The S4 SCADA Security Conference
This year I was asked to come speak at S4, a conference hosted by Digital Bond every January for the past 14 years. I was scheduled to speak on the OTDay, a free day for conference attendees intended to:
"Like it or not, your critical infrastructure SCADA or DCS is running a mission critical IT network. It is time to learn how to apply the mission critical IT technology and practices to Operations Technology (OT)."
My talk, given once in the morning and once in the afternoon to a full room of folks, was titled "Tiptoe Through The Network: Practical Vulnerability Assessments in Control Systems Environments". It covered three primary areas:
- Discovery - Finding the assets on your network can be tricky, especially if you are a large organization with 10,000 or more hosts. However, in a control systems environment different segments may have a very small amount of hosts and devices, which means a new host is not a frequently occurring activity. This means being able to passively monitor the network for new hosts is important. Of course when we think of control systems environments there are concerns with network disruption (exp. on the PLCs). I covered P0f, Bro IDS, Tenable's Passive Scanner for tools. For methods of host discovery I also mentioned the ability of Nessus to pull hosts from VMware APIs and logs using Tenable's LCE.
- Vulnerability Management - Many have seen the slides on this one as part of the Vulnerabilities Exposed Webcast Series. I cover what you need to get a successful program started, including policies, procedures and scan schedules/strategies.
- Passive Vulnerability Scanning - Very much of interest to the ICS crowd! I stepped outside the boundaries and used examples such as Tivo, Nest, Wifi Treadmills and Wifi Scales as examples of how PVS can detect vulnerabilities.
The ICS Village
I got to have some fun in the ICS Village, a network of control systems, firewalls and security appliances setup for attendees to scan and hack. I ran Nessus against the entire environment (with some help from fellow Tenable employees). We generated over a gigabit of traffic on the wireless network in just over an hour, and all of my scans completed without errors. It was really a testament to how a well-tuned Nessus scan can accurately and quickly enumerate vulnerabilities. Below are some examples from the scan data:
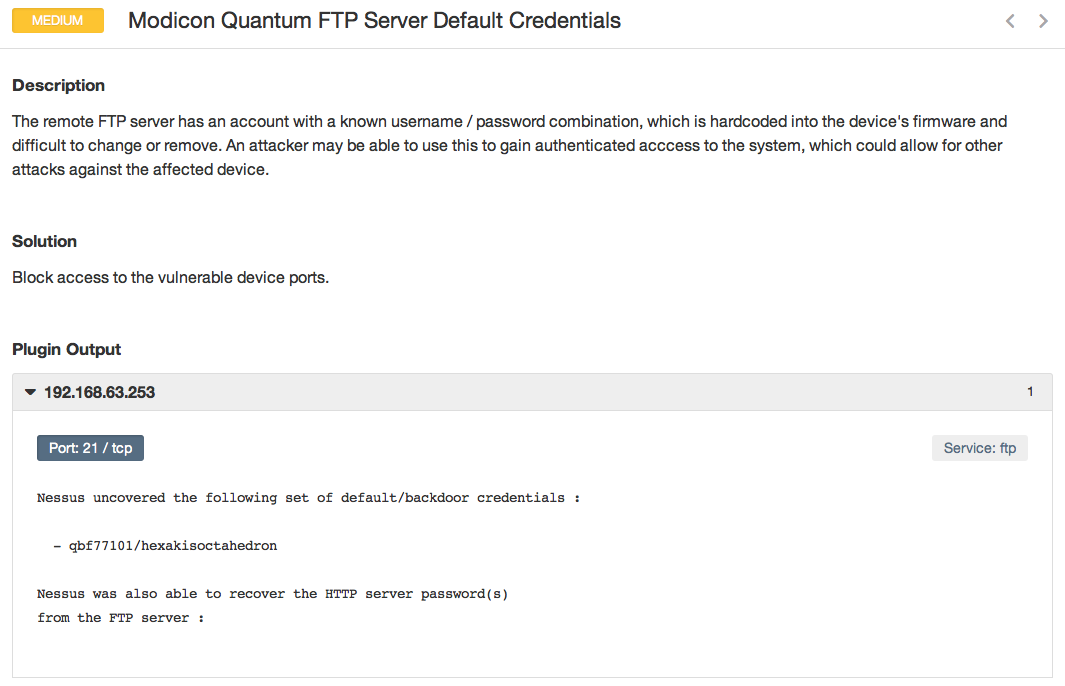
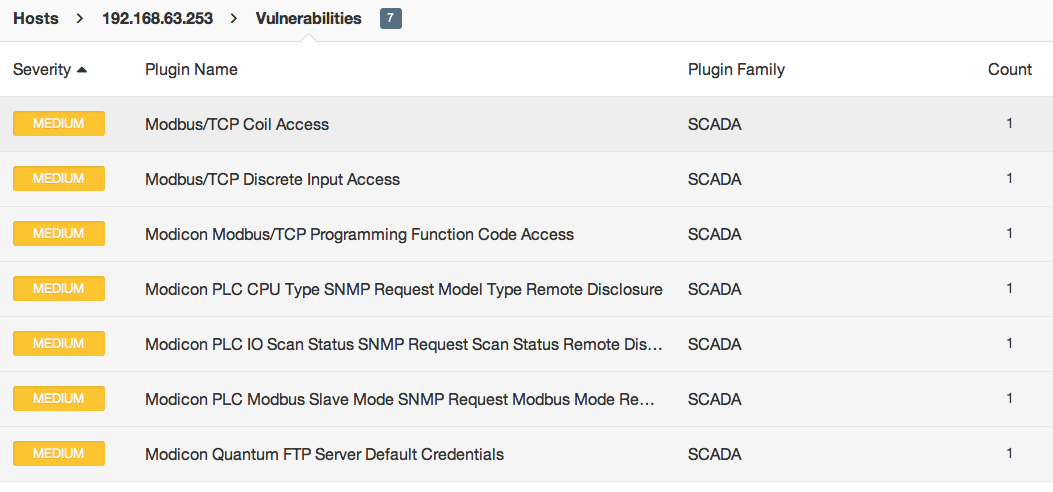
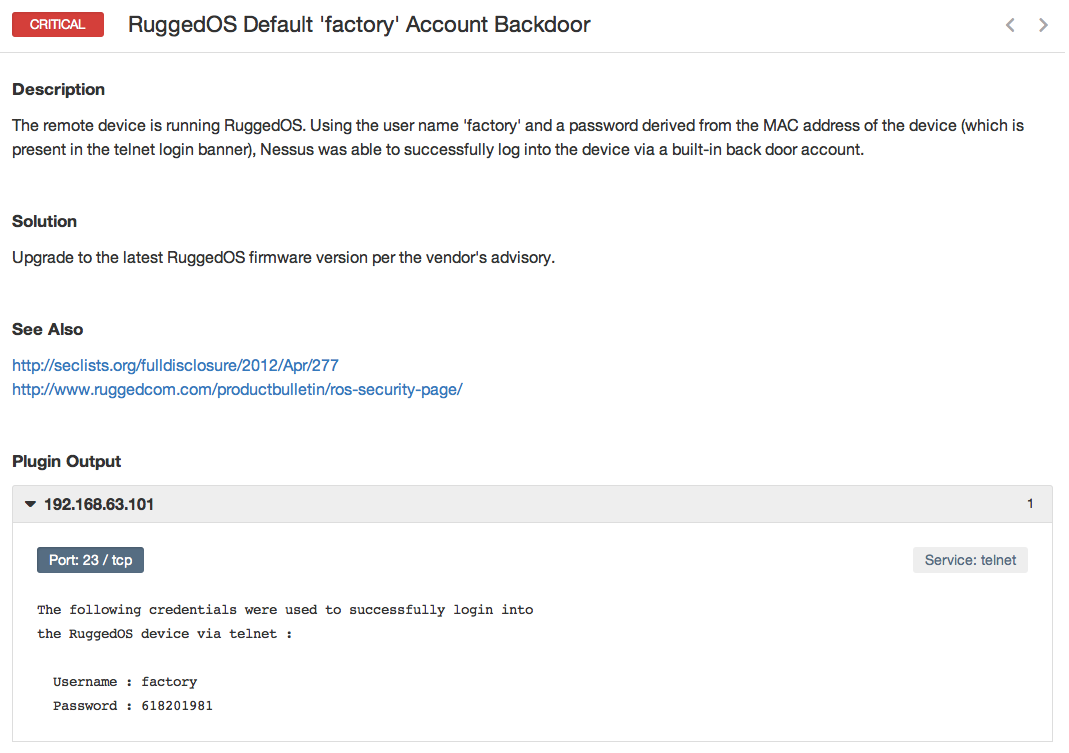
Conclusion
S4 was a great conference and a good opportunity for people to learn about ICS security topics. The OTDay was followed by two days of in-depth technical content. If you are interested in how Tenable's products can detect SCADA related vulnerabilities, please refer to our SCADA solutions page.
- Conferences
- Nessus
- Plugins
- SCADA

