by Cody Dumont
May 3, 2016
Browsers, web servers, and digital certificates allow organizations, as well as end users, to communicate securely across the Internet. Without having a continuous monitoring strategy in place, critical web servers will remain at risk for attack that could result in significant disruptions, loss of confidential data, and financial damages. This dashboard presents a summary of passively detected web servers, browsers, and SSL/TLS certificate information, which can be useful in strengthening security policies within the organization.
Many organizations utilize vulnerability scanners that only perform active scanning, which detect information on new or existing systems. As organizations continue to integrate mobile and cloud-based solutions, the chance of servers or devices connecting to the network temporarily will increase. Systems and devices that connect between scans may not be accounted for, which can leave an organization at risk for unauthorized systems and/or malicious attacks.
The components in this dashboard include the latest information on passively detected web servers, browsers, SSL/TLS certificates, and related vulnerabilities and events. The Nessus Network Monitor (NNM) continuously monitors network traffic in real-time to identify browsers, web servers, and certificate information that may have been missed by active scans through Nessus. The data collected passively helps to identify the web services in use on the network that were not detected during active scans. Several components assist analysts in identifying existing web servers, browsers, and SSL vulnerabilities.
When web servers are detected, NNM may also detect useful information such as expired certificates, weak SSL-based certificates, and exploitable web server vulnerabilities. SSL certificates utilize weak encryption algorithms that can allow attackers to intercept established sessions between a client and a web server. The National Institute of Standards and Technology (NIST) prohibited federal agencies from using TLS 1.0, SSL 2.0, and SSL 3.0 because of the reliance on cryptographic algorithms that are not approved. The Special Publication (SP) required the use of TLS 1.1 or higher to be configured with approved cryptographic schemes and algorithms as a minimum baseline to properly secure confidential data. TLS 1.2 provides the best means to protect confidential data, and supports advanced ciphers such as AES and SHA-2 hash algorithms. Additional information on TLS implementations can be found within the NIST SP 800-52 Rev. 1 publication.
NNM detects the top used browsers on systems where NNM is monitoring the traffic flow. In some cases the browsers could be unauthorized browsers. When multiple browsers are installed on systems the attack surface can increase risk. Various browser elements, such as Java, Flash, and ActiveX, have commonly recurring vulnerabilities. Using NNM and Nessus together provides the security team with the accurate and additional information needed to secure and strengthen the organization.
