Cybersecurity Snapshot: Expert Advice for Securing Critical Infrastructure’s OT and Industrial Control Systems, IoT Devices and Network Infrastructure

Destructive cyber attacks against critical infrastructure have unfortunately become increasingly frequent. Just last week, multinational government agencies blared the alarm about a global cyber espionage campaign targeting critical infrastructure networks. With this type of cyber threat in the spotlight, we’re rounding up recent cyber advice for securing critical infrastructure.
In case you missed it, here are six things to know right now about protecting everything from operational technology (OT) and industrial control systems (ICS) to the countless IoT devices that power our world.
1- Global alert: China-backed APTs hit critical infrastructure in cyber espionage campaign
Let’s start with the most recent news. Last week, multiple U.S. and international government agencies warned critical infrastructure organizations about ongoing and global cyber attacks from advanced persistent threat (APT) attackers backed by the Chinese government (PRC).
The joint advisory – “Countering Chinese State-Sponsored Actors Compromise of Networks Worldwide to Feed Global Espionage System” – urged security teams to immediately take basic but essential steps, including patching known exploited vulnerabilities; adopting centralized logging; and securing network edge devices.

The prime target? The network infrastructure of large telecom providers, although other critical infrastructure sectors, such as the military and transportation, have also been hit.
The threat actors, active since 2021 and identified over the years as Salt Typhoon, Operator Panda, RedMike, UNC5807 and GhostEmperor, are walking through unlocked doors. For initial entry, they look for low-hanging fruit, such as vulnerabilities that have been disclosed and for which patches exist, including these:
Once inside, the attackers try to avoid detection so that they can stay hidden for years to gather intelligence. Their playbook includes:
- Living off the land: They use legitimate, built-in network administration tools and protocols to blend in with normal network traffic and move laterally.
- Credential theft: They are adept at stealing valid credentials to maintain access and escalate privileges.
- Data staging: Attackers often use internal FTP servers as staging areas to aggregate data before exfiltration, a key indicator of compromise.
Here’s a small sampling of the mitigation recommendations:
- Prioritize monitoring firmware and software integrity by performing hash verifications against vendor databases.
- Review network device logs for unusual activity, such as cleared logs, disabled log forwarding, or configuration changes from unexpected locations.
- Implement robust access controls and phishing-resistant multi-factor authentication.
- Prioritize patching publicly known vulnerabilities that represent the highest risk, and specifically the CVEs the advisory singles out.
To get a deep dive into this threat, read this blog from Tenable's Research Special Operations team: "Frequently Asked Questions About Chinese State-Sponsored Actors Compromising Global Networks."
Meanwhile, the FBI last month alerted that a Russian government unit has been hijacking network devices to surveil industrial networks. In the alert “Russian Government Cyber Actors Targeting Networking Devices, Critical Infrastructure,” the FBI warned that the hackers are targeting industrial control systems (ICS) by breaching networks via the years-old bug CVE-2018-0171 in the Cisco Smart Install (SMI) software.
For more information about Salt Typhoon and related China-backed APT attacks against critical infrastructure, check out these Tenable blogs:
- “Salt Typhoon: An Analysis of Vulnerabilities Exploited by this State-Sponsored Actor”
- “Volt Typhoon: U.S. Critical Infrastructure Targeted by State-Sponsored Actors”
- “Telecoms May Face Tougher Regulations After Salt Typhoon Hacks”
- “New CISA Hardening Guidance Provides Valuable Insights for Network Security Engineers”
- “How to protect comms infrastructure from China-backed Salt Typhoon hackers”
2 - CISA to OT operators: If you can’t see it, you can’t secure it
Last month, the Cybersecurity and Infrastructure Security Agency (CISA) tackled the critical issue of visibility of OT wares with a new playbook for how to structure, manage and update an OT asset inventory.
The new guidance – titled “Foundations for OT Cybersecurity: Asset Inventory Guidance for Owners and Operators” – delivers a clear message: an OT asset inventory is the bedrock of any OT security architecture. Without it, OT security is fundamentally impaired.
“An OT asset inventory – an organized, regularly updated list of an organization’s OT systems, hardware, and software – is foundational to designing a modern defensible architecture,” the document reads.
But OT operators shouldn’t stop there.
They also must classify their assets. OT environments are a diverse mix of legacy systems, sensors and specialized devices – along with their usual variety of proprietary communication protocols. CISA recommends creating a taxonomy to understand each component's role.
Classifying OT assets by function and importance helps to:
- Prioritize what matters most.
- Sharpen risk identification and vulnerability management.
- Boost incident response.
Steps To Build An OT Asset Taxonomy

