Understanding cloud-native application protection platforms (CNAPP)
How and why you should secure cloud-native applications
As you adopt more cloud-native applications and services throughout your enterprise, it’s important your teams get comprehensive visibility into all your cloud-based environments so they can more quickly detect and fix cloud exposures. A cloud-native application platform (CNAPP) integrated into your cybersecurity strategy can help you do just that.
With a CNAPP, you can protect and secure cloud applications throughout your entire software development lifecycle — from development through production and deployment.
Instead of using disparate cloud security tools that silo data and create blind spots across your cloud environments, a CNAPP unifies these tools into a single solution. It unites DevSecOps processes with security and infrastructure management.
A cloud-native security platform is an effective way to manage cloud security tools in one system, which ultimately enhances your cloud security resources with less cost and wasted time. It is also a valuable tool to mature your cloud cyber hygiene practices.
And, since CNAPP solutions secure multi-cloud and hybrid infrastructure, you can use data analytics and reporting to make more informed and business-aligned cloud security decisions based on real-time events and information. You can enhance these capabilities with CNAPP tools with artificial intelligence (AI) and machine-learning capabilities.
This CNAPP resource explores what a cloud-native application platform is and how it can help your teams discover software flaws, vulnerabilities, misconfigurations and other security issues throughout your dynamic cloud environments.

Here’s what you’ll discover:
Why is CNAPP important?
A cloud-native application protection platform provides increased visibility into cloud risks.
Learn moreEnhance cloud security with CNAPP automation
An automated CNAPP can help you close the cybersecurity expertise hiring gap.
Learn moreFrequently asked CNAPP questions
Check out this FAQ for common CNAPP questions and answers.
Learn moreBenefits of CNAPP adoption
Tenable Cloud Security is a CNAPP that gives you complete visibility into your cloud-native environment for security.
Learn moreTenable Connect community for CNAPP
Tenable Connect is a great place to talk about cloud-native security, ask questions and share tips.
Learn moreSecure your cloud-native environments
From build time to run-time, best practices can build confidence in your approach to cloud security.
Learn moreDevelop and expand your cloud with confidence
Secure every step of your cloud environment, from code to cloud, all within a developer-friendly cloud-native application platform. Safeguard all your cloud resources, container images and cloud assets to mature your cloud security posture as your cloud work environments evolve and become more complex.
Empower your cloud: Mastering CNAPP security
Traditional security methods used for on-prem IT assets weren't designed for the cloud. Security practitioners trying to bend and mold these practices for the cloud are wasting time — and frustrating themselves — especially because there are more effective ways to secure cloud infrastructure and services.
A CNAPP gives you holistic insight into complex public, private and hybrid-cloud environments so you can expose cloud blind spots and secure this rapidly changing attack surface.
This white paper explores what a CNAPP is and how it can help you quickly and effectively secure the cloud. Read more to learn about:
- The shared responsibility model (Who secures what? You? Your CSP?)
- Security risks in a multi-cloud environment
- How to control cloud identities
- Cloud vulnerability management
- Enterprise advantages from CNAPP usage
Enterprise guide to policy as code: Design, build, and run-time
As your organization adopts more cloud-hosted applications and builds onto your existing cloud-based architecture, security is increasingly complex. Many organizations struggle to shift traditional on-prem security practices to the cloud because these approaches don’t work for cloud workloads’ dynamic nature.
Now is the time to shift left and adopt security best practices built for protecting the cloud and hybrid cloud/on-prem environments. It’s important your teams are proactive and apply these processes before cloud development and deployment. True CNAPP cloud security starts in your earliest planning phases and should be an integral part of your software development lifecycle (SDLC) all the way to run-time.
With Tenable, you can adopt policy as code and infrastructure as code (IaC) to secure modern cloud environments.
Extending vulnerability management from code to cloud
Cloud workloads are complex and dynamic. They continuously introduce new risks. On top of that, traditional vulnerability management approaches don’t work well for the cloud, which makes it challenging for some teams to keep up with those risks. Instead, your security teams should move beyond traditional vulnerability management practices and extend continuous exposure management into the cloud.
This cloud strategy is more than just discovering and fixing vulnerabilities as you find them. It includes proactively exposing and remediating software flaws and misconfigurations across your entire SDLC.
In this ebook, learn more about how adopting a cloud security posture management (CSPM) solution can help you integrate security throughout cloud app development.
Tenable Connect community: Your comprehensive
CNAPP resource for cloud security
Tenable Connect is your one-stop resource for all things related to CNAPP. Whether you have questions for other cloud security professionals or you’re looking to take a deeper dive into how Tenable can help you solve all of your cloud-hosted application security needs, Tenable Connect is the place to be.
CNAPP: An evolving approach to cloud security
Attackers know user credentials are the keys to your cloud environment. One successful social engineering attack can grant access for lateral movement across your cloud, often without your knowledge. Protect your cloud identities and resources with identity and access management.
Read moreUnlocking Kubernetes innovation through simplified cloud security
Kubernetes security is challenging, but the right CNAPP tool can help you overcome these complexities with automated, custom policy enforcement; Helm charts scanning; enhanced access controls and cloud workload protection (CWP) for containerized environments.
Read moreWhy integrating DSPM is key to your CNAPP strategy
As your organization migrates more systems and services to the cloud, the amount of sensitive data attackers may try to exploit increases along with it. An integrated DSPM and CNAPP solution can give you real-time insight into cloud risk so you can quickly close security gaps.
Read moreApplication security from build time to run-time
Effective cloud application security requires a shift left from traditional vulnerability management practices to a risk-based approach that utilizes security best practices to manage dynamic and complex cloud environments.
While every organization has unique factors that directly affect cloud security approaches and maturity, here are six recommended cloud security best practices to ensure your cloud-native applications are safe from development to deployment and beyond.

