Unlocking Kubernetes Innovation Through Simplified Cloud Security with Tenable

Tenable Cloud Security simplifies Kubernetes security by providing any containerized environment with new features including easy custom policy enforcement, enhanced access control, Helm charts scanning and workload protection. The capabilities offer powerful means for securing your clusters effortlessly, with meaningful, identity-driven insights.
In the fast-evolving landscape of cloud computing, Kubernetes (K8s) has emerged as the de facto standard for orchestrating containerized applications.
For all its capability and flexibility, Kubernetes is a formidable challenge to protect – especially for security practitioners not deeply versed in the technology. Clusters often run the most critical workloads to a company’s business and may also have access to the organization's most sensitive resources including confidential company and customer data. The complexity of Kubernetes, combined with its dynamic and distributed nature, makes it a daunting task to ensure that clusters are secure from threats.
As we make our way this week to KubeCon EMEA in Paris, we’re excited to introduce several powerful features in Tenable Cloud Security that simplify Kubernetes security, enabling organizations to focus on innovation without the burden of becoming Kubernetes security experts.
The new Tenable Cloud Security capabilities include:
- Expanded coverage for securing on-prem and self-managed K8s clusters
- An intuitive, custom admission controller for enforcing policy-as-code, facilitating deployment and management
- Just-in-time access to AWS Elastic Kubernetes Service (Amazon EKS) clusters
- Scanning of Helm charts for K8s misconfigurations
- UI-driven container workload protection (CWP)
Comprehensive support for any Kubernetes environment
One of the most significant barriers to Kubernetes security is the diversity of environments in which clusters can be deployed.
From cloud-managed services like Amazon EKS, Azure Kubernetes Service (AKS) and Google Kubernetes Engine (GKE) to on-premises and privately networked clusters, the variety of environments is vast. Tenable Cloud Security bridges this gap by extending its capabilities to include Kubernetes clusters deployed in cloud environments as well as on-prem. This comprehensive capability enables organizations to maintain visibility and control over their Kubernetes clusters regardless of where they’re deployed. This includes clusters which are configured to have restricted Internet access, are managed on-premises or are self-managed in the cloud (that is, deployed on cloud resources but not via a managed service).
This one-stop shop security-management approach provides a clear and easy way to control your entire Kubernetes inventory across all resource types including workloads, services, clusters and service accounts, as shown below:
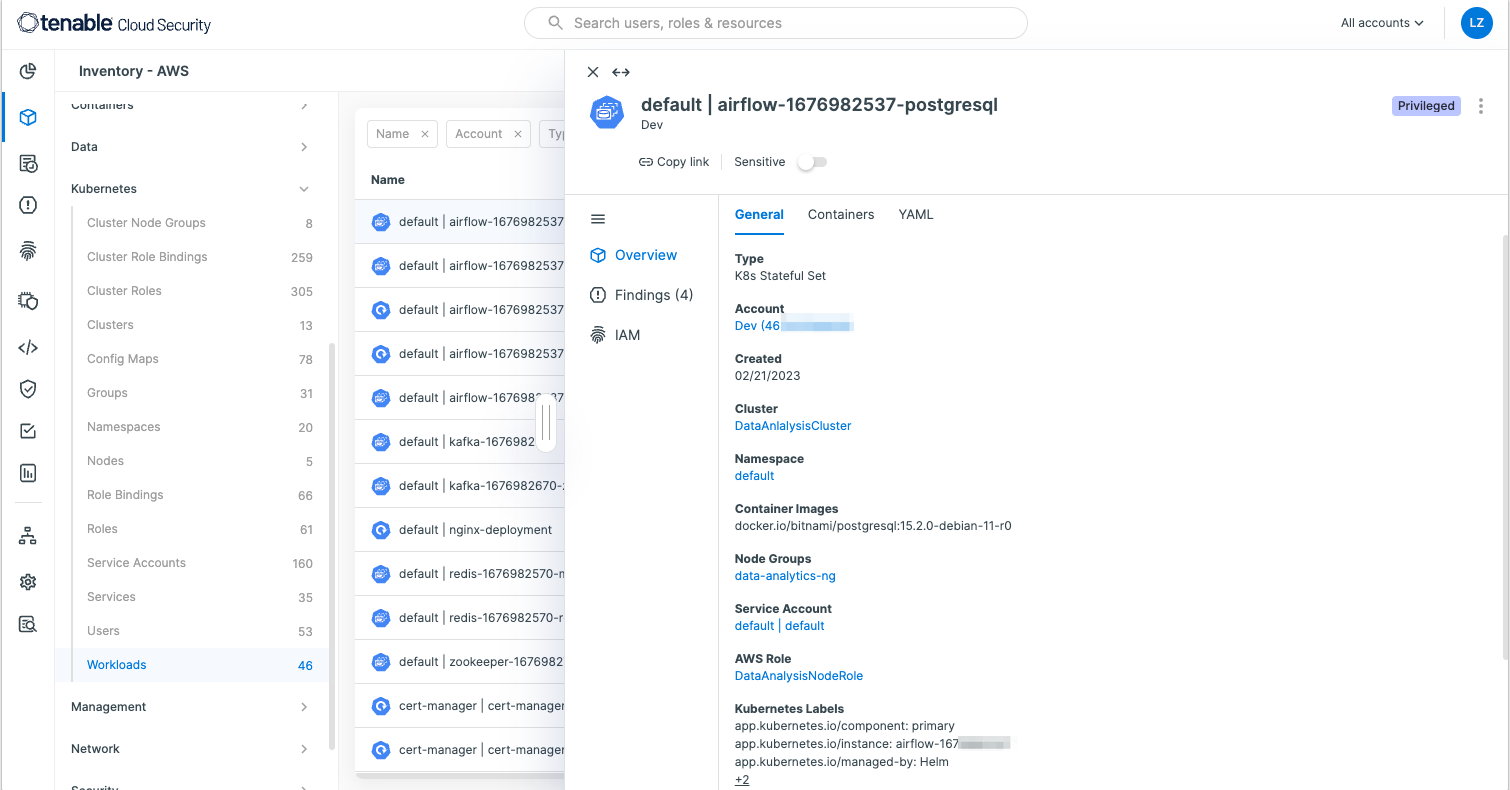
In fact, Tenable Cloud Security provides much more than a straight-up Kubernetes inventory. As a CNAPP solution, it analyzes all components of the cloud infrastructure for misconfigurations, vulnerabilities and permissions risk. For example, it assesses Kubernetes clusters for compliance with popular standards and best practices, such as the Center for Internet Security (CIS) Benchmark for Amazon EKS.
