Cloud security overview
Last updated | January 27, 2026 |
Protect data and workloads across AWS, Azure and GCP
Your cloud attack surface is growing faster than you can manually manage, and traditional vulnerability management practices just don’t work for the cloud. This cloud security guide helps you take control. Learn how cloud security tools help you see all your cloud risks, understand what matters and act before risk becomes a breach.
Table of contents
- What is cloud security?
- Why do I need cloud security?
- Why cloud security matters
- The cloud security and traditional cybersecurity difference
- Why is cloud security important?
- How does cloud security work?
- Types of cloud security
- Cloud security best practices
- Cloud-native application protection platforms (CNAPP)
- Vulnerability management in cloud security
- Exposure management in cloud security
- Cloud infrastructure entitlement management (CIEM)
- Just-in-time (JIT) access control
- Least privilege in the cloud
- Zero trust architecture
- Data security posture management (DSPM)
- Kubernetes security posture management (KSPM)
- Container security
- Cloud workload protection (CWP)
- CI/CD pipeline integration and shift-left security
- Cloud detection and response (CDR)
- Misconfigurations in identity and infrastructure
- Cloud security by provider: AWS, Azure and GCP
- Cloud security posture management (CSPM)
- Multi-cloud and hybrid cloud security challenges
- Frequently asked questions about cloud security
- Take control of your cloud security posture
- Cloud security resources
- Cloud security products
What is cloud security?
Cloud security protects the infrastructure, applications and data that power your business in the cloud.
Security in the cloud spans identity management, configuration monitoring, workload protection and risk response across cloud service providers (CSPs) like Microsoft Azure, Amazon Web Services (AWS) and Google Cloud Platform (GCP).
The cloud security definition includes the technologies, policies and controls used to protect cloud-based infrastructure, applications and data from cyber threats.
Why do I need cloud security?
When you adopt a multi-cloud strategy, your attack surface grows. That introduces new risks like over-permissioned identities, misconfigured resources and exposed sensitive data.
A strong cloud security solution continuously evaluates your environment, surfaces the most critical issues and helps your team remediate them fast.
Why cloud security matters
Your cloud attack surface grows with every new workload, account and API. Tenable Cloud Security studies, like the Cloud Risk Report 2024 (analyzing data from January-June 2024), found that:
- 84% of organizations have risky access keys
- 23% of cloud identities have critical or high severity excessive permissions
- 80% of cloud workloads had unremediated critical CVEs, the widespread container escape vulnerability CVE-2024-21626, remaining unaddressed for extended periods
The point? If you don’t have visibility, automation and contextual risk prioritization in place, you’re exposed.
The cloud security and traditional cybersecurity difference
Understanding the role of cloud security in cybersecurity helps clarify why traditional perimeter defenses aren’t enough in cloud-native environments.
Cloud security doesn’t have a fixed perimeter. Instead, you manage risk across dynamic services and infrastructure.
Your cloud provider secures the physical and foundational layers, but you’re responsible for configuring your workloads, identities and access controls. This shared responsibility model in the cloud applies across all major cloud platforms.
Cybersecurity in cloud computing requires understanding which risks you manage versus what your cloud provider covers, especially regarding configurations, access and sensitive data.
Your cloud security platform must account for this complexity and should:
- Unify visibility across accounts
- Integrate with your identity systems
- Monitor data access patterns
- Detect what Tenable calls toxic combinations, like a public workload that connects to sensitive data through an over-privileged identity.
When you identify these risks early, you can fix them before attackers exploit them.
You also need tools that work across your development and production environments.
For example, you can scan infrastructure as code (IaC) for misconfigurations before deployment, and then monitor how those resources behave once they are live. This shift-left approach helps you embed security into your build pipelines from the start.
If you compare the best cloud security platforms, go beyond basic cloud security posture management (CSPM). Look for a solution that combines workload context, identity governance and data sensitivity into a unified view. That’s how you reduce real risk, not just the noise.
Why is cloud security important?
Your organization’s cloud infrastructure evolves faster than traditional IT ever could. So does your risk exposure.