Identify flaws in infrastructure as code by integrating into your development environment and pipeline.


Assess infrastructure as code on commit or merge requests.


Integrate into the CI/CD pipeline to identify flaws in containers and third-party libraries before deployment.


Continuously scan and assess Kubernetes and your cloud infrastructure to identify drift.


Identify flaws in running containers and compute instances without deploying scanners or installing agents.


Merge critical ad hoc changes and required remediation steps back into build.
Frequently asked CNAPP questions
Do you have questions about CNAPP, but not sure where to start? This CNAPP FAQ has your answers:
What is a cloud-native application protection platform?
What is CNAPP meaning?
What does cloud-native mean?
Is cloud-native safe?
What is a cloud-native application?
What are some core components of cloud-native security?
How do you secure cloud-native environments?
What is a CNSP?
What are some challenges for CNAPP security?
What should I look for in the right CNAPP?
Does traditional vulnerability management work for cloud-native environments?
What is a container?
What is container as a service (CaaS)?
What is policy as code?
What is infrastructure as code?
Infrastructure as a code (IaC) manages and provisions cloud infrastructure through code, typically within configuration files.
Tenable Cloud Security can scan infrastructure as code to find security issues, including vulnerabilities, flaws, policy violations or misconfigurations during the development process. It automates discovery of potential security weaknesses so your teams can remediate them before a breach. IaC is an important component of DevOps, security and compliance.
What is cloud security posture management (CSPM)?
CSPM consists of tools and resources to expose cloud-based issues such as misconfigurations or other compliance or security risks. CSPMs alert security teams when they identify security or compliance issues within a cloud environment.
A CSPM can also give you continuous monitoring capabilities across your production environment to identify cloud-native application issues and address them before deployment. If issues arise post-deployment, a CSPM can also automatically discover exposures and help you remediate them, so you’re always proactive about cloud security.
What is a cloud workload protection platform (CWPP)?
A CWPP helps secure and manage cloud environment workloads. CWPP approaches cloud security from a workload level, not as an endpoint. CWPPs protect the cloud from cyberattacks, even within multiple cloud environments.
A cloud workload protection program provides comprehensive visibility into the cloud to more quickly and effectively identify cloud security issues and prioritize critical issues for remediation first. CWPP supports continuous integration and continuous delivery (CI/CD) for all of your cloud workloads, including servers, virtual machines, containers and serverless workloads.
What is a cloud access security broker (CASB)?
What is Kubernetes?
What is Kubernetes Security Posture Management (KSPM)?
What is a cloud security provider (CSP)?
What is a software development lifecycle (SDLC)?
What is run-time?
Why is it important to integrate a CNAPP into your SDLC?
CNAPP: Close cloud exposures with actionable cloud security
Distributed environments and growing attack surfaces introduce new cloud-based attack vectors. Threat actors are eagerly trying new and more complex tactics to take advantage of your cloud exposures. Close cloud security vulnerabilities, fix misconfigurations and risky entitlements to proactively protect your sensitive cloud data with Tenable’s CNAPP.
Cloud-native application protection platform (CNAPP) blog bytes

CNAPP: What is it and why is it important for security leaders?
There are several benefits in using a cloud-native application protection platform. It provides increased visibility and insight into your cloud application security risks, improves compatibility, detects and remediates security issues sooner. It can also automate security into your CI/CD pipelines. Read this blog to learn more about how a CNAPP can help you secure your cloud environments, from code to cloud.

If you only have five minutes, here’s CNAPP in a snap
From confusion about the cloud shared responsibility model to a vast amount of CNAPP vendors that tout they can manage all your cloud security needs, getting a handle on cloud security best practices can be time-consuming and frustrating. Yet, cloud security breaches are on the rise. This blog and related ebook takes some of the confusion out of the role of a CNAPP in cloud security and clearly explains what it is, how it works and why you need it.