(Source: CISA)
The document, which CISA created in collaboration with multiple U.S. and international government agencies, aims to help critical infrastructure organizations shift from a reactive to a proactive security posture via full asset visibility and thus attain a more resilient and secure OT environment.
For more information about OT security, check out these Tenable resources:
- “Mind the Gap: A Roadmap to IT/OT Alignment” (white paper)
- “Unlock Advanced IoT Visibility in your OT Environment Security” (on-demand webinar)
- “Blackbox to blueprint: The security leader’s guidebook to managing OT and IT risk” (white paper)
- “Fortifying Your OT Environment: Vulnerability and Risk Mitigation Strategies” (on-demand webinar)
- “Identity Security Is the Missing Link To Combatting Advanced OT Threats” (blog)
- “Operational Technology (OT) Security: How to Reduce Cyber Risk When IT and OT Converge” (resource page)
3 - Secure the small stuff: New cryptographic algos to protect IoT devices
From medical implants to industrial sensors, tiny Internet-of-things (IoT) devices are everywhere in critical infrastructure. The problem? Most of them don't have the processing muscle for heavy-duty encryption.
To fix this, the National Institute of Standards and Technology (NIST) just finalized a new standard for lightweight cryptography. It’s built for the billions of IoT devices with limited computational resources.
“We encourage the use of this new lightweight cryptography standard wherever resource constraints have hindered the adoption of cryptography,” NIST computer scientist Kerry McKay, who co-led the project, said in a statement.

(Credit: Image generated by Tenable using Google Gemini)
Detailed in NIST Special Publication 800-232, the standard is built around the Ascon family of cryptographic algorithms and includes four specific algorithms designed for different security needs.
- ASCON-128 AEAD: Encrypts data and proves it hasn't been tampered with.
- ASCON-Hash 256: Creates a digital fingerprint to detect alterations.
- ASCON-XOF 128 and ASCON-CXOF 128: Allow developers to fine-tune security to match devices’ capabilities.
This new standard is designed for straightforward implementation and offers better protection against "side-channel attacks," where adversaries analyze a device's power consumption or timing to glean information.
For more information about IoT security:
- “How to Remediate Risk to Critical OT/IoT Systems without Disrupting Operations” (Tenable)
- “How to Effectively Communicate OT/IoT Risk Across the Enterprise” (Tenable)
- “How to Unlock Advanced IoT Visibility for Cyber-Physical Systems” (Tenable)
- “Disaster Awaits if We Don’t Secure IoT Now” (IEEE)
- “Top 15 IoT security threats and risks to prioritize” (TechTarget)
4 - Buy smart: How to choose cyber secure OT products
Of course, the first step in preventing OT breaches is selecting products that were designed and built securely.
In January, CISA published a guide to help organizations choose OT products with cybersecurity baked in from the start.
Titled “Secure by Demand: Priority Considerations for Operational Technology Owners and Operators when Selecting Digital Products,” the publication highlights 12 cybersecurity elements that OT products should have, including:
- Strong authentication methods, such as phishing-resistant MFA
- Timely, free and easy-to-install security patches.
- Detailed logging in open-standard formats.
- Protection for data both at rest and in transit.
According to CISA, many OT products aren’t designed and developed securely, so they ship with issues such as weak authentication, known vulnerabilities and insecure default settings.
In fact, the agency says it’s common for hackers to specifically target OT products they know are insecure, instead of going after specific organizations.
Back in September 2024, CISA sounded the alarm on critical infrastructure organizations’ susceptibility to common, well-known attack methods in its “CISA Analysis: Fiscal Year 2023 Risk and Vulnerability Assessments” report.
The report’s findings are based on risk and vulnerability assessments (RVAs) of the security of 143 critical infrastructure organizations that CISA and the U.S. Coast Guard conducted in 2023.
Specifically, CISA and USCG assessors had the most success gaining initial access, attaining network permanence, evading defenses and moving laterally by using valid accounts, phishing schemes and default credentials — all simple attack methods.
For example, the use of valid accounts, which are legitimate accounts whose login credentials have been compromised, was the most successful attack technique for achieving:
- Initial access (41.3%)
- Persistence (42.2%)
- Privilege escalation (44.7%)
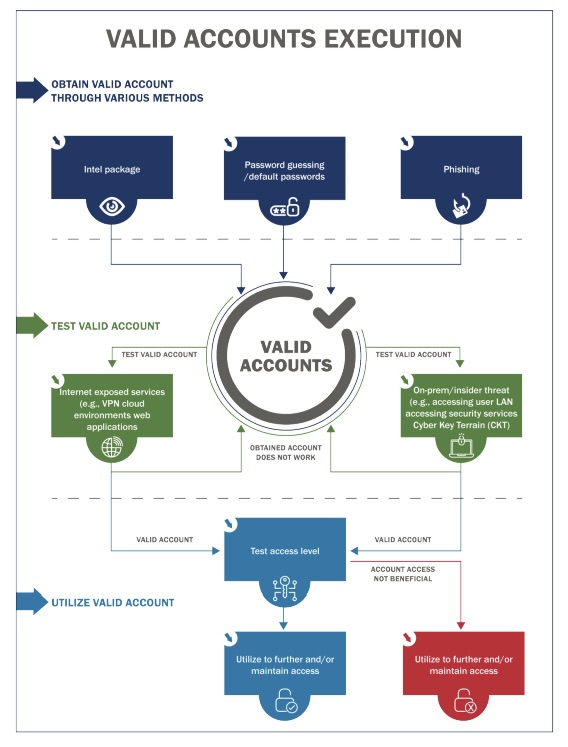
(Source: “CISA Analysis: Fiscal Year 2023 Risk and Vulnerability Assessments” report, September 2024)
The report offers troves of recommendations to critical infrastructure organizations, including:
- Adopt a secure password policy that requires phishing-resistant MFA for remote access; strong passwords; unique credentials, and more.
- Maintain a comprehensive asset inventory, and keep software updated and patched.
- Segment networks and block outbound connections from internet-facing servers to prevent lateral movement and privilege escalation.
For more information about protecting critical infrastructure environments and about operational technology (OT) security, check out these Tenable resources:
- “Critical Infrastructure Cybersecurity: Disrupt OT Attack Vectors in the New Era of Distrust” (white paper)
- “How To Secure All of Your Assets - IT, OT and IoT - With an Exposure Management Platform” (blog)
- “Enhancing Critical Infrastructure Cybersecurity for Water Utilities” (infographic)
- “Adhering to the NIST Framework with Tenable OT Security” (data sheet)
- “Blackbox to blueprint: The security leader’s guidebook to managing OT and IT risk” (white paper)
5 - Trust no one: Bringing zero trust to your OT environment
As OT computing environments become more digitized, converged with IT systems and cloud-based, critical infrastructure organizations should beef up their cybersecurity by adopting zero trust principles.
That’s the key message the Cloud Security Alliance delivered in November via its “Zero Trust Guidance for Critical Infrastructure” white paper, which focuses on applying zero trust methods to OT and ICS systems.
While OT/ICS environments were historically air gapped, that’s rarely the case anymore. “Modern systems are often interconnected via embedded wireless access, cloud and other internet-connected services, and software-as-a-service (SaaS) applications,” reads the 64-page white paper.
The CSA hopes the document will help cybersecurity teams and OT/ICS operators enhance the way they communicate and collaborate.

