by Cody Dumont
January 6, 2015
Managing workstation vulnerabilities is often so time intensive that infrastructure vulnerabilities may be overlooked. Tenable Security Center provides the ability to track vulnerabilities and logs from VMware solutions. This dashboard provides a single view of the current threats to virtual infrastructure. When analyzing threats to the virtual infrastructure, the security professional should include active, passive, and event based detection methods. Additionally, Nessus provides the ability to perform configuration audits by using the API in vCenter or by directly querying the hypervisors.
The dashboard and its components are available in the Security Center Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Security Center Feed under the category Threat Detection & Vulnerability Assessments.
The dashboard requirements are:
- Security Center 4.8.1
- Nessus 6.1.1
- NNM 4.0.3
Organizations use active and passive scanning to identify both hypervisors and virtual machines. Once the hypervisors are properly identified, they can be scanned and their configurations audited using Nessus. When performing active scans of the hypervisors, SecurityCenter CV uses the API in vCenter or the ESXi API to analyze the configuration and detect vulnerabilities. The VMSA number identifies vulnerabilities found. VMware publishes VMware Security Advisories (VMSAs) to document remediations for security vulnerabilities identified in VMware products.
Security Center supports tight integration and API extensibility with virtualization systems, malware defenses, patch management tools, BYOD, and firewalls. NNM provides deep packet inspection to continuously discover and track users, applications, cloud infrastructure, trust relationships, and vulnerabilities. When combined, all of these features provide a more complete view into threat detection and vulnerability management.
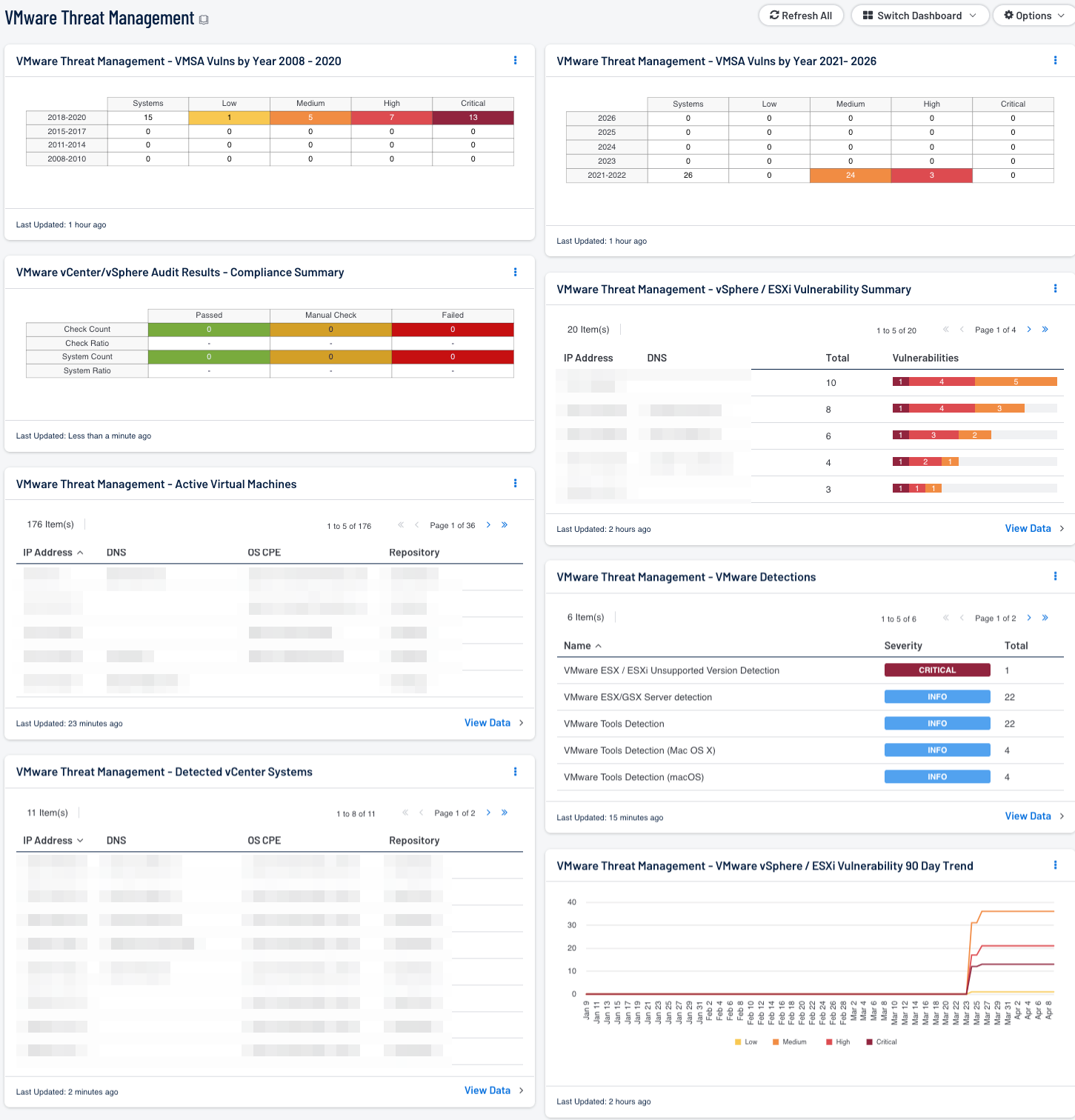
VMware Threat Management - Detected vSphere Systems: This component displays a list of VMware vSphere systems detected on the network. Nessus plugin 57396 identifies systems running VMware vSphere. The table provides the IP address and the DNS name for each system. The table is sorted by IP address, and shows up to 999 entries.
VMware vCenter/vSphere Audit Results - Compliance Summary: When performing configuration audit of systems in accordance with a GRC program, security analysts can benefit from a summary view of the data set. The VMware vCenter/vSphere Compliance Summary table provides a high-level view of the VMware vCenter/vSphere compliance status.
