The Challenges of Securing Industrial Control Systems from Cyberattacks

There are many controller vulnerabilities attackers can exploit to disrupt operations and cause damage. Yet, most organizations don’t patch controllers because many ICS engineers prioritize network stability at all costs.
Cyberthreats are forcing organizations in the industrial sector to take a long, hard look at how they protect industrial control systems (ICS) and, specifically, industrial controllers.
The increase in the number of cyber incidents on ICS networks is a reality the industry can no longer ignore. Yet, ICS networks pose unique challenges for security professionals, primarily because they are not like traditional IT networks. To protect them, you need to understand how they operate, the different technologies they employ and their discrete functions.
Air gaps can no longer protect industrial networks from attacks
Until recently, industrial networks separated themselves from the rest of the world with air gapping.
In theory, an air gap is a great security measure. You disconnect your industrial network from your business network and from the internet to create an impassable barrier that prevents attackers from reaching it.
However, air gapping is no longer a feasible solution for today’s connected and converged world of IT and operational technology (OT).
Trends like IIoT (Industrial Internet of Things) and Industry 4.0 drive organizations to improve existing processes and augment operational systems to facilitate more connections between physical processes and the internet.
This connectivity exposes previously isolated operational environments to cyberthreats.
Vulnerabilities in industrial processes increase cyber risk
A range of vulnerabilities in software and hardware, as well as weaknesses inherited from the legacy design of ICS networks, exposes industrial processes to cyber risks.
Industrial controllers — such as programmable logic controllers (PLCs), remote terminal units (RTUs) and distributed control system (DCS) controllers — are specialized computers that manage the lifecycle of industrial equipment and processes.
Most of these controllers do not require authentication from those attempting to access them and alter their state. Most do not support encrypted communication. This means anyone with network access — a hacker, a malicious insider or even a careless employee — has unfettered access to the industrial process. That’s a threat to business.
There are many controller vulnerabilities for attackers to exploit in order to disrupt operations and cause damage. Yet, most organizations don’t patch controllers because many ICS engineers prioritize network stability at all costs. It’s difficult to patch industrial controllers because doing so can cause disruptions or downtime and can lead to reliability issues and other operational problems.
Unpatched Windows-based workstations that still run legacy operating systems such as Windows NT and XP are also common in operational environments. Many remain unpatched because of the same concerns regarding operational stability and reliability. These unpatched systems further weaken the risk posture of ICS networks.
Lack of visibility and control in industrial control system networks
Since ICS networks were designed before cyberthreats existed, security wasn’t a factor in implementation. Today, these networks require, but still lack, the visibility and security controls common in corporate IT networks. In many ICS environments, automated asset management or configuration controls are not leveraged.
Without fully understanding which assets are in your network, which firmware they run, what code and logic they execute, their configuration and which of them are vulnerable, how can you take measures to properly protect them?
Don’t forget that these environments use specialized operational technologies (OT) from vendors such as GE, Siemens, Schneider Electric, Rockwell and others. They operate differently than IT technologies. They use different hardware, different software and different network protocols. As a result, IT security solutions are not a good fit for these environments.
Control-layer protocols are difficult to secure
When looking to secure ICS networks, one of the biggest technical challenges we face is that ICS networks use different communication protocols.
Applications for human machine interface (HMI), supervisory control and data acquisition (SCADA) and distributed control systems (DCS) all use standard protocols, like Modbus and DNP3, to communicate physical measurements and process parameters (i.e. current temperature, current pressure, valve status, etc.).
Meanwhile, control-layer protocols — which configure automation controllers, update their logic, make code changes or download firmware — are comprised of proprietary and vendor-specific protocols.
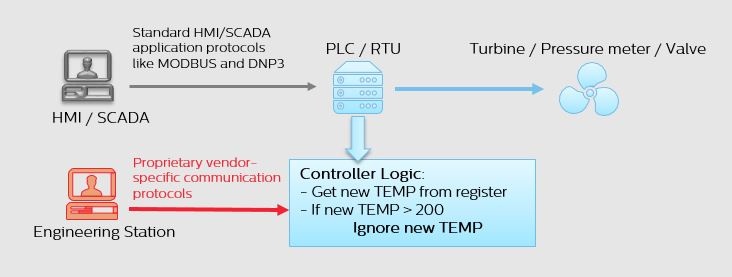
Each OT vendor uses its own proprietary implementation of the IEC-61131 standard for programmable logic controllers. Since these implementations are rarely documented, it is difficult to monitor these critical activities.
Since the goals of most ICS cyberattacks are to cause operational disruptions or physical damage, the adversary may try to change the way the process executes.
While a predefined set of process parameters can be changed through HMI/SCADA applications, the logic maintained on the controller defines the process flow and its restrictions. Therefore, changing the controller logic is the easiest and most successful way to cause such changes.
Contrary to popular belief, this is not difficult. Once inside the network, an attacker can easily download control logic to an industrial controller or change its configuration.
Since attackers execute these actions using proprietary vendor-specific protocols, there is no standard way to monitor control-layer activities. As a result, changes an attacker makes (or even those that occur due to human error) can go unnoticed until damage occurs.
How to overcome the challenges of unsecured OT networks
Due to OT network design, and the lack of basic security controls like authentication and encryption, most ICS attacks do not need to exploit software vulnerabilities. Once an attacker reaches the OT network, they can use a compromised machine to launch an attack on industrial processes.
The current lack of visibility and security controls in ICS networks places industrial processes and critical infrastructures at risk. To prevent unauthorized process changes and protect ICS from external attacks, you should use specialized monitoring and control technologies.
Learn more
Download the ICS Cybersecurity Considerations Checklist to learn more about criteria to help you select an industrial cybersecurity solution to secure and control your critical networks.
- SCADA


