How to Use VPR to Manage Threats Prior to NVD Publication

How does Tenable’s VPR score help users manage newly disclosed vulnerabilities, even before they’re published on the National Vulnerability Database (NVD)? Let’s find out.
In April, we published a blog on how vulnerability priority rating (VPR) was used to help prioritize the most dangerous CVEs in 2019. Many of the vulnerabilities covered in that post were old but newer vulnerabilities shouldn’t be neglected. Our research shows that many vulnerabilities are targeted by threat actors shortly after public disclosure. In the case of zero-days, they’re targeted even before the public is notified. This blog will discuss how VPR can be used to prioritize vulnerabilities prior to publication on the National Vulnerability Database (NVD).
From Vulnerability to NVD CVE
The NVD is a vulnerability repository consisting of databases implementing aspects of Security Content Automation Protocol (SCAP), such as: Common Vulnerabilities and Exposures (CVE); Common Platform Enumeration (CPE); Common Configuration Enumeration (CCE); and Common Vulnerability Scoring System (CVSS). It is a primary source of vulnerability information for cybersecurity practitioners and researchers.
The screenshot in Figure 1 shows a typical CVE entry page displaying the CVE ID, a short description of vulnerability impact and external references, often provided by CVE Numbering Authorities (CNA). Other information can include CVSS metrics (v2 and v3), Common Weakness Enumeration (CWE) and affected product configurations as CPE.
Figure 1. Screenshot of NVD page
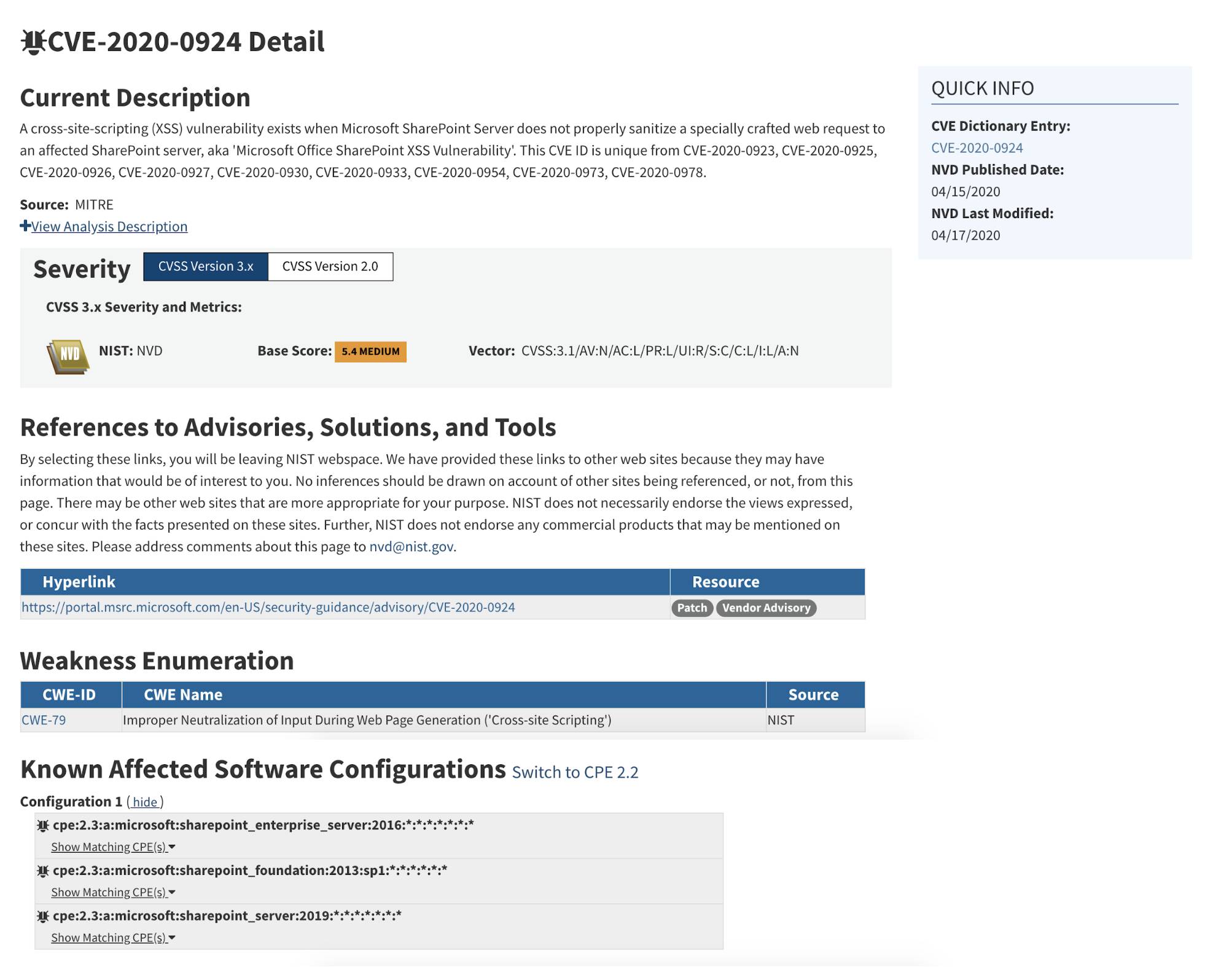
