Data Security Posture Management (DSPM)
Safeguard sensitive cloud data with a unified CNAPP
Protect your cloud data from unauthorized access and other exposures with data security posture management (DSPM) integrated into a unified cloud native application protection platform (CNAPP). By integrating DSPM into your unified cloud security strategy, you get actionable data context that better prioritizes risks and reduces your organization's exposure to customer data breaches and the compromise of AI resources and intellectual property.
Request a demo Take a self-guided tourIdentify and protect sensitive cloud data
Know where your data resides and if it’s sensitive
Find data across multi-cloud environments and classify it
Expose risk with personalized precision
Prioritize data exposures that create attack paths and put your business at risk
Close cloud data risk with contextualized remediation
Take action on data risk with guided and automated remediations
Prioritize and address
multi-cloud data risk
Tenable Cloud Security, with integrated DSPM capabilities, continuously monitors your multi-cloud environment to discover and classify data types, assign sensitivity levels and prioritize data findings in the context of the entire cloud attack surface.
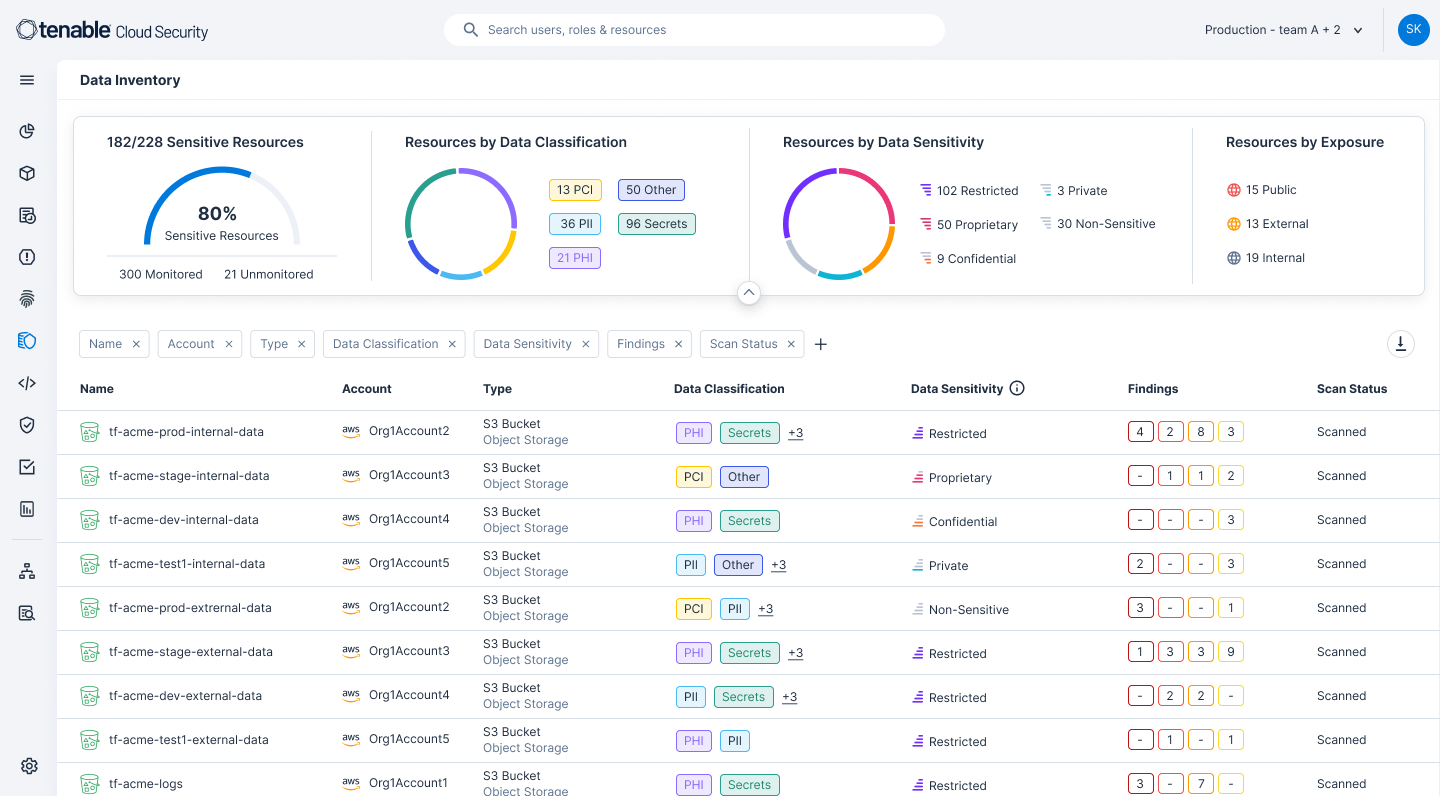
Discover and classify sensitive data
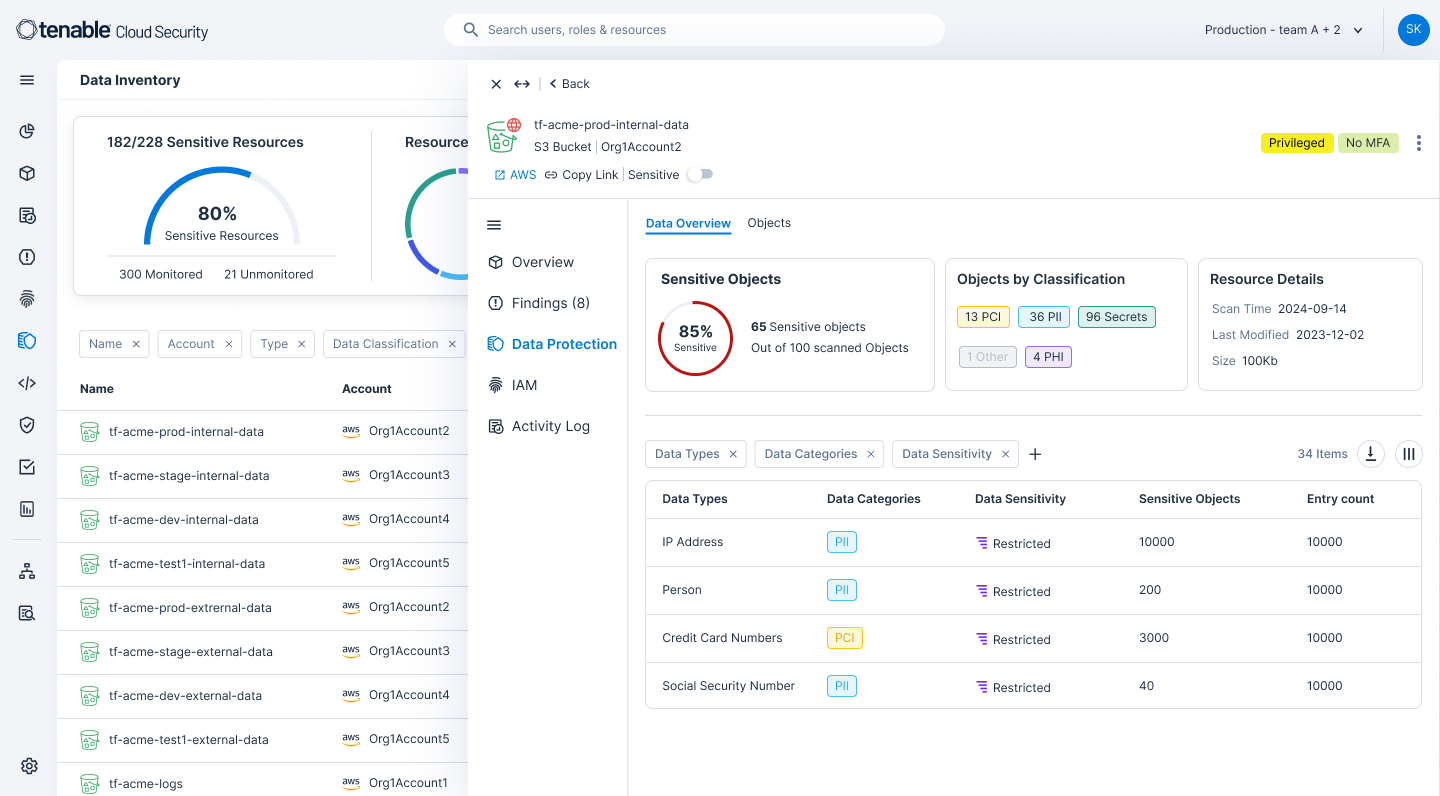
Get full visibility into where data resides across your cloud environment. From AI services and workloads to S3 buckets, Tenable Cloud Security identifies data resources using agentless API scans, classifies data findings by severity levels and then groups data into categories such as company secrets or PHI. This three-layered approach understands account context and reduces alert noise so you can prioritize the exposures that matter most to your organization's overall compliance and security posture.
