Cybersecurity Snapshot: Cyber Pros Taxed by Overwork, Understaffing and Lack of Support, as Stress Takes a Toll

Life is getting harder for cybersecurity pros, but there are ways to improve working conditions. Check out what a study found. Meanwhile, there’s a new, free attack-emulation tool for OT security teams. Plus, the U.S. government is alerting about exploits to CVE-2022-47966 and CVE-2022-42475. We also look at recommendations to mitigate DDoS attacks. And much more!
Dive into six things that are top of mind for the week ending September 8.
1 - Study: Being a cyber pro is tough, and it ain’t getting any easier
Most cybersecurity professionals feel their jobs are getting harder, due to factors like staffing shortages, tighter budgets, growing compliance requirements and increasingly complex attacks.
This in turn harms cybersecurity professionals’ job satisfaction and worsens job churn, as many look for new employers – and some even for a different career – to flee the stress of crushing workloads and lack of organizational support.
That’s according to the report “The Life and Times of Cybersecurity Professionals,” which was released this week by Enterprise Strategy Group (ESG) and the Information Systems Security Association (ISSA), and which surveyed 301 IT and cybersecurity professionals.
“Cybersecurity professionals are charged with protecting the organization while being overworked, overstressed, and understaffed,” Candy Alexander, Board President, ISSA International, said in a statement.

Here’s how cybersecurity pros responded to key survey questions:
- 63% say their work has become more difficult over the past two years
- 44% are “very satisfied” with their jobs, while 36% are “somewhat satisfied” and 13% are either “somewhat” or “very” dissatisfied
- Half say it’s “very likely” (21%), “somewhat likely” (23%) or “likely” (6%) they’ll leave their current job in 2023
- Almost one-third occasionally or regularly consider leaving their profession
- Only 31% say their organizations have an advanced cybersecurity culture
How Cyber Pros Rate Their Organizations’ Cybersecurity Culture
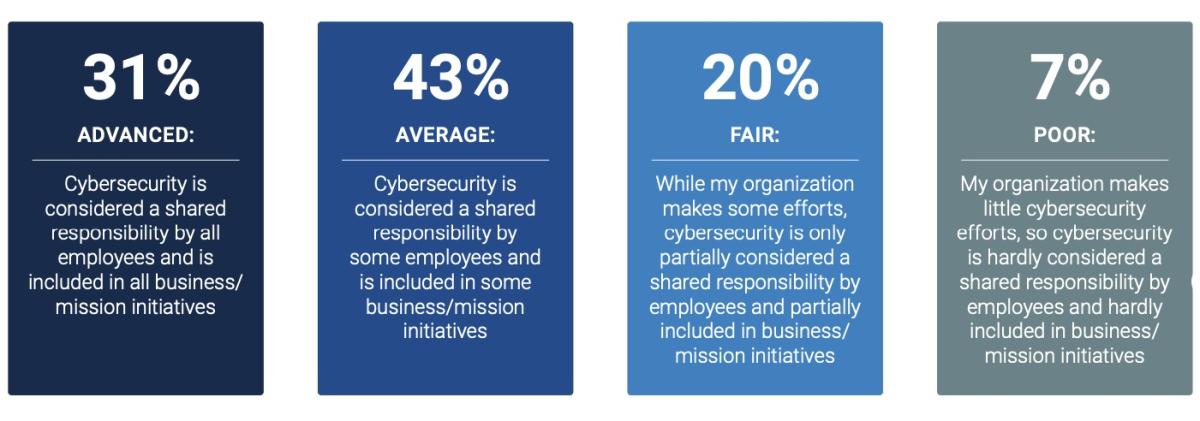
(Source: “The Life and Times of Cybersecurity Professionals” report from ESG and ISSA, Sept. 2023)
“Cybersecurity professional jobs grow more challenging, nuanced, and specialized annually,” Jon Oltsik, the report’s author and ESG Distinguished Analyst, said in a statement.