As your teams adopt multi-cloud architectures and shift to cloud-native applications, they create countless public cloud security risks, like misconfigurations, over-permissioned identities and unmonitored workloads.
Your modern cloud protection strategy isn’t about just securing a perimeter. You’re managing thousands of independently deployed services, each with its own privileges, policies and potential for drift.
The scale of this problem is clear in the Tenable Cloud Risk Report 2024.
Analysts found that 45% of cloud assets analyzed had at least one exploitable risk and 97% of organizations had cloud exposure paths that attackers could traverse to reach critical assets.
These aren’t isolated issues. They’re systemic weaknesses that require continuous monitoring and prioritized remediation.
Poorly managed identities also drive risk.
Recent Tenable research in its Cloud Security Risk Report 2025, consistently highlights that overly-permissive defaults, excessive entitlements, and standing permissions granted to cloud identities are a key driver of lateral movement and privilege escalation.
Without context-aware visibility into identity risk, your team can’t reliably enforce least privilege or detect toxic combinations.
Compliance is another key driver.
A strong cloud compliance strategy is essential whether your team is working toward FedRAMP, ISO 27001, or industry-specific standards like HIPAA. Cloud misconfigurations and excessive permissions pose certification risks.
These issues often stem from a lack of continuous security posture management or audit-ready evidence trails.
A robust cloud security platform can help you identify violations early, resolve them quickly and prove compliance during audits.
But this is more than a defense strategy. It’s also an enabler.
With the right cloud risk management tools, you can deploy new services, scale infrastructure and innovate across business units without introducing unmanaged risk.
Tenable supports that approach through its unified platform. Rather than flooding teams with alerts, Tenable Cloud Security maps relationships between assets, users and data to reveal what truly puts your organization at risk.
For example, a public-facing resource with admin permissions and direct access to sensitive storage is critical — and fixable.
Understanding where risk lives in your cloud, and why it matters, helps you shrink your attack surface, accelerate compliance and move with greater agility across AWS, Azure and Google Cloud.
How does cloud security work?
Cloud security starts with agentless scanning, which discovers every asset, like virtual machines, containers, serverless functions, and storage buckets, and validates their configuration against standards.
From there, tools like Tenable Cloud Security continuously assess risk across all layers of your environment.
At the same time, cloud policy enforcement begins in development with IaC.
As developers push Terraform or CloudFormation manifests, integrated scans check for misconfigurations, such as open network rules or overly permissive roles, before deployment. This is an example of shift-left security, where your teams introduce earlier in your software development lifecycle.
Once you run workloads, identity governance kicks in.
Continuous monitoring and cloud infrastructure entitlement management (CIEM) identify unused or excessive privileges. You shrink your attack surface by applying least privilege enforcement and removing stale entitlements.
If systems detect unusual access, like a Lambda function calling a restricted database, they trigger alerts or remove that access dynamically.
If a vulnerability appears, for example, an exposed container image or public API, automated workflows generate remediation code snippets right into your CI/CD pipeline. These snippets, formatted for Terraform or YAML, enable you to resolve the issue in version control and redeploy quickly and consistently.
Cloud environments don’t stop changing.
Exposure management in the cloud helps you see how assets connect through identities and privilege paths. An exposure graph, for example, shows real-time chains attackers could follow, like from an exposed storage bucket through an idle admin key into a database, and highlights where you should break the chain.
Finally, continuous monitoring and detection (CMD) or cloud detection and response (CDR) track suspicious events, such as IAM policy changes, network alterations, or anomalous container behavior, across AWS, Azure, GCP and Kubernetes clusters.
You get detection, prioritized actions and integration with ticketing systems so remediation teams can coordinate fixes fast.
This working model:
- Finds every asset and checks posture via CSPM, Kubernetes security posture management (KSPM), cloud workload protection (CWP)
- Ensures data remains protected through data security posture management (DSPM)
- Controls all identity access via CIEM and just-in-time (JIT) workflows
- Prevents drift using policy-as-code in CI/CD pipelines
- Shows live visibility using exposure mapping and CDR
That unified approach helps you avoid alert storms, focus on what matters and stay agile while meeting compliance needs.
