by Cesar Navas
October 29, 2019
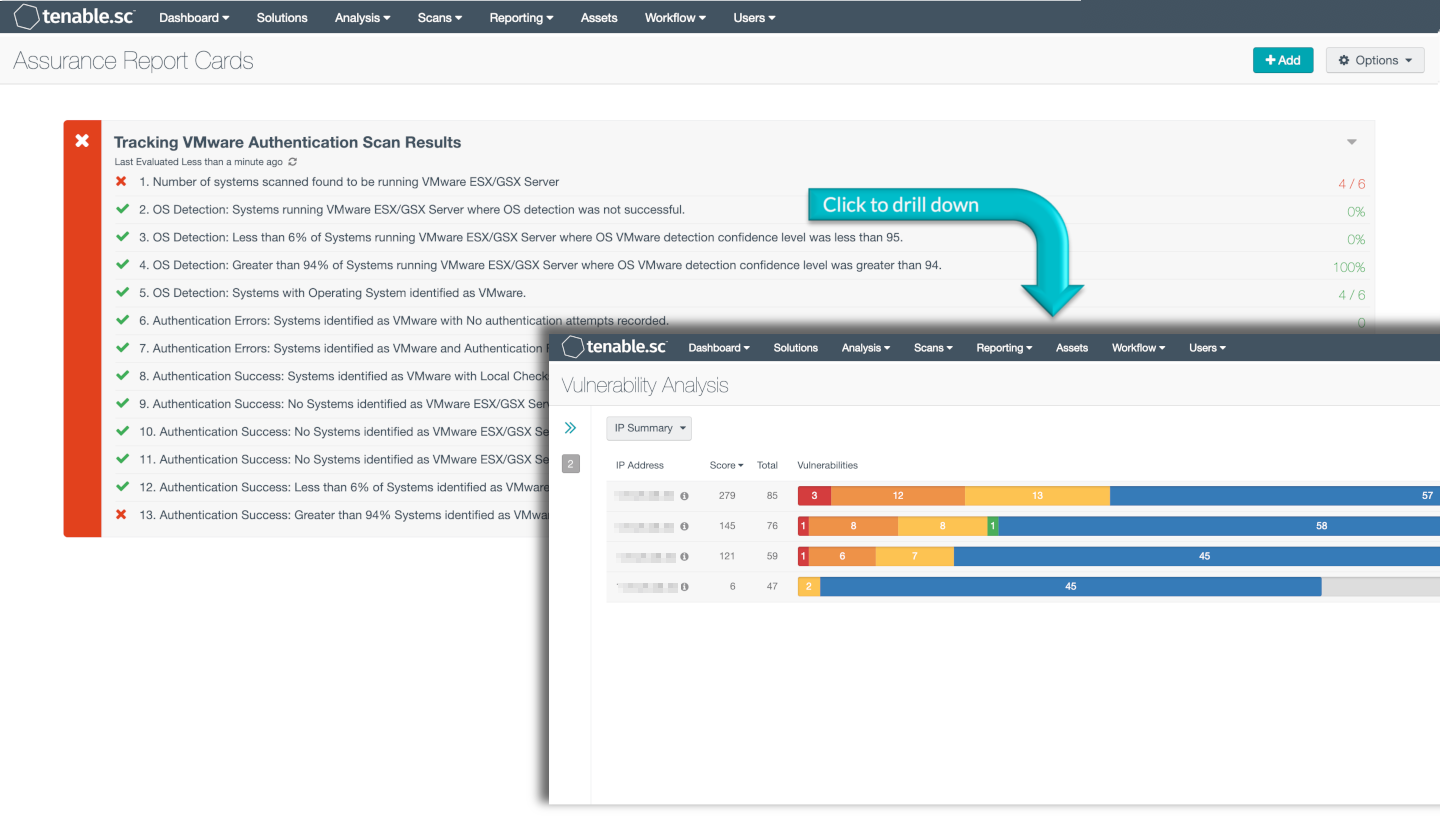
To ensure they have the most complete information about the security posture of assets, organizations should deploy scans that use credentials. Scans that use credentials and successfully authenticate on a system (and run with Local Security Checks enabled) return a more comprehensive set of data about the system. This Assurance Report Card (ARC) provides the ability to report and analyze authenticated scan results for VMware products.
When managing a large enterprise, problems often arise when verifying the validity of a vulnerability scan. While ensuring the os is correctly identified, relevant checks can be run, and the system is authenticated properly, challenges can arise. For example, some hosts may have invalid credentials, or valid credentials but insufficient privileges, or connectivity issues. Through the use of Dynamic Assets, Tenable.sc is able to group devices together for a comparative analysis. Using the ARC, Tenable.sc provides advanced analysis capabilities to facilitate and easily distribute this functionality to organizations.
This ARC presents a series of policy statements which together, can be used to troubleshoot, fix, and verify authenticated scan results. The policy statements are grouped so that the analyst can focus on issues related to os detection, authentication errors, and authentication success. The first four policy statements relate to OS detection and the OS detection confidence level. It reports on systems that are scanned by Nessus that are found to be running VMware ESX or GSX server. The next policy statement is a continuation of the previous and helps identify ESX or GSX servers for which identifying the OS was not possible. Examine these systems so that these systems can be properly identified and then authenticated. Policy statements three and four indicate the OS detection confidence level of systems suspected of being VMware products where the OS was identified.
The following five policy statements help isolate various types of authentication-related issues that may occur. Policy statements five through eight are split between two sections of the ARC: Authentication Errors and Authentication Success. Policy statement five and six help identify VMware products with authentication errors. The next three policy statements start the Authentication Success section of the ARC and provide analysts with a clear view of systems with successful credentials that may still have authentication problems.
