Insights from the 2015 Verizon DBIR
The 2015 Verizon Data Breach Investigations Report (DBIR) was published this week, and it’s full of insights on recent data breaches and recommendations to fortify your organization against the latest threats.
For those who are new to this report, it is an annual publication that investigates security incidents across public and private organizations around the world, with a specific focus on data breaches.
While there are many interesting points to note in the report, here are my top highlights from the DBIR.
Malware
RAM scraping malware aimed at point-of-sale (POS) systems grew significantly in 2014, headlining incidents such as the Target case.
While memory scraping malware was observed in 2011, in recent years more advanced versions have impacted major retailers and have broadened to multiple industries.
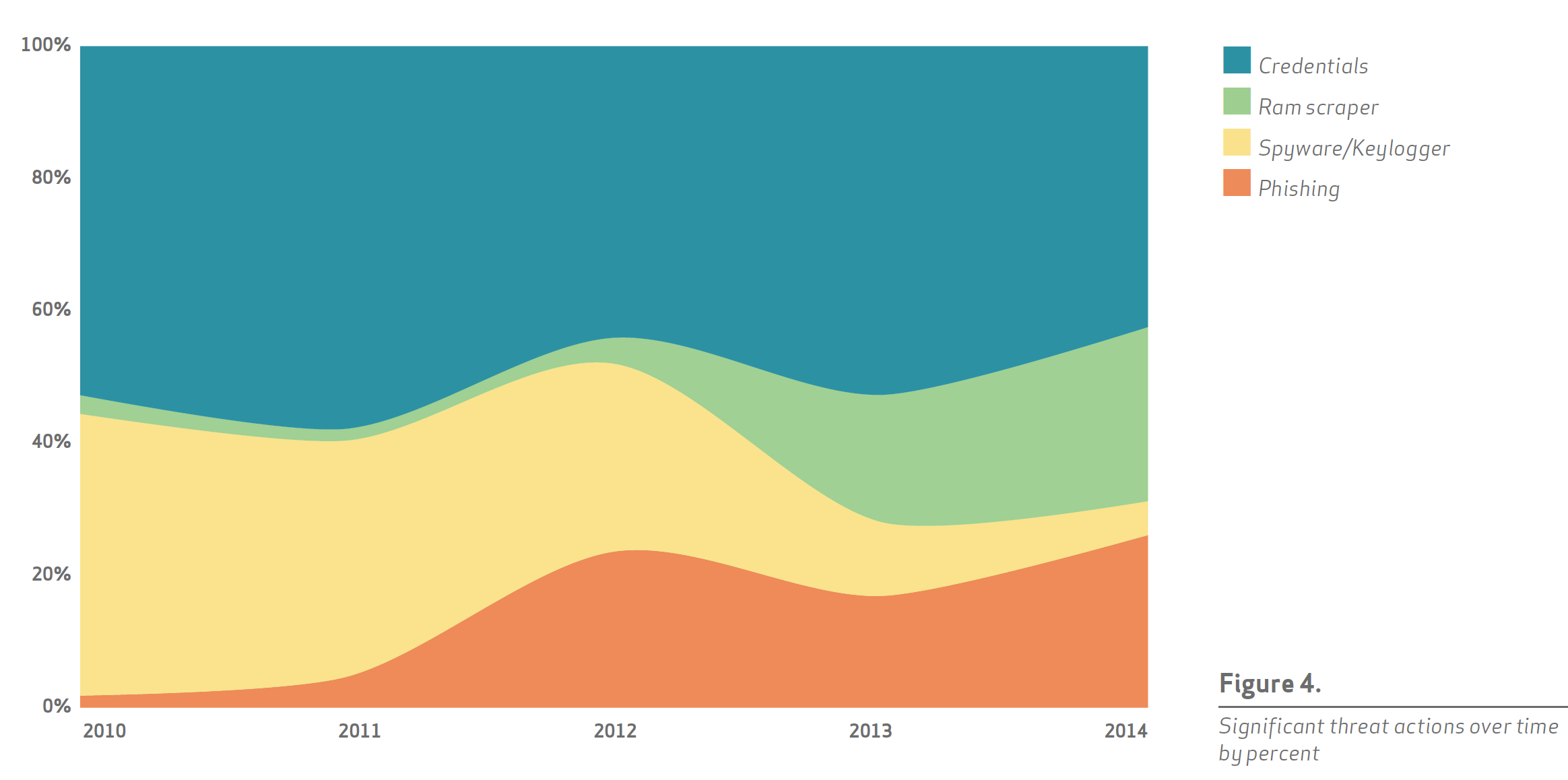
The effects of this class of malware have trickled into the most recent compliance requirements, as noted in Jeff Man’s blog on the latest PCI DSS standards.