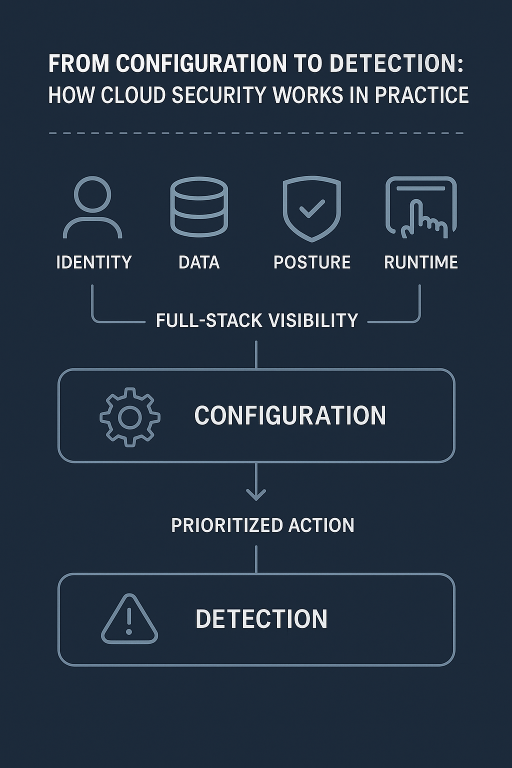
This diagram breaks down how a modern cloud security solution like Tenable connects key layers, identity, data, posture and runtime, to deliver full-stack visibility and prioritized action.
Types of cloud security
Cloud security spans multiple domains, each essential to protecting your cloud environment. These include:
- Infrastructure security, with tools like CSPM, which check your compute, storage and serverless configurations against frameworks like CIS Benchmarks.
- Workload protection, through cloud workload protection platforms (CWPP) that monitor runtime behavior across containers, VMs and functions.
- Kubernetes and container security, combining KSPM and runtime enforcement to secure your clusters and workloads.
- Identity governance, where CIEM, JIT access and least privilege enforcement reduce your blast radius.
- DSPM, which finds and protects sensitive data across services by linking access patterns to exposure risks.
- Network and API security, using segmentation and gateway policies to limit movement and external access.
- Cloud access security brokers (CASBs), which provide visibility into SaaS usage, enforce access policies and prevent data loss across cloud applications.
- CDR, paired with exposure mapping, reveals how misconfigurations, identities and data combine into real attack paths.
Each layer reinforces the others. Together, they form a defense-in-depth model that strengthens your cloud cybersecurity posture across providers.
Explore each domain in detail in our Types of Cloud Security guide.
Cloud security best practices
Now that you know the key types of cloud security, here’s how to implement them.
These cloud security best practices apply across AWS, Azure and GCP and work better when your platform unifies posture, identity and workload visibility.
Use this checklist to guide your next steps and jump to each section for deeper guidance.
Apply these high-impact strategies across your multi-cloud environment:
- Scan for misconfigurations continuously
- Find and fix drift across compute, storage and serverless before it becomes an exposure.
- Enforce least privilege with CIEM and JIT access
- Audit entitlements, remove unused permissions and scope roles dynamically.
- Secure your CI/CD pipelines early
- Shift left by embedding IaC and container scans into your development process.
- Monitor container and workload behavior
- Catch runtime anomalies like privilege escalation or unauthorized movement.
- Map and prioritize exposure paths
- Use exposure graphs to find critical attack chains across identities, workloads and data.
- Protect sensitive data with DSPM
- Discover, classify and restrict access to critical datasets across your cloud.
- Detect and respond in real time
- Integrate cloud-native telemetry and automate remediation workflows.
Cloud-native application protection platforms (CNAPP)
Cloud security isn’t just about finding misconfigurations. It’s about seeing how identity, workloads and data interact across your environment.
That’s where cloud-native application protection platforms (CNAPPs) come in.
Instead of juggling posture, runtime behavior, permissions and data visibility across different tools, CNAPP gives you a single, unified platform. A CNAPP combines CSPM, CWPP, KSPM, CIEM and DSPM into one integrated workflow.
This cloud security platform provides full-lifecycle visibility, so you can manage risk across IaC, runtime activity and identity access.
