Adopt zero trust security solutions across federal environments
Support your federal agency’s zero trust implementation across IT, OT and cloud with the Tenable One Exposure Management Platform. Curb unauthorized access, prevent lateral movement and privilege escalation, and secure mission-critical operations.

How exposure management supports zero trust
Accelerate your zero trust journey with Tenable
Achieve zero trust across IT, OT, and cloud with Tenable’s FedRAMP authorized exposure management solution. Unified visibility, smarter prioritization, and attack path visualizations help you enforce access controls and stop lateral movement.
Verify every identity
Continuously validate users and privileges to reduce risk. Detect over-privileged accounts, monitor behavior, and enforce least privilege and just-in-time access across IT, cloud, and OT environments.
View the webinarSecure every device
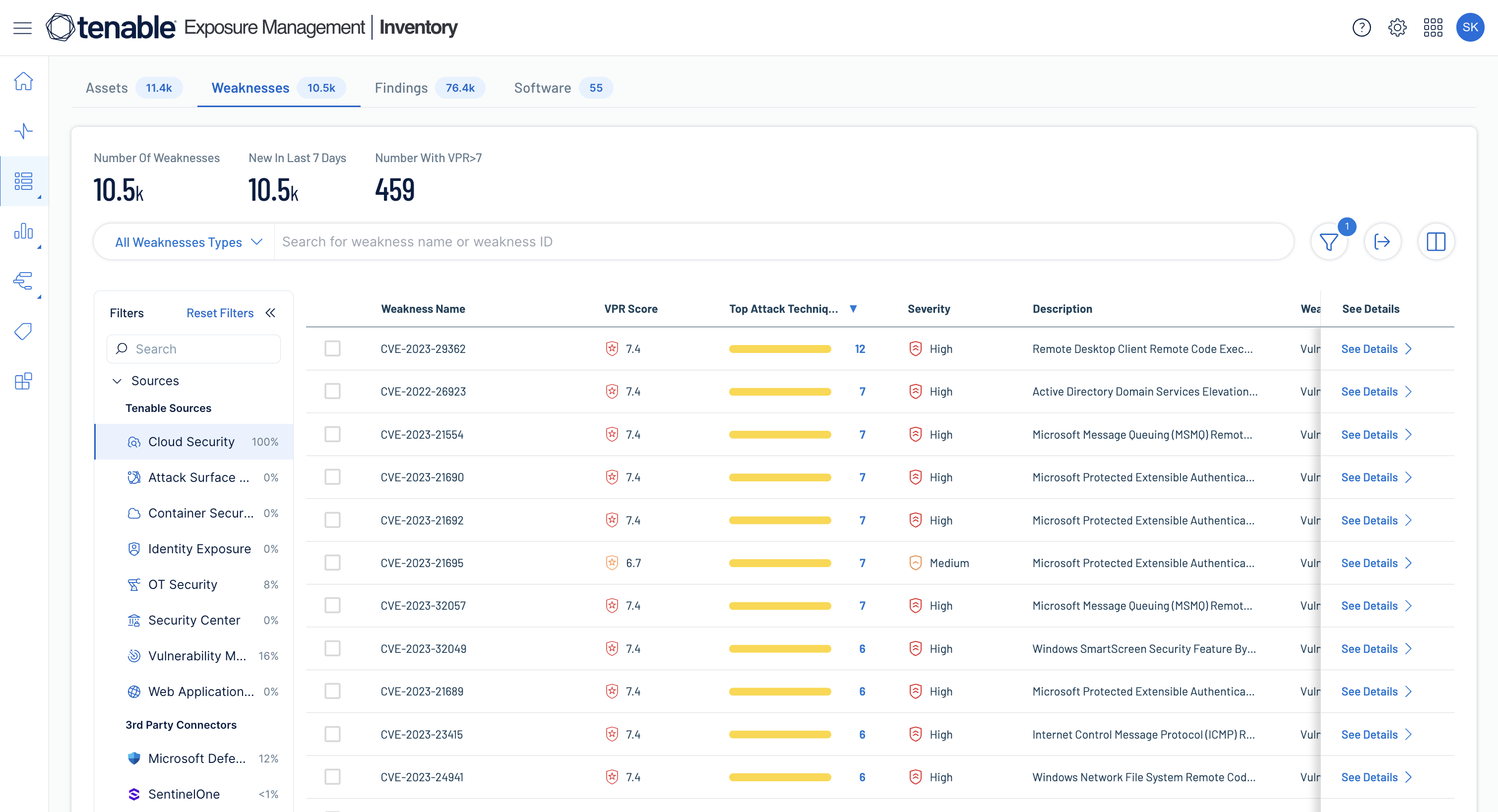
Gain full visibility into IT, OT, and IoT endpoints. Detect vulnerabilities, misconfigurations, and unmanaged devices, prioritize risks, and automate remediation to maintain continuous trust and compliance.