An analyst’s guide to cloud-native vulnerability management
Cloud environments have unique cloud vulnerabilities and other cloud-based security issues like misconfigurations. Traditional vulnerability management practices can't effectively address these exposures. This blog explores why you need cloud vulnerability management practices and how CNAPP tools can help you continuously monitor multi-cloud environments.
CNAPP and cloud security on-demand
The first 90 days of a CNAPP
With the right cloud-native application protection solution, you can operationalize your multi- and hybrid cloud environments in the first 90 days using a CNAPP.
This webinar explores:
- Common cloud security operational challenges and how to overcome them
- How to develop a CNAPP deployment plan for your needs and workflows
- How Tenable Cloud Security can help
Leveraging CNAPP to close the cloud security expertise gap
There are millions of unfilled cybersecurity jobs and that keeps increasing as organizations need cloud-specific security professionals to protect their enterprises.
This webinar explores how to close the expertise gap by:
- Using an identity-first CNAPP for asset discovery, risk analysis and threat detection
- How to quickly and effectively fix vulnerabilities without hiring more staff
- The benefits of automated cloud security
When, why and how your security team needs to harness the power of CNAPP
Many security teams are new to cloud-native application security and the role of a CNAPP in protecting the cloud.
Watch this webinar to learn more about:
- CNAPP fundamentals and architecture
- How CNAPP is different from other security practices
- How to integrate a CNAPP into your existing security frameworks
Develop and strengthen DevSecOps with cloud security as code
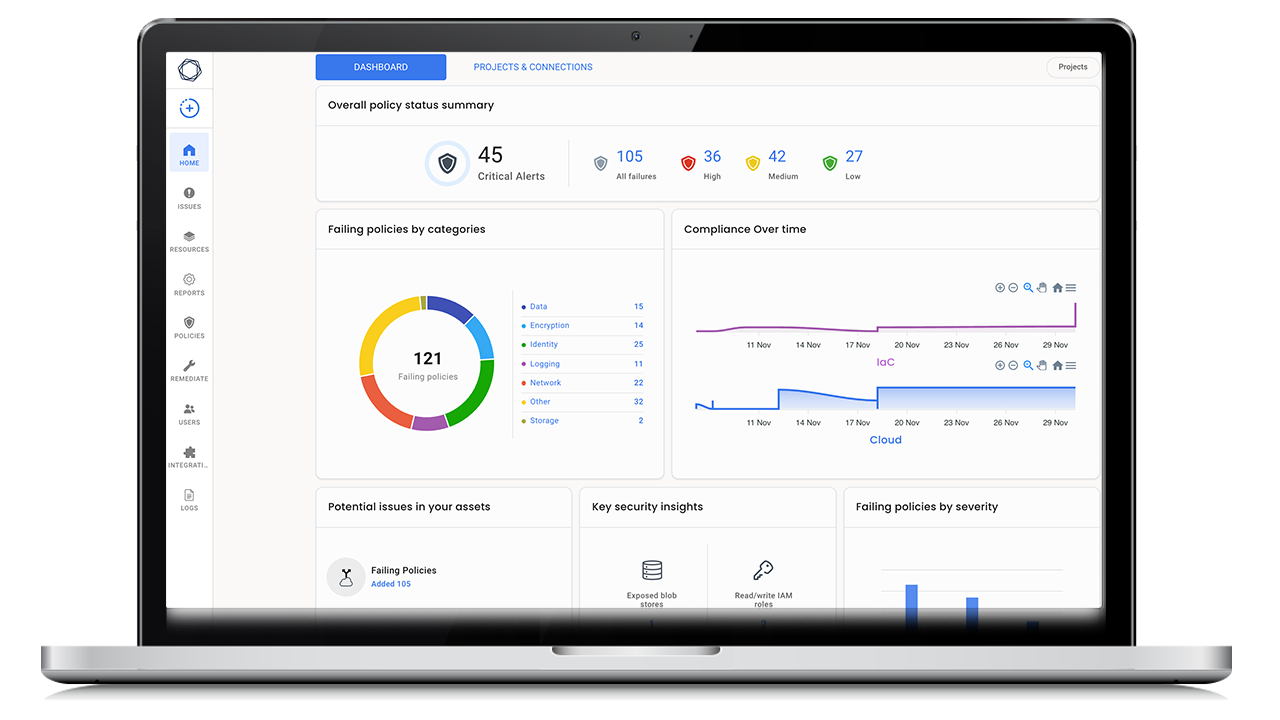
Traditional on-prem security practices leave your cloud attack surface vulnerable to breaches. Tenable’s CNAPP, Tenable Cloud Security, gives you complete cloud visibility so you can continuously discover and assess your cloud-native applications for security issues, all without installing agents or other tedious legacy security processes.
Tenable Cloud Security gives you comprehensive visibility into your cloud-native environment so you can quickly identify and remediate security issues, even as your cloud environment constantly changes. It’s about cloud security from build-time to run-time.
With Tenable Cloud Security, you can mature your cloud-native security practices with:
- Policy as code for continuous assessments
- Governance as code for automated governance
- Drift as code for continuous detection
- Security as code for advanced security
- Remediation as code for automated remediation to find and fix security weaknesses
Try Tenable Cloud Security for free
If your security starts after your teams deploy cloud-native apps, then you’re increasing cyber risk. Proactively protect your cloud by integrating security into your software development lifecycle at every step. Change the way you approach cloud security with Tenable Cloud Security, full-stack cloud-native security, from code to cloud deployment.
- Tenable Cloud Security