It helps you:
- Trace container or VM behavior back to misconfigured infrastructure or exposed secrets
- Surface connections between vulnerable workloads and sensitive data
- Prioritize alerts based on real-world exposure, not just static CVEs
If a container image is vulnerable but isolated, you may not need to act. But if that same workload runs with excessive privileges and connects to a production database, you’ve got a critical risk.
A CNAPP tells you why.
The best CNAPPs integrate with your CI/CD pipelines, enforce policy as code and analyze cloud risk through exposure paths, not isolated findings. That means your team sees what matters, where it matters and how to fix it before it becomes a breach.
Best practices for using CNAPP in cloud environments
Protecting your cloud environment takes more than alerting. You need context, control, and a strategy that scales. These best practices help you use CNAPP effectively and reduce real-world risk.
- Scan for misconfigurations across every cloud service.
- Run continuous posture checks across compute, storage, serverless, and Kubernetes.
- Enforce least privilege and remove unused access.
- Use CIEM tools to detect and eliminate permissions that are not in use.
- Watch for combinations of identity, exposure, and data.
- A public-facing workload might seem safe until it connects to sensitive systems through over-permissioned access.
- Catch drift between code and runtime.
- Make sure your live environment matches the policy you defined. If it doesn’t, you may be exposed.
- Build security into your CI/CD pipeline.
- Scan Terraform, YAML, and container images during development. Fix problems before deployment.
- Map attack paths using asset and identity insights.
- Prioritize based on how attackers could move between services, not just based on isolated findings.
- Monitor containers during runtime.
- Look for unusual actions like privilege changes or lateral movement inside your clusters.
- Track who and what can reach sensitive data.
- Data alone is not dangerous. The access path is what turns it into a risk.
- Apply controls as code.
- Define and enforce policy in your codebase to maintain consistent, auditable protections.
- Prioritize context over volume.
- Focus your energy where workload behavior, permissions, and sensitive data overlap.
Vulnerability management in cloud security
Managing vulnerabilities in the cloud requires precise context. Go beyond scanning code to understand where it runs, who accesses it and how it connects to sensitive resources.
Traditional vulnerability scanners won’t catch issues in hostless environments or short-lived containers.
The Tenable Cloud Risk Report 2024 found that 42% of vulnerable workloads existed only during transient periods, evaporating before conventional tools could even scan them.
A strong vulnerability management solution for cloud environments works like this:
- Scan across layers.
- Check running containers, virtual machines, serverless functions and stored IaC files. Flag vulnerable base images or missing patches and tie them to their current runtime environment.
- Add context to risk scoring.
- Cross-reference vulnerability findings with identity and exposure layers. A low-severity CVE becomes high-risk if it affects a workload exposed to the internet and authenticated via an idle high-permission service account.
- Use CI/CD integration.
- Apply fix suggestions and remediation snippets directly into pull requests or pipelines. Developers can fix vulnerabilities before they merge and deploy, supporting shift-left security.
- Automate remediation.
- Generate cloud-native patch snippets like Terraform, ARM templates, and CloudFormation to fix flaws automatically when possible. That cuts remediation time from weeks to hours.
- Prioritize response triage.
- Security teams receive only high-priority alerts, saving focus for the vulnerabilities attackers are most likely to exploit in your live cloud risk management workflow.
This approach prevents undetected vulnerabilities from slipping into production and keeps infrastructure ahead of drift.
Instead of reacting to alerts, your team proactively eliminates risk across container, API and cloud-native contexts, supported by automation and intelligent prioritization.
Want to learn more about vulnerability management in the cloud? Check out this cloud vulnerability management page for a deeper dive.
Exposure management in cloud security
Exposure management reveals how attackers could traverse from one misconfiguration to another via failed controls or insecure entitlements.
The Tenable Cloud Risk Report 2024 shows that 97% of organizations possessed at least one exploitable path, combining internet accessibility with identity privilege and vulnerable workloads.
Here are a few recommendations to apply exposure management best practices to your cloud environments:
- Map your cloud attack surface.
