Applying Tenable’s Risk-based Vulnerability Management to the Australian Cyber Security Centre's Essential Eight
Learn how Thales Cyber Services uses Tenable to help customers navigate the maturity levels of the Essential Eight, enabling vulnerability management and staying ahead of cyber threats.
In today’s fast-moving digital world, cyber threats are more advanced and relentless than ever. A single security breach can mean financial loss, reputational damage and operational chaos. That’s why cybersecurity isn’t just an IT issue, it’s a business necessity.
To help organizations stay ahead of evolving threats, the Australian Signals Directorate’s (ASD) Australian Cyber Security Centre (ACSC) developed the “Essential Eight” (E8), a practical set of cybersecurity strategies designed to protect IT networks from system intrusion, attacks like ransomware and data breaches. But having security measures in place isn’t enough — they need to be continuously assessed and improved. That’s where the “Essential Eight Maturity Model” comes in.
While the Essential Eight strategies originated in Australia, they offer practical guidance that any organization around the world can apply. Introduced in 2017, this framework helps organizations gauge their cybersecurity readiness and strengthen their defenses over time. Built on real-world insights from cyber intelligence and incident response, the framework evolves to keep pace with the latest threats. Whether you are just starting your cybersecurity journey or looking to enhance existing protections, the E8 offers a clear, effective roadmap to resilience. This roadmap manifests as the Essential Eight Maturity Model, three iterative stages of security controls referred to as maturity levels that an organization can apply across their environment to protect them from an increasing level of threat. In a world where digital threats are constantly changing, having a strong cybersecurity foundation isn’t optional — it’s essential.
How vulnerability management fits within the Essential Eight
Effective vulnerability management for applications and operating systems alike is crucial for cybersecurity maturity under the E8. Using solutions like Tenable Vulnerability Management or Tenable Security Center, organizations can adhere to the E8 and ensure vulnerabilities are detected and responded to promptly.
A structured approach to asset discovery and vulnerability scanning are key to achieving an organization’s target maturity level. At a high level, this success criterion includes:
- Performing automated asset discovery.
- Maintaining regular and frequent vulnerability scanning.
- Understanding which systems are exposed to the internet.
- Knowing the technology stack underpinning your online services.
- Prioritizing and mitigating vulnerabilities according to their software category in line with E8 timelines.
- Identifying and retiring unsupported and security end-of-life software.
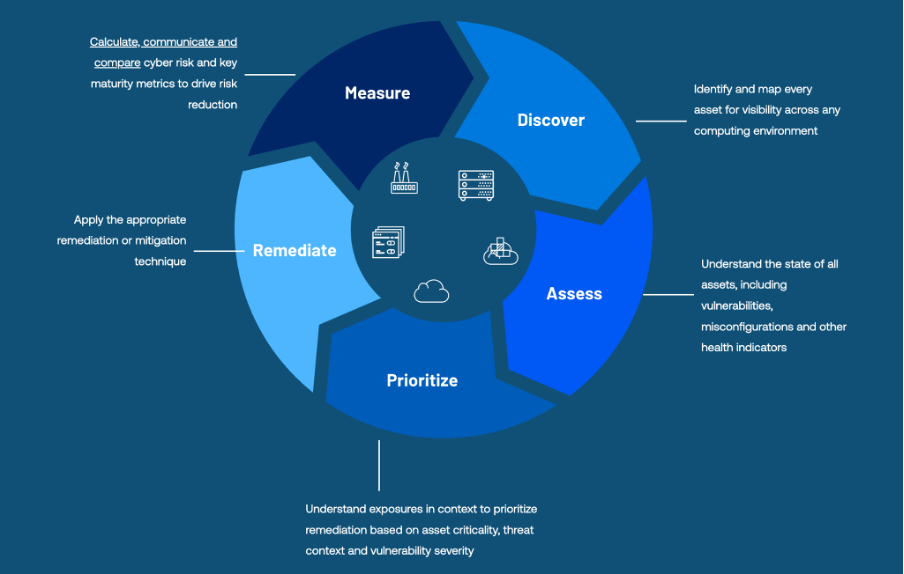
With these controls in place, organizations can streamline patch management, ensuring timely updates and removing unsupported software. By integrating Tenable’s risk-based vulnerability management solutions, businesses can proactively strengthen their security posture and reduce exposure to cyber threats.
