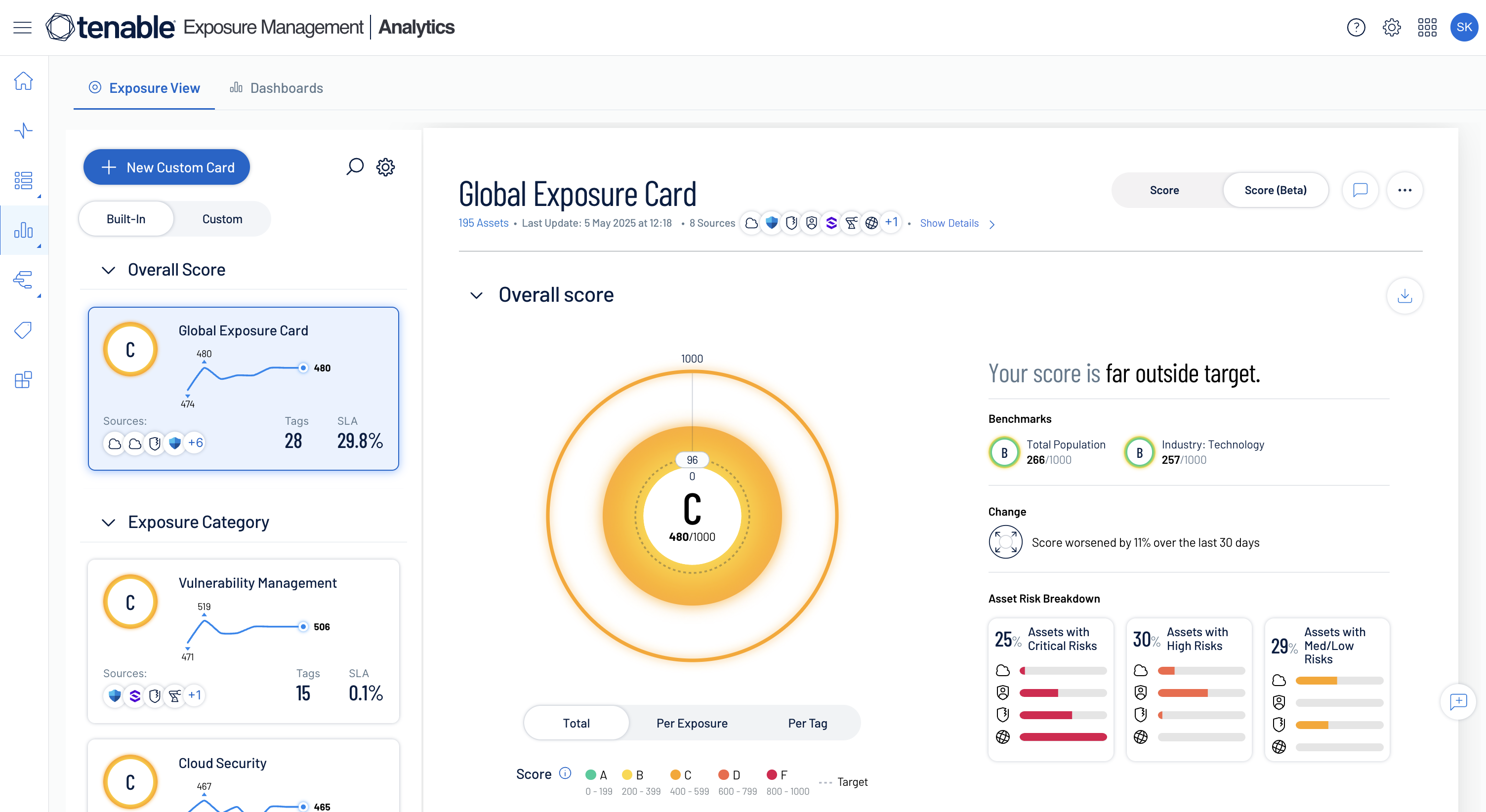
Track trendlines and affected assets
Track how your pre-defined risk combinations create exposure to the organization and evolve over time. Then, drill into high-priority assets with full context about their business criticality, attack paths and controls.
Report on compliance and violations
Automated scanning and continuous monitoring to ensure compliance tracking with industry frameworks to maintain baseline security hygiene.
Explore how Tenable One can help you
-
Simplify risk insights
Use business-aligned exposure insights for proactive risk mitigation and strategic alignment with your organization’s priorities.
Learn more about exposure analytics -
Know your attack surface
Get complete, contextualized asset visibility across your entire attack surface to unify risk assessments for faster remediation.
Learn more about asset inventory -
Prioritize exposures that matter
Normalize risk scoring across domains to pinpoint critical attack paths and toxic risk combinations, ensuring prioritized remediation aligned with business needs.
Learn more about exposure prioritization -
Streamline risk management
Use a dynamic policy engine to map and track risks, enabling tailored hygiene policies and rapid violation prioritization.
-
Respond to emerging threats
Track exposures in real time with historical threat context to streamline vulnerability prioritization and remediation efforts.
Learn more about emergency response -
Accelerate threat analysis
Unify asset visibility and contextual risk intelligence to accelerate investigations while reducing response time, tuned for all roles.
Learn more about threat investigation
Realize better outcomes with Tenable One
Tenable One customers see measurable improvements in security posture and business outcomes.
with technology
Related resources
Get Started with Tenable One
Tenable One has helped our engineers reduce the time spent on manual tasks by 75%, which allows them to focus on actual engineering work.
- Tenable One