by Andrew Freeborn
January 6, 2016
Malware presents a risk to any organization and comes packaged in many forms. Malware can exploit weaknesses in vulnerabilities to make software or hardware perform actions not originally intended. Vulnerabilities can also be widely exploited shortly after publication as malware authors reverse engineer the fix and come up with “1-day exploits” that can be used to attack organizations.
Unfortunately, malware comes in many forms such as office documents and ads you see in a webpage on a computer or mobile device. The attack vectors can become numerous depending on the infrastructure of the organization. This dashboard can assist analysts to quickly identify exploitable vulnerabilities, and aid in mitigation efforts.
Organizations can gain operational awareness of systems with exploitable vulnerabilities on a network. Analysts need to either mitigate the risk from vulnerabilities or remediate them, but not all vulnerabilities are created equal making prioritization sometimes a difficult task. Focusing on vulnerabilities actively exploited by malware helps to reduce the risk to the organization and offer prioritization guidance of which vulnerabilities to remediate. Analysts can use this dashboard along with the knowledge of the software in the organization to better defend themselves.
Even though vulnerabilities can be exploited through custom means as malware, vulnerabilities can also be exploited through common software applications. An attacker can also use these software products to exploit vulnerabilities present in an organization. Products such as Metasploit, Core Impact and exploits listed in ExploitHub can be used by anyone to perform an attack against vulnerabilities. Vulnerabilities that can be exploited through these means are displayed in this dashboard with their relevant percentage of exploitation of vulnerabilities in the organization.
As the nature of this dashboard could be of a high value to an organization, all efforts should be made to detect vulnerabilities in the environment. To the point of this dashboard, vulnerabilities that are being exploited by malware and software exploitation tools are specifically called out to the analyst. This dashboard incorporates all of Tenable’s product offerings of active scanning with Nessus, passive monitoring with PVS (Passive Vulnerability Scanner) and local host log monitoring with LCE (Log Correlation Engine). All of these tools natively work together and intelligently combine their data into SecurityCenter Continuous View. Analysts have the best results possible to detect vulnerabilities exploited by malware through this dashboard.
The dashboard and its components are available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Threat Detection & Vulnerability Assessments. The dashboard requirements are:
- SecurityCenter 4.8.2
- Nessus 6.5.4
- PVS 4.4.0
- LCE 4.6.0
Tenable provides continuous network monitoring to identify vulnerabilities, reduce risk and ensure compliance. Our family of products includes SecurityCenter Continuous View (CV), Nessus, PVS and LCE. SecurityCenter CV performs log normalization from hundreds of unique data sources. Nessus is the global standard in detecting and assessing network data. PVS provides deep packet inspection to continuously discover and track users, applications, cloud infrastructures, trust relationships, and vulnerabilities. LCE performs automatic discovery of users, infrastructure, and vulnerabilities across more technologies than any other vendor including operating systems, network devices, hypervisors, databases, tablets, phones, web servers and critical infrastructure.
This dashboard contains the following components:
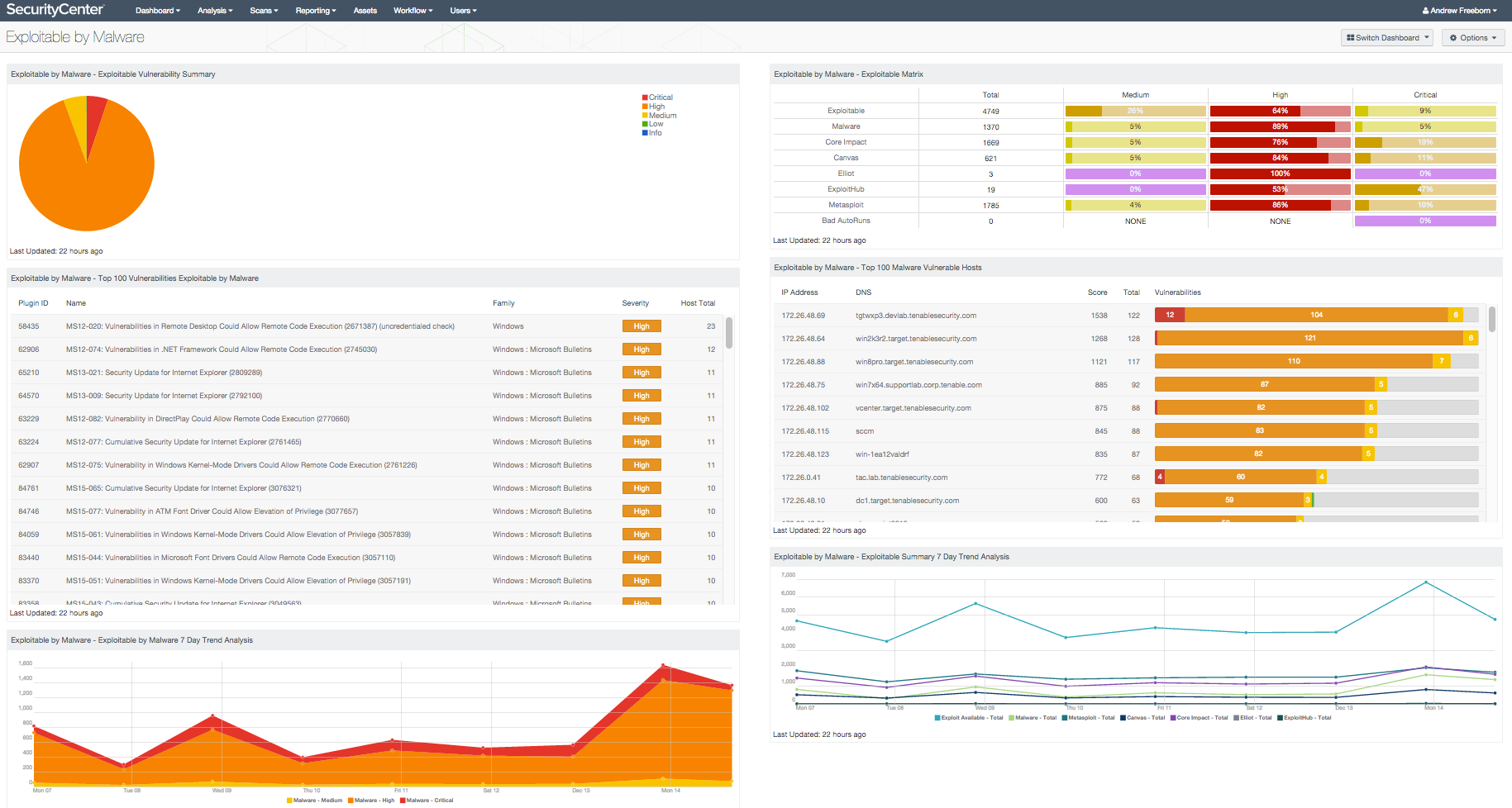
- Exploitable Vulnerability Summary: This component displays a summary of vulnerabilities that are exploitable by malware
- Exploitable Matrix: This component is an indicator matrix of exploitable vulnerabilities
- Top 100 Vulnerabilities Exploitable by Malware: This component provides a host summary of systems with vulnerabilities that are known to be exploitable by malware
- Top 100 Malware Vulnerable Hosts: This component provides a host summary of systems with vulnerabilities that are known to be exploitable by malware
- Exploitable by Malware 7 Day Trend Analysis: This component shows an additive trend analysis of vulnerabilities that can be exploited by malware
- Exploitable Summary 7 Day Trend Analysis: This component displays a detailed trend analysis for exploitable vulnerabilities, by exploit framework