by Ben Smith
February 27, 2020
The United Arab Emirates’ (UAE) National Electronic Security Authority (NESA) Information Assurance Standards state that various information security policies should be in place across the organization and should comply with policies and with any other standards that are applicable. The NESA standard is a composite of many different types of controls and was derived from similar standards including the ISO 27000 standards, NIST 800, and CIS Controls. NESA makes clear that organizations must comply with all applicable policies, laws, and compliance standards. Many controls require the organization to have appropriate policies covering all aspects of information security. On this dashboard, the CISO can easily see the organization’s current compliance state with NESA and how that compares to other similar standards.
Ensuring that policies are in place for all aspects of information security is another goal of NESA. Tenable.sc provides visibility into system configuration policies and vulnerability management controls. The existence and adherence to policies are the result of a healthy vulnerability management program. The CISO can then see the frequency with which vulnerabilities of varying criticalities are discovered in the environment. Total vulnerabilities in the organization’s environment versus vulnerabilities that have been previously mitigated are easily understood.
NESA makes clear that organizations are to perform their own risk analysis. The organization should rely on a risk ranking for all risks in the environment and utilize that information when deciding patching necessity and frequency. Vulnerability Priority Rating (VPR) quantifies how urgently a vulnerability should be remediated. The CISO can easily understand risks that have been ranked this way versus CVSS score. All environments being different, the CISO or security consultant can also understand which risks have changed to a different criticality in the environment by looking at risks that have been recast.
A compliance program requires the ability to track success and failure over time. NESA requires the tracking of success and failure over time. The CISO can efficiently understand how compliance with the NESA standard has changed over a recent time frame by checking a trend over recent timeframe.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Executive.
The dashboard requirements are:
- Tenable.sc 5.12.0
- Nessus 8.9.0
- Compliance Data
Tenable.sc Continuous View (CV) is the market-defining On-Prem Cyber Exposure Platform. Tenable.sc CV provides the ability to continuously Measure an organization’s policy compliance. Tenable.sc provides customers with a full and complete Cyber Exposure platform for completing an effective Cyber Hygiene program prescribed by NESA standard.
This dashboard contains the following components:
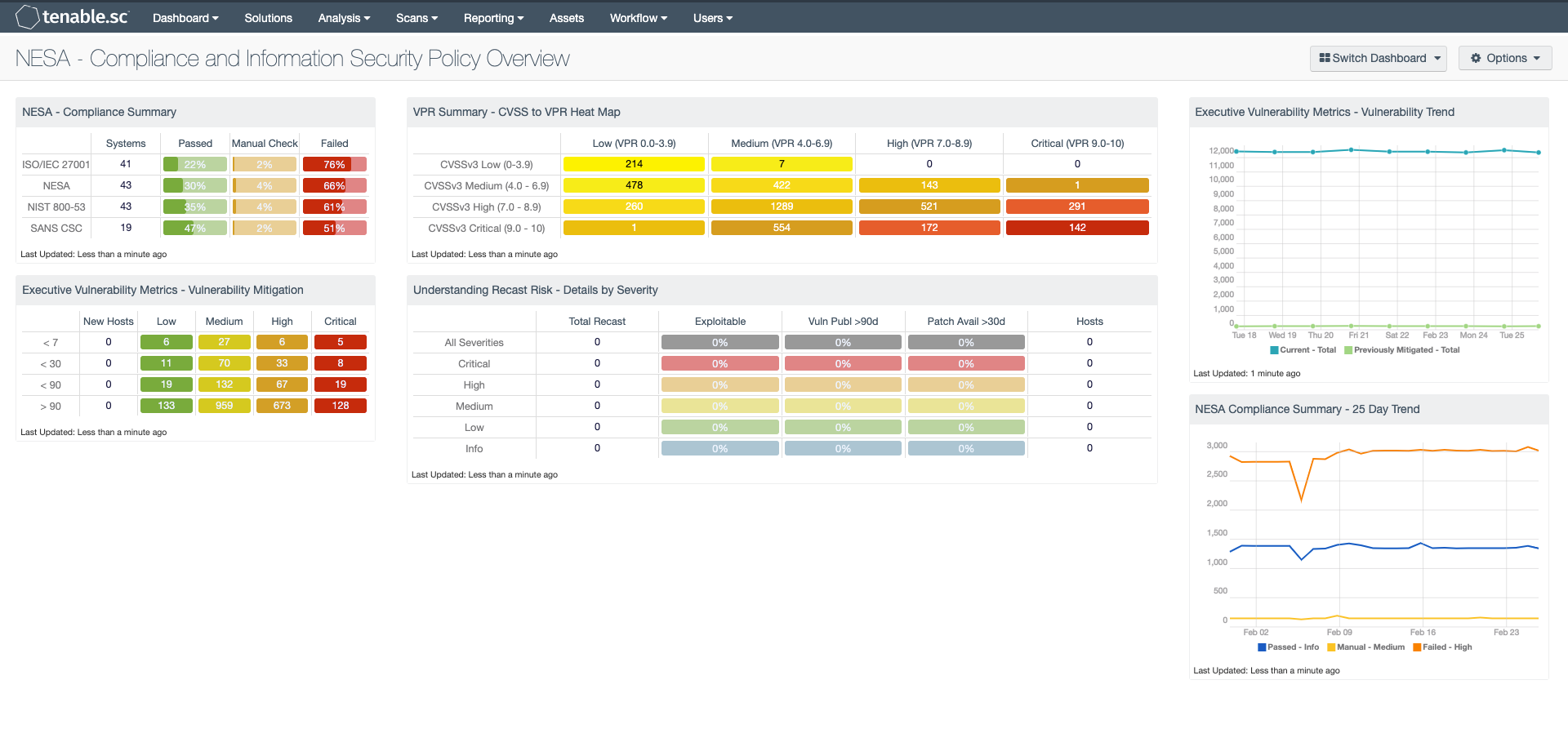
NESA - Compliance Summary: This component displays a summary over of several audit standards, providing a host count, and ratio bars for each severity level. The compliance standards in this component are: ISO/IEC 27001, NESA, NIST 800-53, and SANS CSC. The three columns with ratio bars provide a ratio of total audit checks to a specified status of the check. Checks that have passed are green, failed are red, and checks which require manual verification are in orange.
