Tenable Cloud Security Just-in-Time (JIT) Access
Enhance your security posture with Just-in-Time (JIT) Access for cloud resources
Eliminate the risk caused by threats that gain control of human identities with long-standing access to cloud resources. Instead, grant temporary access to critical cloud resources.

Today, we are using Tenable Cloud Security to deliver temporary access control to a key banking client, meeting our privileged access management cloud use case, and also to rationalize permissions and better control access in our complex AWS environment.
Minimize your access risks while ensuring developers remain agile
Static, longstanding access and elevated permissions to cloud resources can expose your organization to vulnerabilities that attackers can exploit. The challenge is how to maintain user productivity by providing access to what they need without opening your organization to unnecessary risks.
Tenable Cloud Security Just-in-Time (JIT) Access solves this by quickly and seamlessly granting users temporary, time-based access to sensitive cloud resources and business applications when they request them on an as-needed basis.
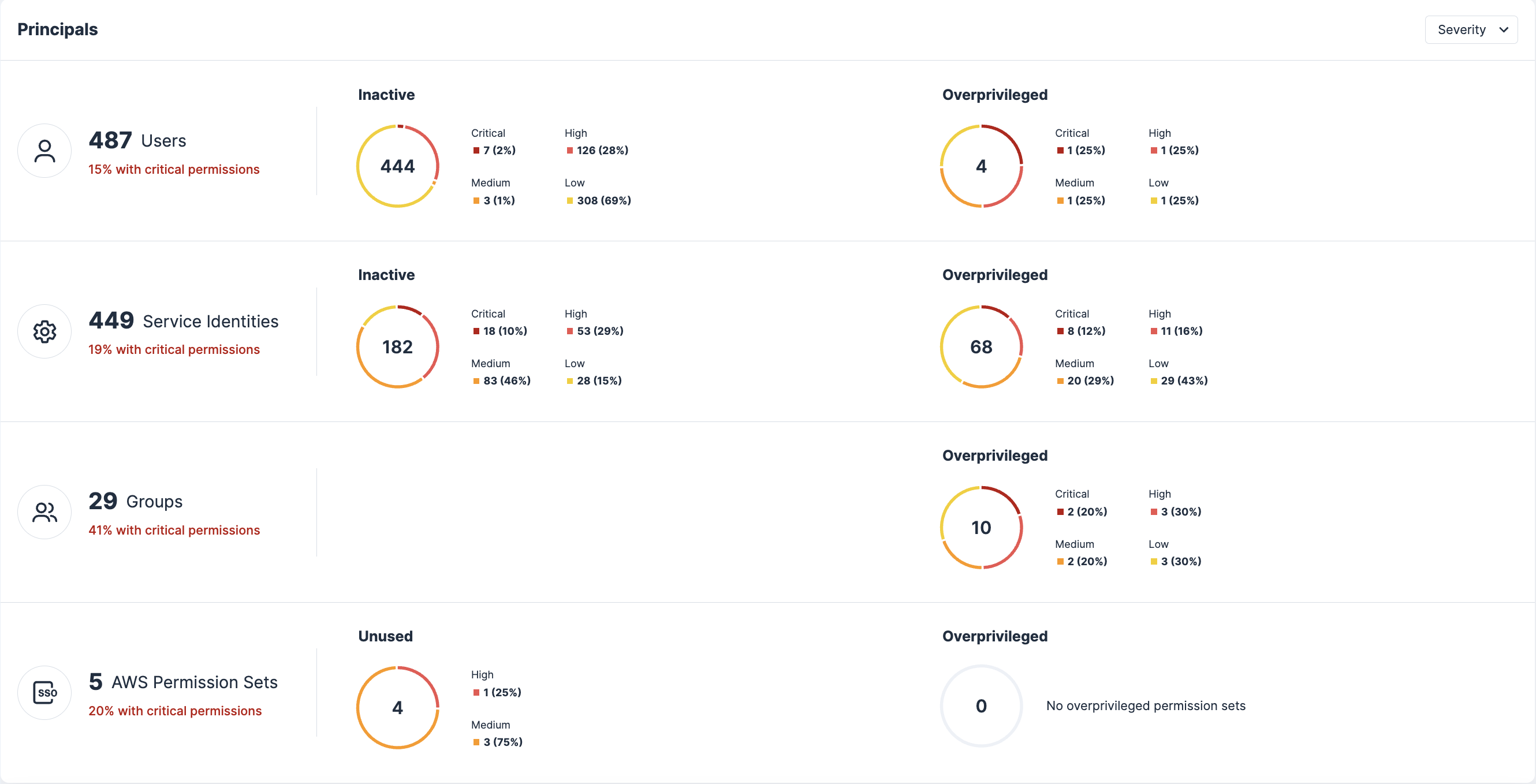
Identify excessive permissions risk
Highlight risks associated with human identities that have excessive access by comparing effective permissions for these identities to actual permissions used using the Tenable Cloud Security Cloud Infrastructure and Entitlement Management (CIEM) capability. This helps your organization understand user behavior and apply least privilege by correctly right-sizing access for your users.
Users can then request and be granted access to additional resources on a temporary, as-needed basis using Tenable Cloud Security Just-in-Time (JIT).
