by Carole Fennelly
August 10, 2023
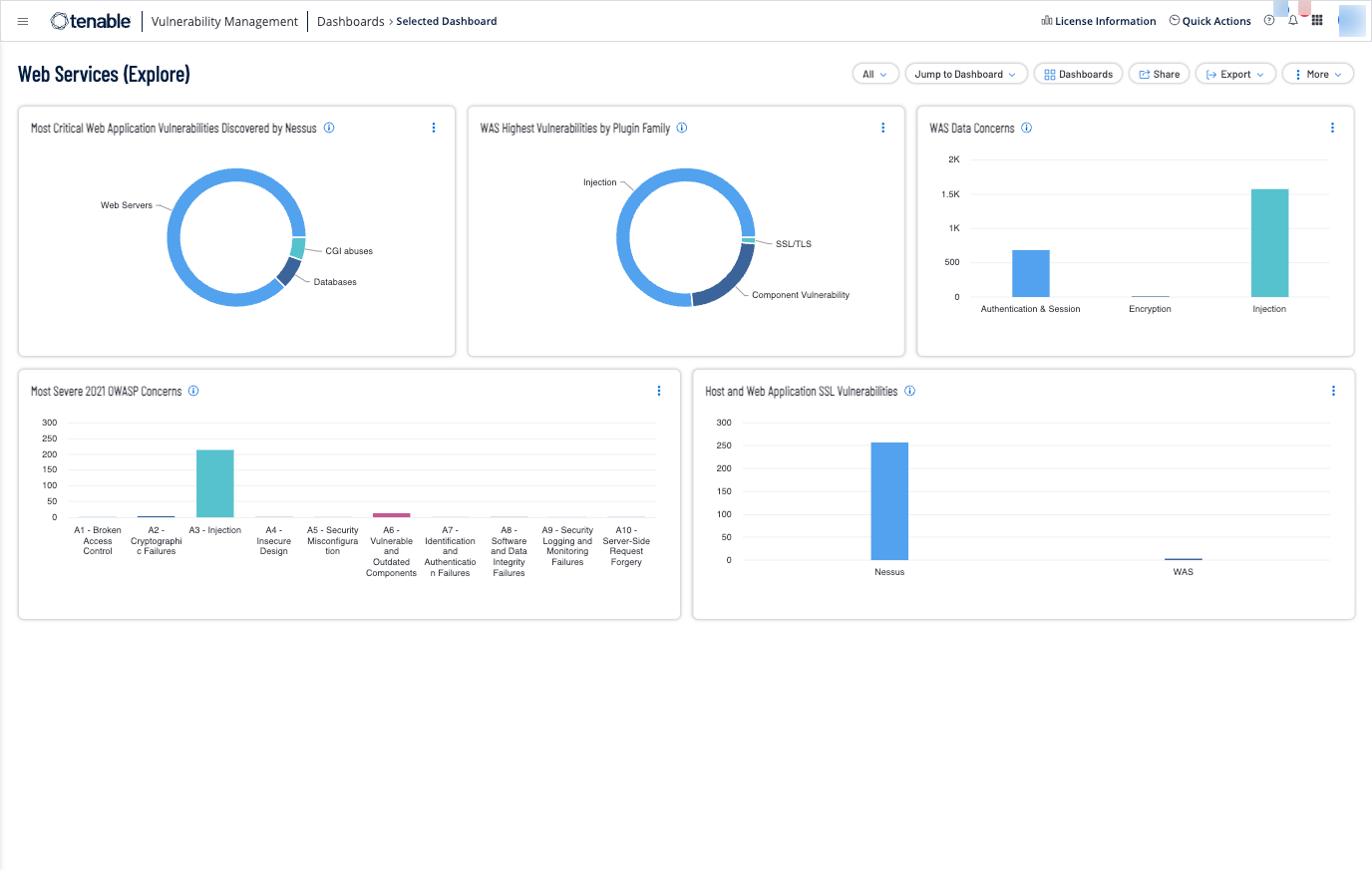
Applications enable users to interface and manipulate data in a consistent manner. Applications often have the ability to interface with system functions and critical databases to add or modify data. Attackers can leverage flaws in applications to bypass access controls. Web applications that are internet-facing are a particular concern since they present a global attack vector. This dashboard helps prioritize remediation efforts by presenting lists of web services to prioritize in various categories.
Security teams leverage data protection controls to maintain confidentiality, integrity, and availability of data. This dashboard enables security teams to review access controls, including authentication, encryption, and protection from data injection.
Security leaders need to SEE everything, PREDICT what matters most and ACT to address cyber risk and effectively align cybersecurity initiatives with business objectives. Tenable.io discovers and analyzes assets continuously to provide an accurate and unified view of an organization's security posture. The requirements for this dashboard are: Tenable Web App Scanning and Tenable Vulnerability Management (Nessus, NNM).
Widgets
Most Critical Web Application Vulnerabilities Discovered by Nessus – This widget uses credentialed Nessus scans to determine web server vulnerabilities. Credentialed scanning provides an internal view of web server health. The vulnerabilities typically found on web servers are detected by the following plugin families: Web Servers, CGI concerns, SMTP problems, remote file accessibility, FTP, RPC, Peer-To-Peer File Sharing, and Databases. This widget uses an additional filter to determine vulnerabilities with a Vulnerability Priority Rating of 7.0 or higher as Tenable's Research Team has determined that these vulnerabilities are actively being exploited. The requirement for this widget is: Tenable Vulnerability Management (Nessus).
WAS Highest Vulnerabilities by Plugin Family – This widget displays vulnerabilities by plugin family related to web applications. The results are filtered to only display critical and high vulnerabilities related to web applications. The requirements for this widget are: Tenable Web App Scanning.
WAS Data Concerns – This widget provides a summary view of the vulnerabilities that are associated with three primary focus areas: Authentication, Encryption, and Injection issues. Organizations need to periodically assess these data protection controls to maintain confidentiality, integrity, and availability of data. The requirement for this widget is: Tenable Web App Scanning.
Most Severe 2021 OWASP Concerns – This widget provides a summary view of the vulnerabilities that fall into any of the ten categories provided by the Open Web Application Security Project (OWASP). These vulnerabilities are also filtered by CVSSv3 Vector and Base Score. The score filter is set to only include vulnerabilities with a CVSSv3 score of 7 or greater, and the CVSSv3 Vectors of Access – Vector: Network, Access Complexity: Low, and Privileges Required: None. The requirement for this widget is: Tenable Web App Scanning.
Host and Web Application SSL Vulnerabilities – This widget displays vulnerabilities that are related to SSL and were detected by Nessus and Web Application Scanning (WAS). Data organized by Host (Nessus) and Webapp (WAS) and by state: Active, Resurfaced, New. The requirements for this widget are: Tenable Web App Scanning, and Tenable Vulnerability Management (Nessus).