Is the Passive Vulnerability Scanner an Intrusion Detection System?
When I was at RSA earlier this year, I gave a variety of media interviews and product demos about Tenable solutions. I demonstrated Nessus detecting malicious processes and the Passive Vulnerability Scanner (PVS) providing an audit trail of all network activity that led up to the infection. I also showed how the Log Correlation Engine (LCE) correlated PVS logged DNS queries to known botnets.
After these demos, I was often asked, “so, is this an IDS?” In one interview (and I hope they print this) I responded by saying that at Tenable, we focus on compromise detection as part of our continuous vulnerability analysis. As the leading vulnerability management vendor in the market, I really tried to emphasize the point that looking for vulnerabilities and configuration issues in known software is just as important as looking for malicious software and malicious users.
Detecting a compromised system is very different from detecting a system that is under attack. Most intrusion detection systems detect attacks and not actual compromises. Tenable’s approach of monitoring files, system settings, logs, application processes and network traffic as part of our continuous vulnerability detection is an excellent platform to hunt malware, compromised system accounts, and botnets.
Below is an example screen shot of an “indicators” dashboard that shows a wide variety of passive and active attack and compromise data in realtime:
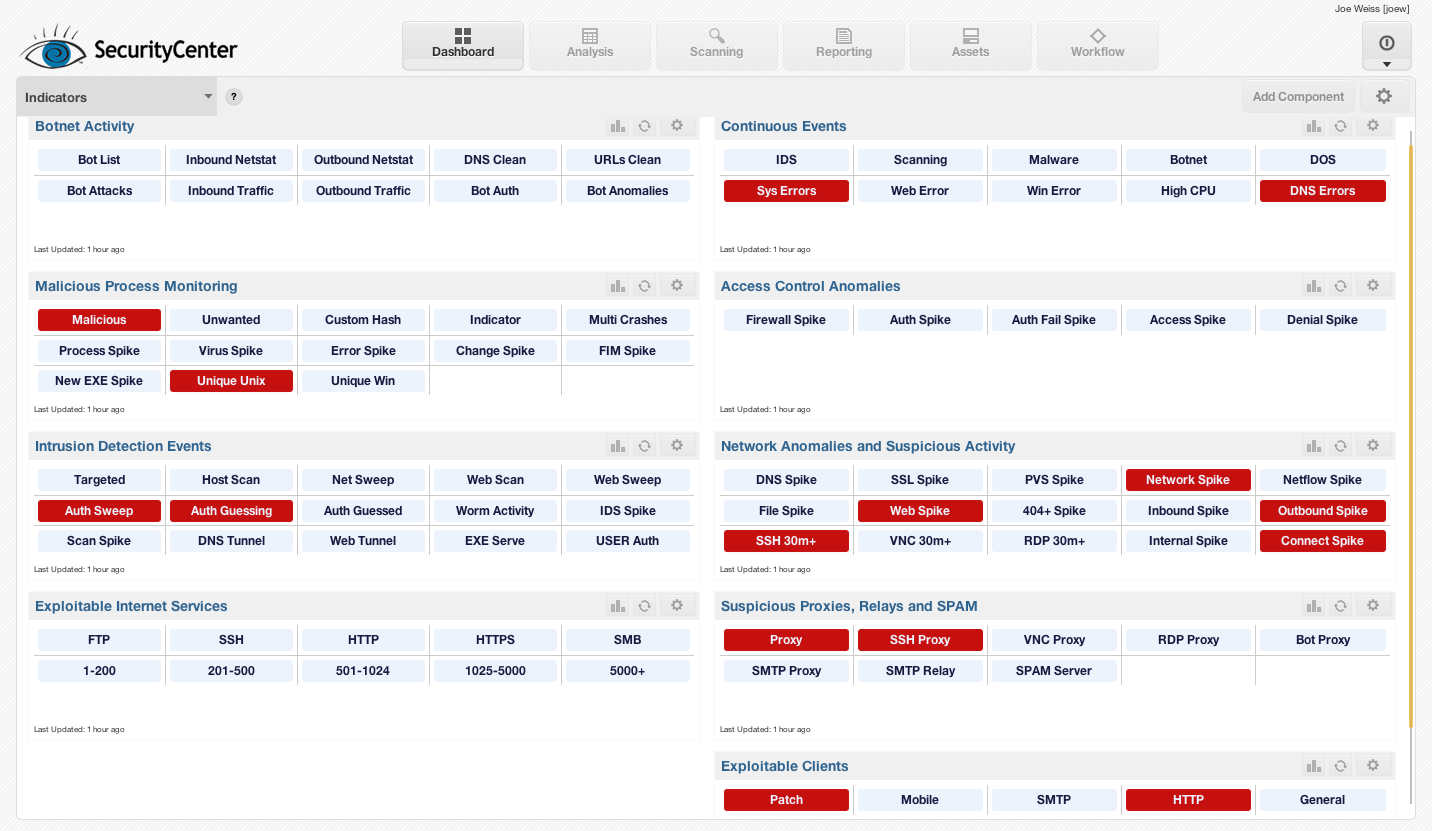
The Passive Vulnerability Scanner is not a network intrusion detection system. It does not have a list of common or recently discovered attack patterns nor does it identify probes and scans. Instead, the focus is to audit your network in real-time. PVS creates two types of data:
- A real-time report of all mobile, IPv4, and IPv6 vulnerabilities, open ports, browsed ports, boundary traversing and applications as if you had Nessus running in real time with full credentials on every system on your network.