The important point here is that continuously monitoring your networks for such classes of malware is essential to improve protection. For organizations that are concerned and would like to monitor for signs of such malware, a solution should include checks for detecting POS malware (POSRAM or Backoff for example), such as Tenable’s SecurityCenter Continuous View (CV).
Vulnerabilities
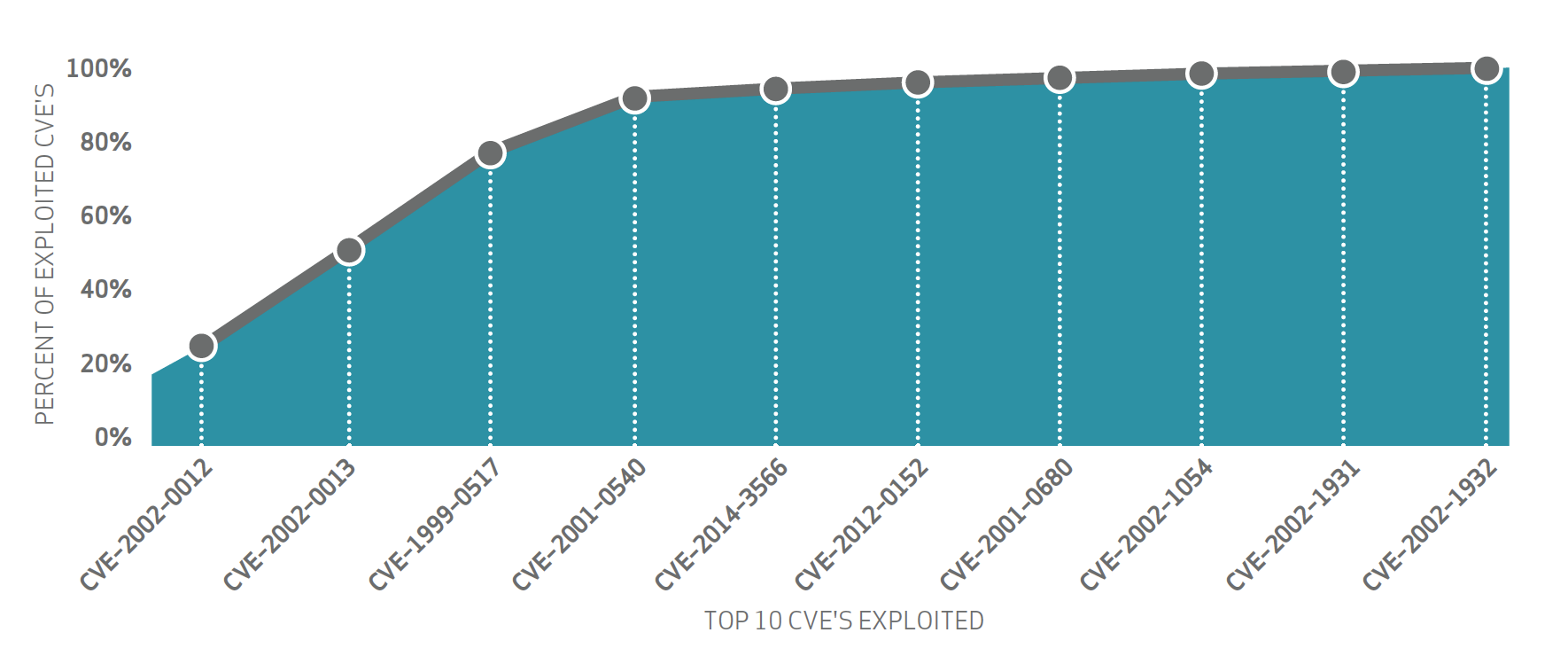
The DBIR notes that 99.9% of exploited vulnerabilities had occurred more than a year after the associated CVE was published. Furthermore, the top ten CVEs accounted for almost 97% of the exploits observed in 2014 as shown below.
Related to this is the trending of cumulative percentages of exploited vulnerabilities. The graph below indicates a critical need to address publicly announced vulnerabilities in a timely fashion since more than 50% of CVEs are exploited within the first 4 weeks of a CVE being published.