Automated asset discovery: Finding the ghosts on your network
Automated asset discovery is the entry point for the “patch operating system” and “patch applications” mitigation strategies, enabling organizations to identify and track all devices, systems and applications within their environment. By leveraging host enumeration and OS fingerprinting scans, businesses can monitor known assets and detect unknown systems, ensuring nothing is left unaccounted for. These scans provide detailed insights against software running on various endpoints, helping security teams prioritize vulnerabilities based on risk.
Beyond traditional scanning, modern asset discovery extends to cloud environments and directory services. Cloud discovery connectors for Tenable Vulnerability Management integrate with platforms like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP) to continuously identify assets in dynamic cloud environments. Meanwhile, Active Directory and CMDB-based queries enhance visibility across enterprise networks by cross-referencing existing records with live asset scans. Together, these techniques create a comprehensive, real-time view of an organization’s digital footprint, strengthening security and compliance efforts. Tenable can simplify these queries through integrations with multiple connectors and products, such as Tenable Identity Exposure and Tenable for ServiceNow.
Understanding your external attack surface: Identifying online services and internet-facing systems
Under the context of the E8, ASD’s ACSC provides the following definition of an online service in its Essential Eight maturity model FAQ:
- “An online service is any service that is directly accessible over the internet, including those sitting behind a perimeter firewall. For example, a web portal, a cloud service or a network device (such as a firewall or VPN concentrator).”
The FAQ also provides the definition for an internet-facing server:
- “An internet-facing server is any server that is directly accessible over the internet.”
The Australian Government’s Department of Home Affairs also offers a definition of internet-facing systems or services in its Protective Security Policy Framework (PSPF) Direction 002-2024 on Technology Asset Stocktake as:
- “For the purposes of this Direction, an internet-facing system or service is directly accessed by untrusted or unknown entities over the internet, as opposed to a service or system accessed solely through the entity’s internal network.”
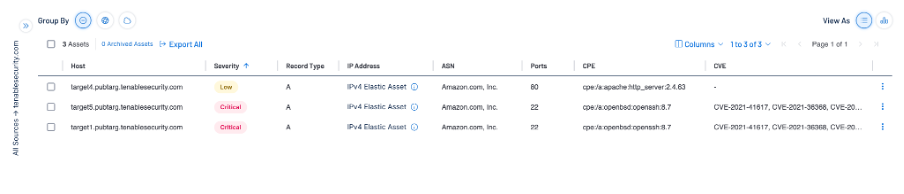
With these definitions in mind, the real challenge lies in assessing and categorizing systems in a way that aligns with their intent for the Australian cybersecurity landscape. That’s where Tenable Attack Surface Management comes into play. Simply plug in your organization’s domain and Tenable will suggest other potentially associated domains, helping you map your external attack surface with precision. By correlating domain names and IP addresses to systems within your technology stack, you start to gain a clear picture of your internet-facing systems.
Tenable Attack Surface Management even goes a step further, providing preliminary Common Platform Enumeration (CPE) identifiers for detected services; a precious advantage when prioritizing vulnerabilities for the E8. Combined with Tenable Web App Scanning, this creates a powerful foundation for identifying and managing internet-facing systems and online services, while also giving you a crucial edge in addressing real-world vulnerabilities that threat actors are already watching.