- Identify how resources, identities, data stores, and network routes interact across your cloud environment. This context allows you to pinpoint where risks overlap and where attackers could move laterally.
- Identify toxic combinations.
- Risk isn’t always about a single misstep. A public API might connect to a container that runs outdated code. If that container uses a privileged service account with database access, you’ve created an exposure chain. Managing exposure means spotting these dangerous combinations before attackers exploit them.
- Prioritize what’s exploitable, not what’s noisy.
- Misconfigurations are common. But not all of them matter. Focus your team’s efforts on those that create access pathways to critical data or production systems. Exposure-aware prioritization considers identity scope, data sensitivity, and network reachability, not just alert volume.
- Disrupt exposure paths at the source.
- Eliminate entire chains of risk, not just individual vulnerabilities. That could mean removing unnecessary permissions, isolating workloads, enforcing policy boundaries, or blocking unused access routes. Breaking exposure paths early keeps attackers from chaining low-risk gaps into major breaches.
Read the exposure management in the cloud guide for deeper insight into how exposure management strengthens your cloud security strategy.
Cloud infrastructure entitlement management (CIEM)
Cloud environments grow fast.
As they do, so does the sprawl of human users, service accounts, and third-party roles.
Many of these retain excessive, outdated, or never-used permissions.
CIEM tools continuously audit those entitlements. They flag risky combinations, unused permissions and access that crosses AWS, Azure, GCP and Kubernetes.
For a secure cloud, consider more than just direct access. Imagine a service account in development that has wildcard permissions. If an attacker compromises that account, they could gain access to containers, workloads and production data.
CIEM helps you uncover these indirect paths that create real exposure.
The right CIEM solution supports least privilege enforcement and just-in-time access. By seeing what each identity actually uses, you can set tighter boundaries, revoke unused access and rotate credentials without disruption.
Want to explore specific use cases and tooling? Check out the CIEM page.
Just-in-time (JIT) access control
Even if you properly scope roles, always-on access still creates risk.
In cloud environments, standing privileges become easy targets, especially if users or services retain access they don’t actively use.
JIT reduces that window of opportunity. For debugging, a developer might need admin rights to a staging environment. With JIT, they request access, perform the task and lose those privileges when the session ends. This more effectively enforces least privilege.
You control how access approval, how long it lasts and what conditions it must meet. It also minimizes attack paths by ensuring fewer identities can access sensitive resources at any given time.
To adopt JIT at scale, you need visibility into all entitlements and automation to handle policy enforcement. A strong cloud security platform helps you build these guardrails into your CI/CD workflows and audit trails.
Want to understand how JIT fits into your least privilege strategy better? Read our full guide to just-in-time access.
Least privilege in the cloud
You can’t reduce cloud risk without reducing access. You need least privilege. But it’s hard to do well without automation and visibility, especially across multi-cloud environments.
Least privilege ensures every human or machine identity only has the access it needs.
This can be tough to enforce manually in AWS, Azure, and GCP. As permissions accumulate, even well-intended policies drift out of scope.
CIEM tools help. They analyze real usage and flag unnecessary or risky entitlements. With CIEM and just-in-time (JIT) access workflows, teams can cut excessive privileges, apply role scoping and build tighter infrastructure-as-code controls that align with actual needs.
Zero trust architecture
Zero trust in the cloud means verifying every access request based on identity, context, and risk before granting it.
You can’t assume trust just because something’s inside your perimeter. That perimeter doesn’t exist in the cloud.
Modern cloud environments span multiple virtual private clouds (VPCs), regions and platforms. Without continuous verification, a token from one environment can quietly unlock another.
Enforcing zero trust means having visibility into identities, workloads and their interactions so you can catch suspicious behavior and stop privilege misuse before it escalates.
A strong zero-trust strategy requires dynamic access control, real-time context and workload monitoring.
For example, if a service account starts accessing sensitive resources it’s never touched before, that behavior should trigger inspection or automation, not wait for an alert to escalate.
Want to go deeper? Explore our full guide to zero trust in the cloud and see how it applies in hybrid and multi-cloud environments.
Data security posture management (DSPM)
Your workloads aren’t the only assets attackers want. Sensitive data is often the real target.