So what can be done? Here are some suggestions from the survey respondents:
- Improve the relationship between IT and security teams by, for example:
- Ensuring security staff is included in IT projects from their start
- Increase cross-training between security and IT staff
- Automate processes that require IT and cyber teams’ collaboration
- Improve the relationship between security and business managers by, for example:
- Boosting cyber teams’ ability to flag and quantify cyber risks as they apply to the business
- Increasing cyber training for executives and board members
- Prioritize cyber resources and investments for business-critical assets
- Improve the cybersecurity program by, for example:
- Increasing training for cyber and IT pros
- Take steps to enhance the organization’s cybersecurity culture
- Hire more staff and boost the cybersecurity budget
To get more details, read the announcement from ESG and ISSA and download the full report.
2 - OT security teams get new adversary-emulation tool
Are you tasked with securing your organization’s operational technology (OT) systems? You might want to check out a new tool that imitates attacks against OT assets so security teams can test and improve their defenses.
Announced this week and developed by CISA and MITRE, the MITRE Caldera for OT tool is an extension to Caldera, an open source, adversary-emulation tool. Caldera for OT consists of a set of plugins that offer support for common industrial protocols. Both Caldera for OT and Caldera are free.
“Caldera for OT introduces 29 distinct OT abilities to the hundreds of existing enterprise-focused abilities already included with Caldera,” reads a MITRE blog.

To get more details, check out:
- the joint CISA-MITRE announcement “MITRE & CISA Release Open-Source MITRE Caldera Extension for Operational Technology”
- the MITRE blog “Announcing MITRE Caldera for OT”
- the Caldera for OT GitHub page
- the Caldera platform’s home page
3 - A temperature check on OT security today
During two recent Tenable webinars about OT cybersecurity, we polled attendees about a variety of related topics. Check out what we found out from participants at the “OT Security Master Class” and “Experts Share Ways To Improve Manufacturing Sector IT/OT Security” webinars.
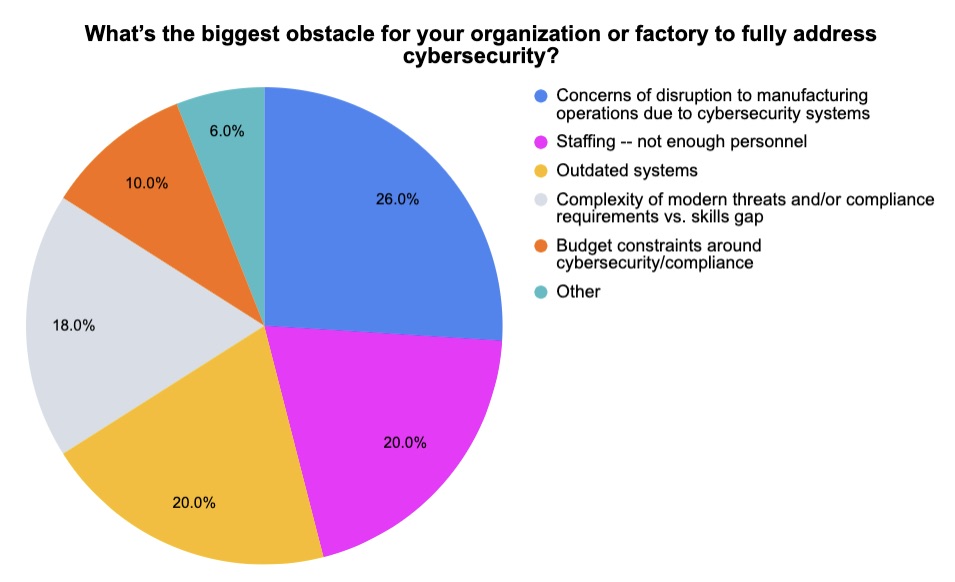
(50 respondents polled by Tenable, August 2023)
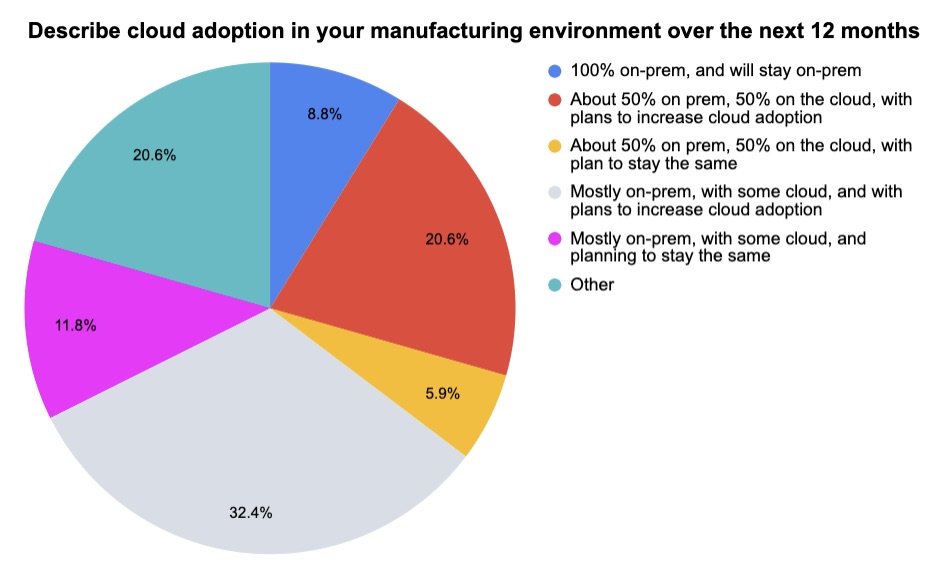
(34 respondents polled by Tenable, August 2023)
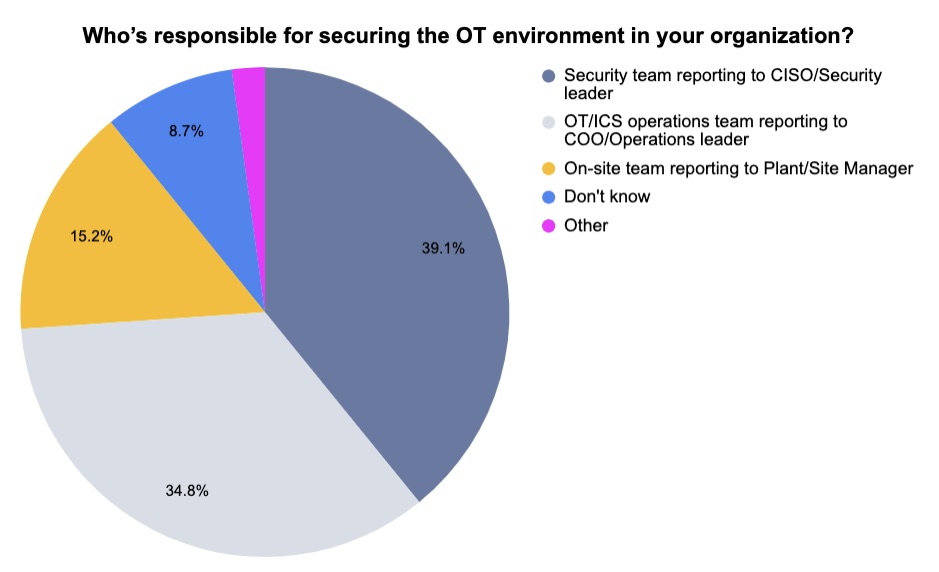
(92 respondents polled by Tenable, August 2023)
For more information about OT cybersecurity, check out these Tenable videos:
Tenable.ot Security Spotlight - Episode 1: The Ransomware Ecosystem
Tenable.ot Security Spotlight - Episode 2: The Business Risk From a Ransomware Attack on OT Systems
Tenable.ot Security Spotlight - Episode 3: Ransomware in OT Systems
4 - CISA: Nation-state APT attackers exploit CVE-2022-47966 and CVE-2022-42475
CISA, the FBI and the U.S. Cyber Command’s Cyber National Mission Force (CNMF) issued a joint advisory this week alerting that nation-state hackers exploited CVE-2022-47966 and CVE-2022-42475 to gain access to an aeronautical organization’s network.
