Tenable
OT Security
The unified security solution for converged OT/IT environments
Safeguard critical systems without disrupting operations.
Request a demo
Take control of your assets
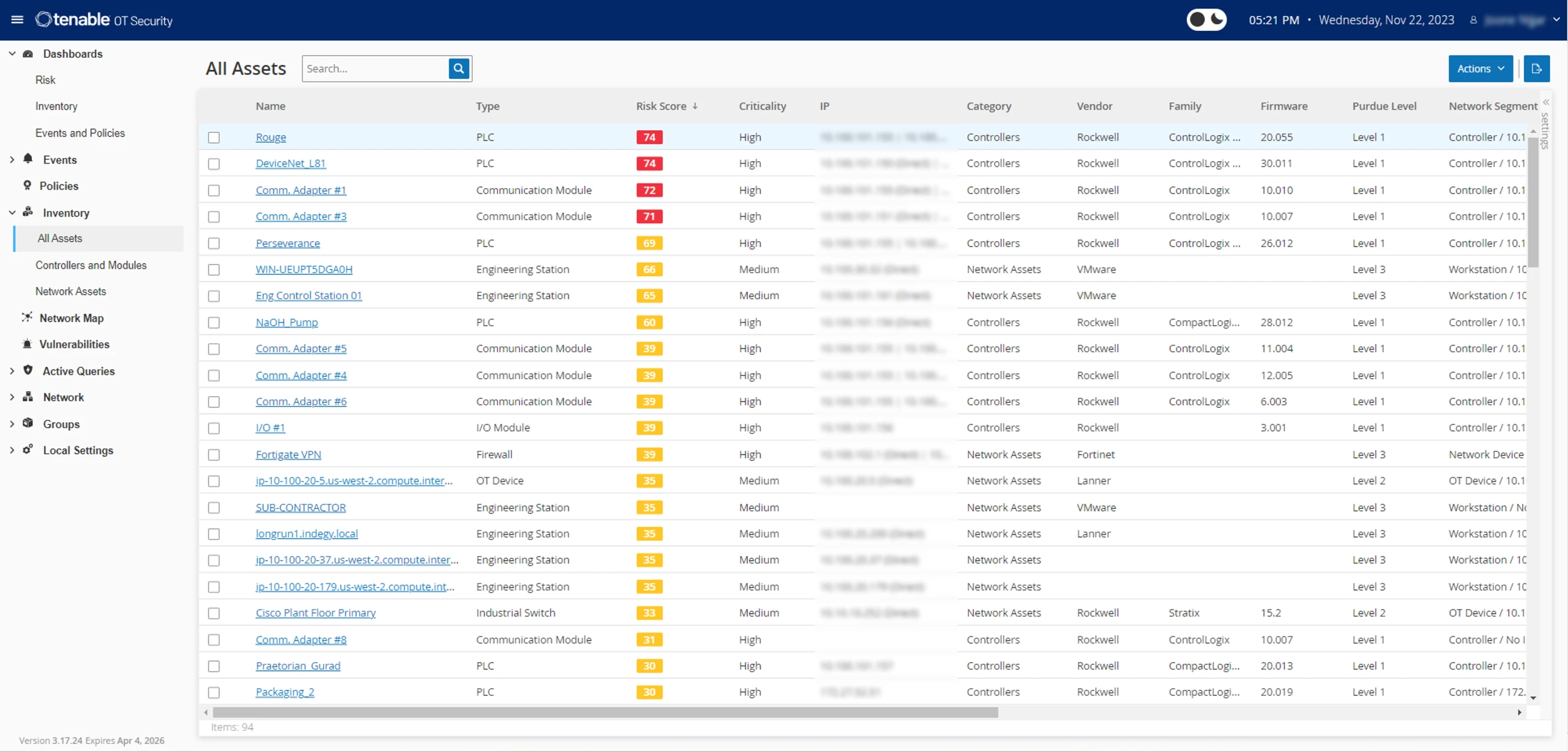
Know every OT/IT asset
Unify the visibility of every asset in your converged environment from a single interface.