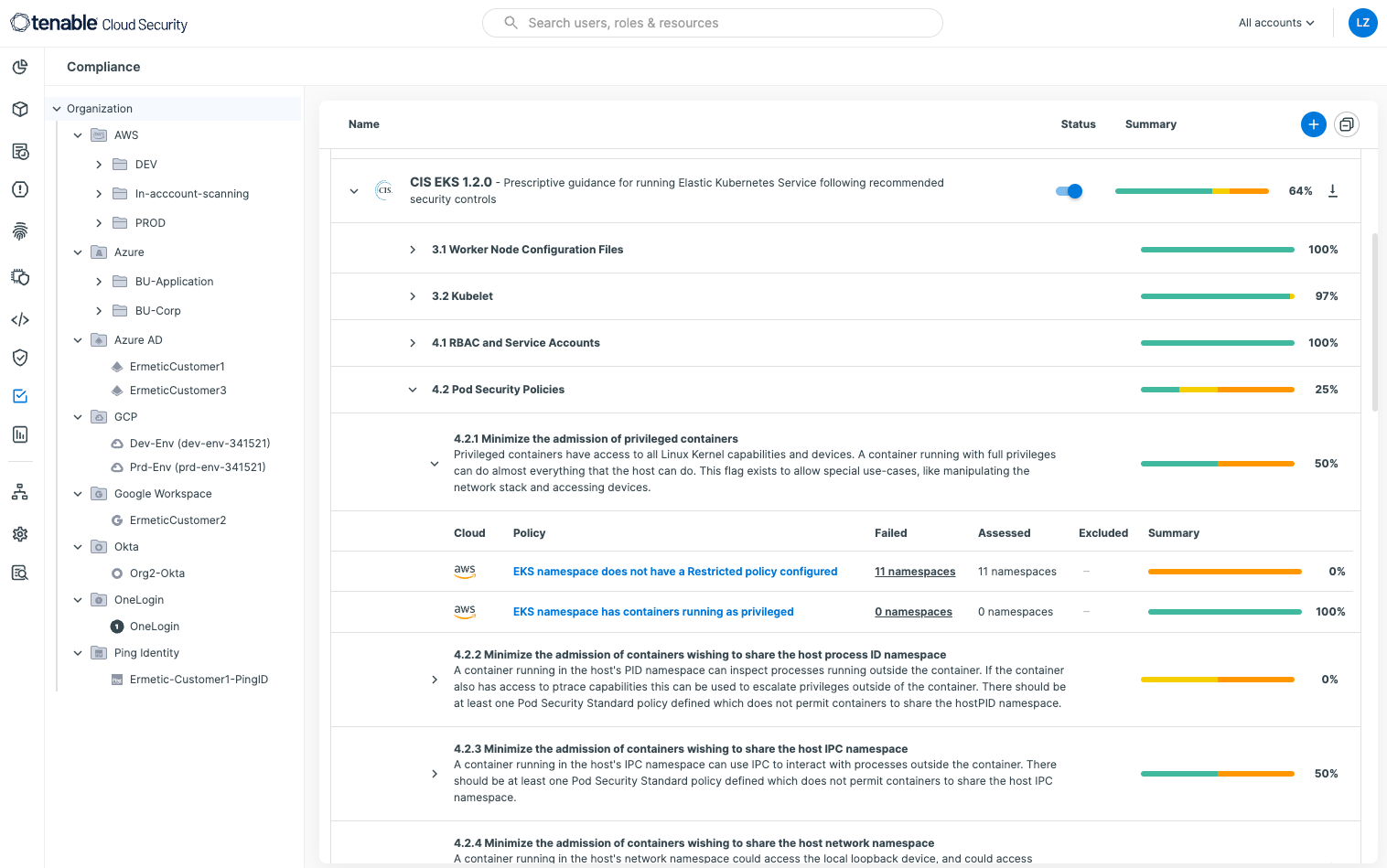
The compliance capability allows you to easily generate reports on how your environment stacks up and determine what actions to take to bridge existing gaps.
Simplifying policy enforcement with custom admission controllers
Kubernetes admission controllers are very effective for implementing "shift left" security by allowing definition of policies as code to be enforced on Kubernetes resources before deployment.
That said, the complexity of deploying an admission controller can be a significant hurdle as its use requires the confidence that security teams will not be blamed if something breaks. Even working with a successful open source implementation such as Gatekeeper can overwhelm experienced practitioners, and slow or stop their use of an admission controller.
Tenable Cloud Security addresses this challenge by introducing an intuitive, easy-to-control user interface for creating and managing a custom admission controller based on Gatekeeper.
This feature empowers security professionals to leverage all the advantages of Gatekeeper with simplicity. It allows organizations to easily enforce their security policies without the need to navigate the technical complexities traditionally associated with admission controllers. By offering a user-friendly way to leverage the powerful Kubernetes admission-control capability, Tenable Cloud Security ensures that security is baked into the deployment process, enabling safer applications from the start.
