Risk-based vulnerability management: Understanding vulnerability risk with threat context and business impact
Your one-stop risk-based vulnerability management knowledge base
Risk-based vulnerability management (RBVM) is a process that reduces vulnerabilities across your attack surface by prioritizing remediation based on the risks they pose to your organization.
Unlike legacy vulnerability management, risk-based vulnerability management goes beyond just discovering vulnerabilities. It helps you understand vulnerability risks with threat context and insight into potential business impact.
Risk-based vulnerability management uses machine learning to correlate asset criticality, vulnerability severity and threat actor activity. It helps you cut through vulnerability overload so you can focus on the relatively few vulnerabilities that pose the most risk to your enterprise.
A risk-based approach to your vulnerability management program facilitates:
- Complete visibility into your attack surface, including modern asset types like cloud, operational technology (OT), IoT, serverless and containers
- Vulnerability prioritization, powered by machine learning, so you can determine which vulnerabilities attackers may be most likely to exploit in the near term
- Dynamic and continuous assessment of all of your assets and vulnerabilities, including asset criticality ratings
Get insight into high-risk vulnerabilities that pose the greatest risk to your organization
Here are few highlights of what you’ll discover in this risk-based vulnerability management knowledge base:
Learn how to prioritize vulnerabilities based on risk
Adopt a risk-based approach for your vulnerability remediation processes with five simple steps.
Learn moreDifferences between legacy vulnerability management and risk-based vulnerability management
Risk-based vulnerability management is a relatively new approach, but it represents best practices for vulnerability management.
Learn moreRisk-based vulnerability management in the cloud
Risk-based vulnerability management isn’t just a process for your on-premises assets. It’s also applicable to your cloud environments.
Learn moreRisk-based vulnerability management frequently asked questions
Have a question about risk-based vulnerability management? Here are answers to some frequently asked questions.
Learn moreTenable Connect community for risk-based vulnerability management
Looking for a place to connect with others interested in taking their vulnerability management programs to the next level? Join the Tenable Connect community and engage with other risk-focused security professionals.
Learn moreReduce the greatest amount of business risk with the least amount of effort
Get complete attack surface visibility and risk-based vulnerability prioritization with Tenable
- Discover and assess every asset across your complete attack surface
- Understand vulnerabilities in context of business risk
- Prioritize high-risk vulnerabilities that pose the most risk
- Communicate business risk to your executives and key stakeholders
From legacy vulnerability management to risk-based vulnerability management
Legacy vulnerability management solutions weren't designed to handle your modern attack surface and the increasing threats that come with it.
Your attack surface is no longer just traditional IT assets. It also includes mobile devices, web apps, cloud infrastructure, containers, Internet of Things (IoT) devices and operational technology (OT) assets.
In these modern networks, legacy vulnerability management tools can’t deliver complete and timely insights into all of the devices across your entire attack surface. That leaves you with blind spots and increases your exposure.
Instead, these legacy tools are limited to a theoretical view of the risk a vulnerability could potentially introduce, which can cause your security team to chase after the wrong issues while missing many of the most critical vulnerabilities that pose the greatest risk to your business.
What’s even more frustrating are the mountains of vulnerability data generally returned from legacy vulnerability management processes. How do you know which vulnerabilities to fix first? How do you know which weaknesses pose the greatest threats to your organization?
Risk-based vulnerability management eliminates guesswork.
By taking a risk-based approach to vulnerability management, your security team can focus on the vulnerabilities and assets that matter most and address your organization’s true business risk instead of wasting valuable time on vulnerabilities attackers may not likely exploit.
If you’re new to risk-based vulnerability management, check out this comparison guide. It breaks down the differences between legacy vulnerability management and risk-based vulnerability management with insight into how a risk-approach can make your vulnerability management program more efficient and effective.
3 things you need to know about prioritizing vulnerabilities
With the already unmanageable number of vulnerabilities continuing to increase for organizations of all sizes, how can you identify the biggest risks to your business so you know what to remediate first?