Normally, the CNA would assign a CVE ID to the vulnerability on its discovery. Subsequently, the CNA would start to prepare information for publishing it to NVD — impact analysis, description of the vulnerability, assign a CVSS vector, and so forth. The completed CVE entry is sent to the MITRE CVE team to be published on NVD. In parallel, the vulnerability may already be disclosed on CNA’s security advisory board.
What is a pre-NVD gap?
As a result of the process outlined above, the CVE publication workflow may result in a delay between the initial public disclosure of a vulnerability and its publication on NVD. NVD acknowledges the existence of such a lag and points out that:
The "Date Entry Created" date in a CVE Entry indicates when the CVE ID was issued to a CVE Numbering Authority (CNA) or the CVE Entry published on the CVE List. This date does not indicate when the vulnerability was discovered, shared with the affected vendor, publicly disclosed, or updated in CVE.
In the remainder of this blog post we refer to the time gap between the public disclosure of a vulnerability and its publication on NVD as a pre-NVD gap. Let’s use CVE-2019-17026 as an example to get a more concrete idea of a pre-NVD gap:
- CVE-2019-17026 was first reported in the Mozilla Security Advisory on Jan 8, 2020
- It was then published to NVD on March 2, 2020
- Two days later, on March 4, 2020, it received CVSS metrics
In this example the pre-NVD gap of CVE-2019-17026 is from Jan 8 to March 2 – a 55-day pre-NVD gap.
Many CVEs experienced big pre-NVD gaps in recent years
Having a pre-NVD gap is not rare for CVEs – 71,000 CVEs are first disclosed in vendor security advisories prior to publication on the NVD, accounting for half of all CVEs. In 2019, 5,300 CVEs had a pre-NVD gap.