The administration of the admission controller via Tenable Cloud Security is extremely simple and done by adding policies in the Tenable Cloud Security console:
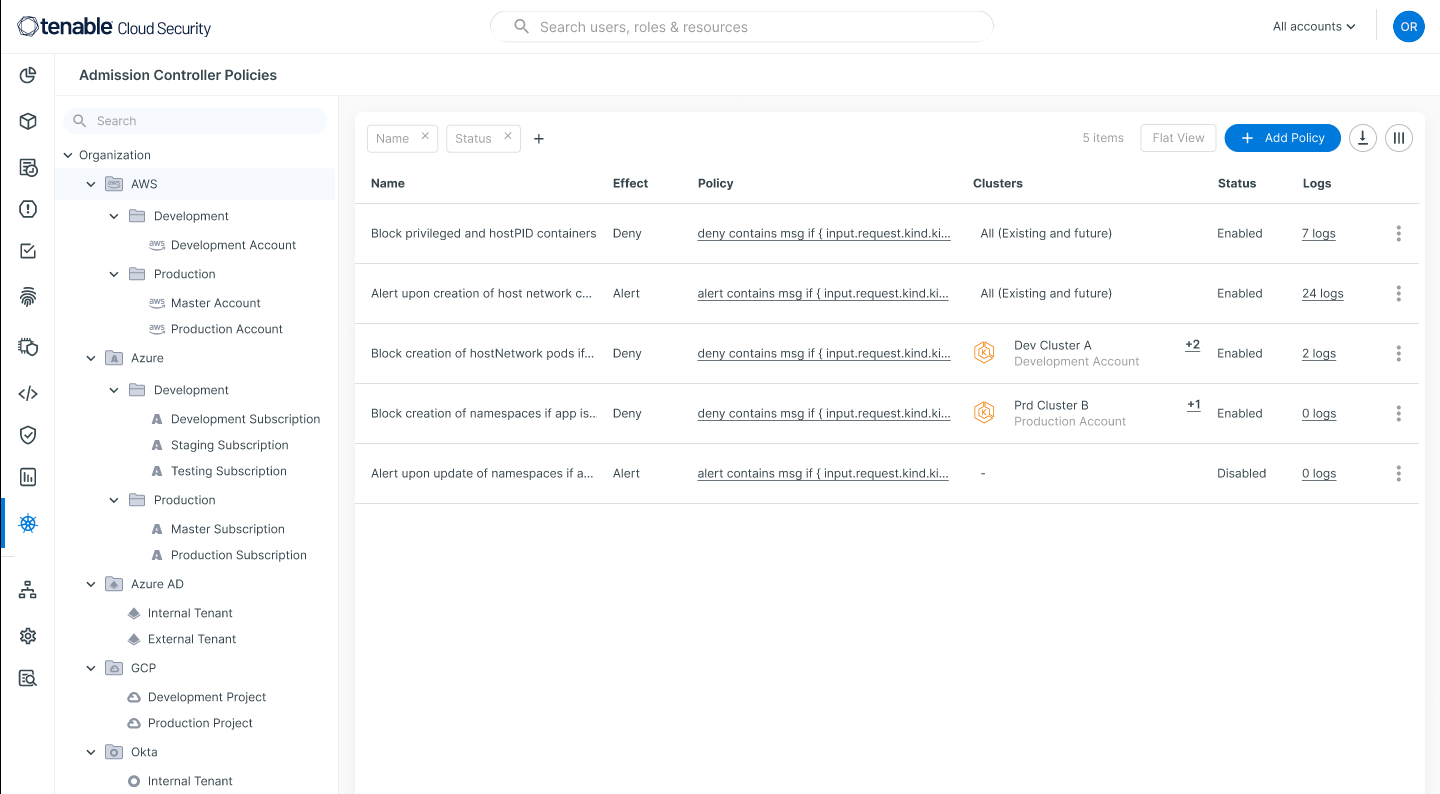
Users can edit policies using Rego expressions or the intuitive Tenable Cloud Security GUI:
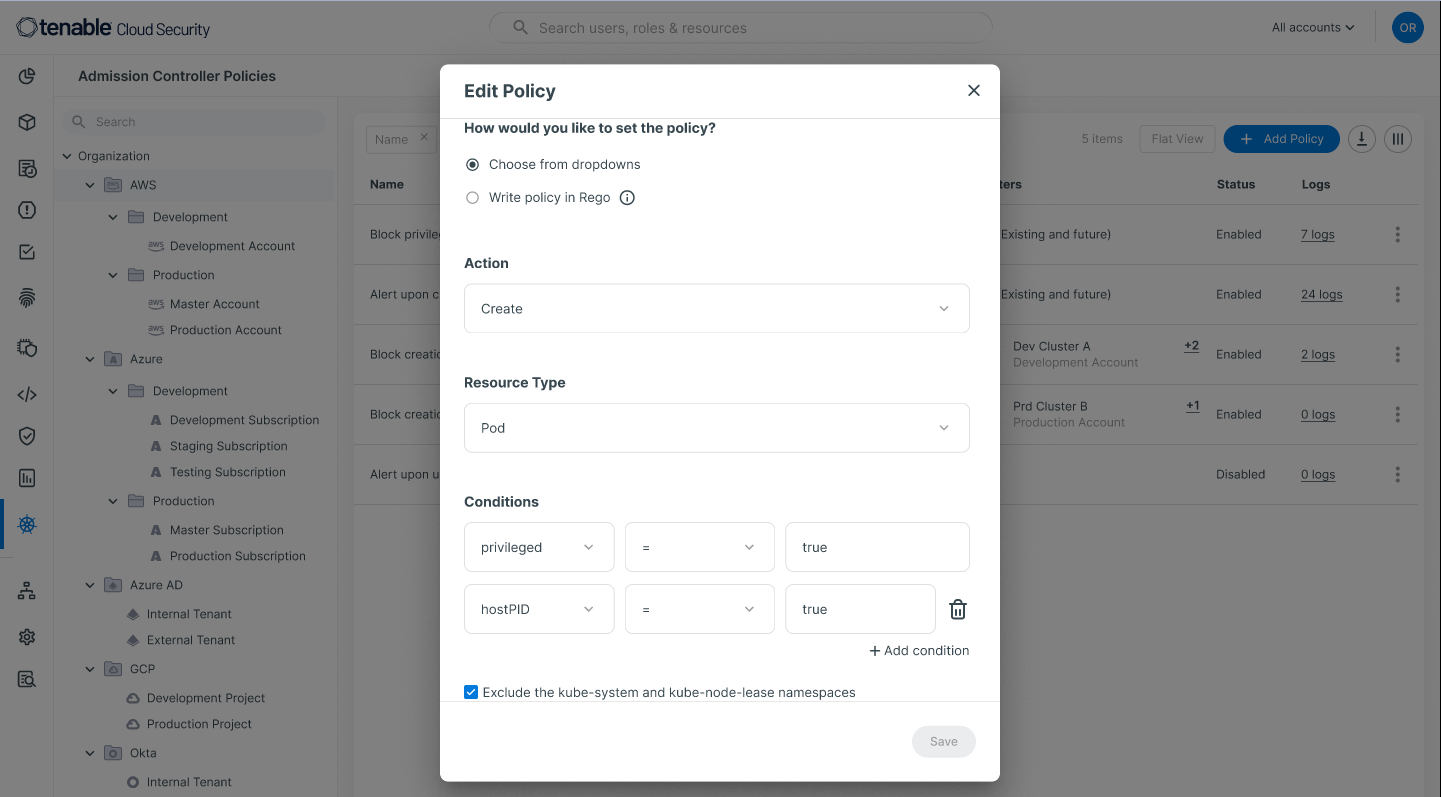
Using an easy-to-consume log created for each policy,Tenable Cloud Security also allows you to audit cases in which the admission controller has prevented deployments:
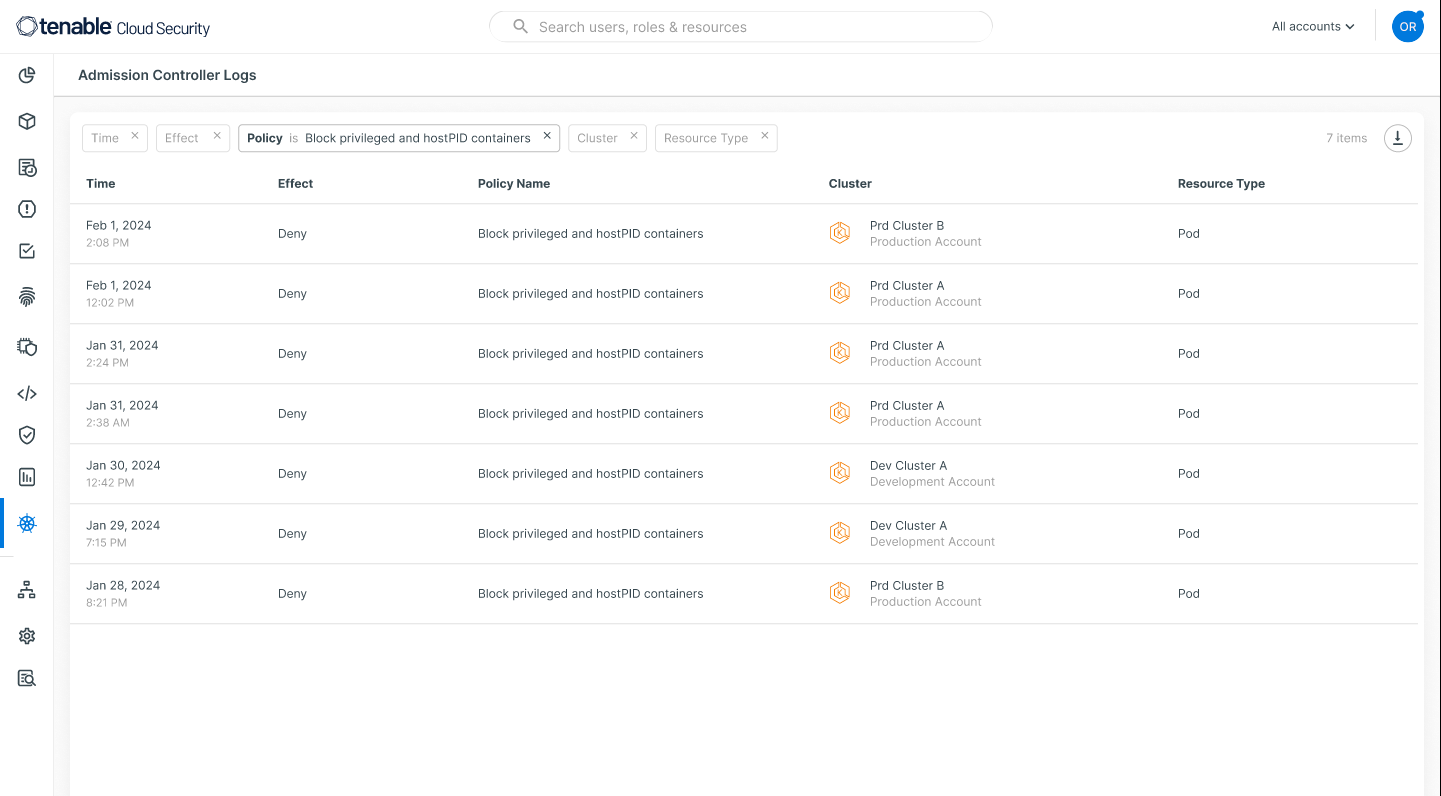
Locking down Amazon EKS cluster access with just-in-time (JIT) control
The recent improvements in Amazon EKS access-management controls have paved the way to provide AWS IAM principals such as IAM users and IAM roles with control-plane access to Amazon EKS clusters. This capability is similar to concepts already seen in Azure and GCP.
The improved AWS controls allow organizations to leverage Tenable Cloud Security’s JIT access management for the control plane of clusters deployed on Amazon EKS. The Tenable JIT mechanism helps customers apply the principle of least privilege by providing minimal standing permissions and granting temporary elevated access requests on a time bound basis according to specific business justifications.
The JIT approach not only enhances security by reducing the attack surface but also offers flexibility and efficiency in managing access to critical resources.
Scanning Helm charts for misconfigurations
Tenable Cloud Security is bringing the shift-left concept of scanning code-provisioning infrastructure to one of the DevOps community’s most popular Kubernetes IaC tools: Helm.
You can now use Tenable Cloud Security to scan Helm charts for misconfigurations before deploying them, as with Terraform or AWS CloudFormation for cloud resources. The capability enables organizations to deploy workloads to Kubernetes clusters with greater confidence.
