Post-Hunt Survival Skills: Scope and Triage
Inevitably when you threat hunt - you will find something. What happens next? A barrage of questions ensues:
- Is it an incident, administrative activity, an external attacker in your environment?
- How did the attackers get in, what did they touch, and what systems and services are impacted.
- Is it simply a misconfiguration of a service, uncovered by the hunt?
Answering these questions can be the most unexpectedly challenging aspect of threat hunting, depending on the size and maturity of your organization. How do you determine when to escalate and call in responders?
Tenable provides many features to find and scope the breadth of an incident prior to the fire drill
The time to deploy new security technologies for response and forensics is not during an incident. Leveraging simple tools that you already have in your arsenal to follow up the hunt is essential to ensuring success. Tenable provides many features to find and scope the breadth of an incident prior to the fire drill to make it less frantic, and to arm incident responders with critical information to enable quick and decisive action.
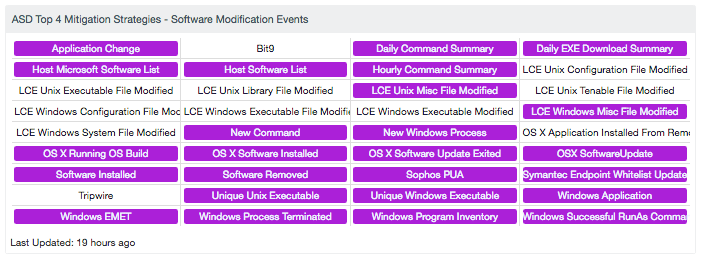
Continuous endpoint data collection
Tenable captures ongoing information about hosts in several categories:
- AutoRuns and Scheduled Tasks
- File Downloads
- Host Changes
- Network Traffic
- Processes Launched
- Software/Services Installed
- Threat Intelligence and Malware Indicators
- User Creation and Modification
This information—already captured in your environment through regular monitoring—can provide the essential information to scope an incident and to identify what happened during an event.
Host persistence - autoruns and scheduled tasks
We’ve blogged before about leveraging the power of Nessus® with built-in threat intelligence to detect malicious or unique autoruns, scheduled tasks, and other registry entries that are signs of attacker persistence.
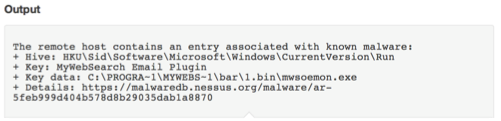
Every scan, whether scheduled or ad-hoc that has the Windows plugin family enabled, comes with a host of autoruns and other detections that capture this invaluable information for responders to work with.
Monitoring host changes
The attackers will have touched something to forward their objective: running reconnaissance commands, installing persistent backdoors or credentials, or accessing and changing files. All of these things leave digital footprints that the responder can follow to recreate what happened. Tenable SecurityCenter Continuous View™ (Security Center CV™) host data sensors continuously monitor activity at the system level, capturing authentication, system changes, files in monitored directories, programs and processes launched, as well as anomalous system activity such as unique executables and binaries or unusual commands launched by a user.
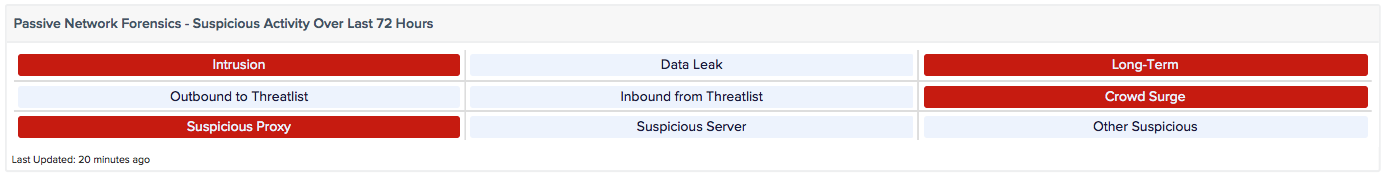
Lateral movement and exfiltration
Lateral movement between hosts in your environment is almost as critical for an attacker’s success as the initial entry point. When attackers remain in one place for too long they get caught. The upside to this is that as an attacker traverses hosts it leaves a spider web of network activity tracking back to the initial entry point. SecurityCenter CV continually monitors network traffic at multiple layers from flow information through protocol inspection, and stores all of the findings without the storage overhead of deep packet inspection tools.
Unexpected connections between hosts are flagged as anomalies, particularly when using an administrative protocol such as SSH or VNC. Traffic is also flagged for abnormally large sizes and abnormally long durations, useful for detecting attempted data exfiltration.