Learn morePrevent lateral movement
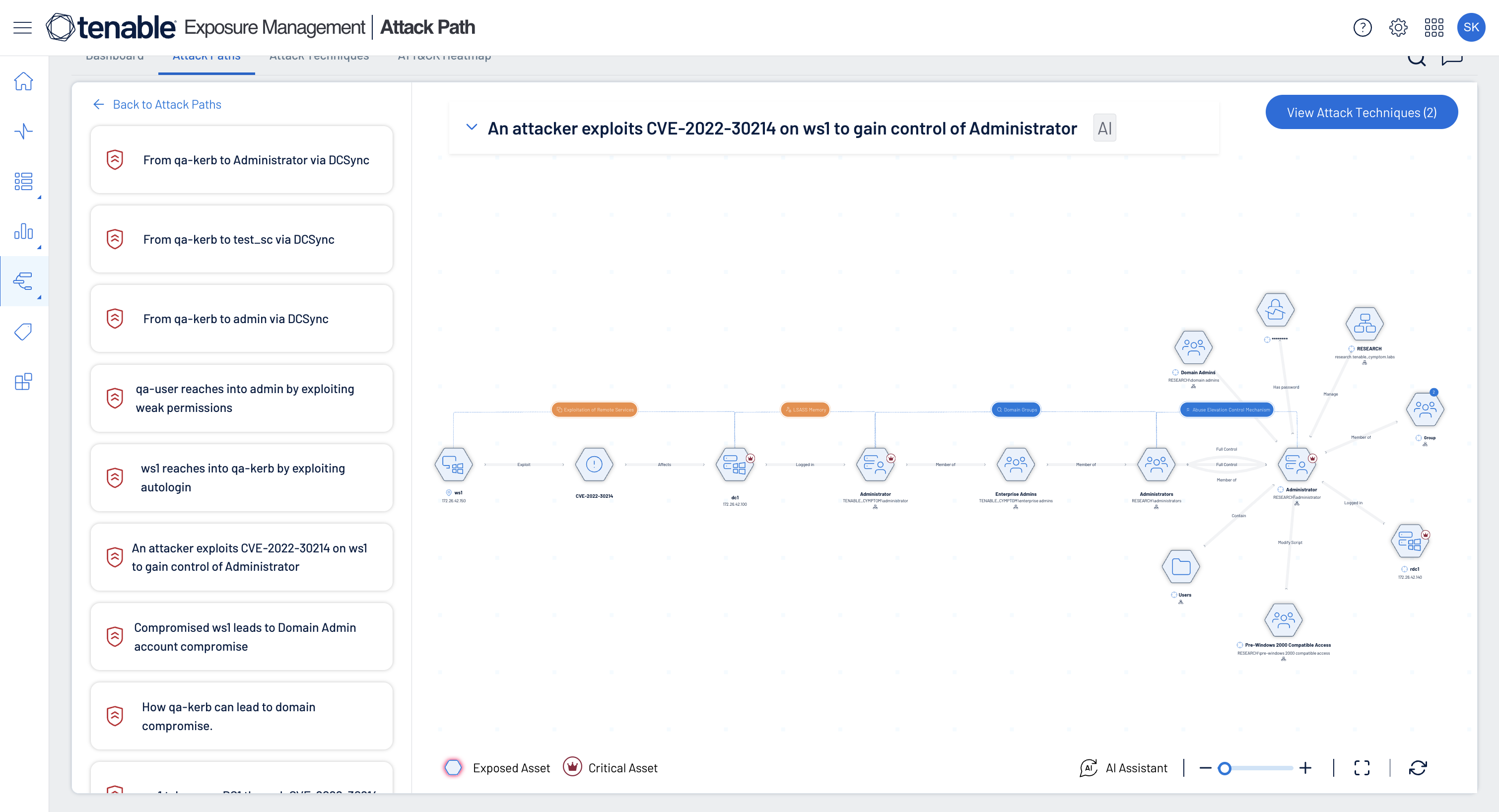
Map exploitable attack paths, segment networks, and monitor east-west traffic. Detect misconfigurations, enforce microsegmentation, and integrate with SDN and orchestration tools to reduce attack surface and contain breaches.
