by Cody Dumont
August 4, 2015
Securing Out of Band Management (OOBM) access is crucial to network security. OOBM allows network admins to gain access to critical systems that are frequently located at remote or isolated locations. SecurityCenter Continuous View (CV) provides risk analysis on OOBM devices or systems.
The dashboard and its components are available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Monitoring.
The dashboard requirements are:
- SecurityCenter 4.8.2
- Nessus 6.3.6
- Compliance Data
Many network design philosophies include an OOBM network. This network is segmented from regular traffic and in cases is described as the management plane, which is dedicated to management ports and other related network channels. The devices on this segment provide administrators with the ability to monitor servers and network devices remotely regardless if the device is powered on, powered off, non-responsive or when not accessible by the standard network channel.
The OOBM ports can come in a many varieties, such as TTY serial ports, direct console access, and dedicated Ethernet IP management ports. Intelligent Platform Management Interface (IPMI) is the most common method of using OOBM with servers or appliances. The IPMI uses the Baseboard Management Controller (BMC), which has its own power source, communication port, and operating system. A common practice with IPMI vendors is to set a well-documented default username and password. The default usernames and passwords are easily searchable on the internet or in their owner manuals. Some vendors of IPMI devices are Dell DRAC/iDRAC, HP Lights-Out (iLO), and IBM Remote Supervisor.
This dashboard provides several components that are related to OOBM and IPMI. Some of the components are general detection and others are focused on a specific vendor. Many of the indicators will change color to match the severity, such as red for critical, orange for high, and so on. However, if the severity can not be determined by the filter, the indicator will turn purple.
SecurityCenter Continuous View (CV) provides continuous network monitoring to identify vulnerabilities, reduce risk, and ensure compliance. SecurityCenter CV enables the analysts to react to advanced threats, zero-day vulnerabilities, and new forms of regulatory compliance. With more supported technologies than any other vendor including operating systems, network devices, hypervisors, databases, tablets, phones, web servers, and critical infrastructure, SecurityCenter CV users are more prepared for the dynamic changing environment.
Components
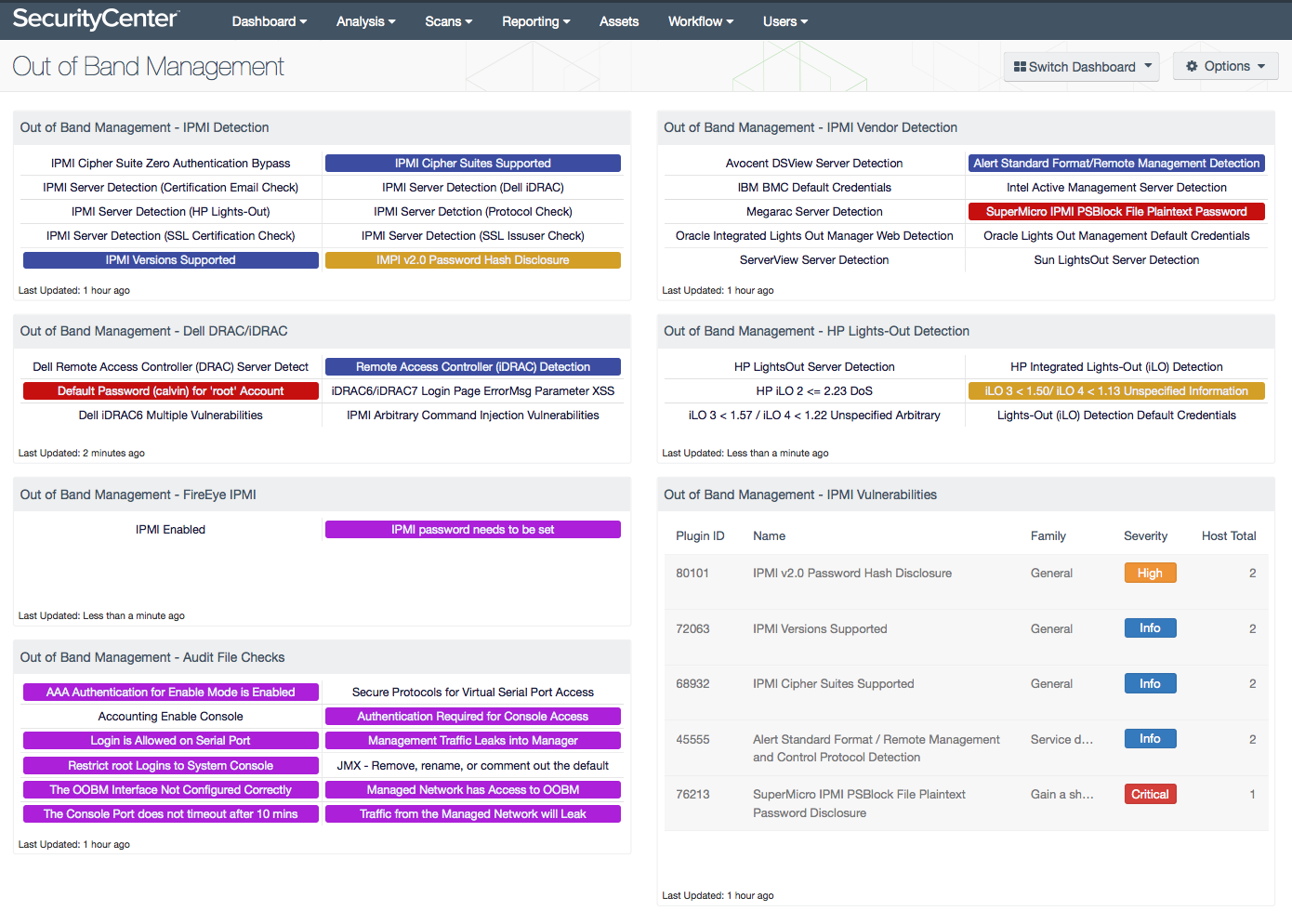