Seamless access request workflows
Your users don’t need access to all resources, all the time. In many cases, they may only need access to specific resources for ad hoc assignments.
JIT provides a seamless workflow that enables users to request access to resources when they need them. In fact, they can quickly submit a request using messaging apps like Slack or Microsoft Teams. Approvers, such as cloud administrators and security teams, can then quickly grant access without slowing down productivity.
Continuously audit and govern access
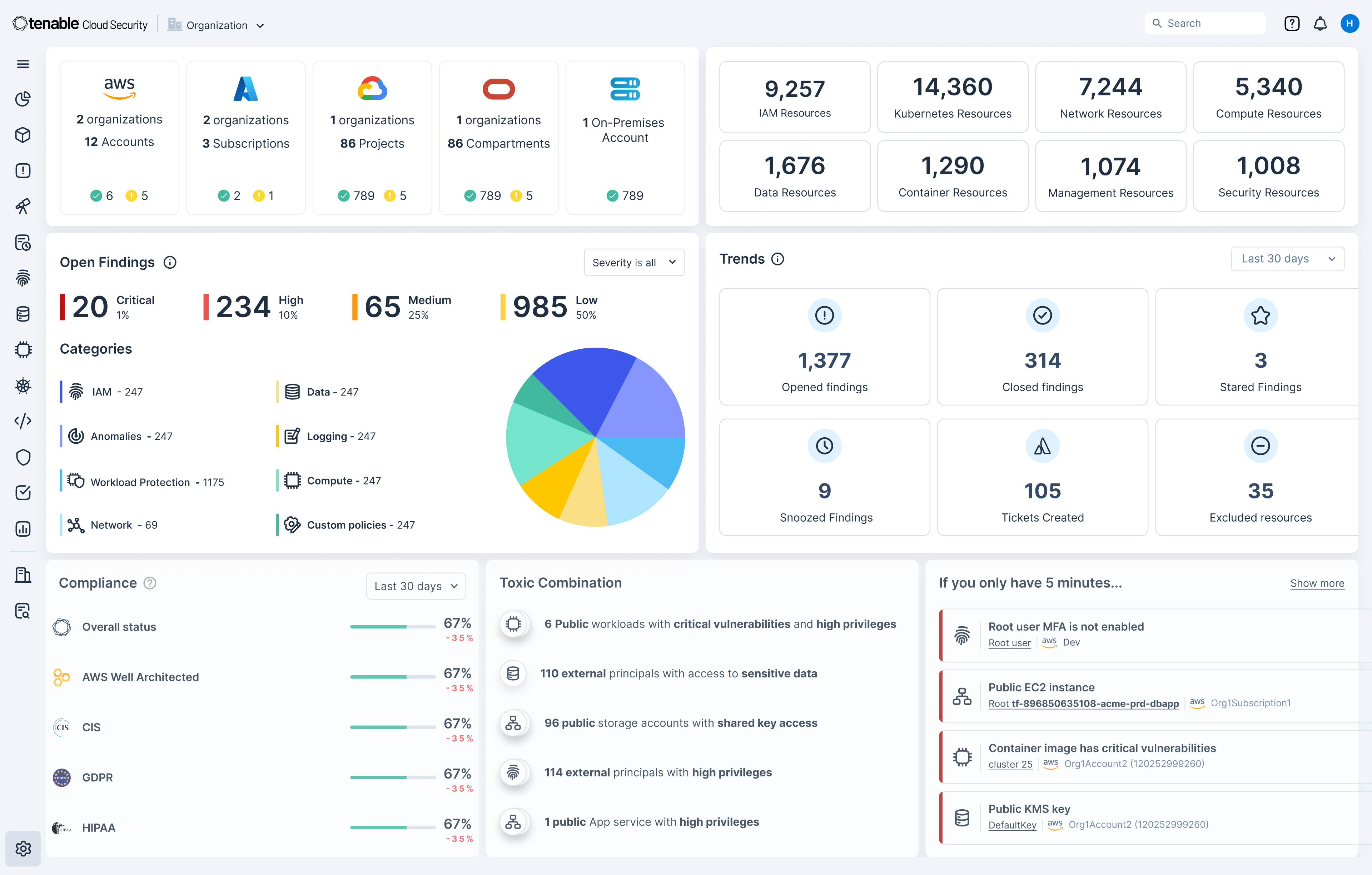
Approvers can visualize the “who, what and when” of user access and permissions including all JIT session activity, access requests and authorizations in a dedicated view. They can also maintain an audit trail and investigate access activity with the Cloud Security Posture Management (CSPM) feature in Tenable Cloud Security.
Using built-in reports, teams can communicate with stakeholders about internal compliance, external audits and daily security activities, including by users during elevated sessions, past requests and the underlying authorization process.
Experience complete cloud-native security
Tenable JIT Access is part of Tenable Cloud Security – a comprehensive cloud-native application protection platform (CNAPP) – that secures cloud environments including AWS, Azure and Google Cloud.
Find out how Tenable Cloud Security automates security and compliance from development to runtime to help you reveal, prioritize and remediate security gaps with better insight and precision today.
Learn moreRelated resources
Learn more about Tenable Cloud Security
Using [Tenable Cloud Security] automation allowed us to eliminate exhaustive manual processes and perform in minutes what would have taken two or three security people months to accomplish.
- Tenable Cloud Security