The Future of Cloud Access Management: How Tenable Cloud Security Redefines Just-in-Time Access

Traditional approaches to cloud access rely on static, permanent permissions that are often overprivileged. Learn how just-in-time access completely changes the game.
The access challenge in modern cloud environments
As cloud adoption accelerates, organizations are grappling with a fundamental security challenge: How do you grant people the access they need — such as on-call developers needing to debug problems, site reliability engineers (SREs) needing to repair issues with infrastructure, or DevOps engineers needing to provision or architect resources — without opening the door to overprivileged accounts and breach risks?
Traditional approaches rely heavily on static, permanent permissions. Human users often receive more access than necessary simply because it’s hard to predict specifically which permissions they’ll need. These permissions rarely get revoked, leaving organizations exposed.
This is where Tenable Cloud Security changes the game. As a powerful cloud-native application protection platform (CNAPP) solution, Tenable Cloud Security doesn't just identify access-related risk — it actively helps you solve it.
In this blog, we explore how you can address the excessive permissions challenge using the just-in-time (JIT) access capability in Tenable Cloud Security.
Just-in-time access: The elegant solution to human identity risk
JIT access enables organizations to dramatically reduce their exposure from compromised identities by providing a substitute for permanent access. Instead of being granted standing access, which may be exploited if and when an identity is compromised, users are provided with the eligibility to request temporary access based on a defined business need.
Here’s how it works:
- All (or at the very least sensitive) standing access is removed.
- Users are assigned eligibility profiles for specific resources or roles.
- Users request access and are optionally required to provide a reason when access is needed.
- If required, the request can be approved by an assigned approver or simply be automatically granted, which still has a huge security benefit compared to a standing permission.
- For highly sensitive cases where more than one person needs to confirm access, several approval levels can be enforced if necessary.
- Access is granted for a limited time (measured in hours), then automatically revoked.
JIT access dramatically reduces the attack surface tied to human identities, ensuring that elevated privileges are used only when necessary and only for as long as needed.
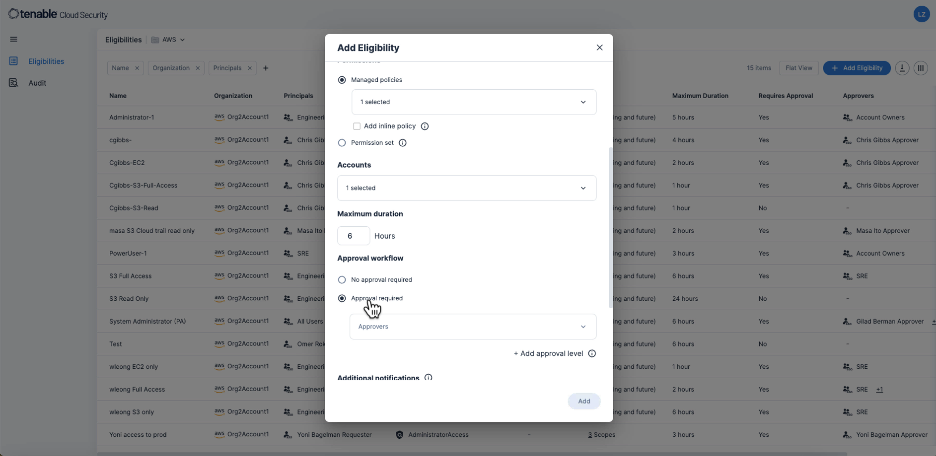
User experience: Where security meets usability
Tenable understands that even the best security solution won't succeed without adoption and cooperation from its target audience. That’s why JIT access in Tenable Cloud Security is designed with a seamless user experience in mind.
Access requests and approvals can be managed directly within messaging platforms, such as Slack or Microsoft Teams, which meet your teams where they are. Users and approvers stay in their native workflows while benefiting from a secure, auditable process.
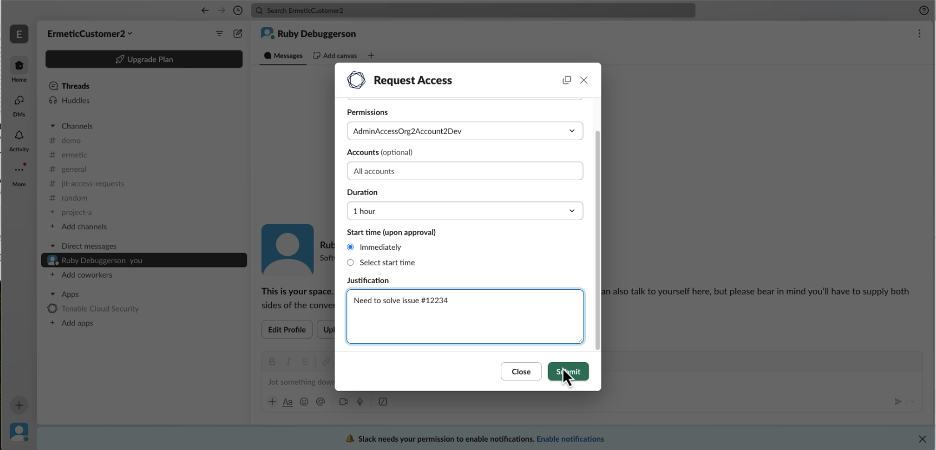
Fig. 3, below, shows how the request, approval and access link are all grouped together on the same thread for a simplified, clean and simple experience.