Figure 2. Annual number of pre-NVD CVEs broken out by pre-NVD gap size since 2006
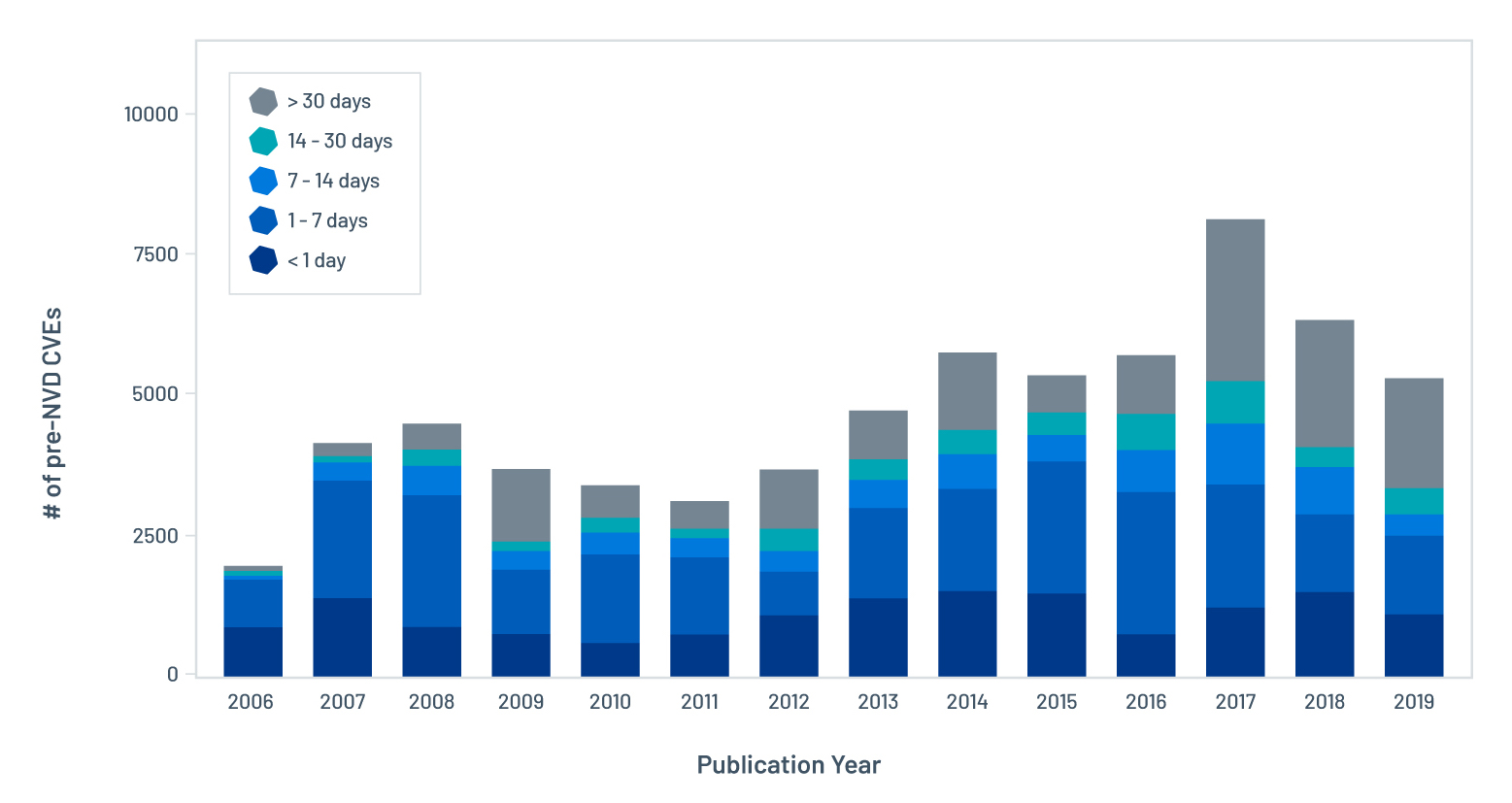
While the pre-NVD gap of some CVEs falls in an acceptable range of one day, our research shows that this gap is much larger for many other vulnerabilities. Figure 2 shows the annual number of pre-NVD CVEs since 2006, broken out by the gap size. Note that the term pre-NVD CVE is used in this blog to refer to CVEs that have been pre-NVD at some point in their lifecycle (and may still be).
This chart tells us several things:
- The annual number of pre-NVD CVEs has stabilized at around 5,000 since 2013. There was a surge in 2017 leading to the highest annual number of pre-NVD CVE that year at 8,100. Since then, this number has dropped to 5,200 in 2019. This shows that CNAs are becoming more agile in publishing CVEs in recent years.
- The distribution of pre-NVD gap size has become more polarized in recent years. Almost half of the annual pre-NVD CVEs were published on NVD within seven days of their initial disclosure, while a significant proportion took at least 30 days to be published. As cybersecurity practitioners, we need to pay attention to CVEs with a large pre-NVD gap as they can have a detrimental impact on your cyber exposure.
