by Ron Gula
July 15, 2015
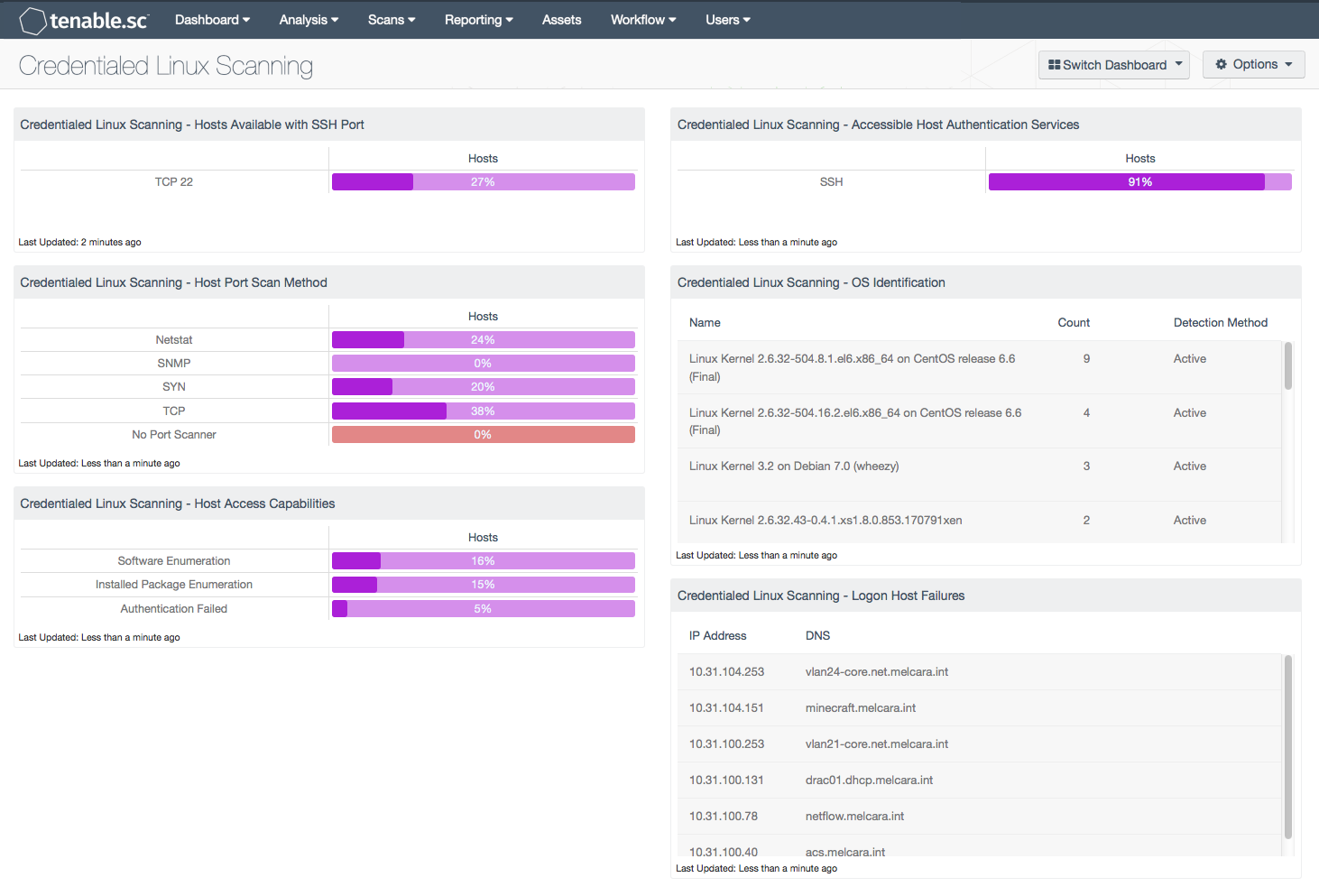
Monitoring the status of Linux/UNIX credentialed scanning is important in supporting both patch and compliance auditing of Linux/UNIX systems. Tenable.sc CV has the ability to perform credentialed scans on Linux/UNIX, thus increasing the accuracy of the collected data. This dashboard monitors Linux/UNIX credentialed scans.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Monitoring.