This white paper explores three critical steps you can adopt to build an effective vulnerability remediation program:
- First, look at all of the vulnerabilities that are currently actively exploited, which reflects real risk
- Next, use a risk-based vulnerability management solution with integrated threat intelligence to address weaknesses with known exploits in the wild
- Finally, remediate vulnerabilities attackers are most likely to exploit within the next 28 days
Based on Tenable research using more than 4.5 petabytes, plus 8 external data sources, Tenable Predictive Prioritization utilizes machine learning and predictive analytics to provide visibility into the likelihood an attacker may exploit a weakness.
In addition to these three steps, you’ll also learn about:
- The pitfalls and drawbacks of using CVSS to prioritize vulnerabilities
- Steps you can take to decrease the number of vulnerabilities that need your immediate attention
- Recommendations for issues like how to prioritize based on risk and which vulnerabilities to focus on first
How to prioritize cybersecurity risks
Legacy vulnerability management processes generally return far too many vulnerabilities rated high/critical for your team to mitigate every last one, no matter how much you want to, and no matter how many efficiencies and tools you adopt.
Even with mature vulnerability management programs, hidden threats lurk in blind spots within your attack surface, and it can be hard to seek out and assess all emerging risks that may affect your business.
Remediation is even more complicated when you add in the factor that some patches and fixes require entire system shut downs.
So how can you maximize efficiency for your security teams to help them make the biggest impact on risk with the least amount of effort?
A risk-based approach to your vulnerability management program will improve the way your organization handles vulnerability assessment and remediation so you always know which weaknesses should get your attention.
In this white paper, you’ll also learn about:
- How to evolve from a static, point-in-time vulnerability data view CVSS provides, to a dynamic view of vulnerability, threat and asset criticality data analyzed by predictive machine learning algorithms that focus on mitigating business risk
- How visibility into all of your IT assets across your attack surface is essential for vulnerability remediation
- How to shift your focus from how many vulnerabilities you have to which vulnerabilities pose the greatest risk and need priority remediation
Predictive prioritization: Data science to focus on the greatest risks to your organization
Organizations of all sizes are overwhelmed by the sheer number of vulnerabilities already in their networks—and that number is increasing rapidly as modern networks grow larger and more diverse.
This leads to an ever-expanding, dynamic attack surface and increasing vulnerabilities, which legacy vulnerability management solutions can’t handle.
Tenable’s Predictive Prioritization can help your team improve your cyber risk management processes by reducing the number of vulnerabilities that need immediate attention by 97%.
Predictive prioritization uses machine learning to identify the relatively small number of vulnerabilities that pose the greatest risk to your organization in the near future. It gives you ongoing, comprehensive insight into your ever-changing attack surface, including all known vulnerabilities related to all of your asset types.
In addition to taking a deep dive into predictive prioritization and how it works, you won’t want to miss learning more about:
- How predictive prioritization goes beyond Common Vulnerability Scoring System (CVSS) scores so you can focus on the 3% of vulnerabilities that matter most
- Insight into how predictive prioritization works, including guiding principles
- Why predictive prioritization is more accurate than other prioritization processes
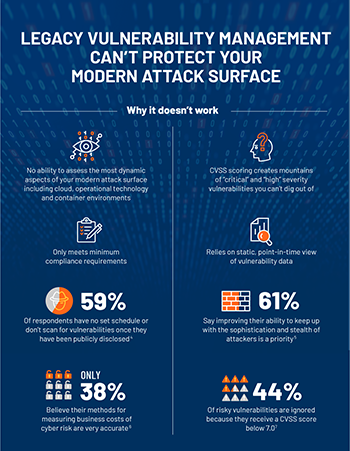
5 reasons why legacy vulnerability management fails
Today’s modern attack surface is complex. It has more asset types than ever before and an ever-growing number of vulnerabilities. In the past year alone, more than 17,000 new vulnerabilities were disclosed and many organizations reported they’ve experienced a damaging cyber attack within the past two years.
If you’re still using legacy vulnerability management practices, your organization may be at risk for an increasing number of attacks.
Why? Because legacy vulnerability management doesn’t give you the complete visibility you need for comprehensive insight into your attack surface, especially for your most critical assets.