Threat activity prior to NVD publication
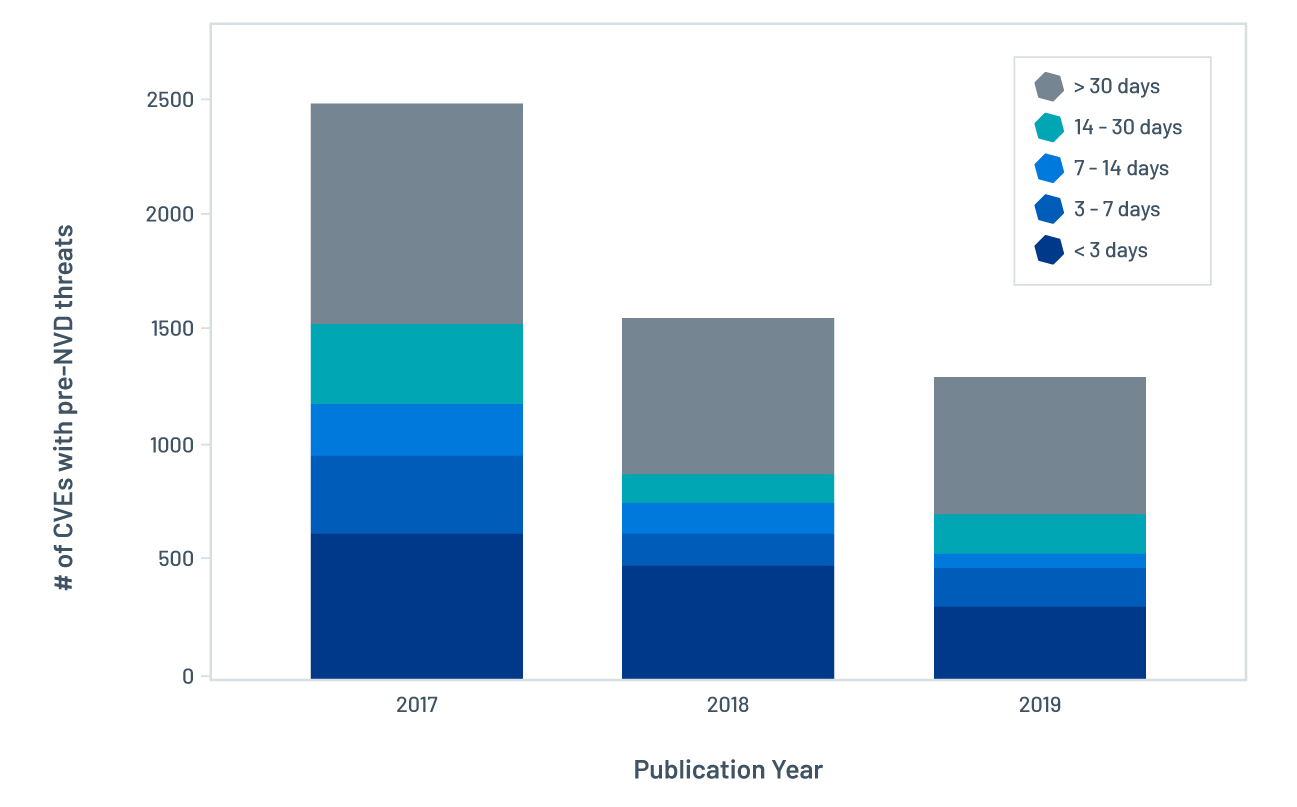
Of course, attackers do not wait until a CVE has been published on NVD before they start targeting it for exploitation. If we cross-reference our threat intelligence data with pre-NVD CVEs, we find that 5,400 out of 43,000 CVEs (12%) published between 2017 and 2019 were associated with threat activity prior to NVD publication.
Figure 3 shows a breakdown of these CVEs by publication year and pre-NVD threat window (i.e. days between the first known threat and its publication on NVD). A large proportion of these CVEs were under threat at least 30 days before NVD publication. As a consequence, any systems impacted by these vulnerabilities will be left exposed to threats before vulnerability information has been made available on NVD.