DSPM helps you discover, classify and protect that data before it’s exposed.
Your cloud doesn’t just run workloads, it holds data. Often, that includes regulated content like financial data, personal health information (PHI) or intellectual property. Yet, most organizations lack holistic visibility into where this sensitive data lives or how users and systems access it.
DSPM tools scan cloud environments to discover, classify and monitor data. They connect that data to its access pathways, like identities, workloads, APIs, and help prioritize protection based on sensitivity and exposure.
This context helps prioritize cloud data security, so your team can address real cloud risk without wasting time on low-risk alerts.
For instance:
- A developer might back up a production database to an unencrypted storage bucket for testing.
- A workload might request data from a sensitive dataset using an identity with excessive cross-project permissions.
- A misconfigured IAM policy might expose a file share containing customer information.
DSPM quickly surfaces these issues and shows which changes will reduce risk without disrupting service.
It also supports compliance by identifying data classification mismatches and helping you align storage and access controls with standards.
Kubernetes security posture management (KSPM)
Kubernetes gives you massive flexibility, but also adds complexity. Securing clusters means watching how workloads run, how identities behave and how you enforce policies at every layer.
Kubernetes orchestrates containers at scale, but also introduces new configuration and identity risk layers.
Each cluster contains nodes, pods, service accounts, role bindings and network policies. You must manage them all to prevent unauthorized access and lateral movement.
A strong Kubernetes security strategy begins with visibility. You need to understand what you’ve deployed, how it communicates and who has access to control-plane and workload-level resources. That includes human users, CI/CD pipelines and automated services running inside the cluster.
KSPM handles this by continuously monitoring your clusters for misconfigurations and privilege paths.
For example, it can detect:
- Workloads running as root or with privileged containers
- Misused service accounts that access the Kubernetes API with broad permissions
- Insecure role-based access control (RBAC) configurations that allow escalation
- Lack of network segmentation between namespaces
By combining KSPM with workload and identity monitoring, you can enforce least privilege, block dangerous runtime behavior and maintain compliance with frameworks like MITRE ATT&CK for Containers, CNCF security best practices and industry-specific guidelines like NIST 800-190.
Container security
Containers make your cloud workloads fast and portable. But without guardrails, they become easy entry points.
Container security protects workloads throughout their lifecycle, from development to runtime, forming a key layer of cloud workload security alongside CWPP and KSPM strategies.
This security starts with your pipeline. Tools scan Docker files and IaC to catch issues before deployment, like outdated packages, embedded secrets or open ports.
Let’s say your CI/CD pipeline deploys a container built on an outdated Node.js image. That alone isn’t a breach, but if the container also runs with root access and connects to a backend with customer data, you’ve just created a critical exposure chain.
Once workloads are live, continuous monitoring takes over.
You can detect unauthorized file changes, suspicious process behavior, or lateral movement attempts.
And because containerized environments change fast, real-time visibility is key. Drift happens quickly, especially when multiple orchestrators like Kubernetes and ECS are involved.
Container security works best tied into your broader cloud risk management strategy. It helps enforce least privilege, validates configuration against compliance frameworks and flags workloads that act outside their intended scope.
Explore our container security guide to see how to reduce runtime risk without slowing development.
Cloud workload protection (CWP)
A cloud workload protection platform (CWPP) protects the workloads already running in your cloud environments. It focuses on live behavior, not just static scan results.
CWP catches threats as they happen, based on how workloads interact with identities, networks and data.
A container might pass all your security checks during deployment. But once it starts running, it can access internal storage or encrypt files, which can be a problem.
CWPP sees that behavior, flags it and gives your team context to act fast.
It works by enforcing policies, watching for threats like privilege escalation or unexpected file access and showing how a single vulnerability could lead to something worse.
Use CWPP to prioritize what matters, respond to runtime attacks and strengthen the rest of your cloud risk strategy.
CI/CD pipeline integration and shift-left security
Shift-left security strengthens your cloud defenses by catching issues earlier. It integrates directly into CI/CD pipelines to scan IaC, container images and cloud configurations during development.