Check out this infographic to learn more about:Top reasons legacy vulnerability management fails
- How risk-based vulnerability management is different than legacy vulnerability management
- How risk-based vulnerability management works
- Benefits of adopting risk-based vulnerability management practices
Tenable Connect community: Your go-to resource for risk-based vulnerability management
Looking for a place to connect with others interested in taking their vulnerability management programs to the next level with a risk-based approach? Join the Tenable Connect community and connect with other risk-based vulnerability management professionals. It’s a great place to ask questions, share ideas and give feedback on how Tenable can help you reach your risk-based vulnerability management goals.
Feeling overloaded by the number of vulnerabilities your organization faces daily?
There were 16,500 new vulnerabilities in 2018, but only 7% of these vulnerabilities had a public exploit available. Threat actors weaponize an even smaller subset. Predictive Prioritization, a groundbreaking process from Tenable, uses advanced data science techniques to help your teams focus on the relatively few vulnerabilities that matter most.
Read moreIf I scan on a particular subnet, can I get a Vulnerability Priority Rating (VPR) for those IP addresses scanned?
Yes. If you perform a scan of a set number of assets, you can then go into the results of that individual scan, click the “Vulnerabilities” tab and see results specifically for those assets. This includes the VPR for each vulnerability associated with those assets. (You can read more about VPR in our FAQ section below.)
See the answerIs there a way to accept a risk by host?
Yes. You can accept risk by plugin based on Repository, then by one of the following: asset group, IP, UUIDs (agent ID), or all available devices. To do this, simply click on the gear wheel for the plugin and make your selections as needed.
See the answerFrequently asked questions about risk-based vulnerability management
Are you new to risk-based vulnerability management? Do you have questions about how you can adopt a risk-based approach for your existing vulnerability management program, but are not sure where to start? This risk-based vulnerability management FAQ is a great resource:
What’s a security vulnerability?
What is risk-based vulnerability management?
How is risk-based vulnerability management different from legacy vulnerability management?
Risk-based vulnerability management is different from legacy vulnerability management in several ways.
First, legacy vulnerability management generally assesses only traditional on-premises IT assets such as desktop computers, services, and devices on your network. Because this approach ignores other parts of your attack surface, such as mobile devices, web apps, cloud environments, IoT, OT and containers, it creates blind spots that put your organization at risk. Risk-based vulnerability management allows you to assess traditional and modern assets across your entire attack surface and then combine this data with threat and exploit intelligence, as well as asset criticality, to predict each vulnerability’s impact on your organization.
Here are a few other ways the two disciplines are different:
Legacy vulnerability management
- Only meets minimum compliance requirements
- Provides static, point-in-time snapshots of vulnerability data
- Is reactive
Risk-based vulnerability management
- Uses best practices to reduce risk across your organization
- Facilitates continuous and dynamic visibility into your assets and vulnerabilities
- Is proactive and focused
What is active scanning?
What is a Common Vulnerability Scoring System (CVSS) score?
The Common Vulnerability Scoring System (CVSS) takes a theoretical view of the risk a vulnerability could potentially introduce. CVSS starts with 0 as the lowest priority and goes up to 10 — the most critical.
Unfortunately, CVSS assesses about 60% of all vulnerabilities with a high or critical CVSS score, even though they may pose little risk to your organization. CVSS is unaware of real-world risk and doesn’t take into account the criticality of each asset within your environment. These are critical pieces of information you need to prioritize remediation effectively.
Tenable supplements CVSS with Predictive Prioritization, an Asset Criticality Rating (ACR) and a Vulnerability Priority Rating (VPR), which are defined below. VPR gives you better insight into risks by also considering threat and attack scope, vulnerability impact and threat score. VPR performs in-depth analyses to determine the top 3% of vulnerabilities that should be remediated first.
What is a Vulnerability Priority Rating (VPR)?
A Vulnerability Priority Rating (VPR) is the output of Tenable’s Predictive Prioritization process.
VPR assesses more than 150 data points, including Tenable and third-party vulnerability and threat data. It then uses a machine-learning algorithm to analyze all the vulnerabilities in the National Vulnerability Database (plus others vendors have recently announced but have not yet been placed in the NVD) to predict which vulnerabilities have the greatest risk of being exploited in the near-future.
