by Cesar Navas
October 28, 2015
Departments and organizations within the US Government need to stay up to date with federally mandated updates to protect and defend their network. The update process is accomplished through the DoD’s Information Assurance Vulnerability Management (IAVM) program with a Vulnerability Management System (VMS). This dashboard provides statistics on the effectiveness of how well notices, updates, and fixes are applied in the environment.
IAVM alerts distributed from USCYBERCOM and the Defense Information Systems Agency (DISA) can contain any number of items such as Information Assurance Vulnerability Alerts (IAVA), Information Assurance Vulnerability Bulletins (IAVB) or Technical Advisories (TA). These alerts, bulletins and advisories address software vulnerabilities to the network environment that need to be addressed. As these IAVAs, IAVBs and TAs are released, administrators and analysts need to determine the priority and implementation time for these updates. This dashboard helps administrators and analysts to monitor the current view of the IAVM program in the environment. As IAVAs, IAVBs and TAs are remediated and new ones are introduced throughout the network, this dashboard provides insight into the constantly changing process.
As the IAVM process is one of the primary methods to protect and defend networks, it is important to understand the three alerts levels such as IAVA, IAVB and TA within the IAVM process. The IAVA alert is a severe software vulnerability that needs to be addressed immediately. Not remediating these threats could very likely endanger and potentially let attackers compromise the network. The IAVB alert is a software vulnerability that does not need to be immediately addressed. However, the alert is enough of a risk that there does need to be a plan of action to mitigate the finding in a relatively short amount of time. There can also be a risk that the vulnerability in the alert could be used as another way for attackers to escalate permissions or pivot in their attack sequence. The TA alerts are generally of a low risk to the environment. The IAVAs, IAVBs and TAs can also be prescriptive rather than descriptive in their message details. Administrators and analysts should further investigate and analyze those prescriptive directions for implementation in their network.
Tenable.sc Continuous View (CV) receives continual updates of the IAVM notices. The frequent updates helps to ensure the application or system can be used in a US Government environment while staying compliant with IAVM program requirements. New alerts, bulletins and advisories enter the network on a continual basis. Administrators and analysts can help reduce risk in their environment by staying on top of new alerts, bulletins and advisories. This aforementioned scenario is a good way of remediating or mitigating the IAVM notice in a continual monitoring and remediation routine.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Executive.
The dashboard requirements are:
- Tenable.sc 4.8.2
- Nessus 8.5.1
Tenable provides continuous network monitoring to identify vulnerabilities, reduce risk and ensure compliance. Our family of products includes Tenable.sc Continuous View (CV) and Nessus. Tenable.sc CV allows for the most comprehensive and integrated view of network health. Tenable.sc CV performs system level patch, configuration, log analysis, application monitoring, and malware auditing for all major operating systems. These operating systems include all flavors of Windows, all flavors of Apple OS X, Red Hat Linux, eleven other Linux variants, Solaris, FreeBSD, AIX, IBM iSeries and HP-UX. Nessus is the global standard in detecting and assessing network data.