Security tools scan Terraform, CloudFormation and Kubernetes manifests during pull requests or builds. They flag risks such as:
- Overly broad IAM roles
- Open ports or insecure network settings
- Vulnerable base images
- Drift between intended policy and actual behavior
Instead of waiting for runtime alerts, developers receive instant feedback. Fix suggestions appear directly in version control to resolve issues quickly and accurately. This speeds up remediation and keeps infrastructure aligned with internal policies and external frameworks.
Effective shift-left security includes:
- Continuous infrastructure as code scanning
- Code-based fix recommendations
- Policy enforcement through Git-based workflows
- Drift detection across development and production
- Contextual risk scoring that reflects real-world exposure
Explore our shift-left security and CI/CD integration guide to see how it works in real environments.
Cloud detection and response (CDR)
Some security information and event management (SIEM) tools fall short in the cloud because they originated for on-prem environments. They miss critical cloud-native behaviors, especially when threats cross services, identities and workloads.
That’s where cloud detection and response comes in.
CDR tools monitor cloud activity for signs of compromise, lateral movement, privilege escalation and data theft. They ingest logs from cloud providers, runtime signals and identity activity. Then they correlate those signals to find real threats.
A strong CDR platform connects context to detection. Instead of isolated alerts, it shows you what happened, why it matters, and how to respond.
For example, your team might surface:
- A service account accessing unusual resources
- A workload making unauthorized API calls across cloud accounts
- A pattern of changes that mirrors known attack techniques
The best CDR tools show you how each detection links to identity, asset exposure or configuration risk. It helps you respond with context.
You can also trigger actions like revoking credentials, isolating a resource, or reversing a change.
Integrations with systems such as Jira, ServiceNow, Slack and cloud-native remediation tools make this fast and repeatable.
CDR also supports investigation. You can review logs, trace actions and build identity timelines to understand the full scope of an incident. That helps your team learn from each event and document it for audits or compliance.
Misconfigurations in identity and infrastructure
Most cloud attacks don’t start with malware. They begin with misconfigurations. These overlooked settings grant excessive access, expose workloads or turn off logging. They may seem harmless individually. But when combined, they form the attack paths adversaries look for.
Identity and infrastructure misconfigurations are among the most common risks in the cloud. An identity and access management (IAM) role might access storage, compute and third-party systems without proper oversight.
A workload may have an internet exposure with no runtime protection. These conditions create openings for lateral movement and data compromise.
Continuous monitoring across IaC and deployed resources is essential, including:
- Overly broad roles or unused credentials
- Public-facing workloads linked to sensitive systems
- Unrestricted firewall rules or misused service accounts
- Missing encryption or disabled audit logs
- Trust relationships that span accounts or projects
These risks are dangerous when they intersect. Picture a virtual machine with a public IP address. That might seem low priority. But if that instance uses a role with elevated access and no logging, it creates a clear path to compromise.
Misconfigurations often combine in ways standard tools miss.
To learn more, explore our guide about cloud misconfiguration detection and remediation.
Cloud security by provider: AWS, Azure and GCP
Securing cloud environments starts with understanding how each provider works. AWS, GCP and Azure all follow the shared responsibility model, but their tooling, identity models and configuration defaults vary in important ways.
What seems like a minor setting in one platform can become a serious exposure in another.
For example, AWS IAM roles often cause trouble when policies allow actions or when you don’t manage trust relationships.
In Azure, risks tend to involve overly broad access across subscriptions or missing network security group (NSG) rules.
GCP frequently introduces complexity through service account sprawl and non-tightly scoped cross-project access.
Managing these differences manually leads to fragmented policies, blind spots and missed exposures.
A unified cloud security solution helps normalize findings across providers, enforce consistent policies and prioritize issues based on risks.
For an in-depth CNAPP platform comparison, check out our complete guide to cloud security by provider.
Cloud security posture management (CSPM)
Cloud environments evolve constantly. New services spin up, permissions change and workloads shift across regions and accounts.
Without centralized visibility, it’s difficult to know whether your infrastructure remains secure and compliant over time.
CSPM addresses this challenge by continuously auditing your cloud configuration against security and compliance policies. It monitors for misconfigurations, drift and noncompliant assets across services like compute, storage, networking and identity.