VPRs, rated from 0 to 10, help you prioritize remediation. VPRs at 10 indicate the most critical threats for priority remediation.
What is Predictive Prioritization?
Predictive prioritization uses a risk-based approach to vulnerability management to determine the probability an attacker may leverage a weakness against your organization.
Predictive prioritization includes asset and threat intelligence and adds machine learning to prioritize vulnerabilities based on the likelihood of an attack. Predictive prioritization gives each vulnerability a score called a Vulnerability Priority Rating (VPR). VPRs are from 0 to 10, with 10 the highest possible threat, so you can prioritize which weaknesses should get priority attention.
What is an Asset Criticality Rating (ACR)?
What is an Asset Exposure Score (AES)?
What is a Cyber Exposure Score?
A Cyber Exposure Score (CES) represents your organization’s cyber risk. CES combines your Vulnerability Priority Rating (VPR) with your Asset Criticality Rating (ACR).
CES ranges between 0 (minimal risk) and 1,000 (highest risk) and represents the average of all Asset Exposure Scores (AESs) in your organization.
CES helps prioritize remediation by examining asset criticality and your business goals, the severity of each potential threat within your network, how likely an attacker may exploit the threat in the next 28 days, and the context of the threat related to how prevalent the exploitation risk is in the real world.
Your CES also helps benchmark your vulnerability management and vulnerability assessment success internally and against peer organizations.
What is a Proof-of-Concept (POC) exploit?
What is PCI ASV?
Risk-based vulnerability management in the cloud
Risk-based vulnerability management isn’t just a process for on-premises assets. It’s also applicable to all your cloud environments.
A risk-based approach to vulnerability management can help you discover, assess, prioritize, remediate, and measure all of your cloud assets to build a mature vulnerability management program.
Here’s how it works:
Discover cloud assets in a dynamic environment
Continuous visibility into your cloud environments is the foundation of risk-based vulnerability management. It ensures you’re not blind to short-lived assets in production and development.
Run assessments built specifically for the cloud
Using security best practices and environment hardening templates from the Center for Internet Security (CIS) and cloud service providers like Amazon Web Services (AWS) and Microsoft Azure, you can audit your cloud environment, find vulnerabilities within your cloud stack and adopt a variety of scanning and monitoring methods to meet your organization’s cloud needs.
Prioritize exposure context
Risk-based vulnerability management helps you understand the context of exposures within your cloud environment so you can prioritize which to fix first. Risk-based vulnerability management helps you allocate your remediation resources to threats that pose the greatest risk to your organization, and you can share that information easily with your DevOps team and automatically send information to your SIEM for response.
Remediate vulnerabilities
When it comes to vulnerabilities, finding them in your live environment is only half the battle. Risk-based vulnerability management helps you remediate vulnerabilities before production by integrating directly into your CI/CD pipeline and image creation processes. With Tenable, you can also integrate bug-tracking and remediation tools using powerful APIs so you know which vulnerabilities your team fixes and when remediation is complete.
Measure and benchmark for better decision-making
Risk-based vulnerability management can help you quickly understand your organization’s Cyber Exposure, even for dynamic assets in the cloud. By including your cloud environments in your CES score, you can compare how well your cybersecurity program works across internal departments, as well as against industry peers.
Want to learn more about risk-based vulnerability management for cloud environments? Check out our Cloud Risk-based Vulnerability Management Solutions page.
Risk-based vulnerability management process
Legacy vulnerability management doesn't give you a unified view of your entire attack surface, which makes it difficult to know which vulnerabilities to fix first. Risk-based vulnerability management helps you see which vulnerabilities actually pose the greatest risk to your organization and puts them into context so you can prioritize remediation. Moving from a compliance-driven approach of legacy vulnerability management to a risk-based approach, your organization can evolve from an infrastructure and IT focus to addressing your entire attack surface. Here’s a quick look into the risk-based vulnerability management process related to the Cyber Exposure Lifecycle:
-
Discover
Identify and map all of your assets across your entire attack surface so you have visibility into all of your computing environments.
-
Assess
Understand the state of all of your assets across all of your environments including vulnerabilities, misconfigurations and other security health issues.
