by David Schwalenberg
May 18, 2016
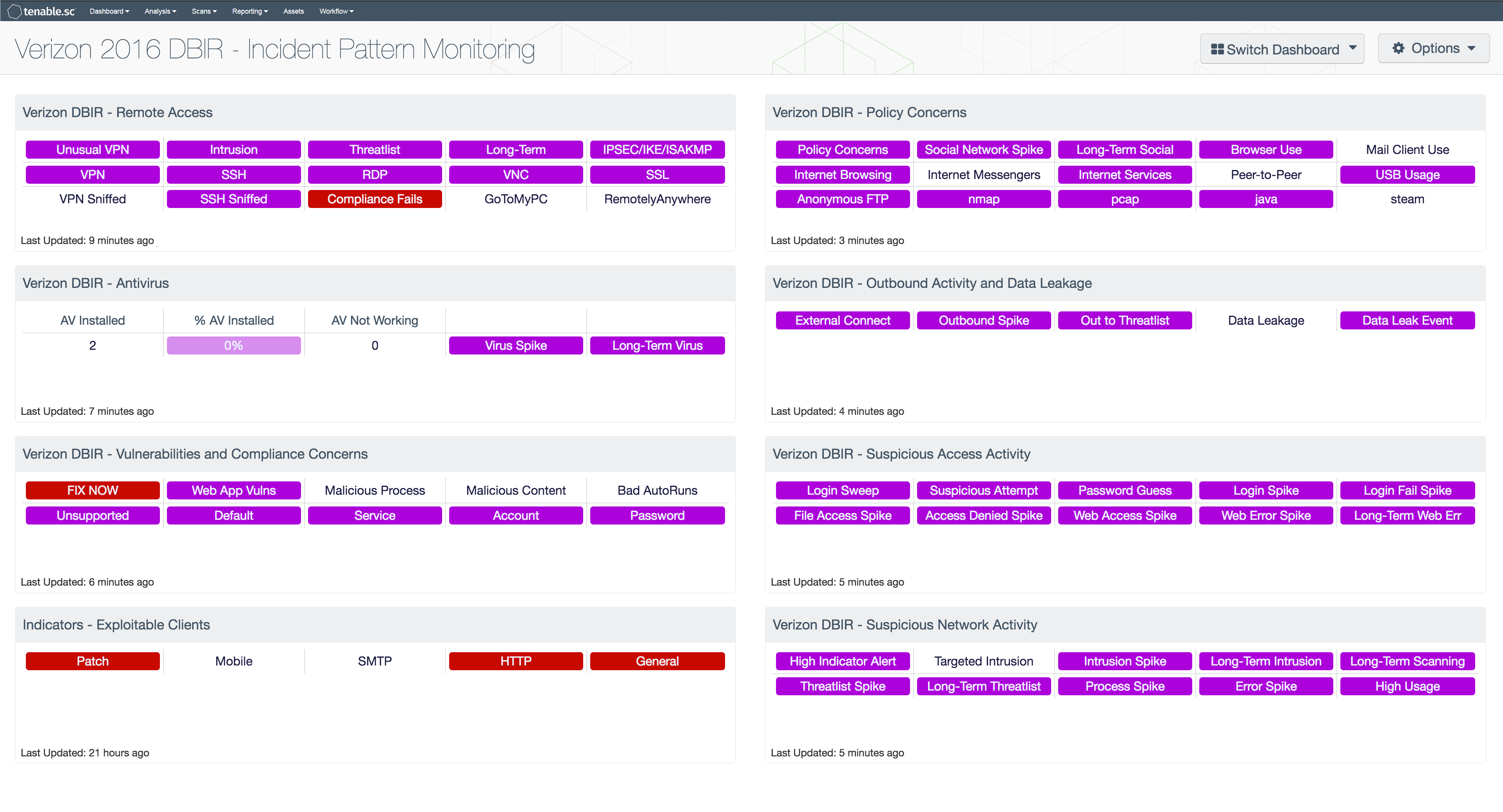
The Verizon Data Breach Investigation Report (DBIR), first published in 2008, is an annual publication that analyzes information security incidents from public and private organizations, with a focus on data breaches. Data breaches continue to have a major financial impact on organizations, as well as an impact on their reputations. Tenable Network Security offers dashboards that can assist organizations in meeting many of the recommendations and best practices in the DBIR.