Expose your lethal gaps
Proactively identify weak points in your OT environment.
Close priority exposures
Eradicate your high risk exposures before they’re exploited.
Unify OT/IT visibility, insight and control
Comprehensive asset visibility
Automate asset discovery and create visual asset maps for a unified view of network assets, including workstations, servers, industrial controllers and IoT devices. Use connector engines to specifically target applications that manage IoT devices and relationships for a complete inventory. Manage your assets by tracking their firmware and OS versions, internal configuration, applications and users, serial numbers and backplane configuration for both OT and IT-based equipment.
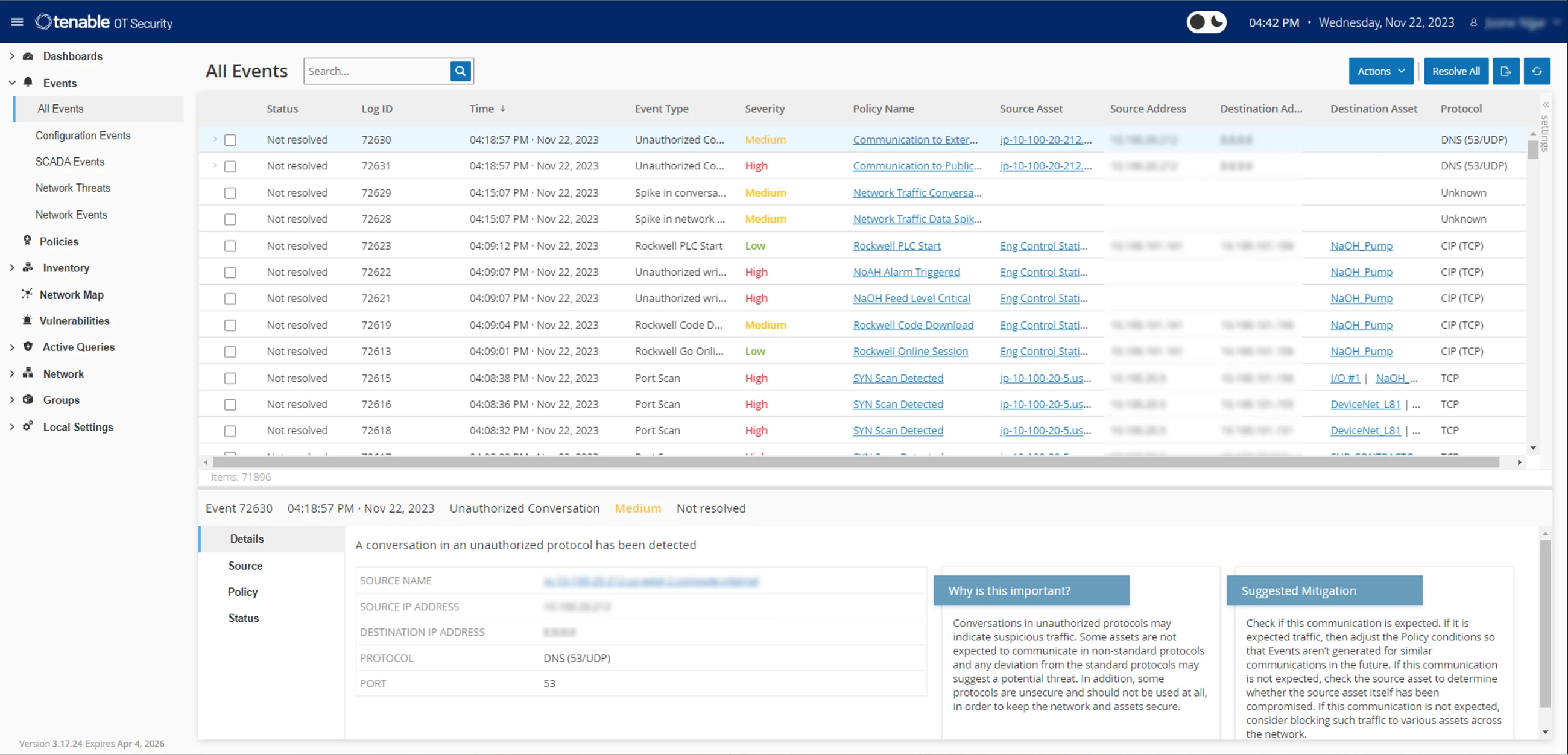
Advanced threat and anomaly detection
Leverage an advanced multi-detection engine to identify network anomalies, enforce security policies and track local changes on devices with high-risk events — all with granular precision. With device-based threat detection, identify issues on dormant devices to detect and mitigate risky events in OT/IT environments. Customize and fine-tune detection methodologies to fit the specific needs of your environment. Enhance threat response with context-rich alerts and a comprehensive audit trail for incident response and forensic investigation.
