CVE-2021-44228: Proof-of-Concept for Critical Apache Log4j Remote Code Execution Vulnerability Available (Log4Shell)

Critical vulnerability in the popular logging library, Log4j 2, impacts a number of services and applications, including Minecraft, Steam and Apple iCloud. Attackers have begun actively scanning for and attempting to exploit the flaw.
Update December 21: A frequently asked questions (FAQ) blog post was published on December 17 with information on Log4Shell and other associated vulnerabilities. For up-to-date information, please refer to our blog post: CVE-2021-44228, CVE-2021-45046, CVE-2021-4104: Frequently Asked Questions About Log4Shell and Associated Vulnerabilities
Background
On December 9, researchers published proof-of-concept (PoC) exploit code for a critical vulnerability in Apache Log4j 2, a Java logging library used by a number of applications and services including but not limited to:
Dubbed Log4Shell by researchers, the origin of this vulnerability began with reports that several versions of Minecraft, the popular sandbox video game, were affected by this vulnerability.
there's a minecraft client & server exploit open right now which abuses a vulerability in log4j versions 2.0 - 2.14.1, there are proofs of concept going around already.
— ᵃᵈᵃᵐ (@twokilohertz) December 9, 2021
Additionally, it appears that cloud services such as Steam and Apple iCloud are also affected.
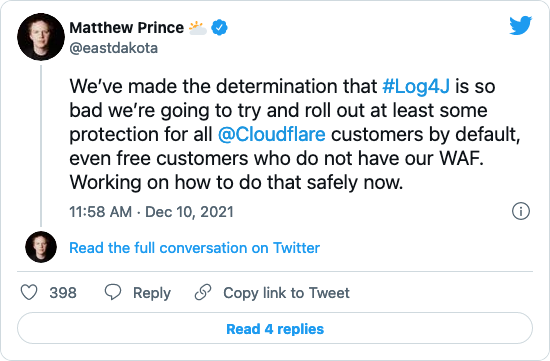
This vulnerability is considered so severe that Cloudflare CEO plans to offer protections for all customers.
Analysis
CVE-2021-44228 is a remote code execution (RCE) vulnerability in Apache Log4j 2. An unauthenticated, remote attacker could exploit this flaw by sending a specially crafted request to a server running a vulnerable version of log4j. The crafted request uses a Java Naming and Directory Interface (JNDI) injection via a variety of services including:
- Lightweight Directory Access Protocol (LDAP)
- Secure LDAP (LDAPS)
- Remote Method Invocation (RMI)
- Domain Name Service (DNS)
If the vulnerable server uses log4j to log requests, the exploit will then request a malicious payload over JNDI through one of the services above from an attacker-controlled server. Successful exploitation could lead to RCE.
In the case of Minecraft, users were able to exploit this vulnerability by sending a specially crafted message through Minecraft chat.
aaaaand then code execution?? #log4j #minecraft pic.twitter.com/aSFzhsm87l
— John Hammond (@_JohnHammond) December 10, 2021
Both GreyNoise and Bad Packets have detected mass scanning activity searching for servers using Log4j.
Mass scanning activity detected from multiple hosts checking for servers using Apache Log4j (Java logging library) vulnerable to remote code execution (https://t.co/GgksMUlf94).
Query our API for "tags=CVE-2021-44228" for source IP addresses and other IOCs. #threatintel— Bad Packets (@bad_packets) December 10, 2021
There are now reports that this vulnerability is being used to implant cryptocurrency miners.
this log4shell payload is... a coin miner
the vulnerability has arrived pic.twitter.com/XUR7I5ydpP— Kevin Beaumont (@GossiTheDog) December 10, 2021
Proof of concept
The first PoC for CVE-2021-44228 was released on December 9 prior to its CVE identifier being assigned. At the time this blog post was published, there were additional PoCs available on GitHub.
Solution
While Apache published a release candidate on December 6 to address this vulnerability, it was incomplete. Apache released 2.15.0 on December 10.
