by Carole Fennelly
August 23, 2023
Many organizations suffer breaches as a result of not following fundamental cyber hygiene practices. Key areas of concern are unsupported products, asset management/vulnerability remediation, and secure communications for sensitive information. A recent publication from the U.S. Cybersecurity Infrastructure Security Agency (CISA) outlines their Strategic Plan FY2023 - 2026 to provide a vision for the future of cybersecurity and help ensure technology products are safe and secure by design. This dashboard provides an overall picture of an organization’s fundamental cyber hygiene. The three goals identified in the Strategic Plan FY2023 - 2026 plan are:
- Address Immediate Threats
- Harden the Terrain
- Drive Security at Scale
Unsupported products, operating systems and applications are a major cause of data breaches. The proliferation of unsupported and end-of-life (EOL) products is a common security problem experienced across all organizations. As applications and operating systems reach EOL, vendors stop offering support, causing security and stability to decrease over time. A comprehensive summary of unsupported products in the environment is provided.
Another major concern is visibility into the assets in the environment and how effectively vulnerabilities on those assets are managed. As vulnerabilities are identified, remediation must be prioritized and tracked in accordance with organizational goals and Service Level Agreements (SLAs). Reviewing remediated vulnerabilities and the remediation time frame provides valuable information to the organization on the effectiveness of the risk remediation program. Vulnerabilities that are known to be exploitable are particularly dangerous, since there are exploit frameworks readily available to exploit them. Details are included on vulnerabilities where a patch to remediate the exposure was available more than a year ago.
Data on secure communication controls for sensitive information is provided. The status on SSL certificates that are expired or soon to be expired is displayed, along with SSL and TLS insecure communication exposures in the environment. Information about exposure of various types of potentially sensitive information is provided. Many organizations are unaware how much sensitive information is exposed, which enables attackers to tailor an attack path specifically targeting the organization, leading to data loss exposures.
Security leaders need to SEE everything, PREDICT what matters most and ACT to address cyber risk and effectively align cybersecurity initiatives with business objectives. Tenable.io discovers and analyzes assets continuously to provide an accurate and unified view of an organization’s security posture.
Widgets
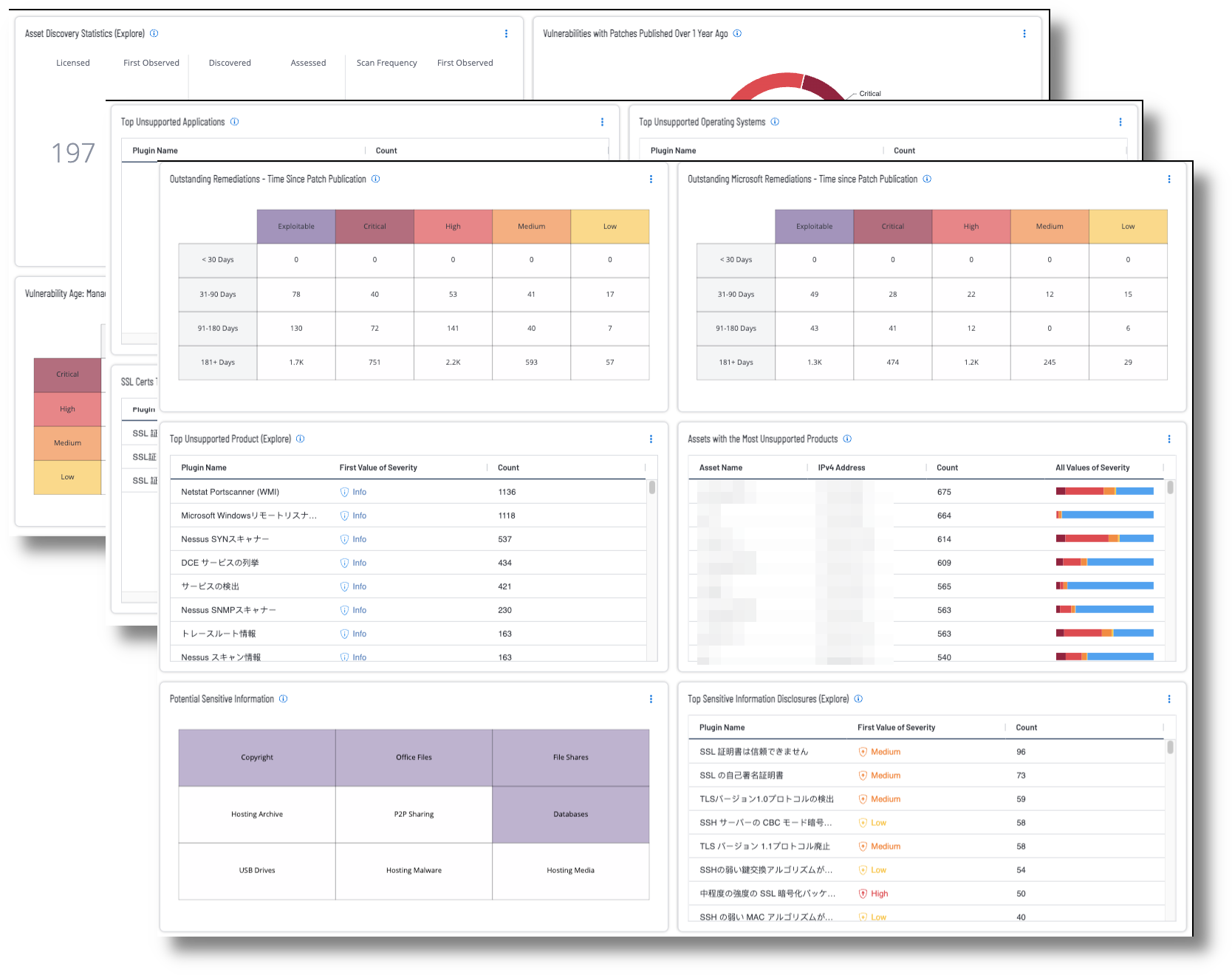
Asset Discovery Statistics:This widget displays statistics for Tenable.io licensed assets that were first observed less than 7 days ago and less than 30 days ago. The Tenable licensed asset limit determines the number of assets that can be scanned for vulnerabilities. The first section displays the total number of licensed assets. The middle column displays the total number of newly discovered assets that are not counted against the license. The last column displays the number of licensed assets that were successfully authenticated with credentials and scanned. More license count details can be viewed on the License page in Settings in Tenable Vulnerability Management. The requirements for this widget are: Asset Data from Tenable Vulnerability Management, Tenable Web App Scanning, Tenable Cloud Security, Tenable Lumin.
