Salesforce Service Monitoring with SecurityCenter Continuous View
Note: Tenable SecurityCenter is now Tenable.sc. To learn more about this application and its latest capabilities, visit the Tenable.sc web page.
Salesforce is one of the most prevalent SaaS applications in business, running sales operations platforms for organizations to gain productivity and efficiency, and to enable better communication. With so much critical business happening inside Salesforce, what would happen if someone compromised it or exported your sales data? How would you even know it happened? How well do you trust your administrators?
SecurityCenter Continuous View™ (SecurityCenter CV™) now has the ability to connect directly to Salesforce, via RESTful API and collect activity logs so that you can monitor what users are doing inside Salesforce, as well as detect any changes they are making to accounts, permissions, and system configuration.
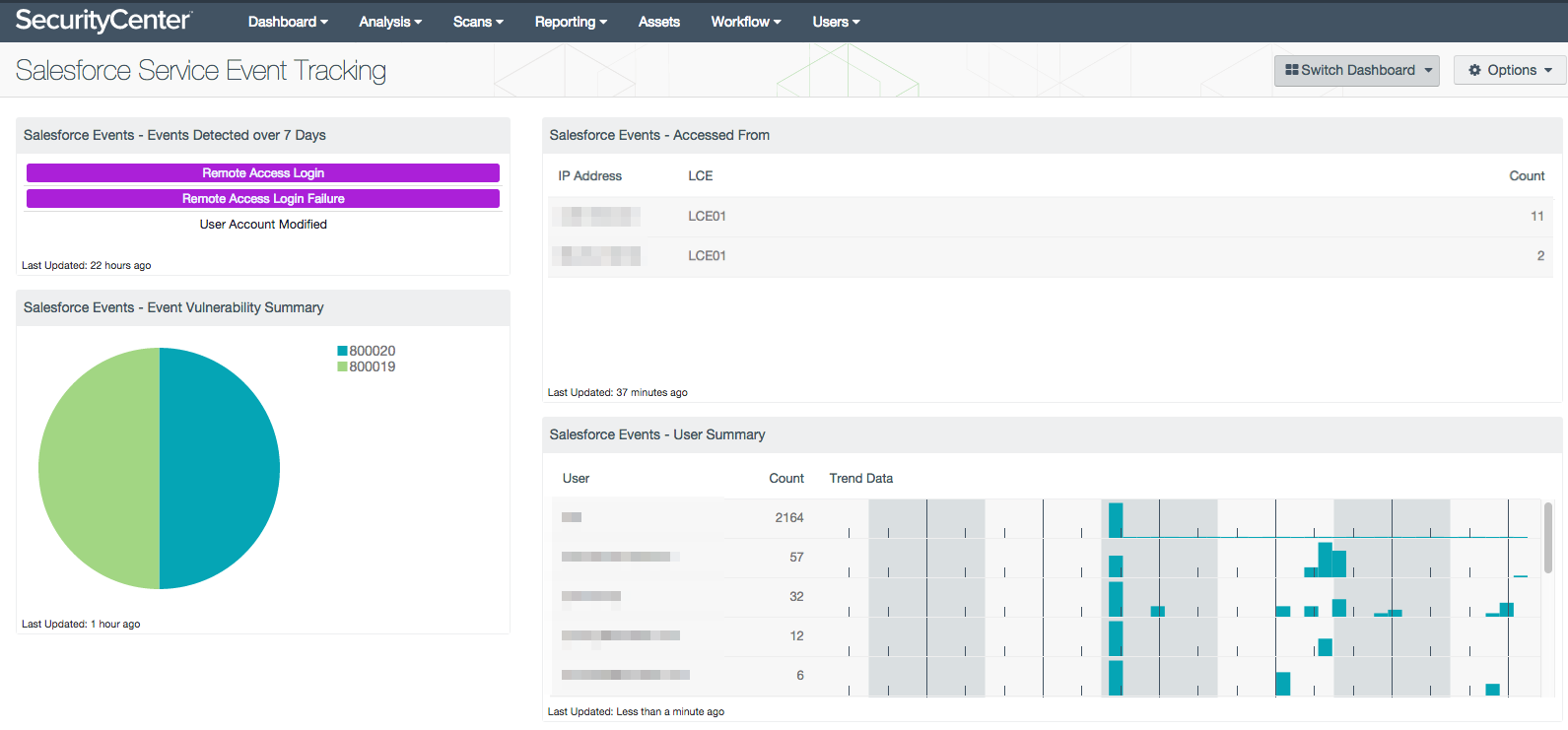
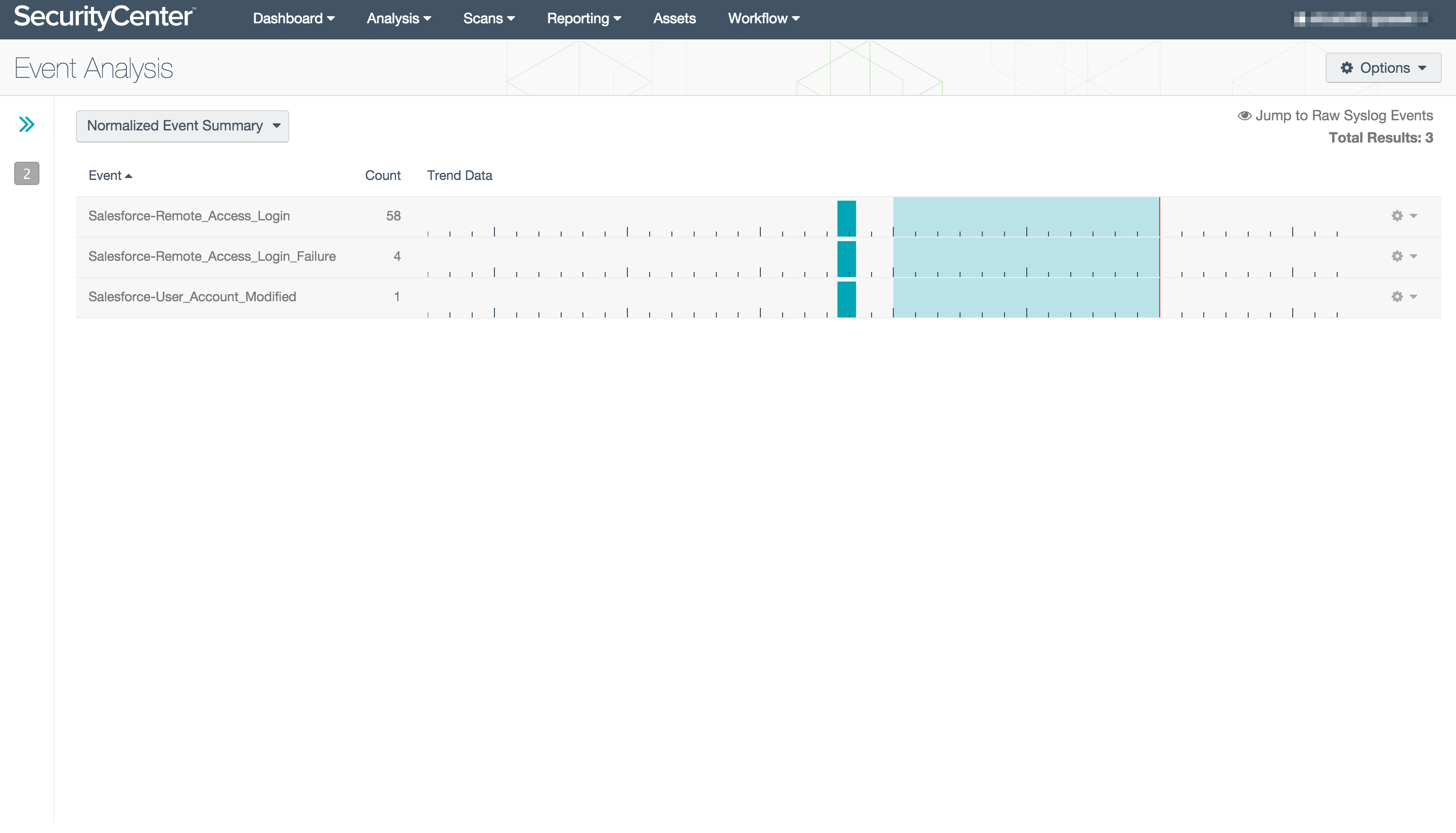
Salesforce event monitoring enables you to see at a glance who is accessing Salesforce, and who is making changes.
In the broader context of your security program, you can see Salesforce events alongside other account modifications and drill down into users who might be misusing administrative permissions network-wide. Access failures in Salesforce will correlate with the rest of your account monitoring, to indicate brute force or password guessing attempts, as well as successful access post-attack. Threatlist events monitor any known bad traffic accessing your Salesforce instance, as well as users originating from hostile IP addresses.
Salesforce events merge into “detected-change” alerts, as SecurityCenter CV tracks account activity across your organization. Users who have never accessed Salesforce before, or who are accessing from a previously unknown IP are pulled out as “New_User_Source” and “New_User_Destination” events, providing visibility into these unusual connections. Deviations from normal Salesforce activity are also captured, sending those events up through SecurityCenter CV and feeding further alerting as indicators of suspicious behavior.
Salesforce is one of the first cloud platforms supported by SecurityCenter CV for API monitoring and is an example of Tenable’s commitment to increasing visibility across organizations’ IT infrastructures and assets; whether they are physical, virtual, or in the cloud.
Consult the Tenable documentation for more information on how to integrate Salesforce monitoring into your security program.
See Auditing a Salesforce.com Account with Nessus for more information on securing Salesforce with Tenable.
- Cloud
- SecurityCenter