Enforce least privilege access to data
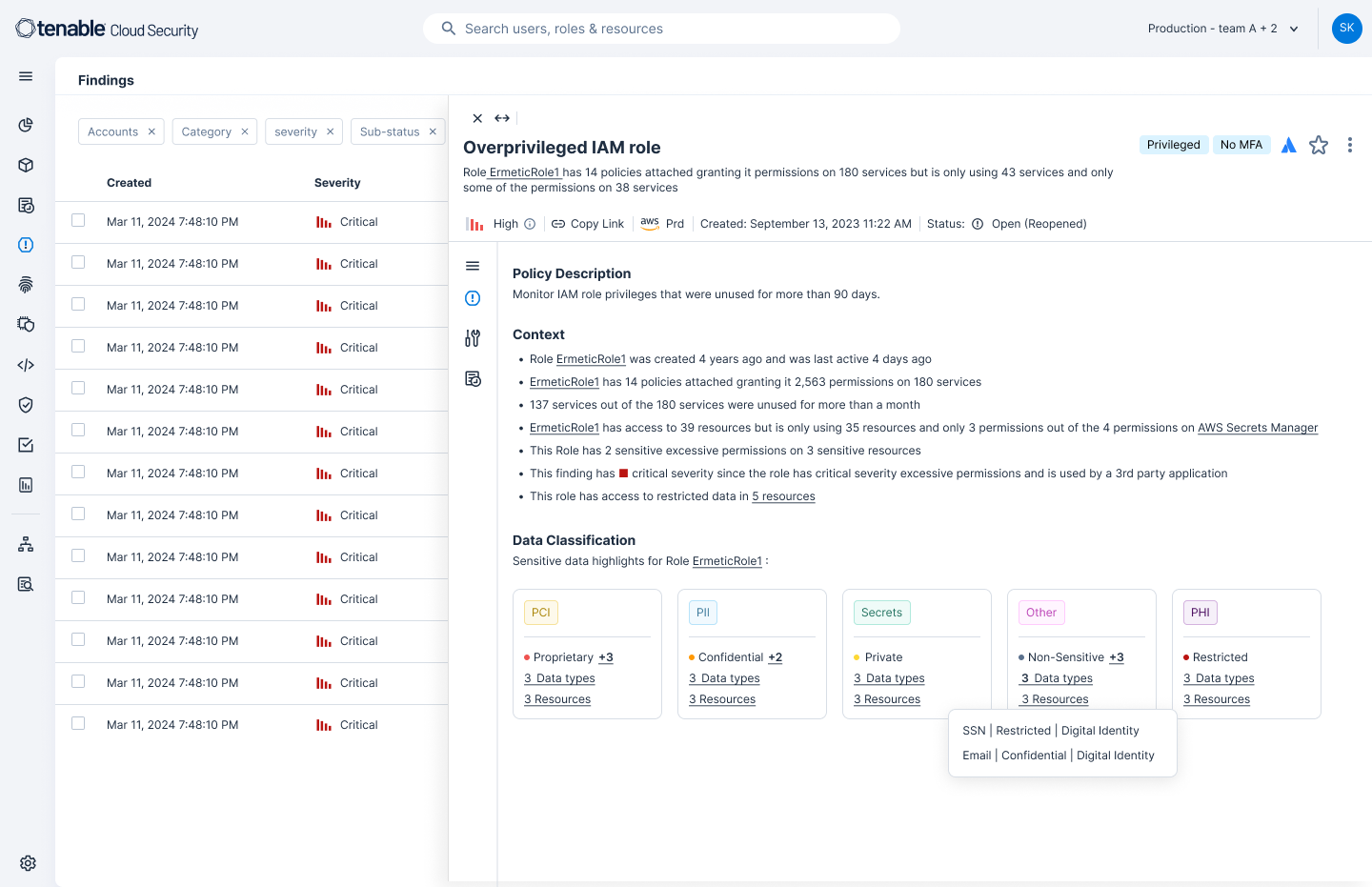
Detect suspicious data-related activity before it becomes a breach and investigate anomalies with granular identity and access insights. Tenable Cloud Security enriches identity findings with data classification context so you can see where a machine or human identity can access sensitive data resources and revoke permissions as needed. View data security context in the identity and access management (IAM) dashboard to perform deep analysis of sensitive data access and take action to block attack paths that an attacker could exploit.
