Taking the Pulse of Your Network: Fitbit® for Security
Continuous network monitoring is not a new concept in network security, but it is a growing trend. Tenable Network Security pioneered continuous network monitoring back in 2004 with the introduction of SecurityCenter Continuous View (SecurityCenter CV) and has been improving the technology ever since. Continuous network monitoring helps executives answer questions like: Where are our risks? How effective is our security program? How do we measure security success? What should we invest in next? If continuous network monitoring is an elusive concept for you, the single best analogy to explain it is as a Fitbit® for security.
Personal health
Unless you’ve been sleeping under a rock, you probably know that Fitbit is a wearable health device that monitors how much sleep, exercise and calories you get each and every day, every minute. It tracks your personal health habits and goals non-intrusively and reports back to you continuously on your progress. It provides reports, charts, metrics and motivational alerts to keep you healthy.
Think of continuous network monitoring as a Fitbit for your network systems
Network health
We can think of continuous network monitoring as a Fitbit for your network systems. It monitors and reports on the most critical fundamentals of network health, including asset discovery, vulnerabilities, network access, user access and malware defense – all behind the scenes and non-intrusively. Once it’s configured, just like Fitbit, it works for you every minute of every day, tracking your progress and alerting you to potential risks. When security teams implement continuous network monitoring, they can be surprised to discover that they are not remediating vulnerabilities fast enough, they need to monitor users more thoroughly, or they need to reevaluate their security investments. Just like the first time someone wears a Fitbit and is surprised to learn that a mile is not 10,000 steps.
Whether you are in business, government or a non-profit, every executive needs assurance that the organization’s digital assets are protected. Every company that leverages networks, mobility, cloud or virtualization is subject to attacks. Tenable’s continuous network monitoring solutions provide assurance that your IT systems are not open to risks, so executives can be confident that their businesses are operating safely over the Internet. Just as with Fitbit, tracking the basics and doing them right assures a healthier, longer life for systems, while regularly monitoring progress towards your system goals.
Tracking 5 critical indicators
Tenable recently introduced 5 Critical Cyber Controls to the security community. These controls are at the heart of continuous network monitoring, to help you track the vital signs of your systems:
- Discover all assets
- Continuously remove vulnerabilities from all assets
- Deploy a secure network
- Assure that users only have access to the systems and data they need
- Continually hunt for malware and vulnerabilities that could potentially attack the well-being of your network
The 5 Critical Cyber Controls are the themes that are common in most complex standards and frameworks such as the SANS Top 20, NIST, or PCI. The 5 controls provide the framework for implementing a healthy security policy. Coupled with continuous network monitoring, the controls can monitor your cyber hygiene and provide motivation to practice a healthier cyber lifestyle.
Holistic health
Continuous network monitoring takes a holistic approach to monitoring security well-being. Not only does it discover all assets and track them for vulnerabilities, but it also monitors networks in real time for threats, gathers contextual analytics and provides assurance that mitigating controls are in place. Continuous network monitoring keeps you on track, continually making progress towards improving your security posture and meeting your business goals.
No other tool can provide such comprehensive assurance that your network systems are in good health
SecurityCenter CV is Tenable’s premier continuous network monitoring solution. It’s like having a Fitbit monitoring your systems 24/7 and alerting you to any problems. SecurityCenter CV harnesses the power of Nessus, Passive Vulnerability Scanner, and the Log Correlation Engine to centralize asset discovery and vulnerability assessment. It supports more technologies than any other vendor, including operating systems, databases, hypervisors, mobile devices, web servers, and embedded systems. With SecurityCenter CV, you can discover 100% of your assets (managed or unmanaged) across physical, virtual, mobile and cloud platforms. SecurityCenter CV also integrates with existing systems for timely analytics, rapid incident response and effective remediation. No other tool can provide such comprehensive assurance that your network systems are in good health.
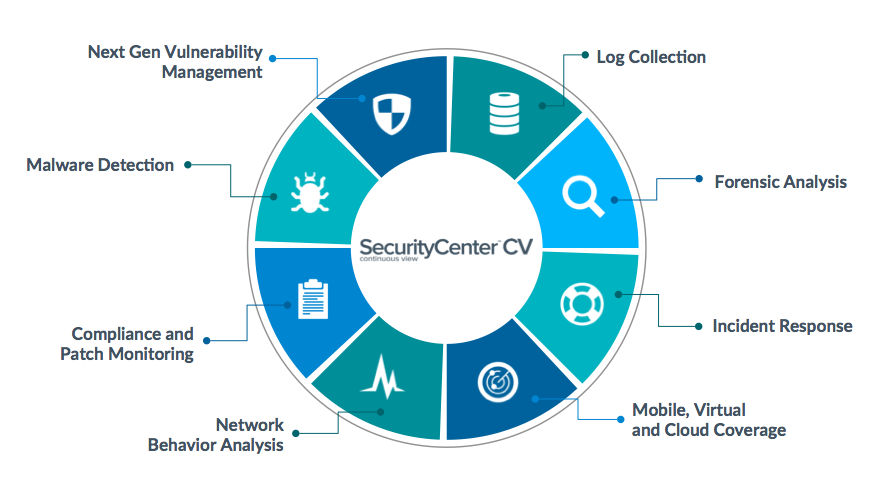
Take charge of your network health
Periodic vulnerability scans, like annual physicals, are limited in the type of protection that they can provide to assure system fitness. However, continuous network monitoring is game-changing technology and is becoming the new normal. Continuous network monitoring is not a fad, it implements the 5 healthy best practices that your organization should be monitoring and it provides daily visibility into your progress. Tenable is proud to be leading the trend.
Resources
- Contact us for more details. And take a look at these resources:
- Tenable’s Critical Cyber Controls for Secure Systems
- Definitive Guide to Continuous Network Monitoring
- SecurityCenter CV
Fitbit is a registered trademark of Fitbit, Inc.
- Vulnerability Management
- Vulnerability Scanning

