by Josef Weiss
October 10, 2016
Incident response is a broad area that not only involves breaches and malicious software, but also involves the handling of unauthorized access from internal or external sources, misuse of systems, and data loss. Without proper incident response procedures, organizations may spend a considerable amount of time and resources recovering from these incidents. Malicious activities may continue to proliferate through critical systems, allowing attackers additional opportunities to exploit more systems and exfiltrate more data. Undetected long-term malicious activity may jeopardize an organization’s competitiveness and long-term survival.
The federal government relies heavily on external service providers and contractors to assist in carrying out a wide range of federal missions. Sensitive but unclassified federal information is routinely processed by, stored on, or transmitted through nonfederal information systems. Failing to properly protect this Controlled Unclassified Information (CUI) could impact the ability of the federal government to successfully carry out required missions and functions.
The National Institute of Standards and Technology (NIST) created Special Publication 800-171 "Protecting Controlled Unclassified Information in Nonfederal Information Systems and Organizations" to provide recommended requirements for protecting the confidentiality of CUI. Federal agencies should use these requirements when establishing contracts and agreements with nonfederal entities that process, store, or transmit CUI.
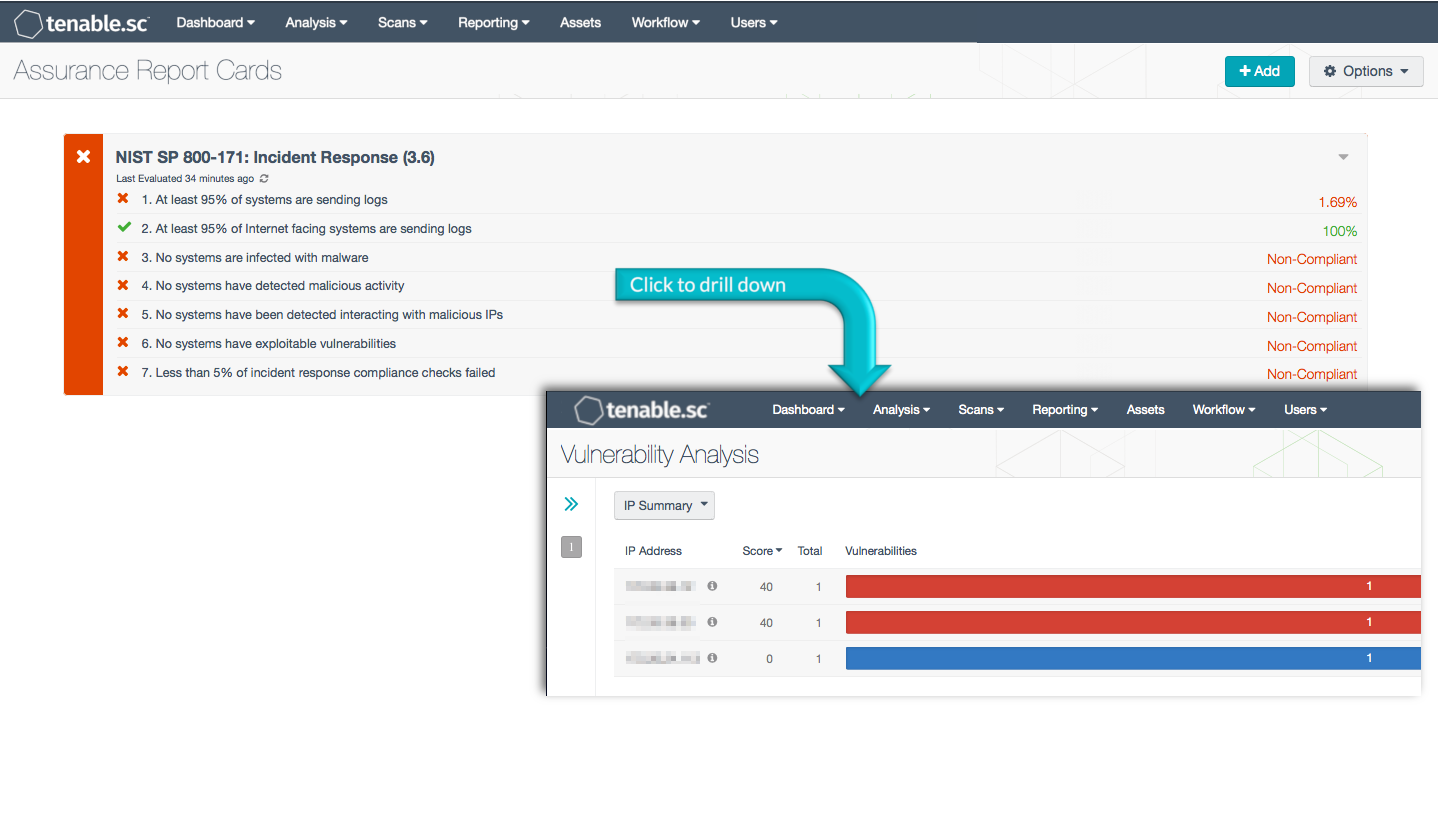
This Assurance Report Card (ARC) aligns with the Incident Response family of security requirements in NIST SP 800-171 (section 3.6). These requirements focus on establishing an operational incident-handling capability for organizational information systems that includes adequate preparation, detection, analysis, containment, recovery, and user response activities. Using this ARC, an organization will be better able to track and improve the overall incident response procedures.
