by Sharon Everson
July 9, 2020
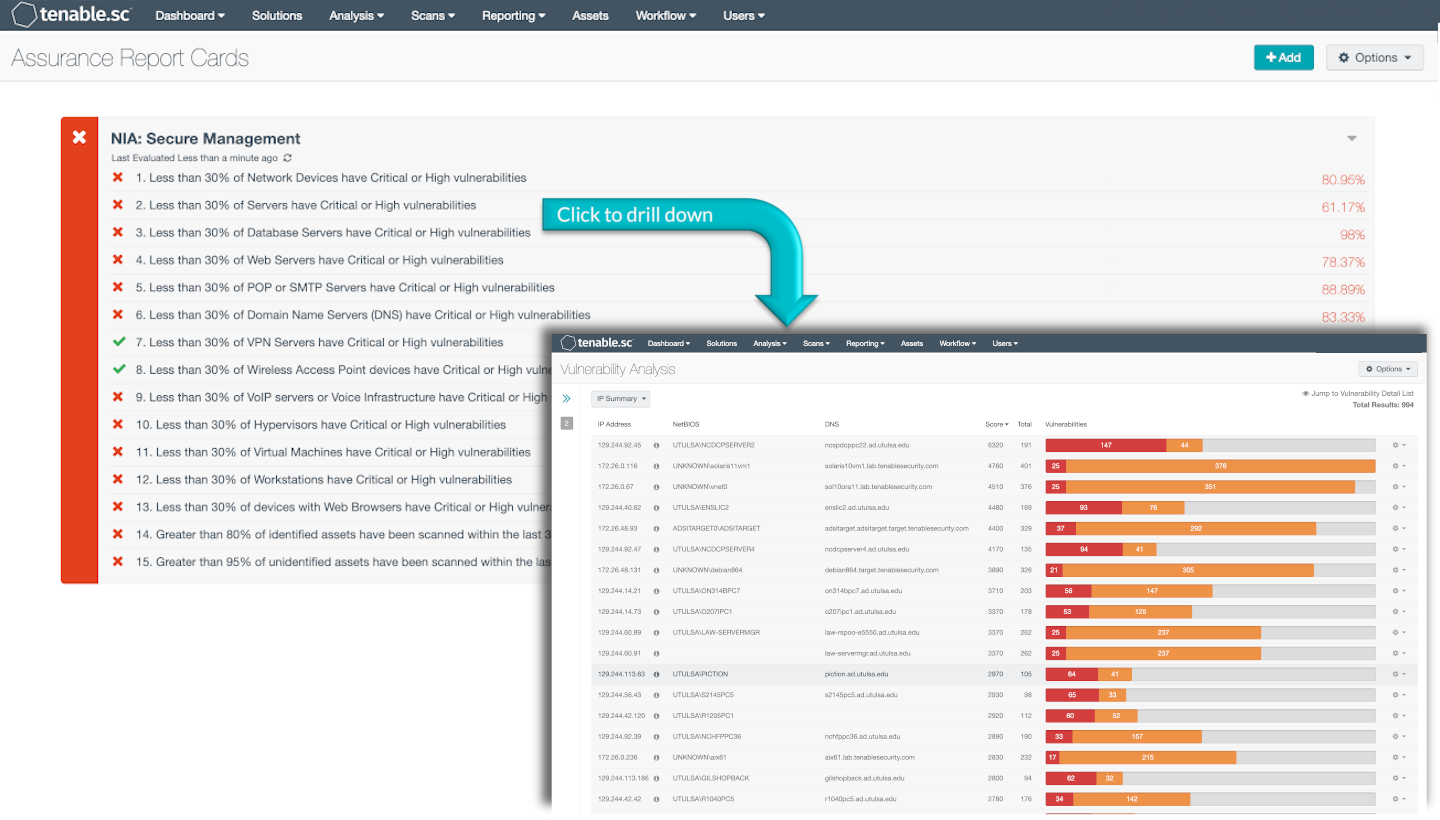
The National Information Assurance (NIA) Policy v2.0 requires that agencies classify their assets. Tenable recommends using the Cyber Exposure Life Cycle model in conjunction with NIAv2 compliance efforts. The first stage, Discovery, of the Cyber Exposure lifecycle includes identifying and mapping assets across computing environments. In order to maintain a standardized method of classification of assets and assess risk on those assets, the risk manager must understand which assets are on the network and make sure they are appropriately classified.
Tenable.sc provides multiple methods of classifying assets, such as services detection, operating system detection, hardware detections, and many others. This ARC uses dynamic asset lists to categorize devices. Risk managers are able to view risks based on asset classifications such as Network Devices, Database Servers, Web Servers, Workstations, or Wireless Access Points among others. The first set of policy statements in the ARC show the percentage of assets with a particular classification that have Critical or High vulnerabilities compared to the total assets with that classification. Thus allowing the security analyst to focus on fixing vulnerabilities one asset classification at a time. The last two policy statements provide the analyst the ability to see vulnerabilities on devices that have been classified and devices that have not been classified. Particular attention is warranted on devices that have not been classified as this could indicate a security risk if the device is unknown and unclassified.
This ARC uses dynamic asset lists to classify devices. Assets are used to group devices that share common attributes. Tenable.sc supports template-based and custom assets. Custom assets can be created to support NIA’s Asset Classification Model. The policy statements in this ARC can be edited to specify custom assets corresponding to NIA policy.