Learn moreSecure applications and workloads
Protect cloud workloads from build to runtime. Scan IaC, container images, and CI/CD pipelines, monitor runtime vulnerabilities, enforce segmentation, and prioritize remediation to prevent lateral movement and reduce exposure.
Learn moreProtect critical data
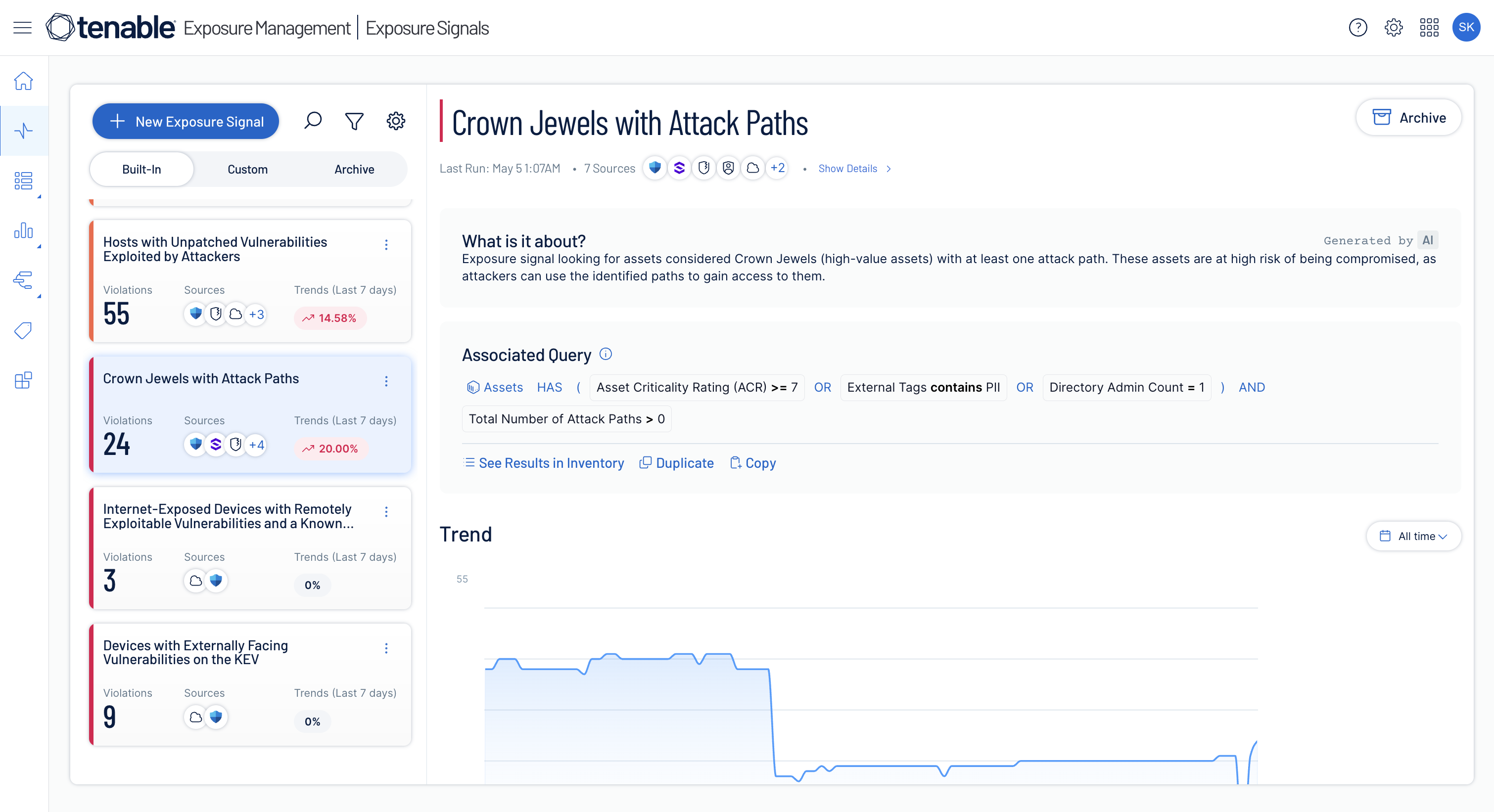
Discover sensitive data across cloud and hybrid environments. Detect risky access, misconfigurations, and policy drift to enforce least privilege, prevent exposure, and maintain continuous compliance.