This dashboard is available in the Security Center Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Security Center Feed under the category Discovery & Detection. The dashboard requirements are:
- Security Center 5.3.1
- Nessus 6.6.1
- NNM 5.0.0
Security Center provides continuous network monitoring, vulnerability identification, risk reduction, and compliance monitoring. Security Center is continuously updated with information about advanced threats and zero-day vulnerabilities, and new types of regulatory compliance configuration audits. NNM provides deep packet inspection to continuously discover vulnerabilities traveling the wire. By integrating with Nessus and NNM, Security Center continuous network monitoring is able to detect events and vulnerabilities across the enterprise.
The following components are included in this dashboard:
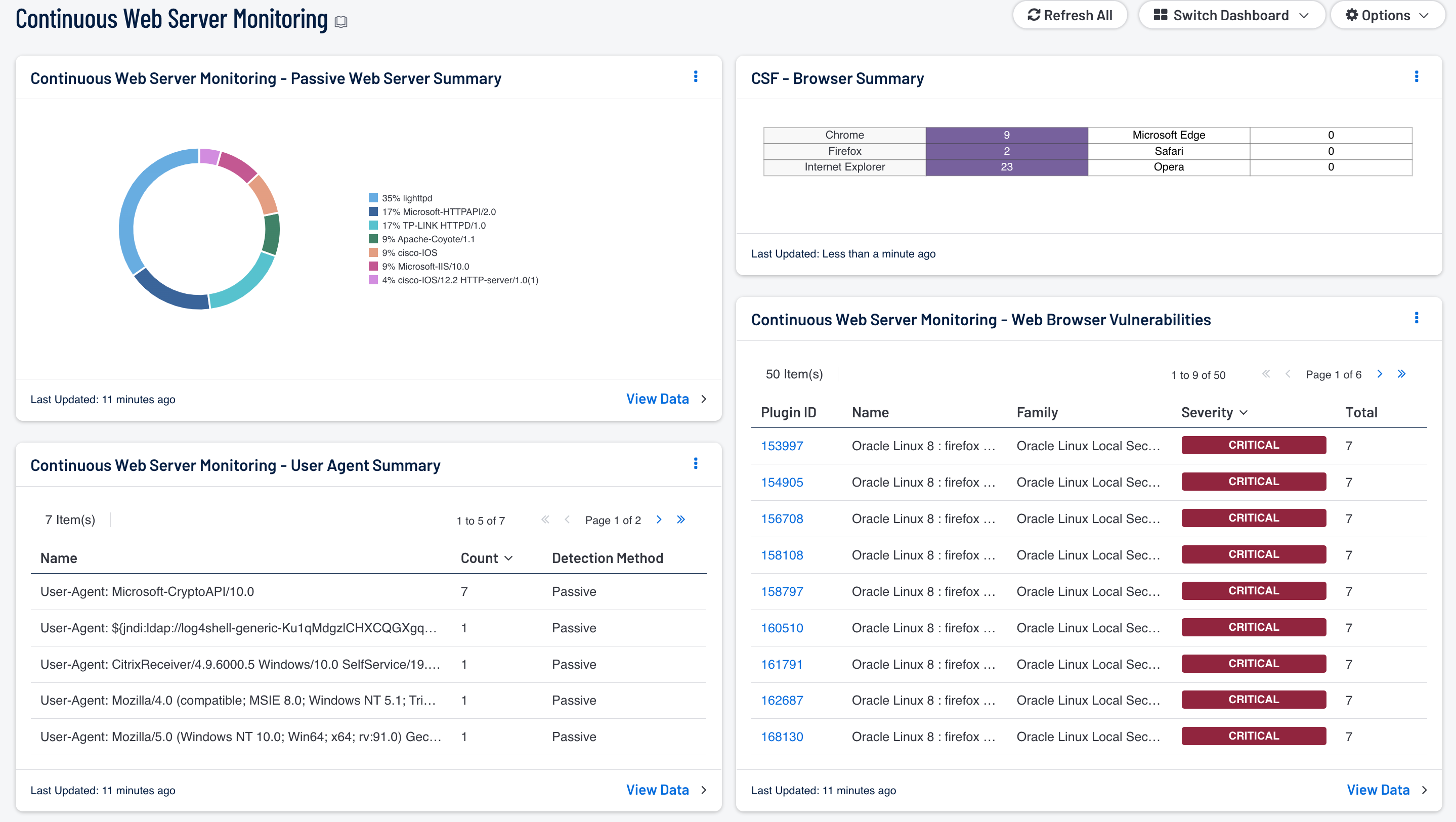
- Continuous Web Server Monitoring – Passive Web Server Summary: The Passive Web Server Summary chart presents the web servers that have been passively detected on the network. This list includes web servers detected by NNM plugins 1442 (detection of web servers that send a 'Server:' string in their server response), 8166 (detection of web servers that do not send a 'Server:' string in their server response), and 7034 (HTTP server vhost detection). This chart provides a complete list of web servers that were not detected during active scans. Analysts can modify this chart per organizational requirements.
- Continuous Web Server Monitoring – User Agent Summary: The User Agent Summary table presents a list of User Agents on the network. Every web browser provides a “user-agent” HTTP header for web page requests. User agents can help analysts identify the browser, operating system, or other service in use by a host. Attackers also leverage user agents to send malicious HTTP requests or obtain content designed for other browsers. Analysts can use the information provided within this table to identify malicious user agents and potential attack vectors that may have been used.
- CSF – Browser Summary: This matrix detects installations for the top six browsers commonly used within organizations. Many organizations have multiple browsers installed on workstations and servers. Having multiple browsers installed on systems can also increase security risk for an organization. The analyst can utilize this component in identifying systems with unapproved browsers. Additionally, this matrix can assist with patching efforts. The analyst can click on the respective browser and drill down to find additional information.
- Continuous Web Server Monitoring – Web Browser Vulnerabilities: The Web Browser Vulnerabilities table presents a list of detected browser vulnerabilities from the top six browsers commonly used within organizations. Many organizations have multiple browsers installed on a variety of systems and devices on the network. The analyst can utilize this component in identifying systems with vulnerable browsers that need to be patched or upgraded. The analyst can drill down to obtain additional information on the vulnerability and system affected.