Tenable.sc uses active and passive plugins to collect asset information including asset name, type, IP address, MAC address, location, serial number, and other important information. One method of identifying the device category is using the plugin “Device Type (54615)”. Plugin 54615 maps operating systems and other asset behaviors to different categories such as a server, router, or firewall. Other methods are also used to identify device categories such as running services or open ports. Tenable.sc provides several scalable approaches to identifying asset types.
The ARC and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance.
The dashboard requirements are:
- Tenable.sc 5.14.1
- Nessus 8.10.1
- Compliance data
Tenable.sc Continuous View (CV) is the market-defining On-Prem Cyber Exposure Platform. Tenable.sc CV provide the ability to continuously Assess an organization’s adherence to best practice configuration baselines. Tenable.sc provides customers with a full and complete Cyber Exposure platform for completing an effective Information Security Management System program prescribed by the NIA standard.
This ARC includes the following policy statements:
1. Less than 30% of Network Devices have Critical or High vulnerabilities - This policy statement identifies the percentage of suspected network devices with Critical or High vulnerabilities compared to the total suspected network devices. Compliance for this policy is less than 30%.
2. Less than 30% of Servers have Critical or High vulnerabilities - This policy statement identifies the percentage of servers with Critical or High vulnerabilities compared to the total servers. Compliance for this policy is less than 30%.
3. Less than 30% of Database Servers have Critical or High vulnerabilities - This policy statement identifies the percentage of Database Servers with Critical or High vulnerabilities compared to the total Database Servers. The database servers in the Database Servers asset includes MySQL Database Server, Oracle Database Server, PostgresSQL, Sybase SQL Anywhere Database Server, IBM DB2 Servers, Microsoft SQL Server and others. Compliance for this policy is less than 30%.
4. Less than 30% of Web Servers have Critical or High vulnerabilities - This policy statement identifies the percentage of Web Servers with Critical or High vulnerabilities compared to the total Web Servers. Compliance for this policy is less than 30%.
5. Less than 30% of POP or SMTP Servers have Critical or High vulnerabilities - This policy statement identifies the percentage of POP or SMTP Servers with Critical or High vulnerabilities compared to the total POP or SMTP Servers. Compliance for this policy is less than 30%.
6. Less than 30% of Domain Name Servers (DNS) have Critical or High vulnerabilities - This policy statement identifies the percentage of Domain Name Servers with Critical or High vulnerabilities compared to the total Domain Name Servers. Compliance for this policy is less than 30%.
7. Less than 30% of VPN Servers have Critical or High vulnerabilities - This policy statement identifies the percentage of VPN Servers with Critical or High vulnerabilities compared to the total VPN Servers. Compliance for this policy is less than 30%.
8. Less than 30% of Wireless Access Point devices have Critical or High vulnerabilities - This policy statement identifies the percentage of Wireless Access Point devices with Critical or High vulnerabilities compared to the total Wireless Access Point devices. Compliance for this policy is less than 30%.
9. Less than 30% of VoIP servers or Voice Infrastructure have Critical or High vulnerabilities - This policy statement identifies the percentage of VoIP Servers or Voice Infrastructure devices with Critical or High vulnerabilities compared to the total VoIP Servers or Voice Infrastructure devices. Compliance for this policy is less than 30%.
10. Less than 30% of Hypervisors have Critical or High vulnerabilities - This policy statement identifies the percentage of Hypervisors with Critical or High vulnerabilities compared to the total Hypervisors. Compliance for this policy is less than 30%.
11. Less than 30% of Virtual Machines have Critical or High vulnerabilities - This policy statement identifies the percentage of Virtual Machines with Critical or High vulnerabilities compared to the total Virtual Machines. The asset specified in this policy statement uses active plugins to discover hosts that appear to be virtual machines, such as VMWare, VirtualPC, VirtualBox hosts, Hyper-V, or a virtual management application on a windows host. Compliance for this policy is less than 30%.
12. Less than 30% of Workstations have Critical or High vulnerabilities - This policy statement identifies the percentage of Workstations with Critical or High vulnerabilities compared to the total Workstations. This number includes devices identified as Apple Computers, Windows, or Linux hosts by Tenable.sc assets. Compliance for this policy is less than 30%.
13. Less than 30% of devices with Web Browsers have Critical or High vulnerabilities - This policy statement identifies the percentage of devices with Web Browsers with Critical or High vulnerabilities compared to the total devices with Web Browsers. Compliance for this policy is less than 30%.
14. Greater than 80% of identified assets have been scanned within the last 30 days - This policy statement identifies the percentage of identified assets with Critical or High vulnerabilities compared to the total identified assets. The identified assets include all devices classified by the previous policy statements in this ARC. Compliance for this policy is Greater than 80%.This policy statement identifies the percentage of unidentified assets with Critical or High vulnerabilities compared to the total unidentified assets. Tenable.sc was not able to categorize these devices using any of the classifications represented by the dynamic assets in the previous policy statements of this ARC. Unclassified assets should be investigated to determine why the asset is not being identified by one of the above policy statements. New dynamic assets and policy statements can be added to the ARC for classifications specific to an agency. Compliance for this policy is greater than 95%.
15. Greater than 95% of unidentified assets have been scanned within the last 30 days - This policy statement identifies the percentage of unidentified assets with Critical or High vulnerabilities compared to the total unidentified assets. Tenable.sc was not able to categorize these devices using any of the classifications represented by the dynamic assets in the previous policy statements of this ARC. Unclassified assets should be investigated to determine why the asset is not being identified by one of the above policy statements. New dynamic assets and policy statements can be added to the ARC for classifications specific to an agency. Compliance for this policy is greater than 95%.