The 2015 DBIR notes that as in previous years, a vast majority of all attacks fall into a few basic patterns. Looking back to the 2014 DBIR for these patterns, suggestions are given for monitoring the network. This dashboard displays several components that can assist an organization in monitoring its network to reduce the successfulness of these attack patterns and so reduce its chances of a data breach.
The DBIR recommends monitoring remote access, preventing web browsing, e-mail, social network activity, and the like on Point-of-Sale (POS) systems, deploying an antivirus (AV) solution, monitoring outbound connections, watching for data exfiltration, monitoring changes, and looking for suspicious user and network activity. The matrix components in this dashboard can assist the organization in monitoring all of these areas.
Clicking on a highlighted indicator in a matrix will bring up the analysis screen to display details on the detections and events and allow further investigation. Setting the tool to IP Summary will display the systems on which the detections and events are present.
Certain devices or subnets on a network may have stricter policies than others. For example, Point-of-Sale systems should not be used for reading e-mail, whereas that is a valid activity for normal workstations. To enable more focused monitoring, consider using asset lists. With asset lists, dashboards can be customized to report only on data from a subgroup of machines, rather than the entire network. For example, an asset list of POS systems can be created, either as a static asset list if all POS systems are in one or more specific subnets, or as a dynamic asset list based on installed software or some other system parameter; this asset list can then be applied to the Verizon 2015 DBIR - Incident Pattern Monitoring dashboard. Then any indications in the Remote Access and Policy Concerns components will be very significant, as the DBIR notes that that sort of activity should be restricted on POS systems. For more information on creating and using assets, see the Tenable.sc User's Guide.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Security Industry Trends.
The dashboard requirements are:
- Tenable.sc 4.8.2
- Nessus 8.5.1
- NNM 5.9.0
- LCE 6.0.0
Tenable.sc Continuous View (CV) is the market-defining continuous network monitoring platform. Tenable.sc CV includes active vulnerability detection with Nessus and passive vulnerability detection with the Nessus Network Monitor (NNM), as well as log correlation with the Log Correlation Engine (LCE). Using Tenable.sc CV, an organization will obtain the most comprehensive and integrated view of its network, in order to best protect its network from data breaches.
Listed below are the included components:
- Verizon DBIR - Remote Access - The Verizon DBIR notes that it is important to restrict remote access to systems. This matrix assists the organization in monitoring its remote access. The Unusual VPN indicator is highlighted purple when a VPN login originates from an IP address that is not normal for the user ID. Multiple indicators highlight VPN, SSH, RDP, VNC, and SSL traffic events within the last 72 hours, including potential intrusion events, events associated with known bad IP addresses (threatlist), and long-term events. The VPN Sniffed and SSH Sniffed indicators are highlighted purple if those protocols, respectively, are passively detected on the network. The Compliance Fails indicator is highlighted red if there are any remote access compliance failures. The GoToMyPC and RemotelyAnywhere indicators are highlighted purple if those applications are detected on the network. Clicking on a highlighted indicator will bring up the analysis screen to display details on the detections and events and allow further investigation.
- Verizon DBIR - Antivirus - The Verizon DBIR advocates deploying an antivirus solution. This matrix assists the organization in monitoring its antivirus deployment. The AV Installed column displays the number of scanned hosts that have AV installed and working properly; the % AV Installed column displays a bar graph of the ratio of systems with AV installed to total systems scanned. The AV Not Working column displays the number of scanned hosts that have AV installed, but it is not working properly or not up to date. The Virus Spike indicator is highlighted purple if a large spike in virus activity was detected in the last 72 hours. The Long-Term Virus indicator is highlighted purple if in the last 72 hours an IP address has been the source of virus or malware events continuously for more than 20 minutes. Clicking on a highlighted indicator will bring up the analysis screen to display details on the detections and events and allow further investigation.