You can scan Helm charts using the same mechanisms that Tenable Cloud Security uses to scan other types of code for infrastructure such as Terraform: Onboard your code repositories to be scanned periodically by Tenable Cloud Security; embed a call to the Tenable Cloud Security API to upload code for scanning as part of your CI/CD; or use a local scanning agent to detect misconfigurations in Helm code.
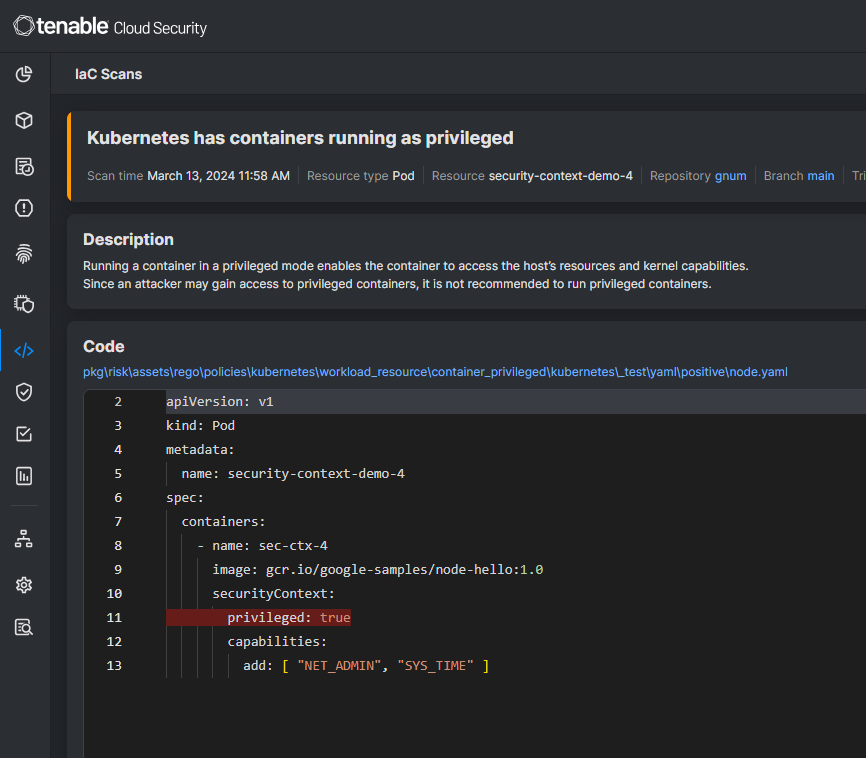
UI-driven workload protection for containerized environments
Last, but definitely not least are our vulnerability-management and malware-detection capabilities, now extended to multiple containerized environments including Kubernetes.
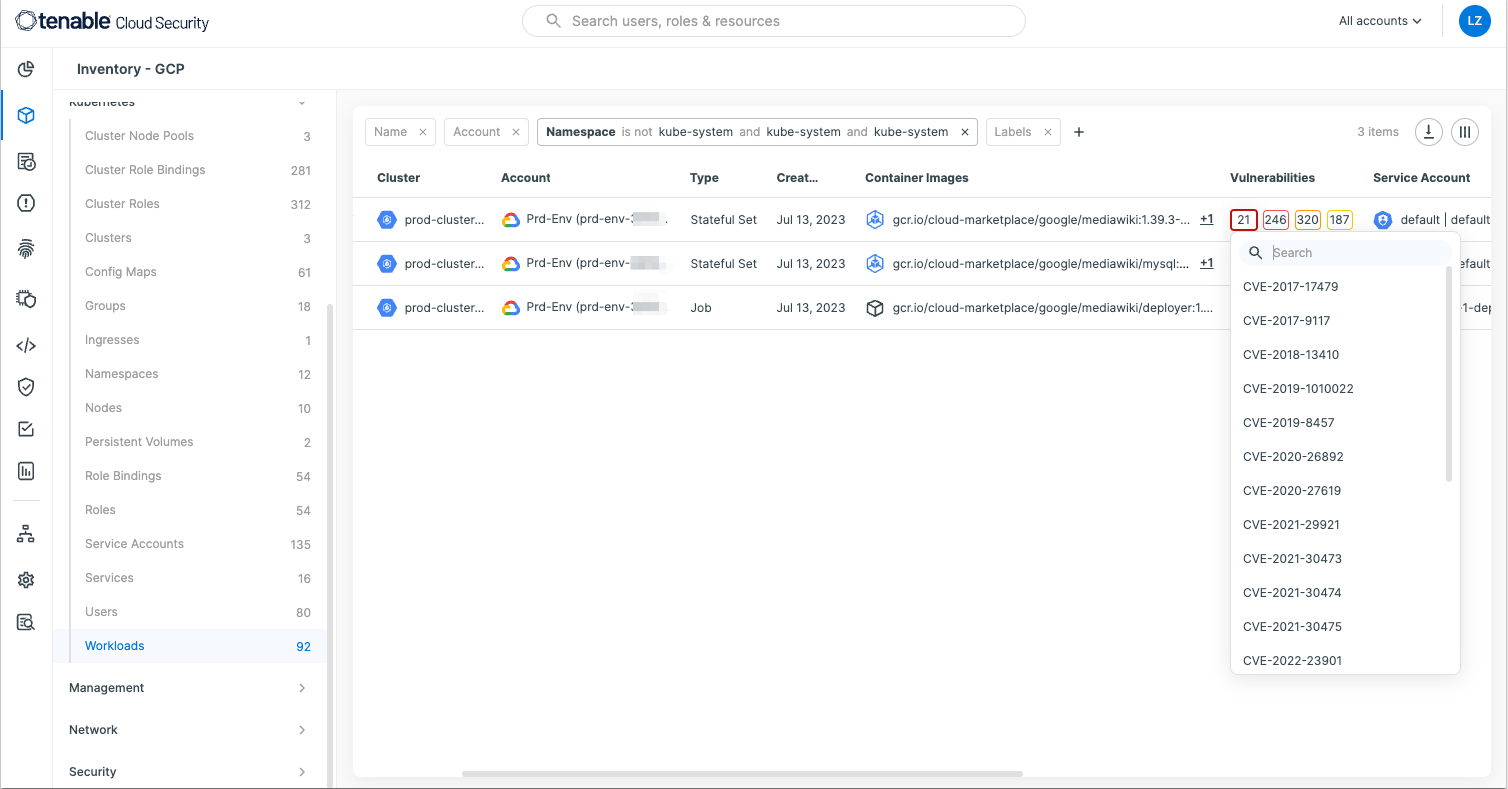
Tenable Cloud Security now detects vulnerabilities in container images and integrates granular information about these findings in the UI presenting the Kubernetes inventory. The solution can:
- detect images deployed to running containers
- scan images in registries before they are deployed
- allow DevSecOps teams to trigger a scan of an image from the CI/CD pipeline, bringing “shift left” to vulnerability management of containers
Tenable’s malware-detection capability also now applies to files included in container images.
These detection capabilities, combined with Tenable Cloud Security’s full visibility into the workload’s identities, access and network configuration, reveal the risks to the workload and the resources within the cluster. You’ll also detect threats arising from the workloads running in your clusters that could impact resources in your cloud environments.
Embrace simplicity in Kubernetes security with Tenable Cloud Security
Kubernetes security doesn't have to be overwhelming. With Tenable Cloud Security's latest features, security practitioners can now effectively manage the security and compliance of their Kubernetes clusters without needing to become experts in the technology.
From comprehensive support for all types of Kubernetes deployments to simplifying policy enforcement and enhancing access controls, Tenable Cloud Security is committed to making Kubernetes security accessible and simply managed. Tenable achieves this by unifying cloud security across workloads, identities, configurations, network, data and more, for both hybrid and public cloud environments.
Don't let Kubernetes security complexity hold back your development team’s innovation. Request a demo of Tenable Cloud Security today and start unlocking the full potential of secure, scalable and simplified container orchestration.
Learn more about the challenges of security in Kubernetes environments in the March edition of the Tenable CloudCover webinar “Kubernetes Confessions: Tune In and Get the Help You Need to Finally Put An End to Those Risky K8s Security Sins” on March 27 at 11 am ET.
- Cloud
- Container security