Log4j 2.15.0 requires Java 8. Therefore, organizations that use Java 7 will need to upgrade before being able to update to the patched version of Log4j.
Apache advises that if patching is not immediately possible, there are mitigation routes that can be taken to thwart attempts to exploit this vulnerability. As the information from Apache continues to be updated, we recommend referring to their guidance here.
Because Log4j is included in a number of web applications and used by a variety of cloud services, the full scope of this vulnerability won’t be known for some time. However, at the time this blog post was published, some products and services that were confirmed to be vulnerable include:
| Product/Service | Confirmed Affected |
|---|---|
| Minecraft | Yes |
| Steam | Yes |
| Apple iCloud | Yes |
| Tencent | Yes |
| Yes | |
| Baidu | Yes |
| Didi | Yes |
| Cloudflare | Yes |
| Amazon | Yes |
| Tesla | Yes |
| ElasticSearch | Yes |
| Ghidra | Yes |
A GitHub repository is being maintained that highlights the attack surface of this vulnerability.
Identifying affected systems
A list of Tenable plugins to identify this vulnerability will appear here as they’re released. Additionally, we would like to highlight the following plugins (available in plugin set 202112112213 and later) :
Remote checks
- Plugin ID 156014 - Apache Log4Shell RCE detection via callback correlation (Direct Check HTTP) - This remote check can be used to identify the vulnerability without authentication. This plugin is compatible with Tenable cloud scanners
- Plugin ID 155998 - Apache Log4j Message Lookup Substitution RCE (Log4Shell) (Direct Check) - This plugin listens for an LDAP BIND connection from a target host. It is not compatible with Tenable.io cloud scanners and may fail to return results in certain networks due to firewall rules or interference from other security devices. We continue to explore options for additional detection and recommend Tenable.io cloud scanner customers use the following four plugins.
For an overview of callbacks in Plugin IDs 156014 and 155998, please visit this post on the Tenable community.
Version checks and local detection (authentication required)
- Plugin ID 155999 - Apache Log4j < 2.15.0 Remote Code Execution
- Plugin ID 156000 - Apache Log4j Installed (Unix)
- Plugin ID 156001 - Apache Log4j JAR Detection (Windows)
- Plugin ID 156002 - Apache Log4j < 2.15.0 Remote Code Execution
Additionally, a comprehensive Tenable.io Web App Scanning (WAS) plugin has been released which can be used to test input fields that can be used to exploit Log4Shell.
- Plugin ID 113075 - Apache Log4j Remote Code Execution (Log4Shell)
For supporting information on each of the plugins above, please visit this post on the Tenable Community.
Tenable has released scan templates for Tenable.io, Tenable.sc and Nessus Professional which are pre-configured to allow quick scanning for this vulnerability. In addition, Tenable.io customers have a new dashboard and widgets in the widgets library. Tenable.sc users also have a new Log4Shell dashboard. To ensure your scanner has the latest available plugins, Tenable recommends manually updating your plugin set. Nessus users, including Tenable.io Nessus scanners, can use the following Nessus CLI command:
nessuscli fix --secure --delete feed_auto_last
For more information on using nessuscli, please refer to this article.