By exploiting CVE-2022-47966, nation-state advanced persistent threat (APT) attackers breached this organization’s Zoho ManageEngine ServiceDesk Plus application, then established persistence and moved laterally. Meanwhile, other APT attackers established presence on the organization’s firewall by exploiting CVE-2022-42475.

Malicious activity at this aeronautical organization began as early as January 2023, CISA determined after conducting an incident response analysis at the organization’s request. Cybersecurity teams should review the joint advisory, which is labeled AA23-250A and titled “Multiple Nation-State Threat Actors Exploit CVE-2022-47966 and CVE-2022-42475”, and implement the recommended mitigations, CISA said in a statement.
To get a deep dive into the joint advisory, check out the Tenable blog “AA23-250A: Multiple Nation-State Threat Actors Exploit CVE-2022-47966 and CVE-2022-42475.”
For more information about these vulnerabilities, check out these Tenable resources:
- CVE-2022-47966, a remote code execution vulnerability in multiple Zoho ManageEngine on-premises products
- CVE-2022-42475, a heap-based buffer overflow vulnerability in several versions of Fortinet’s FortiOS
5 - Fresh guidance on mitigating risk of DDoS attacks
If you feel your cybersecurity team could use a refresher on how to best fend off distributed denial of service (DDoS) attacks, you might benefit from a batch of CISA recommendations published this week.
Titled “Capacity Enhancement Guide: Volumetric DDoS Against Web Services Technical Guidance,” the nine-page document offers actionable tips, best practices and insights for stronger resilience against large-scale DDoS attacks.
Although the guide is aimed specifically at civilian executive branch agencies of the U.S. federal government, CISA notes that it can be equally helpful to all organizations in the public- and private-sectors.
The document is divided into two main sections:
- The first section, titled “Impact Analysis,” aims to help organizations assess the effects and consequences of DDoS attacks on their targeted web services.
- The second section, titled “Risk Mitigations,” offers technical guidance to be used as organizations evaluate DDoS protections for their systems.
To get more details, check out CISA’s announcement and read the full guide.
For more information about protecting your organization from DDoS attacks:
- “Understanding and Responding to Distributed Denial-of-Service Attacks” (CISA)
- “What Is a DDoS Attack and How Does It Work?”(CompTIA)
- “How to Prevent DDoS Attacks: 5 Steps for DDoS Prevention” (eSecurity Planet)
- “DDoS attacks: Definition, examples, and techniques” (CSO)
VIDEO
What is a DDoS Attack (Distributed Denial-of-Service)? (TechTarget)
6 - CIS Benchmarks for SQL Server and Apache Tomcat updated
The latest updates to the Center for Internet Security’s CIS Benchmarks have been announced, and they include new recommendations to securely configure Microsoft SQL Server, Apache Tomcat and others.
Specifically, these CIS Benchmarks were updated in August:
- CIS Apache Cassandra 3.11 Benchmark v1.1.0
- CIS Apache Tomcat 10 Benchmark v1.1.0
- CIS Microsoft SQL Server 2016 Benchmark v1.4.0
- CIS Microsoft SQL Server 2017 Benchmark v1.3.0
- CIS Ubuntu Linux 20.04 LTS STIG Benchmark v2.0.0

To get more details, read the CIS blog “CIS Benchmarks September 2023.” For more information about the CIS Benchmarks list, check out its home page, as well as:
- “How to use CIS benchmarks to improve public cloud security” (TechTarget)
- “CIS Benchmarks Communities: Where configurations meet consensus” (HelpNet Security)
- “CIS Benchmarks: DevOps Guide to Hardening the Cloud” (DevOps)
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Federal
- Government