Vulnerabilities with Patches Published Over 1 Year Ago: This widget provides a quick snapshot of the older vulnerabilities detected in the organization. The vulnerabilities in the chart have patches that were published over one year ago. Analysts can use this chart for a quick overview to help plan vulnerability remediation or risk mitigation efforts. The requirement for this widget is: Tenable Vulnerability Management (Nessus).
Vulnerability Age: Managing SLAs: This widget provides a view of vulnerabilities based on severity and age. The columns display counts of vulnerabilities that have been published within the specified time period and are present in the organization. The rows display the severity level of the vulnerability. Organizations can use this information to determine their compliance with organizational policy and Service Level Agreements (SLAs). For example, if an organization has a SLA that states Critical/High vulnerabilities must be patched within 45 days, any data displayed in the first three columns and two rows indicates non-compliance with the SLA. Vulnerability age is determined from the time the vulnerability was published. The requirement for this widget is: Tenable Vulnerability Management (Nessus, NNM).
Vulnerabilities by State: This widget provides a view into the vulnerability life cycle. Tracking vulnerabilities through each state demonstrates the progress of risk mitigation efforts. Each column represents an elevated level of risk. The first column, Exploitable, shows the count of vulnerabilities that are known to be exploitable regardless of severity. The next three columns show vulnerability counts based on severity. The requirement for this widget is: Tenable Vulnerability Management (Nessus, NNM).
Outstanding Remediations - Time Since Patch Publication: This widget displays the total count of missing patches across the environment. The matrix is comprised of five columns. The first column provides a count of the vulnerabilities that are exploitable, and the last four columns provide counts of vulnerabilities based on severity levels. Each row filters the vulnerabilities based on the patch publication date of less than 30 days ago, 31-90 days, 91-180 days, and greater than 181 days.The requirement for this widget is: Tenable Vulnerability Management (Nessus, NNM).
Outstanding Microsoft Remediations - Time since Patch Publication: This widget displays the total count of missing patches related to Microsoft Security Bulletins using the Windows: Microsoft Bulletins and Windows plugin families. The matrix is comprised of five columns. The first column provides a count of the vulnerabilities that are exploitable, and the last four columns provide counts of vulnerabilities based on severity levels. Each row filters the vulnerabilities based on the patch publication date of less than 30 days ago, 31-90 days, 91-180 days, and greater than 181 days. The requirement for this widget is: Tenable Vulnerability Management (Nessus, NNM).
Top Unsupported Product: This widget provides a sorted list of the most prevalent unsupported products across the environment, sorted from the highest count of unsupported products to the lowest. The first column displays the plugin name that detected the unsupported software, followed by the severity level and then the count. The requirement for this widget is: Tenable Vulnerability Management (Nessus, NNM).
Assets with the Most Unsupported Product: This widget lists the assets that currently have the most unsupported products. The list is sorted with the assets that have the highest count of unsupported products at the top. Displayed is the asset name, IPv4 address, count of unsupported products and a bar that displays all detected values of severity. Ghosting over the severity bar displays the percentage of criticality levels detected for the vulnerabilities. The requirement for this widget is: Tenable Vulnerability Management (Nessus, NNM).
Potential Sensitive Information: This widget displays indicators to detect various types of potentially sensitive information. Displayed are indicators for copyright information, file shares, databases, peer to peer file sharing, USB Drives, websites hosting potentially sensitive information, and Office files. An indicator will be highlighted if the information was detected during an active scan and can be selected to display more details. The requirement for this widget is: Tenable Vulnerability Management (Nessus, NNM).
Top Sensitive Information Disclosures: This widget reports on potential sensitive information exposures that require investigation. The list is sorted with the plugins that have detected the highest count of sensitive information at the top. Displayed are the plugin name, severity, and count of sensitive information detected. The requirement for this widget is: Tenable Vulnerability Management (Nessus, NNM).
SSL Certs That are Expired or Soon-to-Expire: This widget lists assets that have SSL Certificates that have already expired or will soon expire. The SSL Certificate Expiry result lists the assets where the SSL Cert has already expired. The SSL Certificate Expiry - Future Expiry and SSL Certificate Chain Contains Certificates Expiring Soon results provide information on assets that will need to have certificates replaced soon either within the certificate chain or for the remote service itself. The requirement for this widget is: Tenable Vulnerability Management (Nessus, NNM).
SSL-TLS Insecure Communications Issues and Info: This widget lists the current SSL and TLS insecure communication exposures in the environment. The list is sorted with the highest count of exposures at the top. Displayed are the plugin name, severity, and count. The requirement for this widget is: Tenable Vulnerability Management (Nessus, NNM).