by Andrew Freeborn
April 13, 2016
Common user interfaces in a modern workplace involve some type of web interface. Web interfaces allow more diverse sets of users to connect to an application through common web browsers. Allowing users to connect to web-enabled user interfaces typically reduces IT requirements, enabling the user to work more efficiently.
Enabling a web-based user interface may involve more IT requirements for security, but those requirements may not be enabled by default. When a connection is made to a website, the response from the website back to the source usually contains some type of information. The response back to the source could contain a POST response with a few HTTP headers, or a POST response with excessive HTTP headers.
Depending on the web platform, a POST response could contain excessive HTTP headers and all of the other HTTP options a user can perform. In a typical website “transaction”, a typical experience contains HTTP GET and POST. However, other options can be “DELETE” or “MOVE”, which could provide attackers a way to circumvent security controls. Security controls such as packet-layer firewalls and web application firewalls can block non-typical HTTP options to help minimize the risk to the environment. Removing or denying those HTTP options with a configuration management program can also reduce the risk to the web platform.
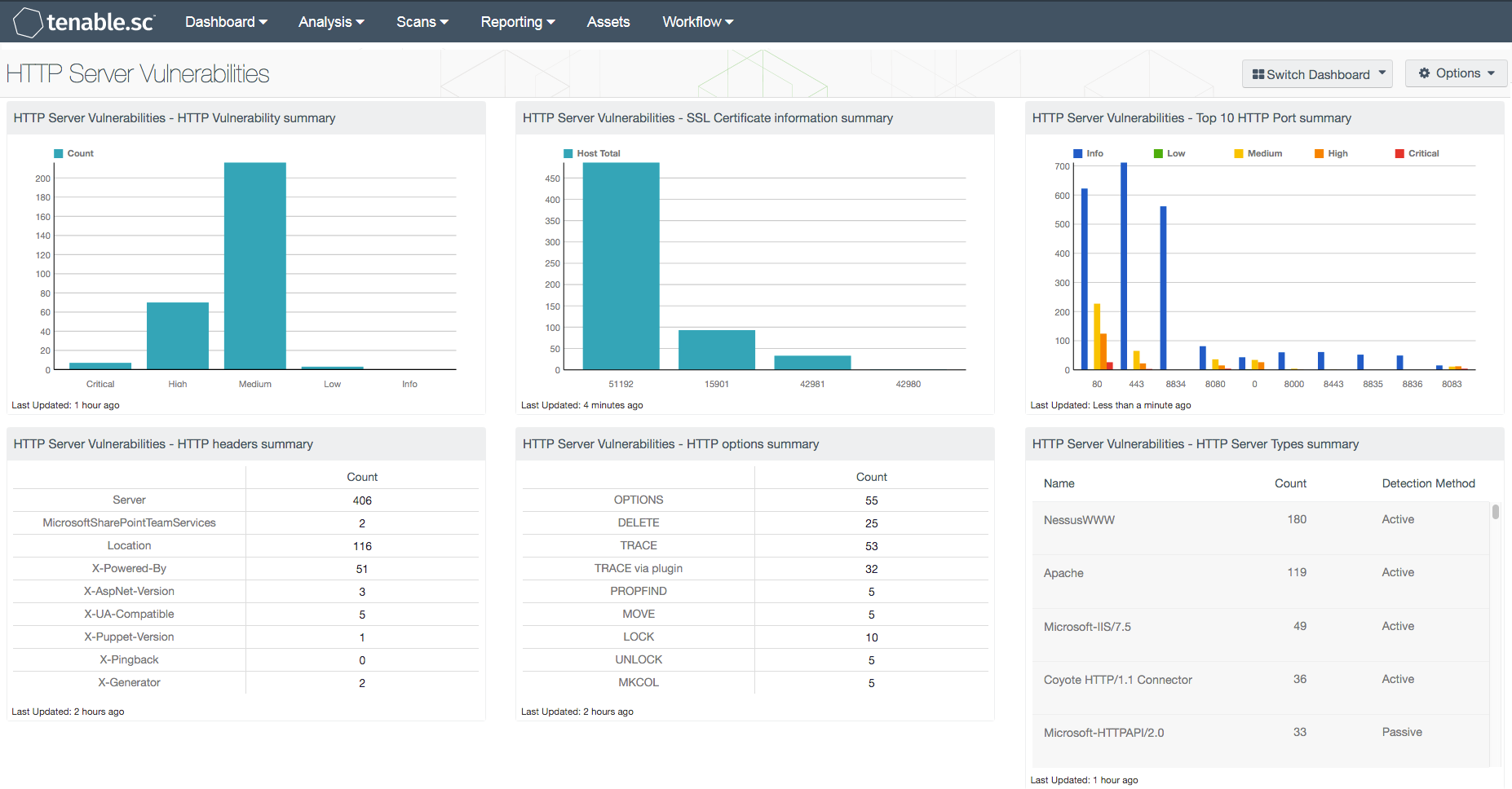
While threats such as unprotected HTTP options exist in web platforms, inadvertent information disclosures are commonly returned in responses. HTTP response headers such as “Server”, and X-Headers such as “X-Powered-By” and “X-AspNet-Version”, provide attackers detailed web platform information. If an attacker can send a basic GET request to a web platform, they could receive detailed information for the web platform, reducing their time for reconnaissance.
With detailed information provided in the HTTP response, an attacker can better tailor attacks and exploitation strategies, which can better match the specific versions of software running on the web platform. Organizations may have differing views of the value of HTTP response headers in the environment. However, if analysts are aware of the headers in the environment, removing or being aware of the headers may help to reduce risk in the environment.