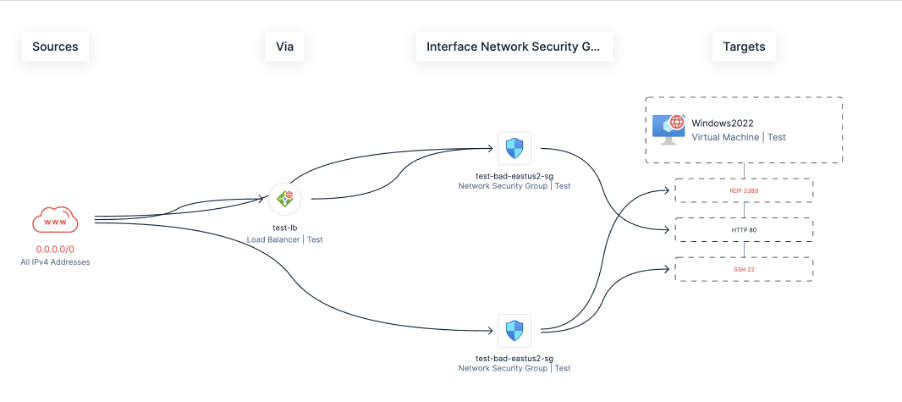
Meanwhile, Tenable Cloud Security seamlessly integrates with your cloud tenant, providing frictionless vulnerability assessments of infrastructure-as-a-service (IaaS), virtual machines, container registries and images. As an additional bonus as a cloud security posture management (CSPM) tool, it offers valuable insight against what systems have exposure to the internet, directly or indirectly. The screenshot below is an example of how Tenable Cloud Security can analyze and provide easy-to-consume information about which configurations within the environment expose an asset to the internet:
Prioritizing vulnerabilities: Because not all risks are created equal
Once you’ve charted out your internet-facing systems, the puzzle pieces start to align. Maintaining a record of these systems using dynamic asset lists or tags allows for smarter prioritization. By leveraging Common Vulnerability Scoring System (CVSS) v3 or, better yet, taking advantage of Tenable’s latest support for CVSSv4, organizations can zero in on zero-day operating system vulnerabilities, assessing them daily and mitigating them within 48 hours if they are critical or actively exploitable. Less urgent vulnerabilities enjoy a more forgiving two-week window.
For those looking for more effective prioritization, Tenable’s Vulnerability Priority Rating (VPR) narrows down the focus to what really matters. While CVSS broadly flags 60% of vulnerabilities as high or critical, Tenable VPR narrowed this to a focused 3% at its launch in 2019. With the latest AI-driven enhancements, Tenable VPR delivers twice the clarity and precision by leveraging real-time data to pinpoint the critical 1.6% of vulnerabilities that represent actual business risk. As the prioritization tasks unfold, the organization will have all the necessary context to ensure vulnerabilities are managed in line with the E8 framework, keeping security tight and cyber threats at bay.
The next question you’re probably asking is: Tenable has a strong emphasis on host-based vulnerability management, how do you separate operating system vulnerabilities from application vulnerabilities? Enter Common Platform Enumeration (CPE) queries — the key to cataloging and organizing your environment’s technology stack.
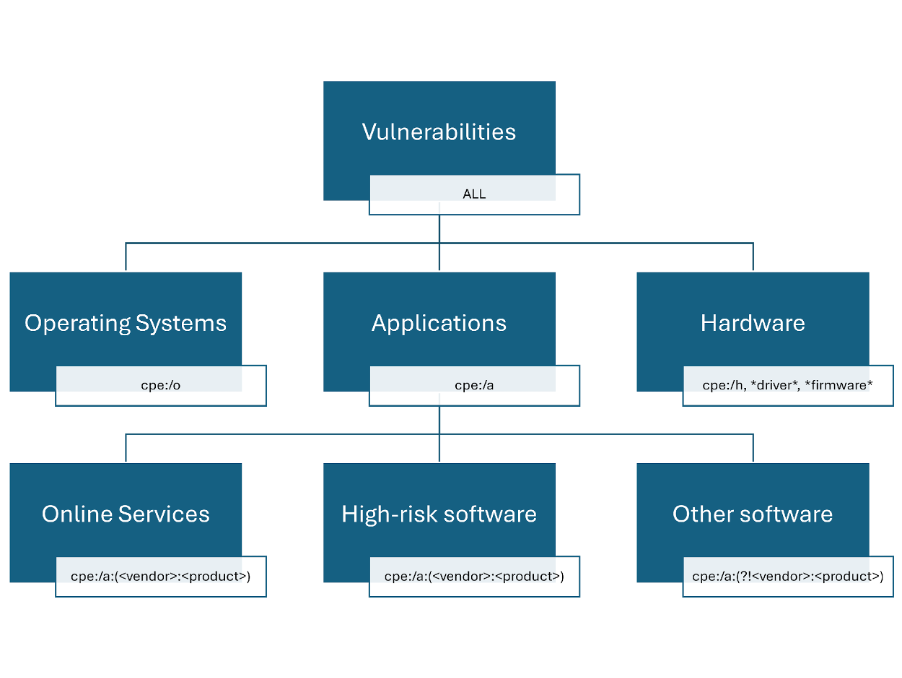
By leveraging CPE identifiers, organizations can pinpoint exactly which software and operating systems are present, making it easier to assign the right remediation timelines with structured vulnerability filtering.
