CVE-2022-22948: VMware vCenter Server Sensitive Information Disclosure Vulnerability

Researchers disclose a moderate severity vulnerability in VMware vCenter Server that can be used in an exploit chain with other vCenter Server flaws to take over servers.
Background
On March 29, VMware published an advisory (VMSA-2022-0009) for a moderate severity vulnerability in VMware vCenter Server, its centralized management software for VMware vSphere cloud computing virtualization systems.
| CVE | Description | CVSSv3 | VPR* |
|---|---|---|---|
| CVE-2022-22948 | VMware vCenter Server Information Disclosure Vulnerability | 5.5 | 6.9 |
*Please note: Tenable’s Vulnerability Priority Rating (VPR) scores are calculated nightly. This blog post was published on March 30 and reflects VPR at that time.
The vulnerability is credited to Yuval Lazar, a security researcher at Pentera. Lazar was also credited with discovering and disclosing CVE-2021-22015, a local privilege escalation vulnerability in vCenter Server.
Analysis
CVE-2022-22948 is a local information disclosure vulnerability in vCenter Server. An authenticated, local attacker with non-administrative (low-privileged user) access to the vulnerable vCenter Server instance could exploit this vulnerability to obtain sensitive information from the server, such as credentials for a high-privileged user.
For complete analysis of this vulnerability, please refer to Lazar’s blog.
This isn’t the first information disclosure bug in vCenter Server to warrant attention. In 2020, VMware addressed CVE-2020-3952, an information disclosure vulnerability in vCenter Server that was assigned the maximum CVSSv3 score of 10.0.
Chaining exploits to achieve full server takeover
By itself, CVE-2022-22948 is a moderately severe vulnerability. However, Lazar’s research found that by chaining this vulnerability with previously disclosed VMware vCenter vulnerabilities, including CVE-2021-21972, an unauthorized file upload vulnerability and CVE-2021-22015, a local privilege escalation vulnerability that Lazar also discovered, an attacker could potentially take full control of an organization’s ESXi servers.
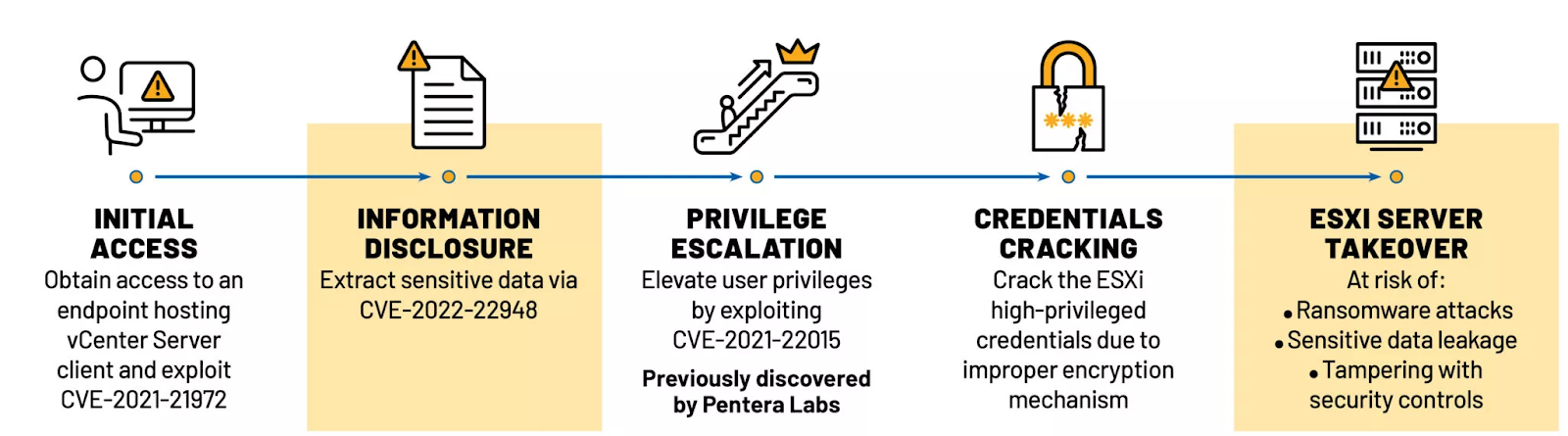
Image Source: Pentera
VMware vCenter Flaws popular amongst attackers in 2021
Earlier this year, we featured CVE-2021-21985, a critical remote execution flaw in VMware vCenter and vSphere as one of the top five vulnerabilities exploited by attackers in our 2021 Threat Landscape Retrospective. While we highlighted CVE-2021-21985 specifically in the top five, it reflects a general trend of attackers targeting vCenter and vSphere using multiple flaws including CVE-2021-22005 and the aforementioned CVE-2021-21972.