Out of Band Management - IPMI Detection: This component displays several indicators for IPMI vulnerabilities that are associated with either the General or Generic plugin families. For example, the IPMI Server Detection (SSL Issuer Check) indicator detects an SSL service that is typically used with IPMI for remote management.
Out of Band Management - Dell DRAC/iDRAC: This component provides indicators for the different Dell DRAC/iDRAC IPMI vulnerabilities. These six Dell DRAC/iDRAC vulnerabilities are Dell DRAC detection, Dell iDRAC detection, default password, Login Page error, iDRAC 6 vulnerabilities, and Dell iDRAC arbitrary command injections. Helping an administrator understand the IPMI security risk on DRAC/iDRAC card will benefit the threat landscape on the network.
Out of Band Management - FireEye IPMI: This component displays FireEye IPMI vulnerabilities. This component will detect if the FireEye IPMI is enabled and if the FireEye password needs to be changed.
Out of Band Management - Audit File Checks: This matrix displays several indicators for audit results related to Out of Band Management (OOBM). This component is using specific plugin names to detect Out of Band audit checks.
Out of Band Management - IPMI Vendor Detection: This component provides several indicators with IPMI remote management access from several vendors. These IPMI vendors are Megarac, SuperMicro, Intel Active Management, Oracle Lights Out, Sun Lights Out, IBM, ServerView, and Avocent DSView.
Out of Band Management - HP Lights-Out Detection: This component displays several indicators for HP Lights-Out devices. HP Integrated Lights-Out (iLO) is the IPMI system board of a host server. HP iLO allows super users or administrators access to HP server hardware, firmware, and communication interfaces. HP built security features into iLO, but new vulnerabilities are discovered all the time. Each indicator will change background color depending on their severity. A blue indicator is for information severity, a green indicator is for low severity, a yellow indicator is for medium severity, an orange indicator is for high severity, and red indicators are for critical severities.
Out of Band Management - IPMI Vulnerabilities: This component will display a table of the top 100 IPMI vulnerabilities. Each row in this table will display Plugin ID, Name, Family, Severity, and Total hosts associated with IPMI vulnerabilities. This displays sorted by total host count in ascending order. This will help an administrator understand how many hosts are affected by each of the IPMI vulnerabilities.