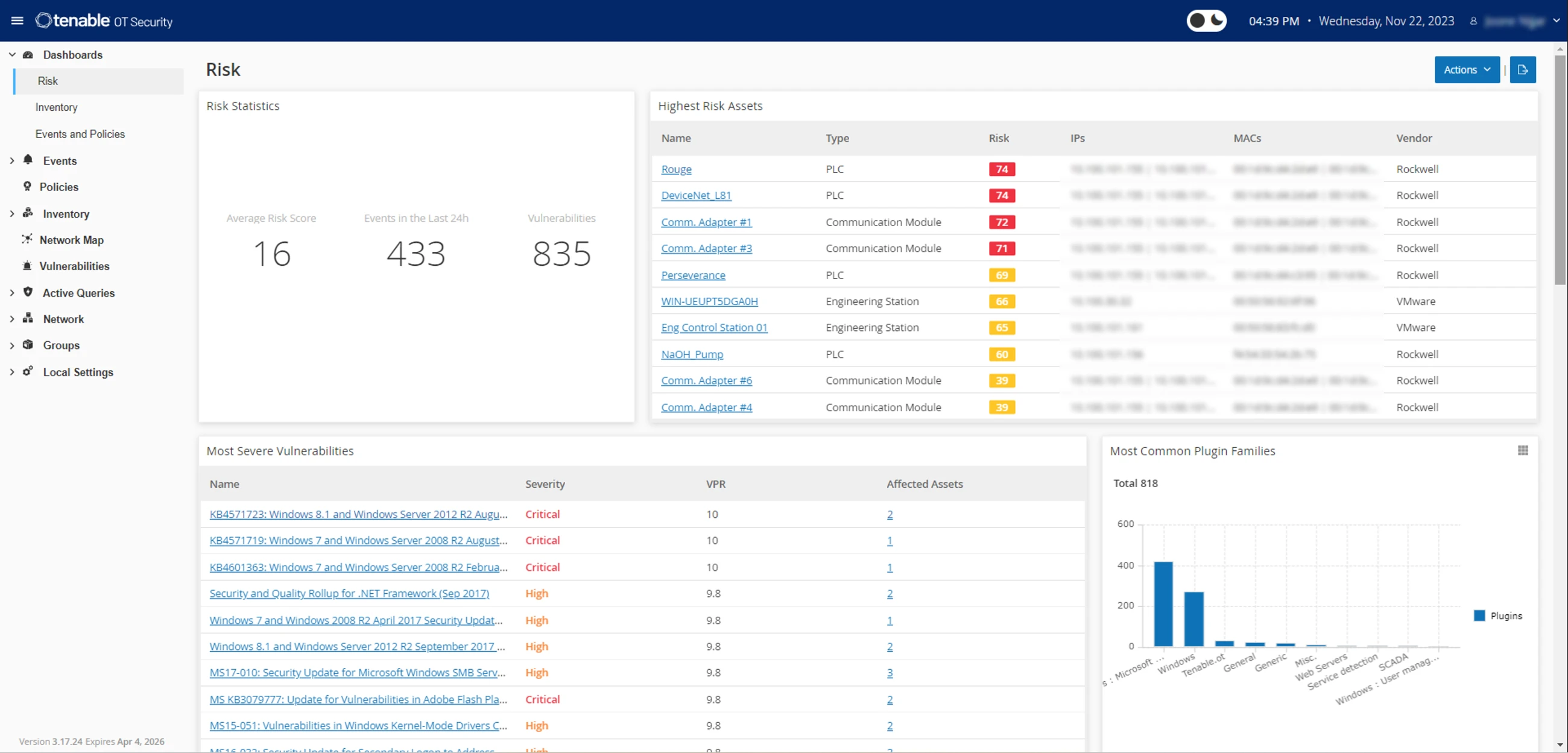
Risk-based OT/IT vulnerability management
Prioritize remediation efforts using Tenable’s Vulnerability Priority Rating (VPR) scoring model to assess vulnerabilities based on context and potential impact. Evaluate each asset with comprehensive data, including firmware versions, proprietary research and insights into asset relationships, exposures, entitlements and attack paths. Empower security teams and key stakeholders with actionable intelligence to make informed decisions and expedite mitigation measures.
Automated asset management
Simplify asset management with enhanced visibility and contextualized insights. Quickly identify assets and their critical exposures using Tenable’s patented hybrid discovery