Executive Vulnerability Metrics - Vulnerability Mitigation: This component contains a matrix displaying mitigated vulnerability ages. The columns identify new hosts (within the past 24 hours), and vulnerabilities from low to critical severities. The rows are labeled by the number of days the vulnerabilities have existed within the environment from the first discovery date, sorted by less than 7, 30, 90 days, and greater than 90 days.
VPR Summary - CVSS to VPR Heat Map: This component provides a correlation between CVSSv3 scores and VPR scoring for the vulnerabilities present in the organization. The CVSSv3 scores are the traditional method of analyzing risk, while VPR is a new method based on data science analysis and threat modeling. Each cell is comprised of a combination of cross-mapping of CVSS & VPR scoring. Using a heat map approach, the filters begin in the left upper corner with vulnerabilities with the least risk. Moving to the right and lower down the matrix the colors change darker from yellow to red as the risk levels increase. Customers should mitigate risks in the lower right corners, and then work towards the upper left cells.
Understanding Recast Risk - Details by Severity: This matrix presents details by severity on vulnerabilities found to exist in the environment that have been recast to a different severity. The vulnerability severities displayed are the recast severities, not the original severities of the vulnerabilities. At each severity level, the number of vulnerabilities is displayed, along with three percentage columns and the number of hosts affected. The percentage columns show the percentages of the vulnerabilities that are exploitable, that were published more than 90 days ago, and that have had a patch available for more than 30 days. If more details are desired (for example, what are the specific critical vulnerabilities that are exploitable?), click on the appropriate matrix cell to display more information.
Executive Vulnerability Metrics - Vulnerability Trend: This component presents a trend chart of both current and previously mitigated vulnerabilities over the last seven days. Information presented within this component can provide organizations with a comprehensive view into how often systems are being scanned, patched, and rescanned. Current vulnerabilities are identified and set to the “Never Mitigated” filter. When a vulnerability moves from the mitigated section to the active section, the mitigation status is set to "Previously Mitigated.” Previously Mitigated or recurring vulnerabilities can be the result of systems not being restarted after a patch was applied, virtual systems reverting to previous snapshots, and services that were disabled or failed to restart. Organizations can use this component to focus efforts on remediating both current and previously mitigated vulnerabilities.
NESA Compliance Summary - 25 Day Trend: This component provides a 25-day trend analysis for all compliance checks. The data points for are calculated using the 'Days Since Observation' set to 'within the last day'. Thus, each data point only calculates the new compliance checks observed daily. The resulting graph more accurately depicts the change in compliance over the period of 25 days.