CVE-2025-4427, CVE-2025-4428: Ivanti Endpoint Manager Mobile (EPMM) Remote Code Execution

Background
On May 13, Ivanti released a security advisory to address a high severity remote code execution (RCE) and a medium severity authentication bypass vulnerability in its Endpoint Manager Mobile (EPMM) product, a mobile management software that can be used for mobile device management (MDM), mobile application management (MAM) and mobile content management (MCM).
| CVE | Description | CVSSv3 |
|---|---|---|
| CVE-2025-4427 | Ivanti Endpoint Manager Mobile Authentication Bypass Vulnerability | 5.3 |
| CVE-2025-4428 | Ivanti Endpoint Manager Mobile Remote Code Execution Vulnerability | 7.2 |
Analysis
CVE-2025-4427 is an authentication bypass vulnerability in Ivanti’s EPMM. An unauthenticated, remote attacker could exploit this vulnerability to gain access to the server’s application programming interface (API) that is normally only accessible to authenticated users.
CVE-2025-4428 is a RCE in Ivanti’s EPMM. An authenticated attacker could exploit this vulnerability to execute arbitrary code on a vulnerable device.
An attacker that successfully exploits these flaws could chain them together to execute arbitrary code on a vulnerable device without authentication. Both vulnerabilities are associated with open source libraries used by the EPMM software. Ivanti has indicated that these vulnerabilities have been exploited in the wild in a limited number of cases.
Customers that restrict API access via the Portal ACLs functionality or an external WAF have reduced exposure to these vulnerabilities.
Ivanti has credited the CERT-EU with reporting these vulnerabilities.
Proof of concept
At the time this blog post was published, there was no public proof-of-concept available for CVE-2025-4427 or CVE-2025-4428.
Solution
The following table details the affected and fixed versions of Ivanti EPMM for both CVE-2025-4427 and CVE-2025-4428:
| Affected Version | Fixed Version |
|---|---|
| 11.12.0.4 and prior | 11.12.0.5 |
| 12.3.0.1 and prior | 12.3.0.2 |
| 12.4.0.1 and prior | 12.4.0.2 |
| 12.5.0.0 and prior | 12.5.0.1 |
Identifying affected systems
A list of Tenable plugins for this vulnerability can be found on the individual CVE pages for CVE-2025-4427, and CVE-2025-4428 as they’re released. This link will display all available plugins for these vulnerabilities, including upcoming plugins in our Plugins Pipeline.
Additionally, customers can utilize Tenable Attack Surface Management to identify public facing assets running Ivanti EPMM by using the following filters:
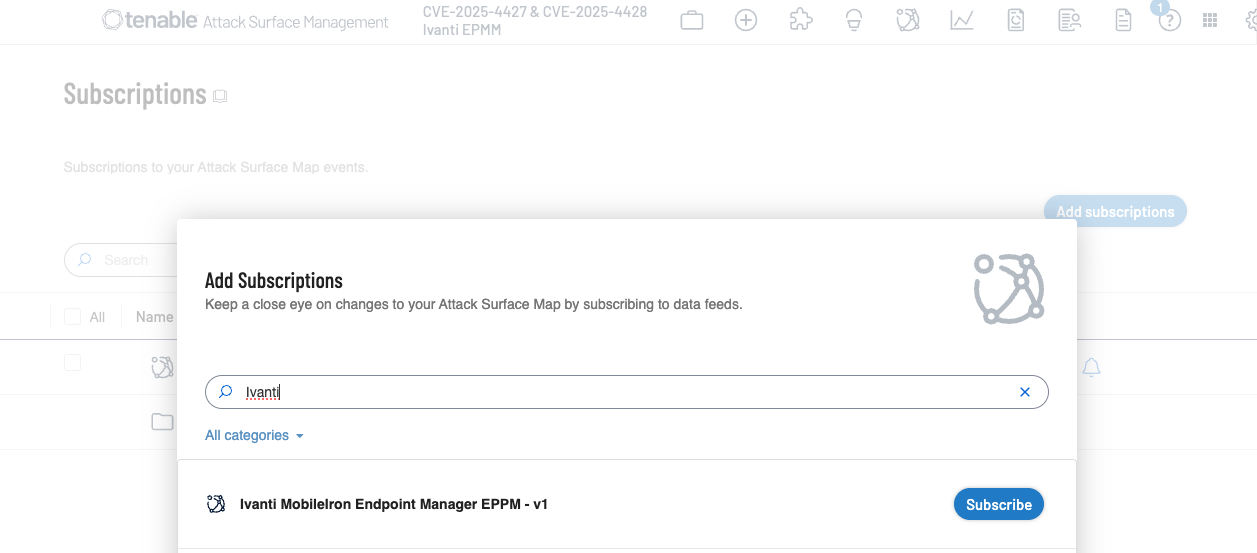
Get more information
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
- Exposure Management
- Nessus
- Tenable Vulnerability Management
- Vulnerability Management
- Vulnerability Scanning



