by Carole Fennelly
November 7, 2022
Exploits leveraged in attacks are imported into various tools and services when the attack is made public. Common exploit frameworks are easy to obtain and are used by security researchers and malicious attackers. Security analysts can effectively reduce risk to the organization by analyzing an exploit’s source tool and the most common targets.
The Cyber Security Framework (CSF) category ID.RA (Risk Assessment) provides guidance to organizations on cyber risk and helps to define recommended actions for the security operations team. The ID.RA-1 category states requirements for the National Institute of Standards and Technology (NIST) 800-53 control CA-8 Penetration Testing. The control states “Penetration testing is a specialized type of assessment conducted on information systems or individual system components to identify vulnerabilities that could be exploited by adversaries.” Some security teams leverage exploitation frameworks such as Core Impact, Canvas or others to help with this control. Tenable.io identifies which vulnerabilities are exploitable by different frameworks.
This dashboard provides a centralized view of which frameworks exploit vulnerabilities found in the organization’s network. In addition to the exploitable attributes, other attributes are used such as plugin family and vulnerability state. Using the dashboard to drill down into the Vulnerability Workbench displays other attributes such as CPE, VPR Key Drivers, and CVSS Vectors. Each of these filters helps the security team to narrow the focus and discover risks that may require prioritization over other vulnerabilities.
Security leaders need to SEE everything, PREDICT what matters most and ACT to address cyber risk and effectively align cybersecurity initiatives with business objectives. Tenable.io discovers and analyzes assets continuously to provide an accurate and unified view of an organization’s security posture. The requirements for this dashboard are: Tenable.io Vulnerability Management (Nessus, NNM).
Widgets
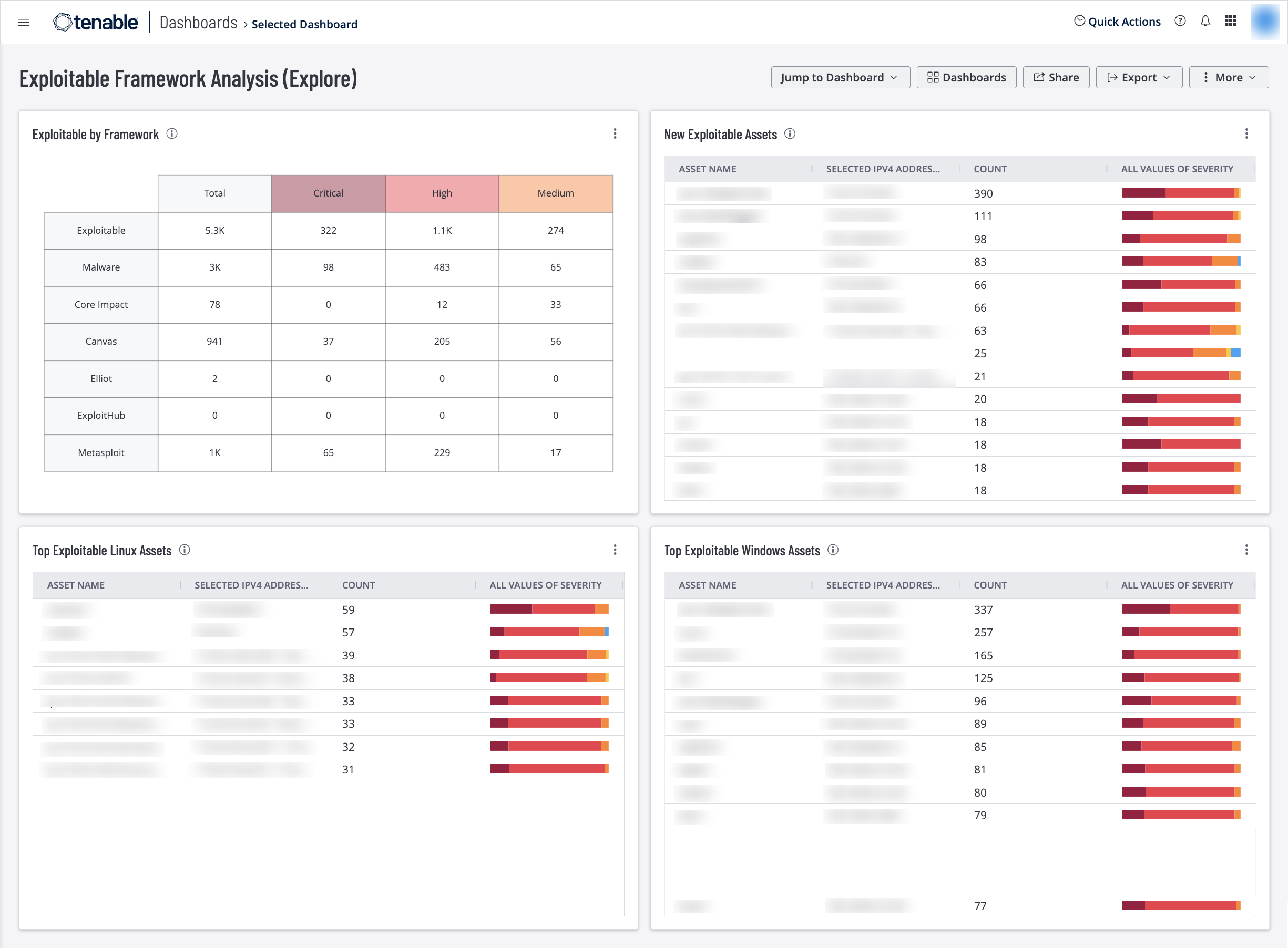
Exploitable by Framework – This widget provides a summary of exploitable vulnerabilities by framework. Exploitation frameworks, such as Metasploit, and Canvas, are designed to detect and exploit software and hardware vulnerabilities in target systems. This widget helps security teams discover risks that may require prioritization over other vulnerabilities. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
New Exploitable Assets – This widget displays the top 20 Assets with Exploitable Vulnerabilities that have been newly discovered. Vulnerabilities marked as New have not been seen before on an asset. A vulnerability can be marked as New if that vulnerability had not been discovered before in a scan, or if that vulnerability was recently published and discovered on a new scan. This allows technicians to see previously secure assets with new exploitable vulnerabilities. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
Top Exploitable Linux Assets – This widget displays a list of the top Linux/Unix assets that have exploitable vulnerabilities, with a Vulnerability Priority Rating (VPR) greater than or equal to 7.0.
Exploitable Windows Assets – This widget widget displays a list of the top Windows assets that have exploitable vulnerabilities, with a Vulnerability Priority Rating (VPR) greater than or equal to 7.0. Security technicians can use this information to focus mitigation efforts by operating system. This allows technicians to notify the asset administrator of the threats posed to their assets. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).