approach, which uses natural language queries to avoid disrupting critical operations. Reveal intricate relationships between physically connected and communicating devices with detailed asset mapping to build robust defense strategies.
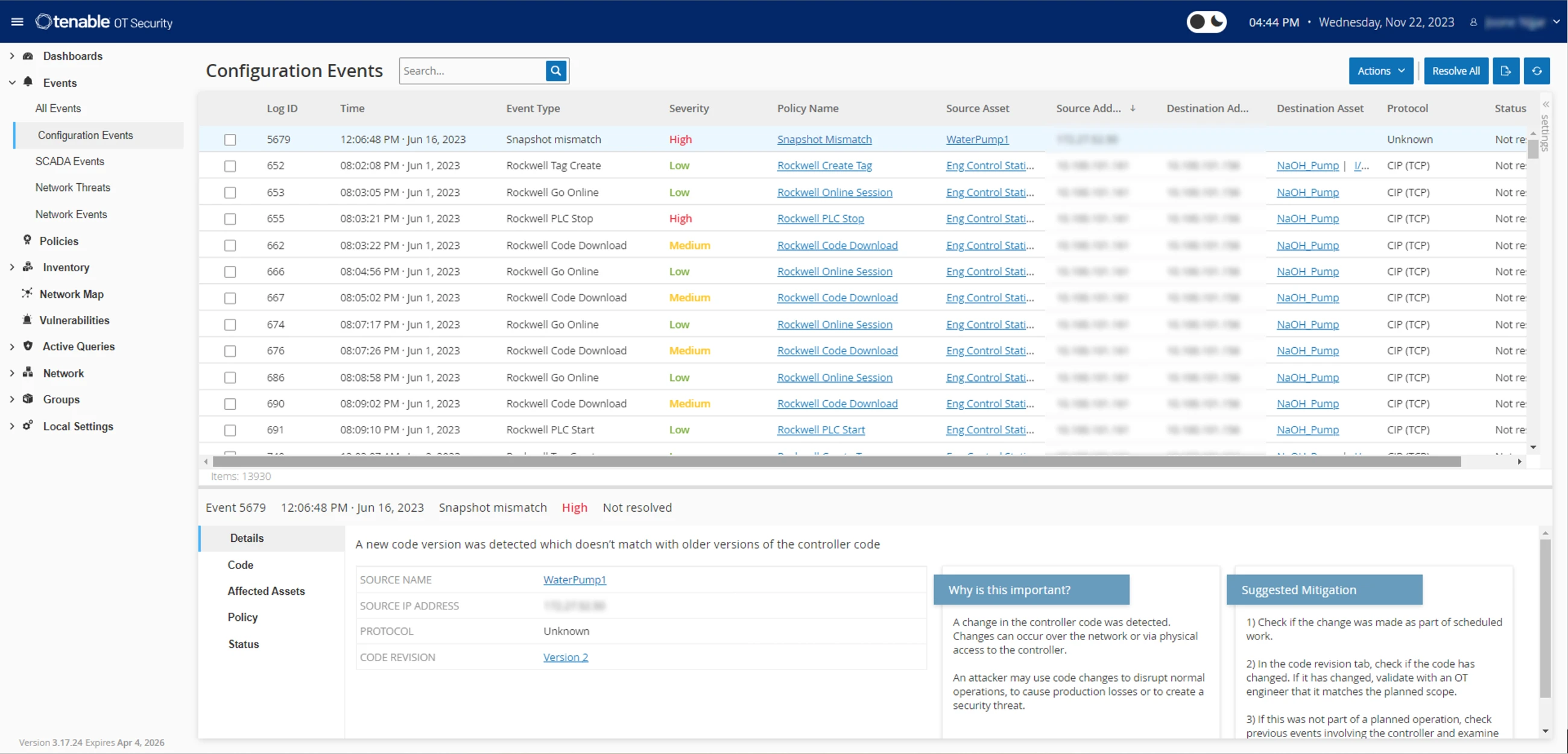
Configuration change tracking
Track malware and user-executed changes over your network or directly on a device. See a timeline of device configuration changes, including specific ladder logic segments, diagnostic buffers and tag tables. Establish a backup snapshot identifying the “last known good state” for faster recovery and compliance with industry regulations.
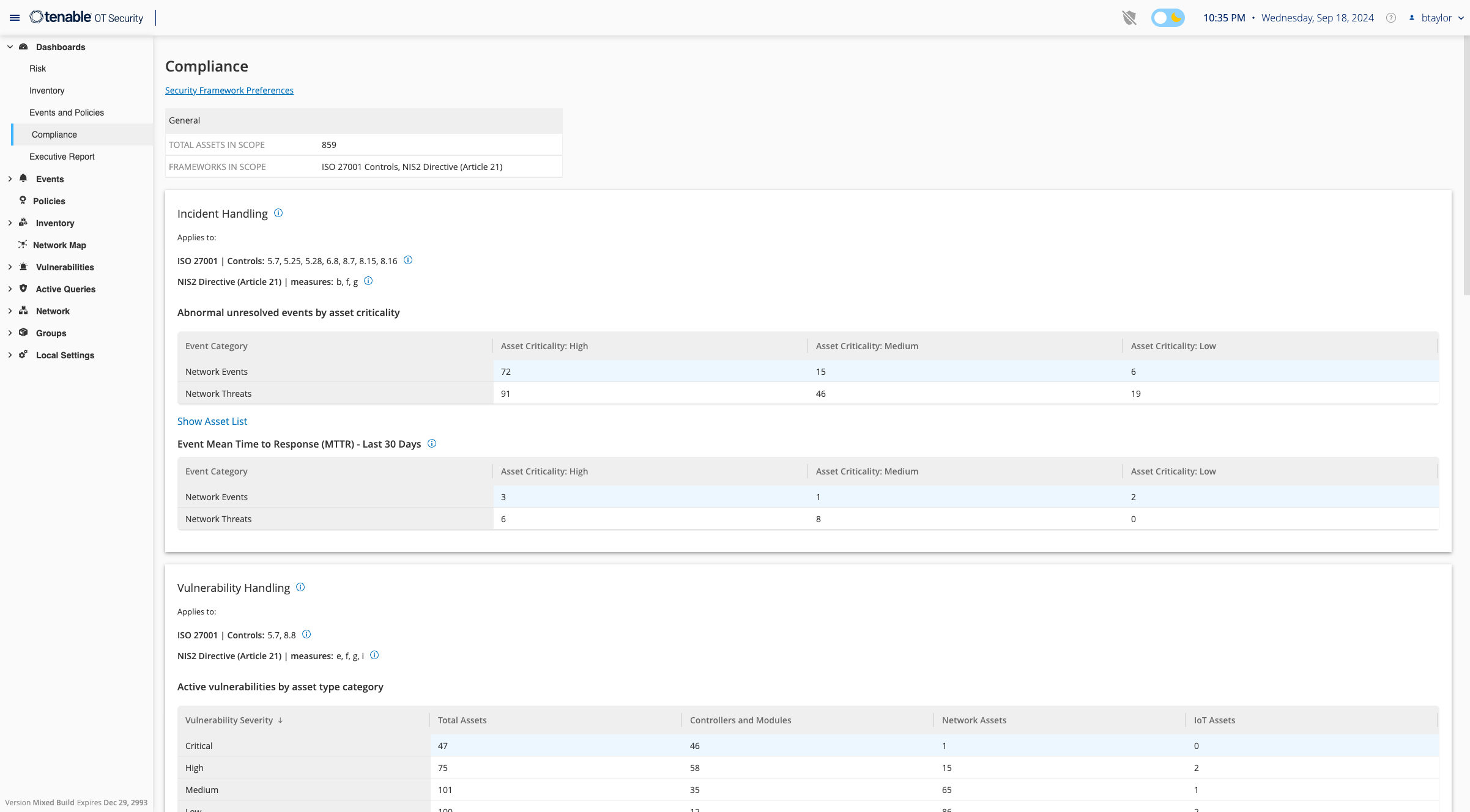
Streamlined audit, compliance and reporting