Figure 3. Number of CVEs with pre-NVD threats since 2017, broken out by pre-NVD threat gap
How to prioritize pre-NVD vulnerabilities for remediation using VPR
It is never too early to remediate vulnerabilities under threat. The previous sections show that NVD is not the most responsive source of information for proactively managing vulnerabilities. Tenable addresses this issue by consuming vulnerability data directly from security advisories for 100+ major vendors, and this number is still increasing.
Extending VPR to scoring pre-NVD vulnerabilities is non-trivial. As discussed in the first part of this blog series, VPR is composed of two major parts: impact and threat. Because many CNAs do not provide CVSS metrics to a vulnerability at its pre-NVD stage, the impact score is not always available to VPR. As a result, VPR combines machine learning with natural language processing (NLP) methods to predict CVSS impact metrics from the raw text descriptions of CVEs. This approach will be discussed in more detail in a future blog post.
In August 2019, Tenable announced that pre-NVD vulnerabilities were now being scored by the VPR model. In total, 12,073 vulnerabilities have been published since August 2019 and 1,592 were pre-NVD at some point following public disclosure. Figure 4 compares the VPR gap, i.e. the time between when a CVE was publicly disclosed and a VPR was assigned, with the pre-NVD gap. VPR is, in general, more responsive than NVD on scoring new vulnerabilities. For example:
- All 1,592 vulnerabilities received a VPR score prior to NVD publication
- 84% of the pre-NVD vulnerabilities were scored by VPR within 24 hours, compared to 38% for NVD
- 499 vulnerabilities took more than seven days to get published on NVD, while only 101 vulnerabilities took more than seven days to receive a VPR score
- 245 vulnerabilities took more than 30 days to get published on NVD
The number of vulnerabilities with a VPR gap will reduce further as Tenable keeps consuming vulnerabilities from more vendors security advisories.