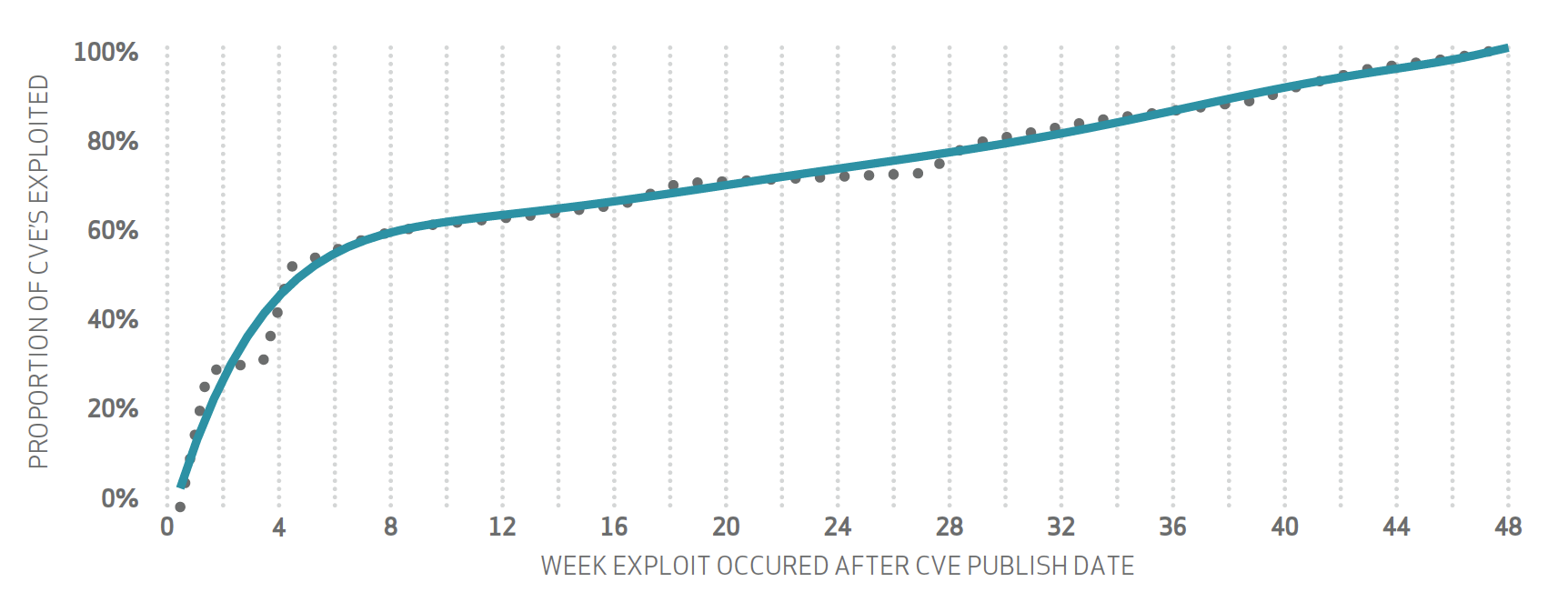
Regardless of which vulnerability management solution is chosen, organizations could vastly improve their security postures by addressing the top vulnerabilities in an expedient manner.
Note that the report findings also indicate that older vulnerabilities (more than 10 years) are still being exploited, so solutions that include broad coverage of older vulnerabilities should be considered. Here are examples of a report and a dashboard that illustrate CVE analysis provided by Tenable’s SecurityCenter CV solution.
Patching
71% of known vulnerabilities had a patch available for more than a year prior to a breach. The DBIR states that a patch deployment strategy focusing on vulnerability coverage is far more effective at preventing data breaches than “fire drills” attempting to patch particular systems as soon as the patches are released.
If there’s one thing that eludes me is the vast amount of resources and dollars spent in purchasing the latest malware products, and yet hosts remain vulnerable to CVEs that are well identified and which can be readily addressed with regular patching.
In fact, Tenable solutions are integrated with major patch management systems to help organizations correlate the results of patching systems with the results of vulnerability scanning to identify gaps in the patching process.
Mobile devices
The DBIR notes that while mobile devices are clearly vulnerable, they are not the preferred vector for data breaches. The report notes that threat actors are using other methods outside of mobile. But organizations should not ignore mobile, and should strive for visibility first and then control. This will be critical if the threat landscape changes.
To help organization identify vulnerable mobile devices, Tenable’s Nessus integrates with major MDM solutions to provide mobile device vulnerability information. When combined with technologies like Tenable’s Passive Vulnerability Scanner (PVS), organizations can include coverage for managed and unmanaged devices for better visibility into both iOS and Android devices when the threat landscape does change.
Effectiveness
40% of controls deemed most effective fall into the Council for Cybersecurity’s Critical Security Controls (CSC) “Quick Win” category. As the DBIR authors put it:
“The results of this process actually reinforce things we’ve said in the past: Don’t sleep on basic, boring security practices. Stop rolling your eyes.”
Check out how Tenable is helping to distill these and other recommendations into 5 critical cyber controls that organizations can implement and use to measure the effectiveness of security in business context with SecurityCenter’s Assurance Report Cards (ARCs).
This summary just scratches the surface of Verizon’s findings, so please read the entire DBIR report to learn about other key findings that may be more relevant for your organization. While there is plenty of information in the report, the sheer length of the report (70 pages) can be a challenge to read and to determine if you are vulnerable or a potential victim. But the report is engaging and enlightening, a necessary professional read. Enjoy it!
- Announcements
- Research Reports