-
Prioritize
Understand the context of your exposures so you can prioritize remediation based on how critical each asset is to your organization, its threat context and vulnerability severity.
-
Remediate
Prioritize which vulnerabilities to remediate first and apply the appropriate remediation or mitigation technique.
-
Measure
Understand your Cyber Exposure so you can calculate, communicate and compare cyber risks internally and against peer organizations to make better security and business decisions.
Risk-based vulnerability management best practices
While risk-based vulnerability management is a relatively new approach to vulnerability management, you can take steps toward a risk-driven program for your organization by implementing these best-practice recommendations:
-
Data fidelity and your attack surface
An effective risk-based vulnerability management program should continually gather and analyze data from across your entire attack surface, including on-premises infrastructure, endpoints, cloud infrastructure, web applications, containers, mobile devices, IoT and OT.
-
Process automation
Streamline your risk-based vulnerability management processes including configuration management, change management, asset management and incident response.
-
Customized analytics
Your risk-based vulnerability management solution should provide analytics and customizable reports for your organization’s needs. You can use the reports to provide each key stakeholder with role-specific analytics. Topline analytics also provide insight into how well your teams collect asset and assessment information, including success metrics to remediate prioritized vulnerabilities.
With risk-based vulnerability management best practices, your security team can build a successful program that delivers high-fidelity data and automated processes to effectively manage your Cyber Exposure across your entire attack surface.
Discover. Assess. Prioritize.
Stop guessing about which vulnerabilities to fix first.
Reduce the number of vulnerabilities that need your immediate attention by 97% and focus on what matters most with Tenable One.
Risk-based vulnerability management blog bytes

5 tips for prioritizing vulnerabilities based on risk
Pinpointing vulnerabilities that pose the greatest risks to your business is challenging, but these five tips can improve the way you handle vulnerability remediation processes.

Predictive Prioritization: How to focus on vulnerabilities that matter most
Enterprises find an average of 870 vulnerabilities per day across 960 IT assets. There isn’t enough time or resources for your team to fix them all, so it’s important to know where to prioritize based on risk. This whitepaper explores how Predictive Prioritization ensures you’re prioritizing the right vulnerabilities for your team—while reducing everyone’s workload.

Should you still prioritize exploit kit vulnerabilities?
The objective of strategic vulnerability remediation prioritization is to identify vulnerabilities that pose the greatest risk to your organization. Many organizations rely on the Common Vulnerability Scoring System (CVSS) to prioritize, but given the time and resources available, CVSS often yields far too many “critical” vulnerabilities for most to realistically remediate.
Vulnerability management on-demand
Transitioning to risk-based vulnerability management
Today, your modern attack surface constantly expands with diverse asset types, from traditional IT to OT and the cloud. If you're still using traditional vulnerability management practices for all of these asset types, you're likely overlooking critical exposures with blind spots that increase your cyber risk.
On top of that, most vulnerability management tools mark far too many vulnerabilities critical or high, most of which attackers won't ever actively exploit or they're not relevant to your unique attack surface.
In this on-demand webinar, learn more about making the shift to risk-based vulnerability management and:
- Best practices to prioritize, automate, report and manage your vulnerability and asset data
- How to automate asset and vulnerability tracking
- Conduct compliance audits using easy-to-understand dashboards
Gain insight into your organization’s overall cyber risk with Tenable One
Tenable One can help you visualize, analyze and measure your cyber risk across your entire attack surface. It transforms vulnerability data into meaningful insights so you can manage exposures and focus on the top 3% of vulnerabilities that pose the greatest risk to your organization.
Risk-based scoring and prioritization
Combine vulnerability data with asset criticality and threat intelligence so your security team can focus on vulnerabilities that matter most.
Total attack surface visibility
With complete visualizations of your entire attack surface, your team can quickly measure and communicate cyber risk.
Exposure analytics and benchmarking
Powered by the industry’s richest set of vulnerability intelligence, you can quantify your cyber risk and benchmark internally to determine your program’s effectiveness.
Shift to a risk-based vulnerability management strategy with Tenable One
Visualize and measure your organization’s exposure, track risk reduction over time and benchmark against your peers with Tenable One.
- Tenable Cloud Security
- Tenable Vulnerability Management