Among the topics covered are:
- Critical infrastructure’s unique threat vectors
- The convergence of IT/OT with digital transformation
- Architecture and technology differences between OT and IT
The guide also outlines this five-step process for implementing zero trust in OT/ICS environments:
- Define the surface to be protected.
- Map operational flows.
- Build a zero trust architecture.
- Draft a zero trust policy.
- Monitor and maintain the environment.
To get more details, read:
- The white paper’s announcement “New Paper from Cloud Security Alliance Examines Considerations and Application of Zero Trust Principles for Critical Infrastructure”
- The full white paper “Zero Trust Guidance for Critical Infrastructure”
- A complementary slide presentation
For more information about OT systems cybersecurity, check out these Tenable resources:
- “What is operational technology (OT)?” (guide)
- “Discover, Measure, and Minimize the Risk Posed by Your Interconnected IT/OT/IoT Environments” (on-demand webinar)
- “How To Secure All of Your Assets - IT, OT and IoT - With an Exposure Management Platform” (blog)
- “From Compliance Burden to Security Advantage: A Practical Approach for OT/IT Security” (on-demand webinar)
- “Tenable Cloud Risk Report 2024” (white paper)
- “Managing OT and IT Risk: What Cybersecurity Leaders Need to Know” (blog)
6 - SANS publishes ransomware response framework for ICS/OT environs
What's your plan when ransomware locks up your OT and industrial control systems? If you don't have one, the SANS Institute is here to help.
Its new framework, “A Simple Framework for OT Ransomware Preparation” provides a hands-on guide for building a response playbook. The key message? Preparation is everything.
With the document, published in April, SANS aims to outline an actionable, hands-on approach for critical infrastructure organizations seeking to build or fine-tune ransomware response playbooks.
“In the OT world, a lack of preparation can have real-world consequences,” reads a SANS blog titled “Building a Better OT Ransomware Response Plan: A Simple Framework for ICS Environments.”
At a high level, SANS recommendations for critical infrastructure organizations with OT / ICS environments include:
- Before drafting the playbook, you need to collect foundational data about your environment, such as its architecture, asset inventory, key staff and security controls.
- It’s also key to proactively foster collaboration between the IT, OT and cybersecurity teams.
- The ransomware-preparedness playbook should cover five key areas:
- Preparation
- Identification
- Containment
- Eradication
- Recovery
“By focusing on the unique challenges of OT networks, such as their architectural immaturity and the criticality of safe operations, the framework provides actionable guidance to enhance incident response capabilities,” the document reads.
- Cybersecurity Snapshot
- Federal
- Government
- Internet of Things
- OT Security
- SCADA