Figure 4. Compare VPR publication gap with pre-NVD gap, broken out by gap size
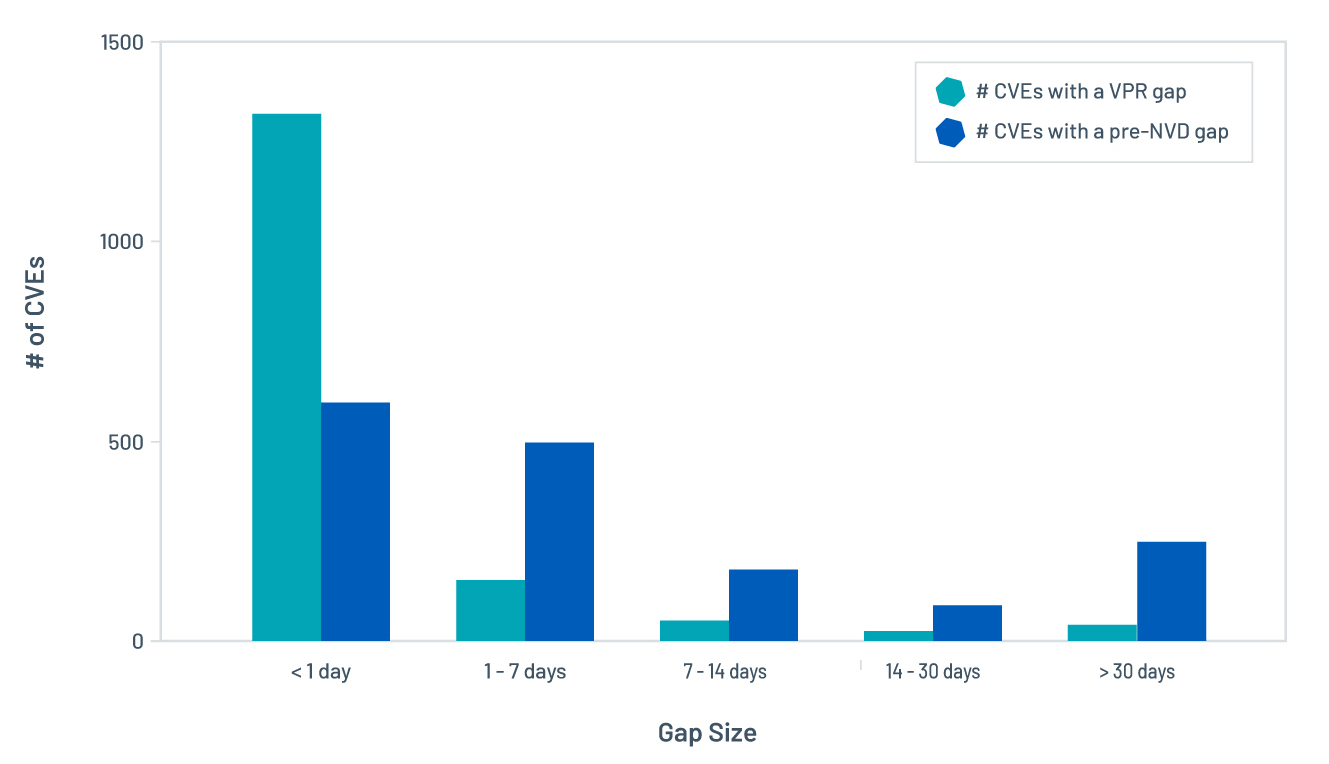
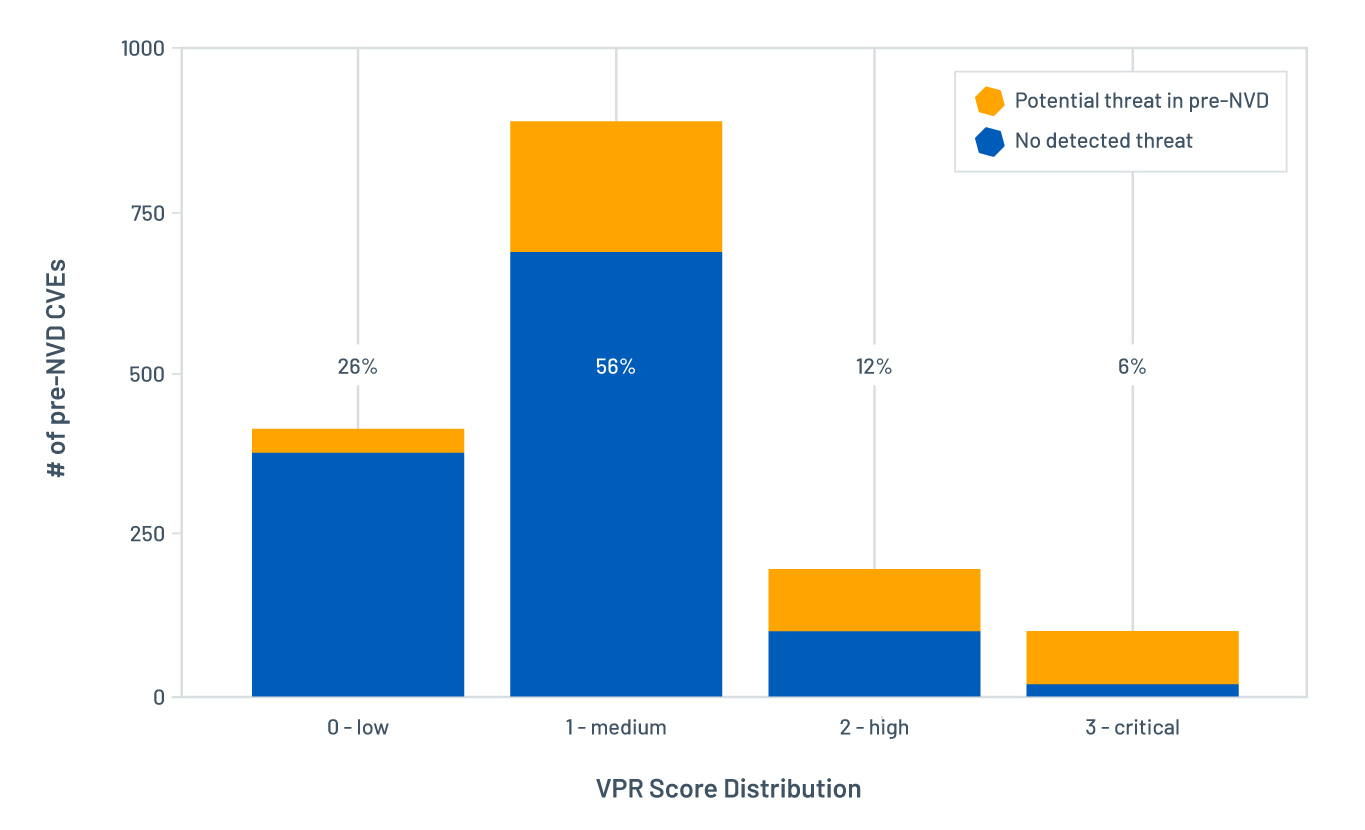
Figure 5 shows the distribution of VPR scores assigned to the 1,592 pre-NVD CVEs during their pre-NVD stage. We see that 98 are rated as VPR Critical, 83 of which were associated with pre-NVD threats. This means VPR gives organizations the opportunity to reduce their attack surface by remediating newly disclosed vulnerabilities that are being targeted in the wild. The proportion of vulnerabilities associated with pre-NVD threats increases in line with the VPR criticality levels — 85% of the VPR Critical vulnerabilities are related to pre-NVD threats, 50% to VPR High and 25% to VPR Medium. This is in line with what was covered in the first part of this blog series.
Figure 5. VPR score distribution for the 1,592 vulnerabilities in the pre-NVD stage
Case Study: CVE-2019-17026
This section uses CVE-2019-17026 as an example to illustrate how VPR can be leveraged for pre-NVD vulnerabilities. Let’s look at the event timeline:
- January 8, 2020: CVE-2019-17026 was first published on Mozilla Security Advisory. In the same security advisory, Mozilla announced it was aware of this vulnerability being exploited in the wild. Tenable published an analysis of this vulnerability following disclosure. On the same day, Tenable published plugins 132714 and 132715 to detect the affected Firefox vulnerability on Windows and plugins 132712 and 132713 for MacOS X. They were published with a VPR score of 9.7 due to the fact that the vulnerability has been leveraged in targeted attacks.
- January 8 to March 1, 2020: The level of threat increased during the pre-NVD phase of this vulnerability. Multiple discussions and research of the exploitation of this vulnerability were observed across various sources, including Twitter, underground forums, Dark Web sites and technical blogs. This drove the VPR score up to 9.9 at its highest peak prior to NVD publication.
