The Role of Attack Surface Management (ASM) in Cybersecurity
Why Attack Surface Management is Integral for Your Exposure Management Strategy
Your modern attack surface consists of all the potential points of contact an attacker may attempt to access within your IT environment. Attack surface management (ASM) is a process that enables your organization to get comprehensive visibility automatically and continuously into your assets so you're always aware of what you have, how they're being used and where they may have any vulnerabilities or security issues—from a user and attacker's point of view. Attack surface management enables your security teams to seek out security issues, prioritize remediation, and stay one step ahead of attackers.
In this knowledgebase, we’ll help you better understand the role of attack surface management as a cybersecurity best practice.

Here’s what you’ll discover:
Dealing with Your Attack Surface Beyond Vulnerabilities
Get a more realistic view of your cyber exposures and rethink how you define your attack surface.
Learn MoreAttack Surface Management Frequently Asked Questions
Explore answers to frequently asked questions about attack surface management and its benefits as a cyber strategy.
Learn MoreAttack Surface Management Solutions
Empower your teams to proactively seek out likely attacks with a single, unified view of your attack surface.
Learn MoreTenable Connect community for Attack Surface Management
Tenable Connect is a great place to connect with other security professionals and talk about all things related to ASM.
Learn MoreExposure Management for the Modern Attack Surface
The Tenable One Exposure Management Platform can help you discover all of your assets so you can understand all of your exposures, prioritize which cyber risks mean most to your organization, and prioritize remediation to prevent likely attacks.
Protecting State and Local Governments Against Ransomware
Ransomware attacks are on the rise. Attack methods are more complex, and cybercriminals are more resourceful. No longer are threat actors looking only to gain access to your network through an exploit. Attacks today can spread malware across your entire enterprise. Attackers are banking on that they can move laterally undetected long before you realize they’re there. That’s why your organization needs a strong, proactive cybersecurity defense—especially if you’re a government agency. Any device, application, operating system or network is at risk, and you can’t stop these threats if you don’t know where they are. A proactive defense begins with insight into all of your assets and security weaknesses, so you can predict where you have the greatest cyber exposures and then prioritize how you’ll address them.
With Tenable, you can defend your organization against ransomware attacks by finding and addressing flaws before attackers can access them.
Attack Surface Monitoring Insight
Don’t Ignore Attack Surface Management
As your organization embraces more remote work, distributed computing, IoT deployments and cloud adoption, your attack surface grows. As such, you can no longer ignore attack surface management as part of your exposure management strategy. It’s one of the top six things in cybersecurity that needs your attention today. In this Cybersecurity Snapshot, see what the other five hot topics are and explore why ignoring attack surface management now can leave your organization in peril.
Finding the 'Unknown Unknowns' Across Your Entire Attack Surface
If your organization doesn’t have insight into all of your assets, vulnerabilities, misconfigurations and security issues, you can’t protect them. These “unknown unknowns” often keep security teams awake at night. Without insight into all of your cyber exposures, you’re leaving doors open for attackers to step right through, all while increasing your cyber risks.
These “unknown unknowns” are often hidden in your assets with internet-facing connections. When these assets are in a public space—especially when you don’t know about them—it creates more opportunities for attackers looking for quick and easy exploits.
With an attack surface management strategy, your organization can get to the heart of this issue by continuously scanning and monitoring all of your public-facing assets. With this information, you can have clear visibility into your assets, no matter where they are, turning those unknowns into the known so you can address them.
Tenable Connect community: Your go-to resource for attack surface monitoring
Tenable Connect is a great resource for information about attack surface monitoring. Whether you have questions for other exposure management professionals or you’re looking to take a deeper dive into how Tenable can help you gain more visibility into your attack surface so you can manage it, Tenable Connect is the place to be.
How can we automatically scan all externally facing services on AWS?
We have AWS connector configured, and this shows all our EC2 instances and we're able to use this to scan private instances within our VPC. However, what we'd like to do is automatically scan all public-facing IP addresses in AWS on a continuous basis… Is this possible with Tenable? How do other people monitor the external attack surface?
Read MoreClose your Cyber Exposure Gap and Protect Your Attack Surface
Networks and attack surfaces are changing fast. Today, there’s so much more than servers, network devices and endpoints. Now you’re responsible for securing everything from cloud platforms and application containers to Internet of Things (IoT) devices, and perhaps operational technology (OT) systems. How can you manage it all?
Read MoreCompare Vulnerabilities Between Hosts to Determine Elevated Risk Levels
We have multiple servers going live in our org, and all report multiple informational-level weaknesses. While eliminating each would not be practical, the combination of all weaknesses existing together may allow a bad guy to gather more data of the potential attack surface. I'm looking for a plugin or scan strategy that can identify and report such weaknesses...
Read MoreFrequently Asked Questions About Attack Surface Management
Are you new to attack surface management? Do you have questions, but not sure where to start? This attack surface management FAQ has the basics:
What is an attack surface?
What is attack surface management?
What does attack surface management do?
What is attack surface mapping?
What is external attack surface management (EASM)?
Is external attack surface management (EASM) included in Tenable Attack Surface Management?
Can I use Tenable for attack surface management?
Why is attack surface management important?
What are some attack surface examples?
Can I limit my attack surface?
What’s the difference between an attack surface and an attack vector?
What should an attack surface management solution do?
How can attack surface management help decrease cyber-attacks?
Know Your External Attack Surface
Discover and Assess All of Your Internet-Facing Assets and Connections
Modern attack surfaces are constantly evolving. There are more assets, more services and more applications connected to the internet, inherently creating new risks for your organization. With Tenable Attack Surface Management you can map out all of your internet-facing assets and assess their security posture.
Attack Surface Management Blog Bytes