More details on each of the policy statements included in the ARC are given below. Clicking on a policy statement will bring up the analysis screen to display more details related to that policy statement. The ARC policy statement parameters are guides that can be customized as necessary to meet organizational requirements.
This ARC is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance. The dashboard requirements are:
- Tenable.sc 5.4.0
- Nessus 8.4.0
- LCE 6.0.0
- NNM 5.9.0
- Compliance data
Tenable's Tenable.sc Continuous View (CV) is the market-defining continuous network monitoring solution, and can assist an organization in identifying, tracking, and reporting incidents. Tenable.sc CV is continuously updated with information about advanced threats, zero-day vulnerabilities, and new regulatory compliance data. Active scanning periodically examines systems to find vulnerabilities, and can also make use of audit files to assess compliance. Passive listening provides real-time monitoring to collect information about systems and vulnerabilities. Host data and data from other security devices is analyzed to monitor policy and configuration settings activity. Tenable.sc CV provides an organization with the most comprehensive view of the network and the intelligence needed to secure systems and safeguard sensitive information.
ARC Policy Statements
At least 95% of systems are sending logs - This policy statement displays the number of systems that are sending logs to the Tenable Log Correlation Engine (LCE) to total systems. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Logs can provide valuable information on network, application, and security events from multiple devices across a network. To get the clearest picture of network status and security, all systems on the network should be sending logs to LCE.
At least 95% of internet facing systems are sending logs - This policy statement displays the number of internet facing systems that are sending logs to the Tenable Log Correlation Engine (LCE) to total internet facing systems. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Systems that face the internet should especially be sending logs to LCE. Logs can provide valuable information on network, application, and security events from multiple devices, which can help to identify possible intrusions or attacks. To get the clearest picture of network status and security, all systems on the network should be sending logs to LCE.
No systems are infected with malware - This policy statement displays non-compliance if any hosts are infected with malware. CSC 8 suggests that malware defenses be established that control the installation, spread, and execution of malicious code. Malware can be a simple annoyance such as an adware, or can be more serious such as a virus or Trojan. Malware can cause serious harm or transmit information to unwanted third parties and should be identified and removed as quickly as possible.
No systems have detected malicious activity - This policy statement displays non-compliant if malicious activity has been detected on any systems. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Tenable.sc CV is continuously updated with information about advanced threats and vulnerabilities. Malicious processes, known bad files, and interactions with known bad IP addresses can be detected actively and passively. Any malicious activity should be further investigated by the organization.
No systems have been detected interacting with malicious IPs - This policy statement displays the percentage of total systems that have been detected interacting with known malicious IP addresses. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Tenable.sc receives a daily updated list of IP addresses and domains that are participating in known botnets. Using this information, systems on the network that interact with known malicious IP addresses can be detected. Any systems interacting with known malicious IP addresses should be investigated immediately by the organization to minimize security risks.
No systems have exploitable vulnerabilities - This policy statement displays the ratio of systems that have exploitable vulnerabilities to total systems. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. An exploitable vulnerability is one for which malware already exists that can take advantage of the vulnerability in order to gain control of a system. Reducing the number of exploitable vulnerabilities can greatly help to reduce the risk to the network. Any exploitable vulnerabilities should be remediated immediately.
Less than 5% of incident response compliance checks failed - This policy statement displays the percentage of incident response compliance checks that failed. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Incident response settings may include log retention and access settings, among other things. Compliance is measured against those policy checks that reference standards such as NIST 800-53, NIST 800-171, and the CIS Critical Security Controls.