- March 2, 2020: CVE-2019-17026 was published on NVD and two days later it was analyzed resulting in a CVSSv3 score 8.8.
- March 3, 2020 and after: The threat to this vulnerability remains high since its publication on NVD. More threat events have been detected on various sources, including mainstream media, Twitter, Dark Web sites, Paste sites and so on. In April, it was disclosed that this vulnerability has been exploited by an advanced persistent threat (APT) named DarkHotel, targeting China and Japan. The VPR for this vulnerability remains Critical at the time of publication.
Key Takeaways
In this blog, we have shown that it is not uncommon for a vulnerability to be targeted by threat actors prior to publication on NVD. Given the publication delays that can occur, security practitioners need to be cautious about using NVD as a single source of truth for vulnerability information. We showed that VPR rates new vulnerabilities in a timely manner – 84% of new vulnerabilities are scored by VPR within one day of public disclosure and 93% are scored within the first week. We also demonstrated how VPR can be leveraged to reduce the attack surface by remediating pre-NVD vulnerabilities under active exploitation.
Acknowledgments
Special thanks are extended to Bryan Doyle, data scientist manager, Kevin Flynn, senior product marketing manager, Susan Nunziata, senior director of editorial and content, and Matthew King, marketing manager, for reviewing this blog and contributing many great ideas.
Get more information
- Start your free trial now to see VPR in action – available in Tenable.io (in the cloud) and Tenable.sc (on-premises)
- Learn more about Tenable Predictive Prioritization and VPR
- SecurityCenter
- Tenable Vulnerability Management
- Tenable Vulnerability Management (DO NOT USE)
- Threat Intelligence
- Vulnerability Management