The components in this dashboard contain:
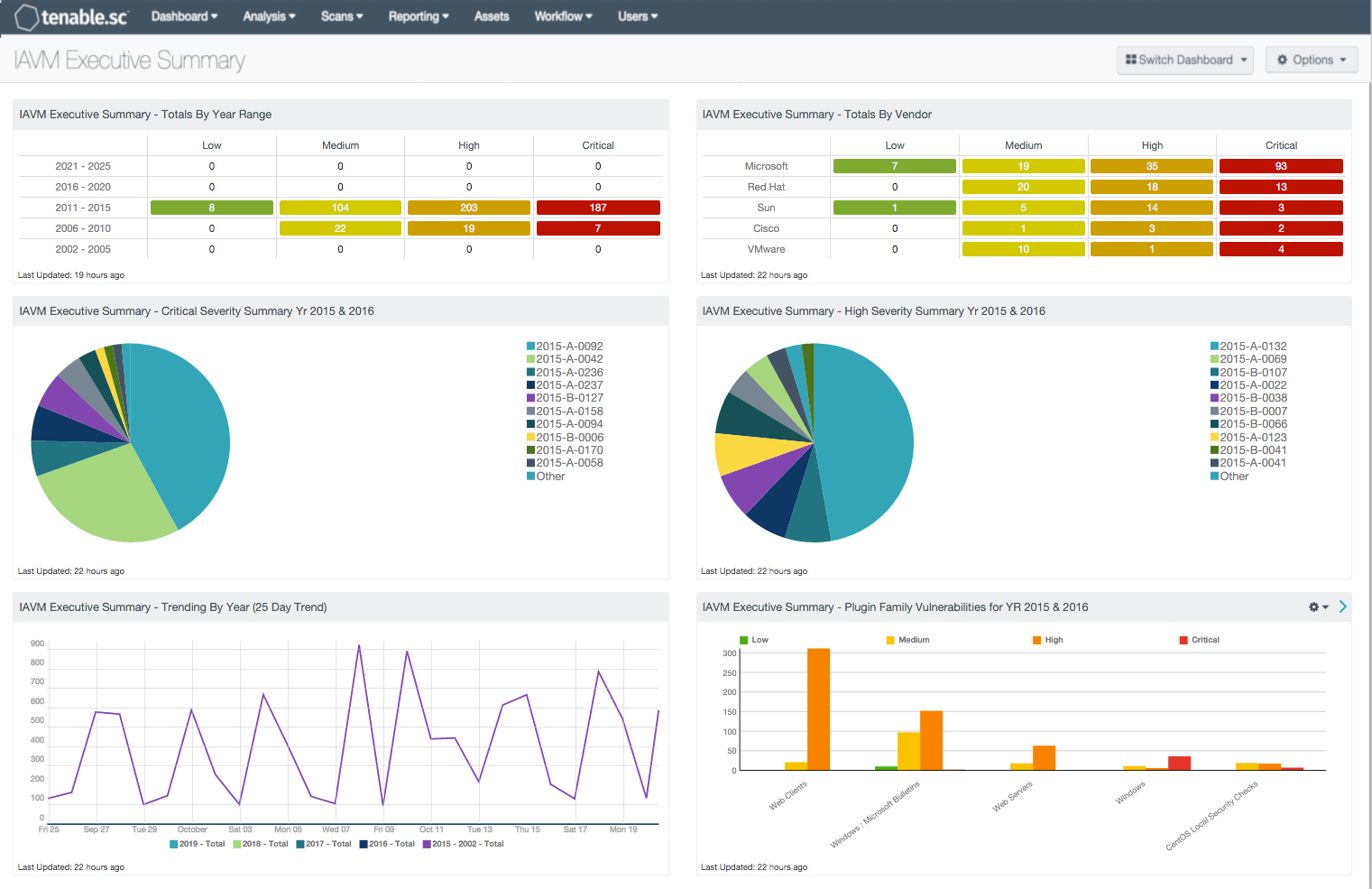
- Totals By Year Range: This component shows a host count for each severity level for the corresponding year range.
- Totals By Vendor: This component provides a correlation between the IAVM notice number and software vendors. Using the CPE field, Tenable.sc is able to map the IAVM notice number to the software vendor and severity level.
- Critical Severity Summary Year 2015 & 2016: This component provides a pie chart of the top 10 critical severity IAVM vulnerabilities found in 2015 and 2016.
- High Severity Summary Year 2015 & 2016: This component provides a pie chart of the top 10 high severity IAVM vulnerabilities found in 2015 and 2016.
- Trending By Year (25 Day Trend): This component displays a 25-day trend analysis of IAVMs per year.
- Plugin Family Vulnerabilities for Year 2015 & 2016: This component bar chart shows the vulnerabilities for 2015 and 2016 broken down by the plugin family.