Cybersecurity Snapshot: SANS Offers Tips for Maximizing Smaller OT Security Budgets

A SANS Institute survey found that budgets for ICS/OT security have shrunk, and advises on how to do more with less. Plus, hiring managers boost starting salaries to recruit stellar cyber pros. In addition, CISA’s Cybersecurity Awareness Month campaign challenges tech vendors to build safer products. And much more!
Dive into six things that are top of mind for the week ending October 6.
1 - SANS: How to cope with cuts in ICS/OT security budgets
If your organization has cut its spending for securing industrial control systems (ICS) and operational technology (OT) systems, how can your ICS/OT security team make the best use of its smaller budget?
You’ll find actionable recommendations in the “SANS ICS/OT Cybersecurity Survey: 2023’s Challenges and Tomorrow’s Defenses” report, which polled 700 ICS/OT security professionals and found that ICS/OT security budgets trended down this year.
“Essentially, budgets are down in just about every category we analyzed,” the SANS Institute report reads. This includes a significant jump in respondents who said their organization has no budget for ICS/OT security at all – from 7.7% in 2022 to 21.8% in 2023.
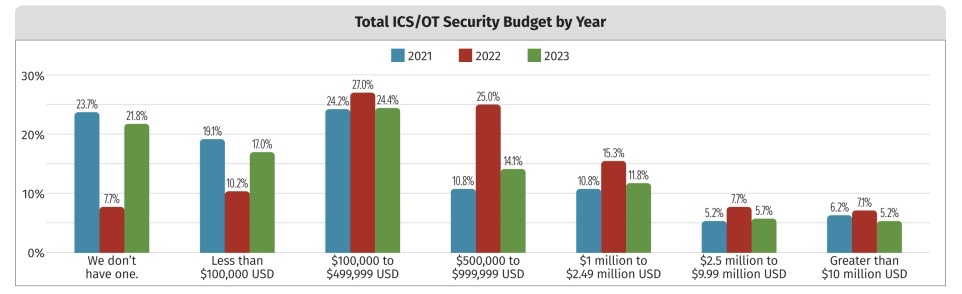
(Source: SANS Institute’s “SANS ICS/OT Cybersecurity Survey: 2023’s Challenges and Tomorrow’s Defenses,” September 2023)
Ironically, as budgets fell, the number of organizations that rated threats to ICS/OT systems as “severe” (25%) or “high” (44%) increased. So how can you allocate your limited dollars to reduce the greatest risks? The report’s suggestions include:
- Boost security awareness among the staff
- Use assessment tools from trusted providers such as MITRE
- Adopt a risk-based program for vulnerability management
- Obtain ICS network visibility through continuous network security monitoring
- Prepare an ICS-specific incident response plan
SANS also recommends checking out its white paper "The Five ICS Cybersecurity Critical Controls."
Coping with tight budgets is just one of many ICS/OT security issues covered by the report. To get more details, download the report.
For more information about ICS/OT security, check out these Tenable blogs and videos:
- “Three U.S. Policy Recommendations to Strengthen OT Cybersecurity”
- “A Practical Way To Reduce Risk on the Shop Floor”
- “OT security teams get new adversary-emulation tool”
- “Empowering Cybersecurity Excellence: IBM and Tenable Collaborate for IT/OT Security Innovation”
- “ETHOS: Bringing the OT Security Community Together for Threat Information Sharing”
Anatomy of a Threat: Rockwell Automation Vulnerabilities (CVE-2023-3595) and (CVE-2023-3596)
Tenable.ot Security Spotlight - The Ransomware Ecosystem
Tenable.ot Security Spotlight - Ransomware in OT Systems
2 - Cyber pros to hiring managers: Show me the money!
Good news for cyber professionals: Cybersecurity ranked as the top technology skill for which hiring managers are willing to increase starting salaries, according to Robert Half’s “2024 Salary Guide,” published this week. Specifically, 55% of tech hiring managers polled will bump up cybersecurity salaries to land desired candidates.