Dealing with the Attack Surface Beyond Vulnerabilities
Understanding your attack surface is a critical part of being able to measure and prioritize cyber risk. In this blog, explore how Tenable’s data can help you get a more realistic view of all of your cyber exposures and rethink how you define your attack surface.

How to Discover and Continuously Assess Your Entire Attack Surface
Discovery and assessment tools for each asset type across your enterprise play an important role in helping your teams eliminate network blind spots and gaining a better understanding of your attack surface. In this blog, learn more about how you can get a unified view of your attack surface to prioritize remediation.

Protecting the Atomized Attack Surface: Cybersecurity in the New World of Work
Remote workforces and a push to move more business-critical functions into the cloud are increasing cyber exposures for organizations of all sizes. Some organizations may have even put these tools into service without any—or very immature—security controls. In this blog, explore how teams can better work together to protect your enterprise.
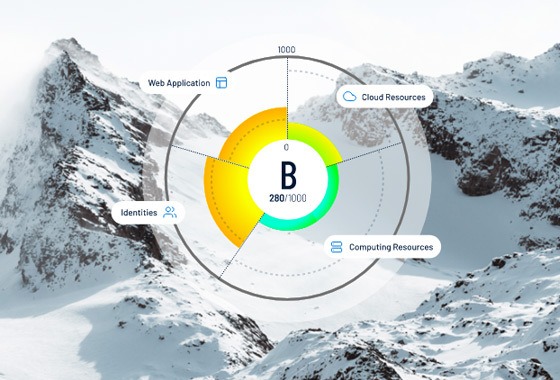
Introducing Tenable One: Industry-First Exposure Management Platform
Tenable One, is an exposure management platform that unifies discovery and visibility into all assets and assesses their exposures and vulnerabilities across your entire attack surface for proactive risk management. In this blog, learn more about how Tenable can help your teams with new capabilities that are foundational for exposure management.
Proactively Address and Manage Cyber Risks with Tenable One
Attack surfaces are rapidly expanding and as such our threat landscape is constantly evolving. Many organizations, especially those who rapidly spun up new technologies and services during the pandemic may not even know about all of the assets across their organization. Some of these tools were put into use with limited security controls, and in worst cases, with no controls at all.
Without insight into your entire attack surface, your organization faces increased cyber risk. So, how do your teams get that insight they need to conduct asset inventories and understand and prioritize vulnerability management for your most critical business services?
Tenable One empowers your security teams to proactively seek out likely attacks with a single, unified view of your attack surface. Within one platform, your teams can see all of your assets and their associated vulnerabilities on-prem and in the cloud. This enables them to better predict the consequences of an attack so they can prioritize remediation with actionable results that meet your organization’s specific needs.
- Quantify your cyber exposure
- Disrupt attack paths
- Eliminate blind spots
- Compare risks internally or externally to guide business decisions
See Tenable One in Action
With Tenable One, your teams can focus efforts on preventing likely cyber-attacks with insight into how you can accurately communicate your organization’s cyber risk for better business performance.
- Tenable Attack Surface Management


