Easier Credentialed Scanning with Nessus Cloud and Nessus Manager

Note: Nessus Cloud is now a part of Tenable.io Vulnerability Management. To learn more about this application and its latest capabilities, visit the Tenable.io Vulnerability Management web page.
For a long time now, we have been discussing the benefits of doing credentialed vulnerability scans with Nessus®—the benefits of getting more accurate and richer results. If you instruct Nessus to do a non-credentialed scan, it can probe a service remotely and attempt to find vulnerabilities; but if you provide Nessus with credentials, it can query the local host to see much more information. For example, you can determine if a patch for a given vulnerability has been applied. The credentialed scan is far more accurate (and safer) than running a remote check.
The credentialed scan is far more accurate (and safer) than running a remote check
However, we have also heard from people who don’t run credentialed scans. Sometimes it’s for reasons that frankly don’t seem that reasonable. For example, we've heard people say they like the lower count of vulnerabilities that non-credentialed scans produce. Or that they can’t patch the vulnerabilities they’re finding with non-credentialed scans, so why would they want to discover even more?
More often though, we hear that the reason people aren’t doing credentialed vulnerability scans is that it’s just not possible—or it’s too difficult—to get and maintain credentials. Maybe the network department is very protective of the organization’s network infrastructure equipment and the credentials to those systems. Or maybe the systems team has a strong credential management policy, and they’re updating credentials frequently but finding it resource-intensive to get those updates to all the groups that need the credentials.
For these reasons and others, we’ve recently made updates to Nessus Cloud and Nessus Manager to make it easier to run credentialed vulnerability scans, releasing Nessus Agents and also introducing Nessus support for the CyberArk Enterprise Password Vault.
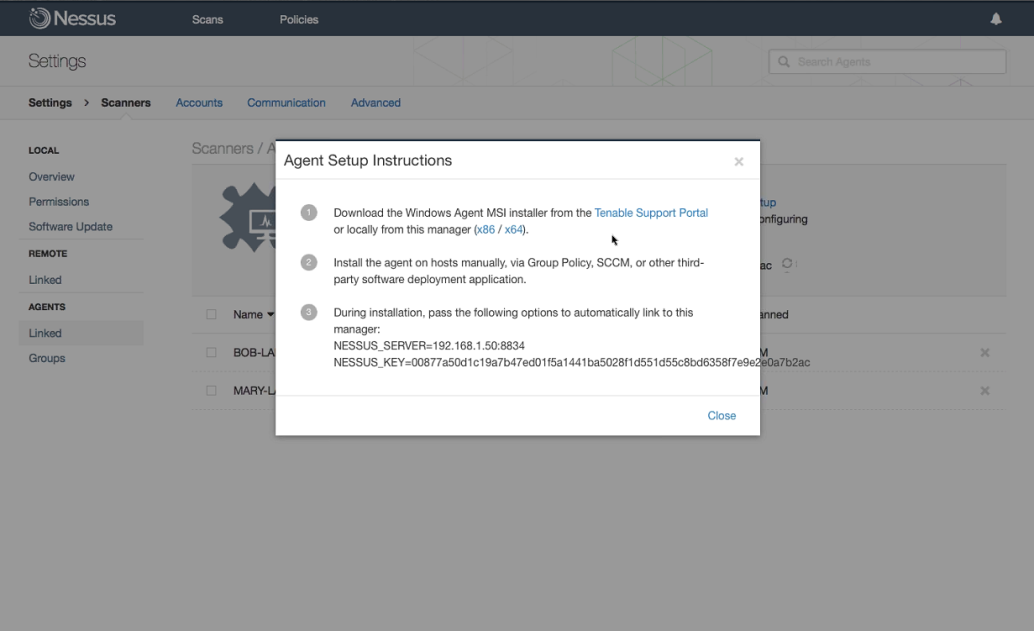
Nessus Agents eliminate the requirement for host credentials
As we’ve discussed in previous articles, Nessus Agents are lightweight programs installed locally on a host – a laptop, virtual system, desktop, and/or server. Agents receive scanning instructions from a central Nessus server, perform scans locally, and report vulnerability, compliance and system results back to the central server. We introduced Nessus Agents earlier this year. Our customers tell us that agents help them reduce credential management headaches.