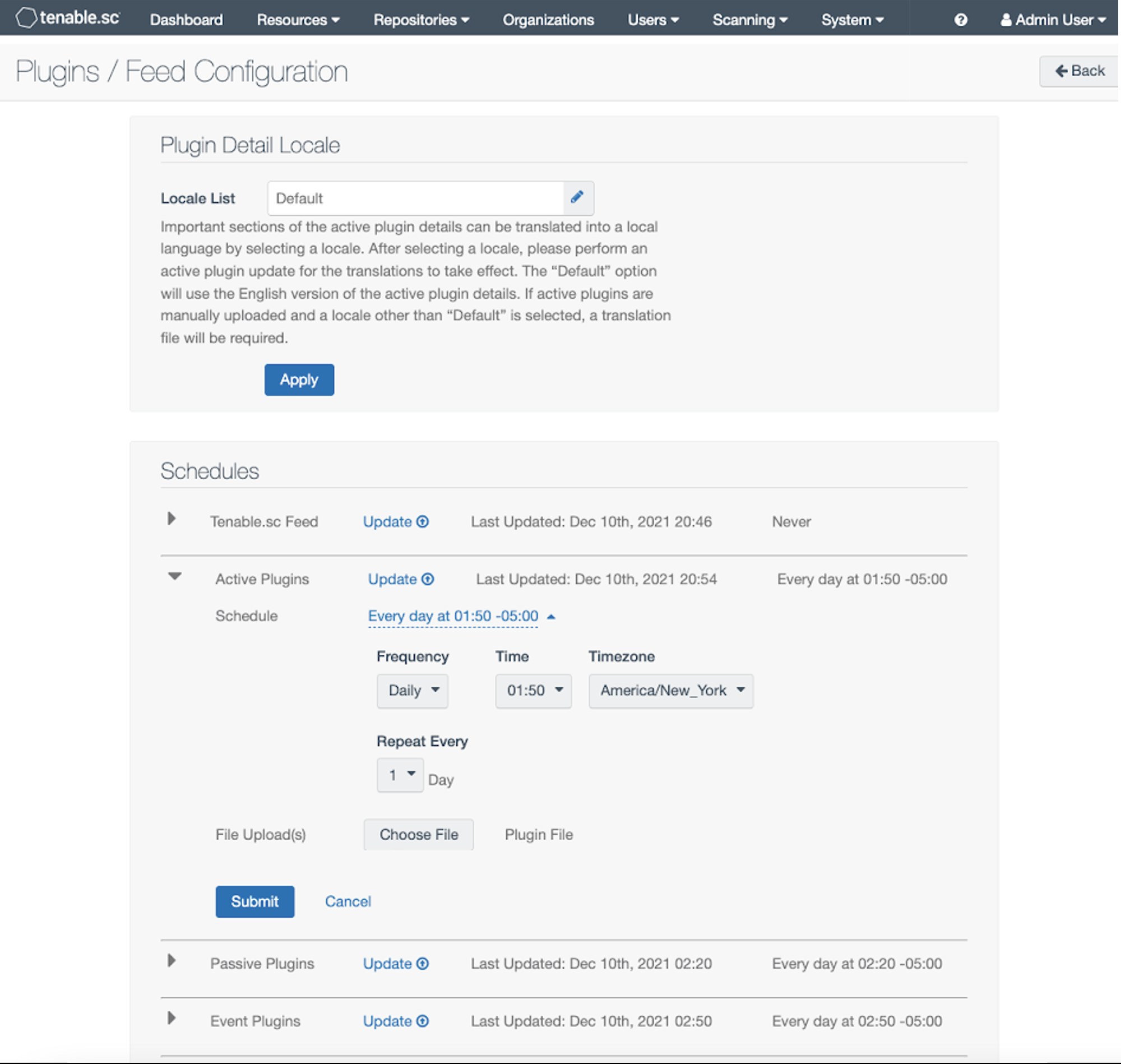
Tenable.sc users can manually update plugins using the [Update] links in the Plugins/Feed Configuration UI as shown in the following screenshot
Organizations that don’t currently have a Tenable product can sign up for a free trial of Nessus Professional to scan for this vulnerability.
Get more information
- Webinar: Vulnerability Alert - Responding to Log4Shell in Apache Log4j
- Apache Log4j2-3201: Limit the protocols jNDI can use and restrict LDAP
- Security Advisory: Apache Log4j2 remote code execution vulnerability (CVE-2021-44228)
- Log4Shell: RCE 0-day exploit found in log4j2, a popular Java logging package
- Apache Log4j 2 Release Page
- How Nessus Receives Plugins and Software Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management