In addition to HTTP options and response headers, this dashboard provides analysts with a view of the certificates used on web platforms. Analysts can see certificates that have expired, will expire soon, and will in the future become valid certificates. Using this information, analysts can work with the various teams in the organization to reduce potential certificate issues along with ensuring best practice certificate usage.
The dashboard also contains components such as a list of web platforms and HTTP/HTTPS ports in use in the organization. The components can help assist analysts to ensure that authorized web platforms and ports are in use and raise awareness of unknown or unexpected findings. The remaining component of the dashboard provides an overview of low, medium, high and critical severity vulnerabilities found with web servers in the organization. A report in the Tenable.sc feed is also available to view this data in report format located at, “HTTP Server Vulnerabilities” (http://www.tenable.com/sc-report-templates/http-server-vulnerabilities-report).
The dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Threat Detection & Vulnerability Assessments. The dashboard requirements are:
- Tenable.sc 4.8.2
- Nessus 8.6.0
Tenable provides continuous network monitoring to identify vulnerabilities, reduce risk, and ensure compliance. Tenable's family of products includes Tenable.sc Continuous View (CV), Nessus, Nessus Network Monitor (NNM), and Log Correlation Engine (LCE). Tenable.sc CV provides the most comprehensive and integrated view of network health, and is the global standard in detecting and assessing network data.
This dashboard contains the following components:
- HTTP headers summary: The “HTTP headers summary” matrix component provides analysts counts of the detected HTTP headers to provide context of potential issues in the organization
- HTTP options summary: The “HTTP options summary” matrix component provides analysts with counts of the detected HTTP options to provide context of potential issues in the organization
- HTTP Server Types summary: The “HTTP Server Types summary” table component identifies the various versions of web platforms detected in the organization
- HTTP Vulnerability summary: In the “HTTP Vulnerability summary” bar chart component below, management and analysts can see the counts of vulnerability severities affecting web platforms
- SSL Certificate information summary: The “SSL Certificate information summary” bar chart component provides a count of certificate issues detected in the organization
- Top 10 HTTP Port summary: In the “Top 10 HTTP Port summary” bar chart component, the top 10 HTTP ports’ vulnerability summaries are provided