VMware Threat Management - VMSA Vulns by Year 2008 – 2020: This component lists VMware Security Advisories (VMSA) according to year and severity level. The years covered in this component are 2008 – 2020. VMware publishes VMSAs to document remediations for security vulnerabilities identified in VMware products.
VMware Threat Management - VMSA Vulns by Year 2021 – 2026: This component lists VMware Security Advisories (VMSA) according to year and severity level. The years covered in this component are 2021 – 2026. VMware publishes VMSAs to document remediations for security vulnerabilities identified in VMware products.
VMware Threat Management - Active Virtual Machines: This table provides a list of VMware active virtual machines. Using plugin 57397 (VMware Active Virtual Machines) and credentials, Nessus has identified the following systems running VMware vSphere. When scanning vCenter, plugin 57397 will attempt to discover active virtual machines. If virtual machines are detected, then a list of the machines will be displayed along with their operational status.
VMware Threat Management - vSphere / ESXi Vulnerability Summary: This component provides a list of vulnerable vSphere or ESXi servers detected on the network. The table uses the IP Summary tool and displays columns for the IP address, DNS Name, Total vulnerability count, and the vulnerability bar. The colors in the bar indicate severity and are as follows: info is blue, low is green, medium is yellow, high is orange, and critical is red. The number located within each color represents the number of vulnerabilities of that severity detected. The filter detects vulnerabilities with VMSA as part of the plugin name. VMware publishes VMware Security Advisories (VMSAs) to document remediations for security vulnerabilities identified in VMware products.
VMware Threat Management - VMware Detections: This table provides VMware infrastructure detections using several different methods. Using active and passive, this table identifies several different elements of a VMWare deployment, such as VMware Workstation or Fusion, and infrastructure devices such as ESXi and vCenter.
VMware Threat Management - VMware vSphere / ESXi Vulnerability 90 Day Trend: The chart provides a summary of vulnerability count during the past 90 days for VMware Security Advisories (VMSA). VMware publishes VMware Security Advisories (VMSAs) to document remediations for security vulnerabilities identified in VMware products. The chart displays a line for each severity level, where low is green, medium is yellow, high is orange, and critical is red. The data points are calculated every 24 hours to allow analysts to more accurately detect changes in the vulnerability count over time.