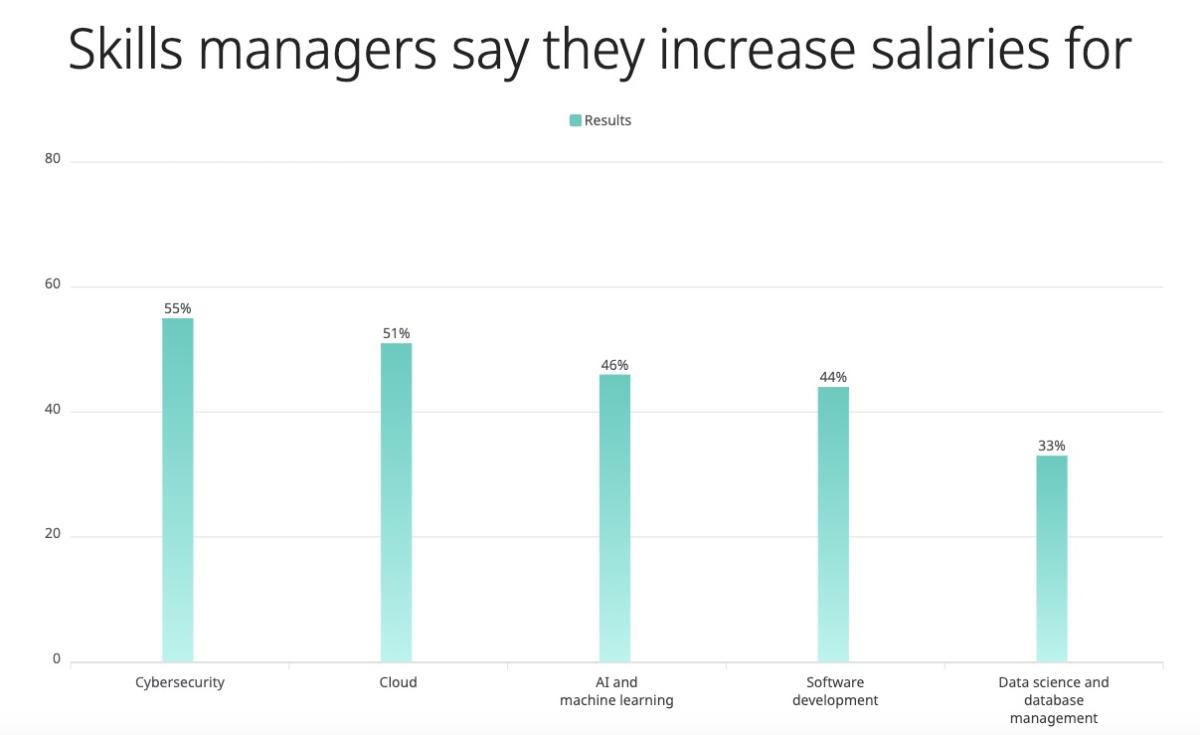
(Source: Robert Half’s “2024 Salary Guide”, September 2023)
Unsurprisingly, cybersecurity pros rank among the most in-demand technology workers, along with those skilled in cloud, DevOps and AI.
So what’s the cybersecurity role with the highest starting salary? That’d be systems security manager, commanding a U.S. average ranging from about $137,000 a year for entry-level employees to almost $200,000 for the most experienced – not counting bonuses, benefits or perks. Starting salaries vary greatly depending on geography. For instance, the range for this role in San Francisco is from about $185,000 to $268,000.
Other highly compensated cybersecurity jobs include: security architect; data security analyst; network security engineer; and systems security administrator.
Regarding technology executives, CISOs ranked just below CIOs and right above CTOs, with a national average starting salary range of $176,000 to $259,000. That range climbs to around $238,000 to $350,000 in San Francisco, for example.
Overall, the hiring market in the technology sector as a whole is strong, making it a job candidate’s market. “Job gains in the tech sector outnumber losses, and the unemployment rate remains well below the national average,” reads the report's technology section.
Other key findings for the technology sector include:
- 61% of tech hiring managers plan to expand their teams
- 35% need to fill open positions
- 90% say finding top tech talent remains a challenge
- 64% of tech workers are looking for or planning to look for a new job
To get more details, check out the report’s announcement, the full report and the report’s technology section specifically.
3 - CISA calls on tech vendors to do better in cybersecurity awareness campaign
Technology manufacturers should build security features by design into their products and ship them with the highest security default settings, a move that would significantly boost protection for end users.
So said the U.S. Cybersecurity and Infrastructure Security Agency (CISA) in its announcement of its Cybersecurity Awareness Month campaign “Secure Our World,” which also aims to promote cybersecurity best practices among individuals and businesses during October.

Customers shouldn’t have to constantly monitor, update and repair their systems to mitigate cyberattacks, CISA says in a campaign page aimed at tech vendors titled “Secure Your Products.”
“Design your products to minimize security flaws and sell them with default settings that make them safe ‘out of the box,’” reads the page. It’s an echo of a similar message the White House sent to tech vendors when it released the National Cybersecurity Strategy earlier this year.
Overall, the “Secure Our World” public awareness campaign aims to promote widespread adoption of four basic, foundational cybersecurity practices:
- Use strong passwords and use a password manager to generate and store them.
- Use multi-factor authentication for all critical accounts.
- Beware of emails, texts and calls that ask for sensitive information and prompt you to click on links or open attachments, as they could be phishing attacks.
- Keep your devices’ software updated.
“As cyber threats continue to evolve, we encourage everyone to do their part to stay cyber-safe,” CISA Director Jen Easterly said in a statement.