Transform your compliance process into a competitive advantage. Simplify compliance management and enhance incident response to help security teams mitigate risk and stay ahead in an evolving regulatory landscape. Easily map your OT security posture to the latest global frameworks and standards in a single dashboard for real-time visibility into compliance status.

Available through Tenable One: The world’s only AI-powered exposure management platform
Tenable One solves the central challenge of modern security: a deeply divided approach to seeing and doing battle against cyber risk. We remove risk by unifying security visibility, insight and action across the attack surface to rapidly expose and close gaps. Customers use Tenable One to eradicate priority cyber weaknesses and protect against attacks—from IT infrastructure to cloud environments to critical infrastructure and everywhere in between.
Learn more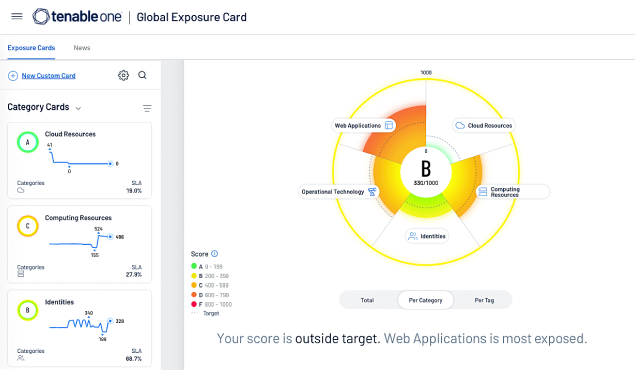
Tenable OT Security 3-minute explainer videos
Tenable OT Security protects your industrial networks from cyber threats, malicious insiders and human error across today's rapidly converging OT/IT environment.
Top threats to ICS
Industrial control plane
Asset management
Protection on both fronts
Industrial controllers





Related resources
Get Started with Tenable OT Security
We found that Tenable OT Security understood cybersecurity from an industrial control system perspective, not just an IT perspective. And that’s what really drew us to them.
- Tenable OT Security