See and understand risk
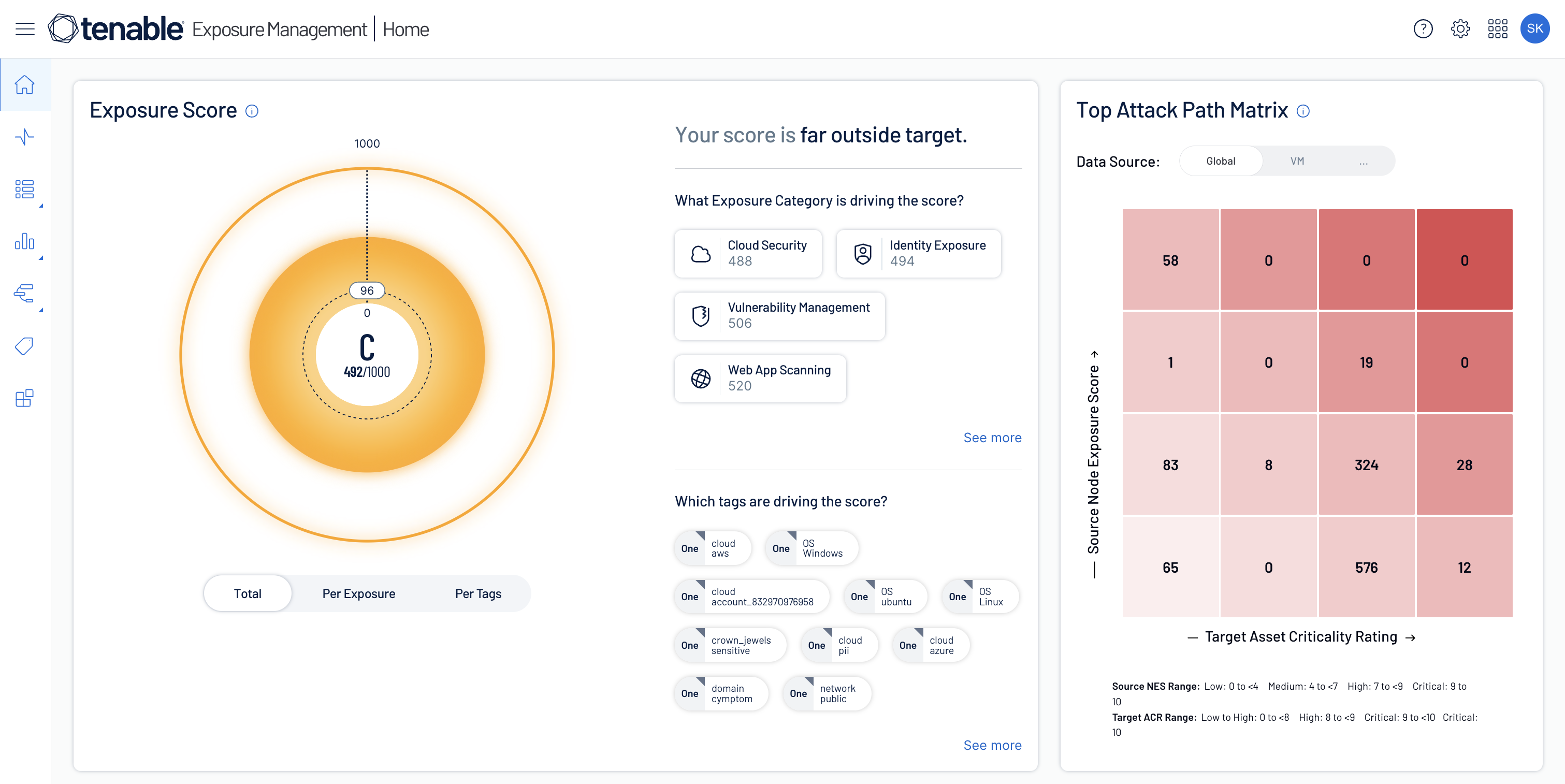
Correlate identity, device, cloud, and OT data into unified exposure insights. Visualize attack paths, monitor anomalies, and prioritize remediation to continuously reduce risk across all environments.
Take a self guided tourRelated products
Related resources
Get Started with Tenable One
Tenable One has helped our engineers reduce the time spent on manual tasks by 75%, which allows them to focus on actual engineering work.
- Tenable Identity Exposure
- Tenable One
- Tenable Vulnerability Management