Most of the VMware vulnerabilities referenced in this blog (with the exception of CVE-2021-22015) are included in the Cyber Security and Infrastructure Agency (CISA)’s catalog of known exploited vulnerabilities.
Ransomware groups in particular favor VMware vulnerabilities in the last few years. For instance, the Conti ransomware group and its affiliates have exploited multiple VMware vulnerabilities as part of their attacks to gain initial access into organizations. Since 2020, researchers have discovered that a number of ransomware groups like RansomEXX/Defray777, HelloKitty, REvil, BlackMatter and Hive have also targeted ESXi. There are also reports of an unknown ransomware group encrypting virtual machines in VMware ESXi servers.
Attack chains like the one identified by Lazar could prove to be valuable for ransomware groups and affiliates.
No in-the-wild exploitation observed
Presently, there are no indications that CVE-2022-22948 has been exploited in the wild. Because it is a local, post-authentication vulnerability, it isn’t feasible to identify exploitation attempts. However, an uptick in attempts to exploit CVE-2021-21972 might be indicative of attackers looking to leverage this exploit chain in the wild.
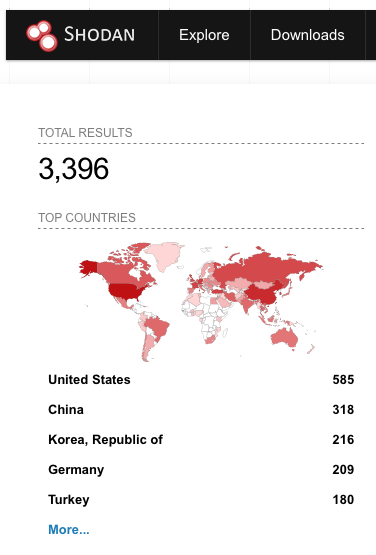
Because an attacker would need to exploit an initial access vulnerability like CVE-2021-21972 before being able to exploit CVE-2022-22948, we believe it’s important for organizations to ensure their VMware systems are patched and up-to-date to prevent exploitation of legacy vulnerabilities. Based on a previously shared Shodan search query for CVE-2021-21972, we’ve found that there are still nearly 3,400 publicly accessible instances of vCenter Server on the internet. While it is unclear what percentage of these instances are vulnerable to CVE-2021-21972, a cursory search of the Shodan results shows more than a few vCenter Server instances running affected versions that are six to eight years old.
Proof of concept
At the time this blog post was published, no public proof-of-concept exploit existed for CVE-2022-22948. However, Lazar’s blog post includes an example of a Python script successfully decrypting the password for a high-privileged user within the vCenter Server that can be used to take over the ESXi.
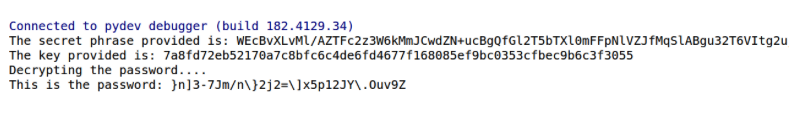
Image Source: Pentera
Solution
According to VMware’s advisory, Windows 6.5 and 6.7 versions of vCenter Server are not affected. However, the Windows 7.0 version of vCenter Server and the Virtual Appliance versions of vCenter Server are affected.
Identifying affected systems
A list of Tenable plugins to identify this vulnerability can be found here.
For Nessus plugin ID 159306, “VMware vCenter Server 6.5 / 6.7 / 7.0 Information Disclosure (VMSA-2022-0009),” users are required to enable the “Show potential false alarms” setting, also known as paranoid mode, in their scan policy in order to enable this plugin in a scan.
We also recommend enabling only this specific plugin in a paranoid scan. Scan policies configured to have all plugins enabled will see an increase in the number of triggers, as it will include all paranoid plugins during the scan.
Enabling Paranoid Mode
To enable this setting for Nessus and Tenable.io users:
- Click Assessment > General > Accuracy
- Enable the “Show potential false alarms” option
To enable this setting for Tenable.sc (formerly SecurityCenter) users:
- Click Assessment > Accuracy
- Click the drop-down box and select “Paranoid (more false alarms)”
Get more information
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management