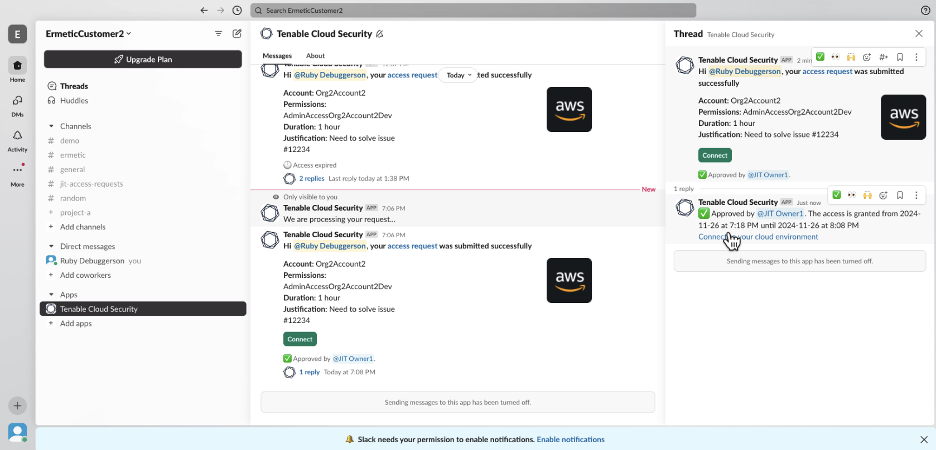
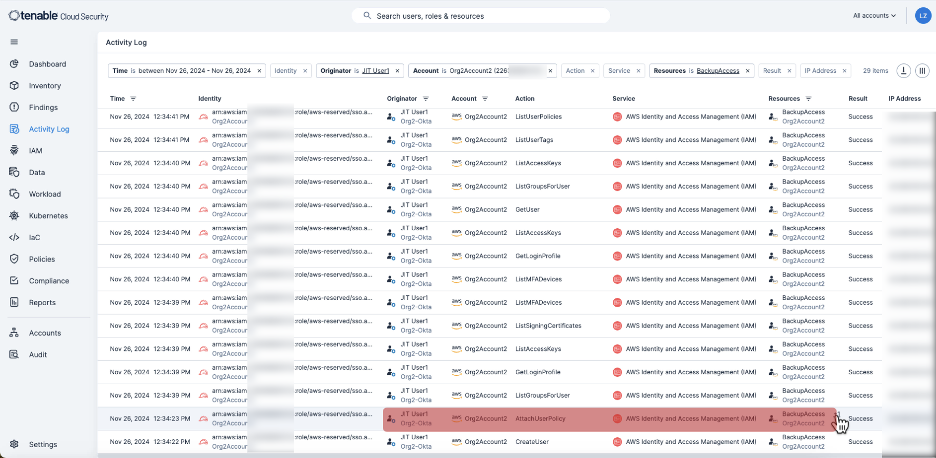
And speaking of audits, Tenable Cloud Security doesn’t just log access. It provides a clean, intuitive activity log interface for every session. Unlike the often fragmented logs from cloud providers, these are tailored for easy auditing, compliance review or incident response. So, if you want to apply more scrutiny and review what happened during sessions, or if you are compelled to do so in the event of an incident, it’s extremely easy to open up the session log and review it.
Expanding the reach: JIT access in Tenable Cloud Security now extends to SaaS applications
Based on customer feedback, Tenable extended JIT functionality to cover identity provider (IdP) group memberships. This is a big deal.
In many organizations, access to software as a service (SaaS) applications (such as secrets managers, observability tools, ticketing platforms, etc.) is governed through group memberships in identity providers like Okta or Microsoft Entra ID. With Tenable Cloud Security, you can now provide temporary group membership through the same JIT access model — effectively controlling and auditing access to SaaS apps with the same granularity and automation as cloud resources.
This means Tenable Cloud Security customers now have unified control over cloud infrastructure and SaaS access through a single solution.
Simplified procurement: JIT access is now included with Tenable Cloud Security
Perhaps the most exciting news: JIT access no longer requires a separate purchase. As of today, it’s included with Tenable Cloud Security.
Billing is simple. Just as Tenable Cloud Security charges based on the number of cloud resources, JIT access treats each eligible user as a billable resource. If you're a Tenable Cloud Security customer, you already have access to the full power of JIT — no separate contract, no additional platform. For example, if you have a team of five developers eligible to request elevated permissions, these would count as an additional five billable resources, no matter how many eligibilities they have.
Why JIT access makes Tenable Cloud Security the CNAPP of choice
Tenable Cloud Security doesn’t just identify problems. It solves them:
- It prioritizes identity risks with real-world context.
- It provides granular, real-time controls for both service and human identities.
- It offers native integration with your daily collaboration tools.
- It simplifies auditability and incident response.
- It extends protection beyond the cloud to the SaaS layer.
- It streamlines adoption with an intuitive UX and frictionless billing model.
Conclusion: Access management, reimagined
The best security tools blend into your workflow and quietly eliminate risk before it becomes a problem.
Tenable Cloud Security's JIT access capability is more than a feature — it's a philosophy shift. It reduces identity-based risk without sacrificing agility. It simplifies compliance without adding overhead. And it empowers teams to move fast, stay secure and maintain clarity over who has access to what, when and why.
If you're already a Tenable Cloud Security customer, there’s never been a better time to start using JIT access. And if you're evaluating CNAPPs, ask yourself: do they help you fix the problem, or just show you where it is?
With Tenable Cloud Security, the answer is clear.
Visit https://www.tenable.com/announcements/provide-access-just-in-time to learn more about how JIT access capabilities in Tenable Cloud Security can help you reduce your exposures.
- Cloud