- A real-time log of all network traffic that is like an enhanced version of NetFlow that logs artifacts such as SSL certificate names, shared Windows files names, queried domain names, and browsed HTTP web sites.
The passive vulnerability data is useful for auditing activity on the network and identifying systems with applications and network connectivity that is suspicious including:
- Comparing all Internet browsing and served ports. While this does not detect attacks that occur 100% over common streams of network traffic, such as HTTP, attacks that communicate on “uncommon” ports such as IRC, DNS, or high ports, are readily identified regardless if they are client or server based.
- New web sites hosted on existing web servers. I’ve personally worked with organizations that have detected malware and compromised web servers by detecting new web sites being added to their Apache and Windows services.
- Auditing the web user-agents in use. While it is more than possible for malware to perfectly emulate Firefox and other common browsers, there is a large amount of malware that claims to be something that is still readily identified. PVS logs all user agent strings observed for each host in one spot making this audit very easy to report against.
- Identifying unique client-side network activity. PVS logs all client-side network application usage such as SNMP, NFS, FTP, IRC, and Telnet. In environments where there is infrequent usage of these protocols, this activity is an indicator of suspicious activity.
- Identifying unique network services. PVS also logs all services running on every port. Regardless if a compromised system implements port knocking or only accepts connections from known hostile IP addresses, PVS will log the service. For example, if a system was compromised and an intruder placed a web server on port 31000 that only answered to IP addresses from a network block in China or Mississippi, PVS would report an HTTP speaking protocol there.
- Identifying the active DNS server in use. Often, compromised systems will leverage DNS servers external to the organization. This can be done through direct re-configuration of the underlying operating system or simply performing DNS queries to known DNS servers.
- Changes in trust relationships. PVS keeps track of which clients connect to which servers and on which ports. Dramatic changes in client-server trust counts on different ports can indicate worms, scanning and manual probing.
As an example, below is a screenshot of a web server found on port 2869 by the PVS:
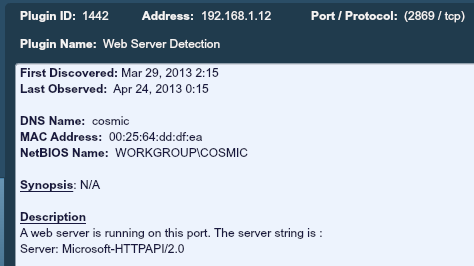
There are many other “passive vulnerability” items detected by PVS that indicate compromise that are too numerous to identify and list here. Many of the customers and users of the PVS I speak with tell me they identify malware, infected systems, and software installed by intruders with PVS because something stood out from the other systems that were passively profiled.
Below is an example screen shot of a dashboard that shows real-time network activity based on SSL, VNC, RDP and SSH traffic.
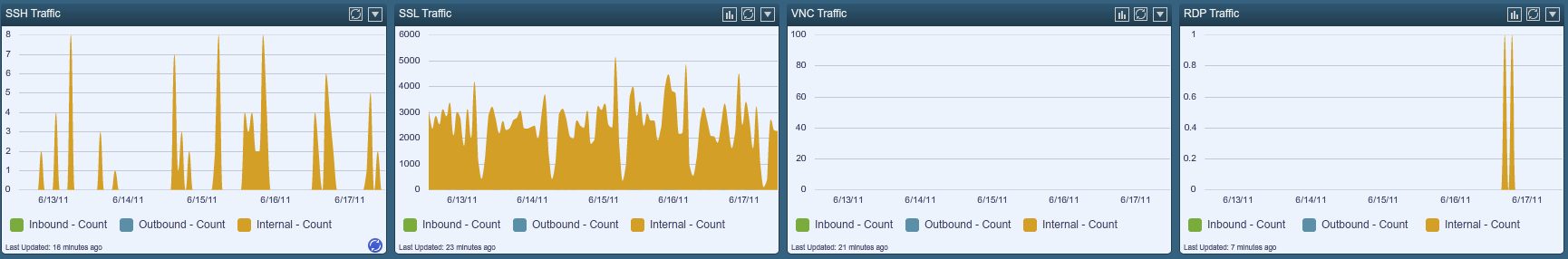
PVS’s real-time logs are another great resource to detect intrusions and compromised systems. I’ve worked with many organizations that send their PVS real-time logs to applications such as Splunk. We also have organizations who deploy the Tenable Log Correlation Engine to process PVS real-time logs. There are so many built-in correlations for the PVS within LCE that we recently announced that all Tenable SecurityCenter ContinuousView licenses would now include a 5 TB LCE license.