To get more details, check out CISA’s:
- Cybersecurity Awareness Month page
- “Secure Our World” campaign home page
- Cybersecurity Awareness Month 2023 Resources and Partner Toolkit
- Cybersecurity Awareness Month video message
4 - FBI: Back-to-back ransomware attacks become trendy
Ransomware attackers are increasingly delivering a one-two punch to their victims, timing the second strike to hit usually 48 hours after the first. The goal? To further pressure the targeted organization to pay the demanded ransom.
That’s according to the U.S. Federal Bureau of Investigation (FBI), which detailed this trending technique known as dual ransomware in a recent advisory. Usually each dual attack combines two different ransomware variants, such as AvosLocker, Diamond, Hive and LockBit.
“This use of dual ransomware variants resulted in a combination of data encryption, exfiltration, and financial losses from ransom payments,” reads the five-page document. The advisory also describes new data destruction tactics used by ransomware attackers.
Mitigations detailed in the advisory include:
- Regularly back up data and keep the backups offline
- Encrypt all backed up data and store it in a way that it can’t be altered
- Monitor the security posture of your third-party vendors
- Adopt a recovery plan
To get more details, read the full advisory.
5 - Assess multi-cloud security with CNAPPgoat open source tool
Involved with cloud security? Check out CNAPPgoat, an open source tool for easily provisioning and destroying interactive sandbox environments where your team can test its cloud security skills, processes, tools and posture.
Created by Ermetic, a cloud-native application protection platform (CNAPP) innovator that Tenable acquired this week, CNAPPgoat allows security teams to simulate unsecured and vulnerable assets, as well as validate their defenses, in customized cloud environments. Launched in August, CNAPPgoat supports Amazon Web Services (AWS), Microsoft Azure and Google Cloud Platform (GCP).
Provisioning a vulnerable environment with a broad range of risk scenarios opens up a variety of use cases, including:
- Create a sandbox for assessing your team’s capabilities, procedures and protocols
- Use vulnerable environments for hands-on training workshops
- Provision a “shooting range” for pentesters to test their skills

This week, CNAPPgoat’s large library of vulnerable scenarios got bigger with a new one that lets you experiment with a technique that leverages exposure to server side request forgeries (SSRF) to trigger calls to AWS services from within an Amazon Elastic Compute Cloud (EC2) instance.
To get more details, check out:
- The statement and blog announcing CNAPPgoat’s launch
- CNAPPgoat’s Github page
- This week’s blog about the new scenario “Exfiltrated, Signed, Delivered – What Can Go Wrong When an Amazon Elastic Compute Cloud (EC2) Instance is Exposed to SSRF”
- Tenable’s announcement and blog about the Ermetic acquisition
6 - Report: CL0P ransomware attacks against MOVEit crater in August
After dominating the spotlight in June and July with its widespread exploitation of vulnerabilities in the Progress Software MOVEit Transfer tool, the CL0P gang went quiet in August, causing total ransomware attacks to fall 22% compared with July.
That’s according to data from the NCC Group’s latest “Monthly Threat Pulse” report, which also noted that although August attacks fell from the previous month, they nonetheless grew 144% year-on-year.

“After two record months for ransomware attacks, the fall in attacks in August was to be expected,” Matt Hull, Global Head of Threat Intelligence at NCC Group, said in the report, adding that CL0P’s MOVEit attacks “somewhat inflated” the June and July numbers.
“This being said, the number of recorded victims in August were still significantly higher than this time last year,” Hull added.
Lockbit ranked first among threat actors, accounting for 32% of August attacks, followed by BlackCat (11%) and 8Base (8%). CL0P was responsible for only 1% of attacks.
Among targeted verticals, industrials ranked first, hit by 31% of the attacks, as threat actors sought to steal personally identifiable information and intellectual property, as well as extort hefty ransoms from large organizations.
To get more details, read the full report.
For more information about ransomware protection:
- “FAQ for MOVEit Transfer Vulnerabilities and CL0P Ransomware Gang” (Tenable)
- “7 Steps to Help Prevent & Limit the Impact of Ransomware” (Center for Internet Security)
- “Ransomware Preparedness: Why Organizations Should Plan for Ransomware Attacks Like Disasters” (Tenable)
- “CVE-2023-20269: Zero-Day Vulnerability in Cisco Adaptive Security Appliance and Firepower Threat Defense Reportedly Exploited by Ransomware Groups” (Tenable)
- “Mitigating malware and ransomware attacks” (U.K. NCSC)
VIDEOS
Anatomy of a Threat: MOVEIt (Tenable)
Tenable CEO Amit Yoran discusses Las Vegas ransomware attacks (CNN)
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Government
- OT Security
- Risk-based Vulnerability Management