The dashboard requirements are:
- Tenable.sc 4.8.2
- Nessus 8.4.0
- NNM 5.9.0
During the initial rollout of Linux/UNIX credentialed scans, an important task to monitor is tracking systems that failed authentication. When a system fails a credentialed scan, patch and compliance auditing will be incomplete or possibly inaccurate. Just as important is the continuous analysis of the scans’ results, as changes to networks and hosts could affect the risk exposure of an organization.
The dashboard consists of six components covering network and host resources required to perform a successful agent-less patch and/or compliance audit leveraging the appropriate Linux/UNIX account. The six components leverage the following plugins, which must be enabled during a credentialed scan:
- 19506 - Nessus Scan Information
- 11936 - OS Identification
- 21745 - Authentication Failure - Local Checks Not Run
- 10267 - SSH Server Type and Version Information
- 22869 - Software Enumeration (SSH)
- 12634 - Authenticated Check: OS Name and Installed Package Enumeration
All of the components on this dashboard need to have their assets’ filters modified so the displayed results will only show Linux/UNIX credentialed scans. Further information can be found at Using Assets with Dashboards How-To Guide.
Tenable.sc Continuous View (CV) is scalable vulnerability management system that identifies the biggest risk across the entire enterprise. Tenable’s products allows for the most comprehensive and integrated view of network health. Nessus and Tenable.sc are continuously updated with information about advanced threats and zero-day vulnerabilities, as well as new types of regulatory compliance configuration audits, allowing organizations to respond to new threats as they emerge.
Components
Credentialed Linux Scanning - Hosts available with SSH port: This matrix component indicates the percentage of hosts with vulnerabilities discovered on TCP Port 22 (SSH). Nessus uses Secure Shell (SSH) for credentialed scans on Linux/Unix operating systems. Nessus supports three types of authentication methods for use with SSH: username and password, public/private keys, and Kerberos. If SSH servers are running on another port, the scan policies will need to be modified, and the filter in this matrix will need to be modified to reflect the correct SSH service port.
Credentialed Linux Scanning - Accessible Host Authentication Services: This matrix component highlights the percentage of hosts that are running an OpenSSH service detected by plugin 10267. While performing patch and configuration auditing, Tenable recommends leveraging the Netstat scanner, used via SSH, to considerably speed up, and in some cases improve port scan accuracy. The “SSH Server Type and Version Information” (10267), detects the SSH server type and version information by sending an empty authentication request. This plugin obfuscates the version by collecting banner information from the SSH session or other methods.
Credentialed Linux Scanning - Host Port Scan Method: This component displays indicators for different types of successful Nessus scanning methods by host percentages. When scanning Linux/Unix systems there are several different methods for conducting port scanning. The scan policy can be configured to use more than one port scan method. There are four port scan methods used when scanning a Linux/Unix system; this component highlights each of the four methods.
Credentialed Linux Scanning - OS Identification: This table component displays the various Linux/UNIX platforms being audited with a credentialed scan. This table is sorted by OS count and displays the OS version, count, and detection method. This information is useful to an analyst who needs to know the numerous Linux/UNIX platforms that are being scanned in the network environment.
Credentialed Linux Scanning - Host Access Capabilities: When a Nessus server logs on to a Linux/UNIX host, there are many factors that can still block a successful patch and/or compliance audit. The "Host access capabilities" matrix component measures the success of accessing various host resources required by a host logon session. If the resources are available, then the Nessus scanner can enumerate software and installed packages. If the login fails or the login session does not provide the necessary resources, then authentication will fail, highlighted as a percentage over the hosts audited in the final bar in the component. The authentication failure status is provided by plugin 21745 reporting a problem.
Credentialed Linux Scanning - Logon Host Failures: This table displays the Linux/UNIX systems that failed login for credentialed scans. If the resources are available, then the Nessus scanner can enumerate software and installed packages. If the login fails or the login session does not provide the necessary resources, then authentication will fail. The authentication failure status is provided by plugin 21745 reporting a problem. This filter in this component uses a regular express to exclude SMB login failures, which helps eliminate false positives of Windows login failures.