Our customers tell us that agents help them reduce credential management headaches
Nessus Agents make it easier to do credentialed vulnerability scans because after the agents are installed, they don’t need ongoing host credentials. When you first install Nessus Agents (either manually or with a software management system), you install them under the local SYSTEM account in Windows or root on Unix-based operating systems. The agents then inherit the permissions of the account used for installation so they can perform credentialed scans, even if the credentials on the system have changed. Even better, Nessus Agents auto-update, so you don’t need to worry about installing new versions of agents in the future.
CyberArk Enterprise Password Vault support
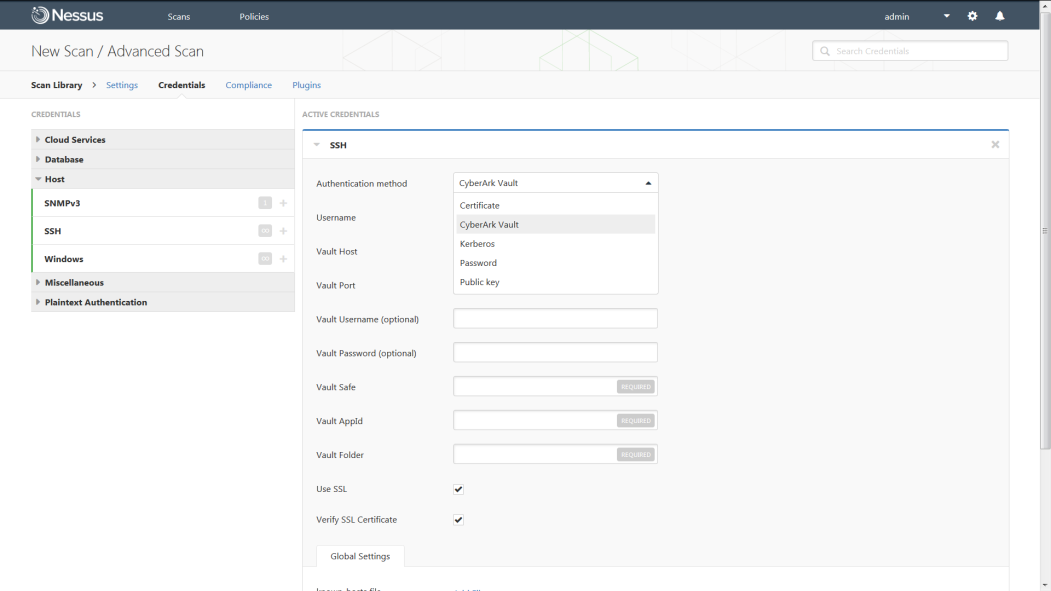
Nessus Cloud and Nessus Manager are now integrated with CyberArk. We've received many requests from customers to add support for this popular enterprise password vault to Nessus. As CyberArk describes on their website, they enable organizations to secure, manage and track the use of privileged credentials whether on-premises or in the cloud, across operating systems, databases, applications, hypervisors, network devices and more.
Nessus will get credentials from CyberArk to use in scans
To enable CyberArk to share credentials with Nessus Cloud or Nessus Manager, you simply navigate to the Credentials area in the Advanced Scan tab and enter your CyberArk Vault information. From then on, Nessus will get credentials from CyberArk to use in scans, which saves you time by no longer having to manually add credentials into Nessus.
Summary
While Nessus can perform both non-credentialed and credentialed vulnerability scans, there are definite advantages to credentialed scans. With both Nessus Agents and CyberArk password vault options, our goal is to make credentialed scanning easier for you in Nessus Cloud and Nessus Manager.
You’ll find more information about Nessus Agents on our website, including new OS support for Mac OS X, CentOS and Red Hat Linux (released this month). If you’re using Nessus Cloud or Nessus Manager and would like to check out CyberArk integration, visit the Tenable Support Portal and read the Nessus 6.4 release notes.
- Agents
- Cloud
- Integrations
- Nessus