But effective CSPM does more than flag misconfigurations. It should also link posture violations to identity access and data sensitivity.
CSPM also supports policy-as-code. Your team can define and enforce configuration baselines in code and then validate during deployment and runtime. It prevents noncompliant changes from entering production and ensures every cloud asset stays within acceptable boundaries.
Multi-cloud and hybrid cloud security challenges
Multi-cloud and hybrid environments increase complexity for security teams.
Each provider uses its own identity models, policy engines and configuration defaults.
On-prem systems often add another layer of siloed tools, logs and controls.
The result? Fragmented visibility, inconsistent policies and exposure gaps attackers can exploit.
These challenges slow detection and response. When identity logs live in one dashboard, posture findings in another and workload events elsewhere, correlating issues takes too long. And that’s assuming teams even catch them.
Visibility is the core challenge. Without it, you will struggle to answer basic questions like:
- Who has access to what across clouds and accounts?
- Are configurations consistent across platforms and regions?
- Where do cloud identities cross boundaries or carry unused privileges?
Effective cloud risk management requires normalization across environments. That includes scanning IaC before deployment, applying policy-as-code across providers and using exposure-aware tools that connect configuration drift, identity risk and runtime behavior.
Hybrid cloud compliance brings its pressure.
Frameworks like ISO/IEC 27001, FedRAMP and NIST 800-53 require proof of consistent access control, encryption and audit logging, regardless of where a service runs. That means you need visibility into cloud and on-prem systems that connect.
Explore our guide to multi-cloud and hybrid cloud security to see how connected insights improve security and compliance readiness.
Frequently asked questions about cloud security
What is cloud security in cybersecurity?
Cloud computing security includes the policies, technologies and processes that protect cloud infrastructure, applications and data from threats across platforms like AWS, Azure and Google Cloud. It covers everything from misconfiguration management and access control to runtime protection and vulnerability management.
Why is cloud security important?
Cloud infrastructure introduces new risks like ephemeral workloads, decentralized identity and fast-changing services. Without visibility and control, attackers exploit misconfigurations and over-permissioned roles. Strong cloud security helps teams prevent breaches, enforce compliance and maintain uptime across distributed systems.
What are examples of cloud security risks?
Common cloud risks include:
- Publicly accessible storage buckets
- IAM roles with excessive permissions
- Inactive but credentialed service accounts
- Containers running with escalated privileges
- Cross-cloud trust relationships without proper boundaries
Tenable surfaces and prioritizes these risks with real-time misconfiguration detection and identity risk analysis.
Which services fall under cloud security?
- Real-time risk assessment across AWS, Azure and GCP
- Role and policy analysis
- CIEM for entitlement and identity control
- Image and container scanning in CI/CD pipelines
- Compliance reporting aligned to frameworks like SOC 2, ISO 27001 and FedRAMP
What are the biggest cloud security challenges?
Top cloud security challenges include:
- Lack of unified visibility across multi-cloud deployments
- Unused or excessive permissions that attackers exploit
- Drift between intended and actual infrastructure configurations
- Shadow IT and unmanaged assets
- Compliance enforcement in fast-changing environments
What is the average salary for a cloud security professional?
Cloud security engineers in the U.S. typically earn $140,000-$180,000, while architects and DevSecOps leads can earn $170,000-$220,000 depending on experience, location and platform expertise. Skills in Kubernetes, CNAPP and CIEM drive higher compensation.
Take control of your cloud security posture
Your cloud environment won’t slow down and neither will your risk.
Misconfigurations, over-permissioned identities and vulnerable workloads create fast-moving exposure paths across multi-cloud infrastructure. Security teams need visibility and control.
Tenable delivers that control through an integrated platform built for cloud-native environments. Tenable Cloud Security connects misconfiguration data, identity risk and workload behavior into a single context, so your teams respond based on actual cloud exposure.
Whether building a shift-left strategy, preparing for compliance audits, or untangling IAM complexity, Tenable helps you see what’s at risk and act.
Cloud security resources
Cloud security products
Cybersecurity news you can use
- Tenable Cloud Security