Finally, threat intelligence plays a role here as well. As discussed in Threat Hunting 201, all traffic inspected is automatically matched against intelligence sources, to immediately flag attempts to communicate with known malicious destinations.
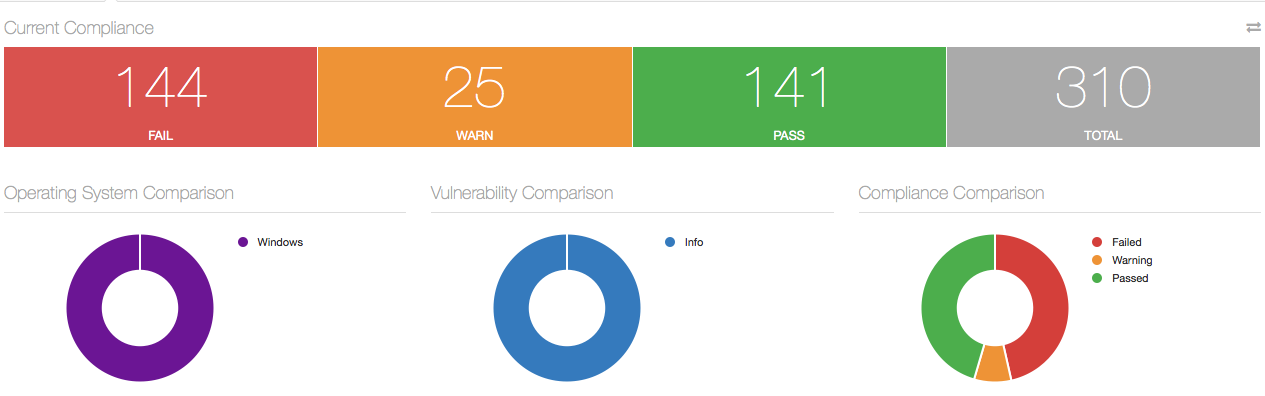
Targeted triage audits
Once an initial scope has been put together, you need a targeted data capture of the hosts involved to grab artifacts and to build an incident timeline. Nessus can facilitate data capture on hosts using customized audit files to run commands, pull information and organize the data.
For Windows hosts, running PowerShell Cmdlets from within Nessus policies opens up some very innovative use cases that rapidly perform targeted forensic searches across your environment and output the results as compliance findings in Nessus and SecurityCenter.
PowerShell forensics is a rapidly emerging method for dealing with Windows incidents, and Nessus can facilitate calls to other tools like Invoke-IR PowerForensics by wrapping it in logic-based automation using an audit file.
Not content to work in Windows-only environments, audit files also have the ability in Linux/Unix environments to run CMD_EXEC checks, which execute a shell command and then compare the resulting output. The possibilities here are limited only by your team’s imagination and command-line familiarity.
<custom_item>
type: CMD_EXEC
description: "Make sure that we are running FreeBSD 4.9 or higher"
cmd: "uname –a"
timeout: 7200
expect: "FreeBSD (4\.(9|[1-9][0-9])|[5-9]\.)"
dont_echo_cmd: YES
</custom_item>As with all forensic info-gathering, use with caution and understand what commands you are automating with Nessus, as well as their expected output. In an ideal scenario, your security team would preemptively build files with frequently needed triage commands and just leverage these audits when incidents occur to save time and ensure that scripts work as intended. More mature organizations can automate the whole process using SecurityCenter CV, and launch targeted Nessus audits against hosts triggered by real-time detections like high-level indicator events to provide a complete package of data before you even know you need it.
Using your existing security tools in unexpected ways not only makes your team more agile in their response but it also helps to reduce the crisis mindset
Hunting forces many organizations to deal with security incidents that they have never prepared for. Using your existing security tools in unexpected ways not only makes your team more agile in their response but it also helps to reduce the crisis mindset by leveraging familiar technologies that the team is already comfortable with. Tenable Nessus and SecurityCenter CV are extremely useful and versatile tools in your arsenal to thwart the bad guys—scoping incidents and quickly gathering artifacts, while continuously uncovering weaknesses in your environment and managing your vulnerabilities.
More information
See my previous blogs on threat hunting techniques:
- Threat Hunting 101: Taming Your Data
- Threat Hunting 201: Quick Wins with DNS
- Threat Hunting 202: Practical Whitelisting
And visit our website to learn more about Tenable’s Threat Hunting solution.
- Nessus
- SecurityCenter
- Threat hunting