- Verizon DBIR - Vulnerabilities and Compliance Concerns - This matrix assists the organization in monitoring its network for vulnerabilities and compliance concerns. The FIX NOW indicator is highlighted red if any vulnerabilities are found that can be exploited by Metasploit. These vulnerabilities must be mitigated immediately, as the Verizon DBIR notes that a vulnerability being added to Metasploit is a reliable predictor of exploitation in the wild. The bottom row of indicators in the component highlight vulnerabilities and non-passing compliance checks that contain specific keywords; these indicators can assist in discovering unsupported products, insecure account and password settings, and more. Indicators can be removed or new indicators added as desired. Clicking on a highlighted indicator will bring up the analysis screen to display details on the vulnerabilities and allow further investigation.
- Verizon DBIR - Changes - This matrix assists the organization in monitoring changes on its network. Each indicator is based on one or more LCE change events; the indicator is highlighted purple if the event occurred in the last 72 hours. Many of these indicators highlight new additions to the network, such as new hosts, new software, and new open ports. Indicators are also included to highlight firewall and router changes. Any new additions or changes should be investigated to determine if they are authorized. The Change Spike indicator is highlighted if a large number of changes were detected compared to previous change event rates. The File Integrity Spike indicator is highlighted if a large number of file change events were detected. Clicking on a highlighted indicator will bring up the analysis screen to display details on the change events and allow further investigation.
- Indicators - Exploitable Internet Services - This component indicates if NNM has detected any Internet facing exploitable services.
- Verizon DBIR - Policy Concerns - The Verizon DBIR notes that certain activities should be restricted on certain hosts, such as playing games or checking e-mail on POS systems. This matrix assists the organization in monitoring potential policy violations on its network, including general policy concerns, social network activity, browser and mail client use, P2P activity, USB usage, and more. These indicators are highlighted purple based on active and passive detections, and on events that occurred in the past 72 hours. Active and passive detections of allowed anonymous FTP are highlighted; the Verizon DBIR notes that unsecured FTP servers can be a great risk. The bottom right four indicators in the component highlight installed software such as nmap and pcap that may be considered against policy on certain systems. Indicators can be removed or new indicators added as desired. Clicking on a highlighted indicator will bring up the analysis screen to display details on the detections and events and allow further investigation.
- Verizon DBIR - Outbound Activity and Data Leakage - The Verizon DBIR advocates monitoring outbound connections to prevent data exfiltration. This matrix assists the organization in monitoring its outbound activity. The External Connect indicator is highlighted purple if outbound connections are passively detected from a system inside the network (as defined by the "Monitored Network IP Addresses and Ranges" NNM configuration parameter) to a system outside the network. The Outbound Spike indicator is highlighted purple if a large spike in outbound connections was detected in the last 72 hours. The Out to Threatlist indicator is highlighted purple if traffic outbound to a known bad IP address was detected in the last 72 hours. The Data Leakage and Data Leak Event indicators are highlighted purple if data leakage was detected passively or via events, respectively. Clicking on a highlighted indicator will bring up the analysis screen to display details on the detections and events and allow further investigation.
- Verizon DBIR - Suspicious Access Activity - This matrix assists the organization in monitoring for suspicious access activity such as suspicious login activity and spikes in file and web accesses. Each indicator is based on one or more LCE events; the indicator is highlighted purple if the event occurred in the last 72 hours. Login spikes can occur when an account is compromised and shared and used by many hackers. Login failure spikes may indicate brute-force password guessing. File access and access denied spikes may indicate suspicious access to files. Web access spikes may indicate a busier-than-normal web server or more Internet browsing. Web error spikes and long-term Web errors can identify web application scanning and web probes. Clicking on a highlighted indicator will bring up the analysis screen to display details on the events and allow further investigation.
- Verizon DBIR - Suspicious Network Activity - This matrix assists the organization in monitoring for suspicious network activity. Each indicator is based on one or more LCE events; the indicator is highlighted purple if the event occurred in the last 72 hours. High Indicator Alert indicates that a suspicious sequence of ten or more events occurred. The intrusion indicators highlight network intrusion activity; Targeted Intrusions are those intrusions that can be correlated with current network vulnerabilities, and so represent attacks that are likely to succeed. The threatlist indicators highlight interactions with known bad IP addresses. Process spikes may indicate new programs, programs used in new ways, or even malicious software. Error spikes may indicate hardware failures, misconfigurations, or attacks. High usage (CPU, disk, memory, or process load) may indicate underpowered hardware, malware, or DoS attacks. Clicking on a highlighted indicator will bring up the analysis screen to display details on the events and allow further investigation.