Finally, the last policy statement shows those systems identified as VMware products with successful authentication, with local checks enabled, and without authentication errors.
This ARC is available in the Tenable.sc feed, which is a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The ARC can be easily located in the Tenable.sc feed under the Compliance category. The ARC requirements are as follows:
- Tenable.sc 5.12.0
- Nessus 8.7.1
This ARC provides the organization with a clear and simplified method to identify VMware products for analysis. By first Discovering the systems suspected of being a VMware product from the scanned devices, the ARC can then assess the operating systems of the targets to ensure the devices are indeed VMware products. Then the data is Analyzed for proper authentication, which facilitates the Fix and Measuring steps to the Cyber Exposure Lifecycle. Tenable.sc is the On-prem solution for understanding the picture of the network, while keeping the data under the organization’s control. Built on leading Nessus technology, Tenable.sc discovers unknown assets and vulnerabilities, and monitors unexpected network changes before they turn into breaches.
This ARC includes the following policy statements:
1. Number of systems found to be running VMware ESX/GSX Server: This policy statement displays a ratio number of the systems identified as a VMware product compared to the total number of systems scanned.
2. OS Detection – Systems running VMware ESX/GSX Server where OS detection was not successful: This policy identifies systems that are suspected of being a VMware product, but the OS was not discovered. Systems that match this policy should be investigated for misconfiguration, valid login credentials, or for proper identification as a VMware product. Compliance for the policy is No systems matching the policy.
3. OS Detection - Less than 6% of Systems running VMware ESX/GSX Server where OS detection confidence level was less than 95%: This policy identifies systems that were suspected of being a VMware product, however to a degree, Nessus was not confident of the operating systems. Systems matched by this policy should be investigated for misconfiguration, valid login credentials, and for proper identification as a VMware product. Compliance for the policy is less than 6% systems matching the policy, which allows for new systems that are found to be on the network.
4. OS Detection - Greater than 94% of Systems running VMware ESX/GSX Server where OS detection confidence level was greater than 94: This policy identifies systems that were scanned and suspected of being a VMware product. Nessus is confident of the identified operating system. Compliance for the policy is greater than 94% of systems matching the policy.
5. OS Detection – Systems with operating system identified as VMware: This policy statement displays a ratio of the systems identified as a VMware product compared to the total number of systems scanned. Compliance for this policy is “Any matching the policy.”
6. Authentication Errors - Systems identified as VMware with No authentication attempts recorded: This policy identifies systems where no authentication was attempted. This could mean no suitable protocol was presented to Nessus, no credentials were available for the operating system, or another issue is present. These systems should be investigated and special attention should be given to how the operating system was detected and what condition exists that prevented proper authentication attempts. Compliance for the policy is “No matching systems."
7. Authentication Success: Systems identified as VMWare and Authentication Failures: This policy identifies systems where the operating system is correctly identified and with authentication success., However, the credentials provided with the scan failed to allow Nessus to login correctly. Invalid credentials, incompatible protocol settings, or other similar problems could cause this issue. The vulnerability data collected on this system should be considered incomplete. Compliance for the policy is “No systems matching the policy.”
8. Authentication Success: Systems identified as VMware with Local Checks disabled: This policy provides a list of systems that have been successfully authenticated however, local checks were not enabled. While these systems should be considered successfully authenticated, there could be missing vulnerability data. System administrators should investigate these systems for misconfiguration. This policy statement displays the percentage of VMware products identified compared to the total number of network devices with Local Checks disabled. Compliance for the policy is “No systems matching the policy.”
- Authentication Success: No Systems identified as VMware ESX/GSX Server with Authentication Success and Authentication Failure: This policy identifies systems where the operating system is correctly identified and with authentication success however, the credentials provided with the scan failed to allow Nessus to login correctly. Invalid credentials, incompatible protocol settings, or other similar problems could cause this issue. The vulnerability data collected on this system should be considered incomplete. Compliance for the policy is “No matching systems.”
- Authentication Success: No Systems identified as VMware ESX/GSX Server with Authentication Success through SSH and with Failed SOAP Authentication: This policy identifies systems where the operating system is correctly identified and with successful SSH authentication however, the credentials provided for SOAP authentication failed to allow Nessus to login correctly. Invalid credentials, incompatible protocol settings, or other similar problems could cause this issue. The vulnerability data collected on this system should be considered incomplete. Compliance for the policy is “No matching systems.”
- Authentication Success: No Systems identified as VMware ESX/GSX Server with Authentication Success through SSH and with Failed vCenter Authentication: This policy identifies systems where the operating system is correctly identified and with successful SSH authentication however, the credentials provided for vCenter authentication failed to allow Nessus to login correctly. Invalid credentials, incompatible protocol settings, or other similar problems could cause this issue. The vulnerability data collected on this system should be considered incomplete. Compliance for the policy is “No matching systems”.
- Authentication Success: Less than 6% of Systems identified as VMware with Local Checks Enabled & Errors: This policy provides a list of systems that have been successfully authenticated however, there were recorded problems related to permissions or access to any number of resources. While these systems should be considered successfully authenticated, there could be missing vulnerability data. System administrators should investigate these systems for misconfiguration or possible insufficient privileges for the scan account. This policy statement displays the percentage of VMware products identified compared to the total number of network devices with Local Checks enabled. Compliance for the policy is less than 6% of systems matching the policy, which allows for new systems that are found to be on the network.
- Authentication Success: Greater than 94% Systems identified as VMware with Successful Authentication, Local Checks, and without Errors: This policy identifies the majority of VMware products on the network. Analysts can rely on the vulnerability data collected for these targets. Nessus was able to login and collect missing patches, compliance settings, and many other risk indicators based on the applied scan policies. Compliance for the policy is greater than 94% of systems matching the policy.