- Correlating all web, file sharing, network protocols and SSL traffic with a real-time list of high quality botnet IP addresses.
- Correlating all web and DNS queries with DNS names and URLs that are known to be botnets.
- Tracking systems that perform proxies and leap-frog attacks based on the SSH, VNC, and Windows RDP protocols.
- Tracking anomalies and spikes in all types of logged PVS network sessions including SSL, DNS, NFS, web queries and, in particular, spikes in failed DNS queries.
- Summarizing all executable files that have been downloaded on a daily basis.
- Summarizing all DNS domains queried on both an hourly and daily basis.
- Tracking all network traffic by learned user IDs. This facilitates analysis and reporting of any particular user’s network traffic.
- Tracking client-side network browsing activity including web, VNC, SSH, and Windows RDP.
Below is a screen shot of a botnet dashboard which was created by leveraging PVS logs and LCE log searches to create graphs and trend lines of specific botnets.
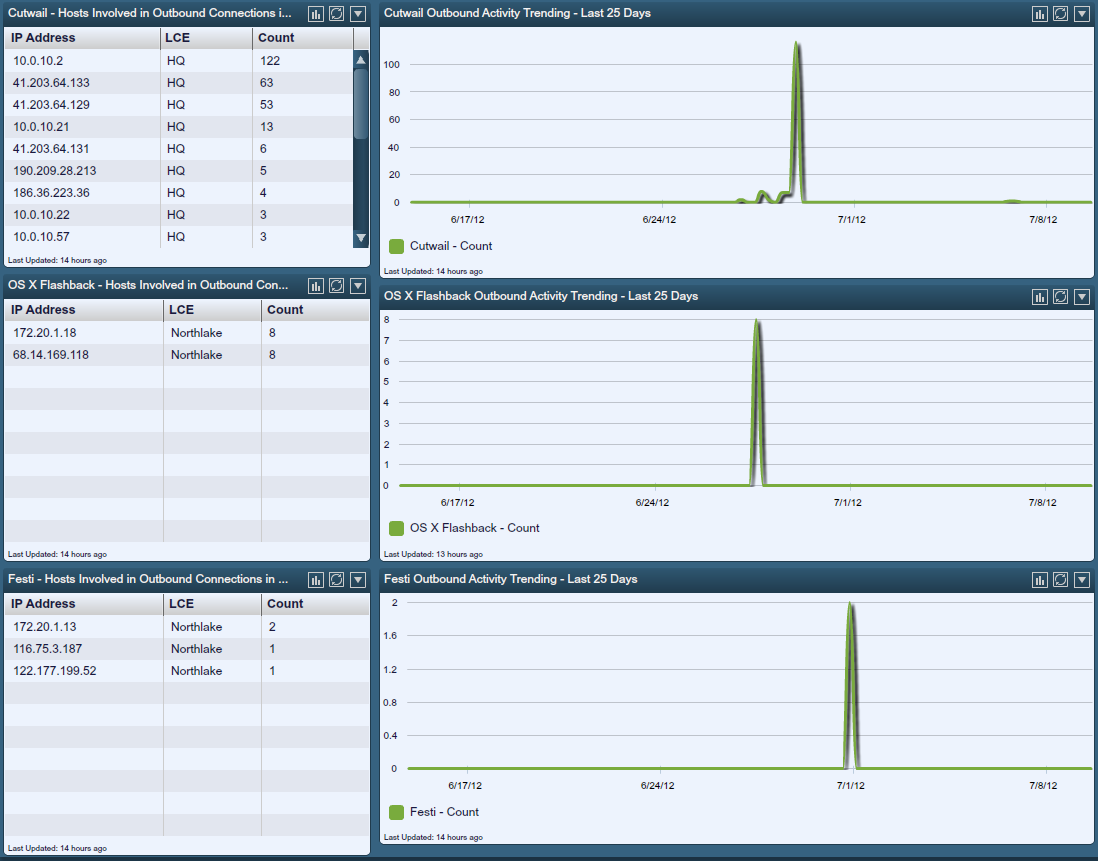
There are many more types of correlations performed by LCE on PVS real-time logs. There are also a wide variety of forensic audits that can be used to perform forensic investigations of system behavior and network traffic.
When combined with Nessus active scans and logs from firewalls, operating systems, intrusion detection systems, and other sources, real-time data from PVS becomes a binding source of data that provides real-time context making the detection of intrusions possible.
Tenable’s Continous View offering allows organizations to deploy multiple Nessus scanners and Passive Vulnerability Scanners as well as a single SecurityCenter and single Log Correlation Engine. To learn how to leverage this platform for both unparalleled vulnerability discovery and the ability to hunt malware and intruders, please click here to read more.
- Log Analysis
- Passive Network Monitoring