Prioritize remediation based on your security and compliance goals
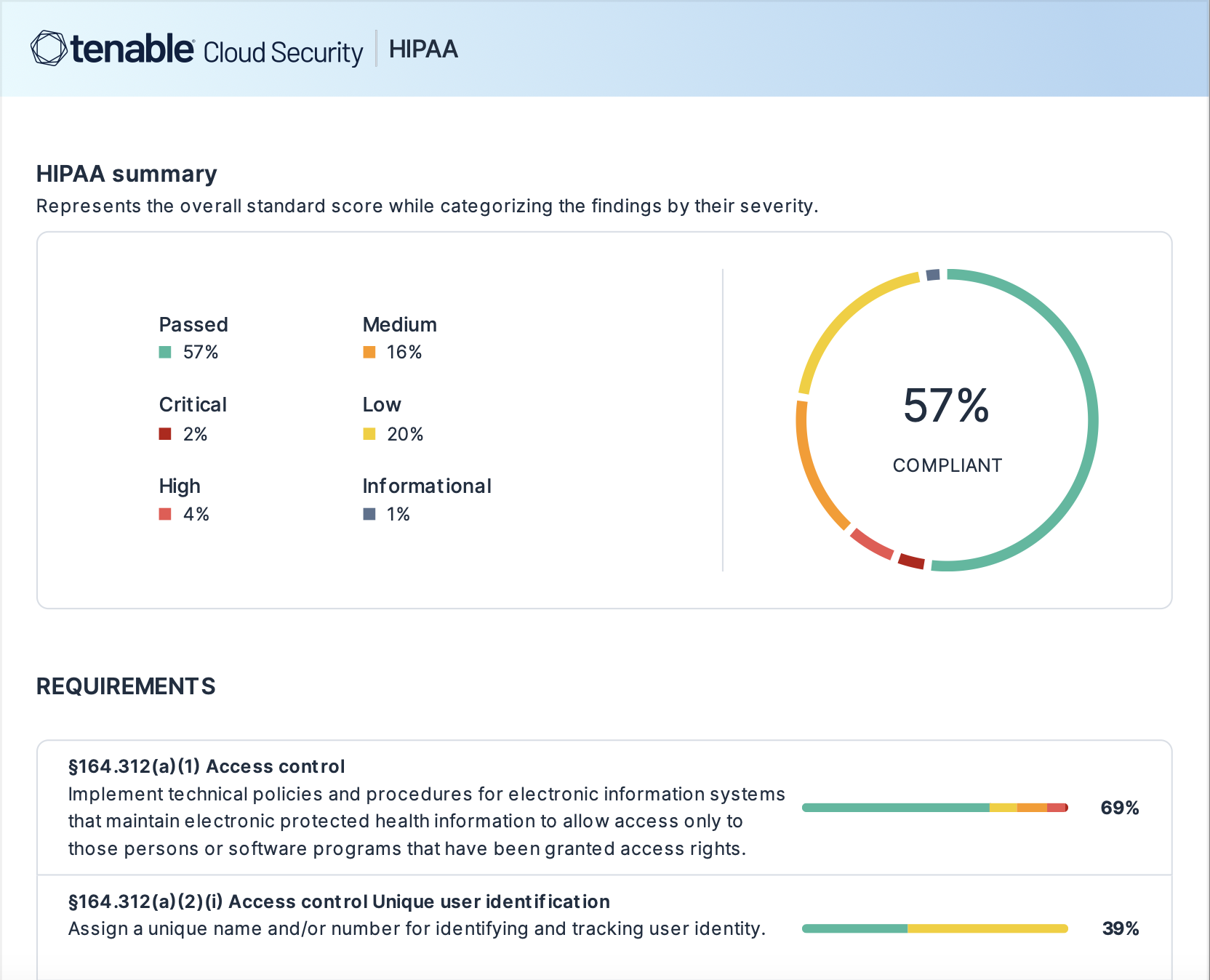
Take advantage of built-in and customizable policies to evaluate data configurations and get alerts on critical exposures specific to your business. Tailor security findings with custom data labels or import them from your cloud environments. Take action on these prioritized risks with step-by-step remediations and deep context that provides details behind risky configurations or privileges. Generate one-click reports to communicate industry-specific compliance requirements for PII, PHI and PCI.
Learn more about Tenable Cloud Security
Using [Tenable Cloud Security] automation allowed us to eliminate exhaustive manual processes and perform in minutes what would have taken two or three security people months to accomplish.
- Tenable Cloud Security