Online services follow the same urgency as internet-facing operating systems, aligning with the 48-hour and 14-day remediation windows, respectively. With a structured software inventory and a clear categorization of commonly targeted applications by their CPE values, security teams can prioritize effectively. High-risk software gets the 14-day patching treatment, while lower risk applications enjoy a more relaxed one-month timeline. This approach ensures riskier vulnerabilities are addressed first, reinforcing your organization’s security posture and showing effective maturity for “patch applications.”
For more information on CPE, check out the below links:
- https://nvd.nist.gov/products/cpe
- https://community.tenable.com/s/article/Explaining-the-different-CPE-values-on-the-Tenable-Plugins-site
Measuring success: Security isn’t a destination, it’s a journey
Achieving an effective maturity level for patching operating systems and applications isn’t a one-time milestone; it’s an ongoing commitment. As threats evolve and systems shift, new vulnerabilities surface daily. Many organizations start strong, only to feel overwhelmed by the backlog revealed through successful vulnerability scanning. But that moment of discomfort is actually progress — it means you're finally seeing your security posture clearly, and that’s a win.
To support organizations on their maturity journey, Tenable has partnered with Thales Cyber Services, combining deep industry expertise to deliver targeted vulnerability management dashboards aligned with the Essential Eight. Within Tenable Vulnerability Management, three purpose-built dashboards have been introduced to support implementation and deliver clear, actionable reporting.
The design and formatting of these dashboards draw inspiration from ASD’s Blueprint for Secure Cloud, replicating its table structures and terminology to align with corresponding security controls. Each vulnerability context defined by the E8 is represented through repeatable widgets, and sample CPE queries are included to help most organizations quickly leverage these common patterns and accelerate their maturity journey from day one.
These dashboards don’t just track progress — they help organizations stay on course. By aligning with the Essential Eight and providing clear, actionable insights, they turn the journey of cybersecurity maturity into a measurable, repeatable process.
Conclusion: Strengthening cybersecurity with Tenable and the Essential Eight
By automating asset discovery, understanding external attack surfaces, and prioritizing vulnerabilities based on real-time data, organizations can achieve enhanced cybersecurity resilience. Tenable’s tools offer a comprehensive, risk-based approach that aligns with the Essential Eight, ensuring timely remediation and robust protection against cyber threats. With Tenable’s support, businesses can continuously improve their security posture, reduce exposure and stay ahead of emerging risks.
To learn more about how Thales Cyber Services can help organizations in Australia build a robust cybersecurity framework that ensures the protection of critical information and data visit us here.
Learn more
- Read the blog Narrowing the Focus: Enhancements to Tenable's VPR and How It Compares to Other Prioritization Models
- Download the white paper Enhancements to Tenable Vulnerability Priority Rating
- See what Tenable Vulnerability Management can do for you
- Risk-based Vulnerability Management
- Tenable Vulnerability Management




