by David Schwalenberg
June 20, 2016
Compliance and regulatory changes can be challenging to manage effectively. Not only do organizations have to keep systems updated with the latest patches, but systems also need to be hardened to reduce the attack surface. Default configurations for operating systems, applications, and devices tend to be geared for ease-of-use rather than security. If these systems are not locked down, attackers will find opportunities to exploit them. Hardening systems remove
The Center for Internet Security (CIS) publishes a series of configuration benchmarks used across multiple industries. The benchmarks are well-vetted, and support security actions that organizations can take to assess and improve their current security state. Developed based on specific knowledge of the threat environment and currently available technologies, the Controls are informed by actual attacks and effective defenses and reflect the combined knowledge of many experts.
Tenable.sc measures compliance using audit files that cover a wide range of major regulatory and other auditable standards, such as the Critical Security Controls (CIS) and other CIS benchmarks, the CyberSecurity Framework, HIPAA, NIST SP 800-53, PCI, STIGs, and more. Tenable provides over 450 audit files, available for download from the Tenable Customer Support Portal , in categories such as operating systems, applications, databases, and network devices. Audit files can be customized if desired to match an organization’s security policy. For more information on using audit files, see Nessus Compliance Checks: Auditing System Configurations and Content.
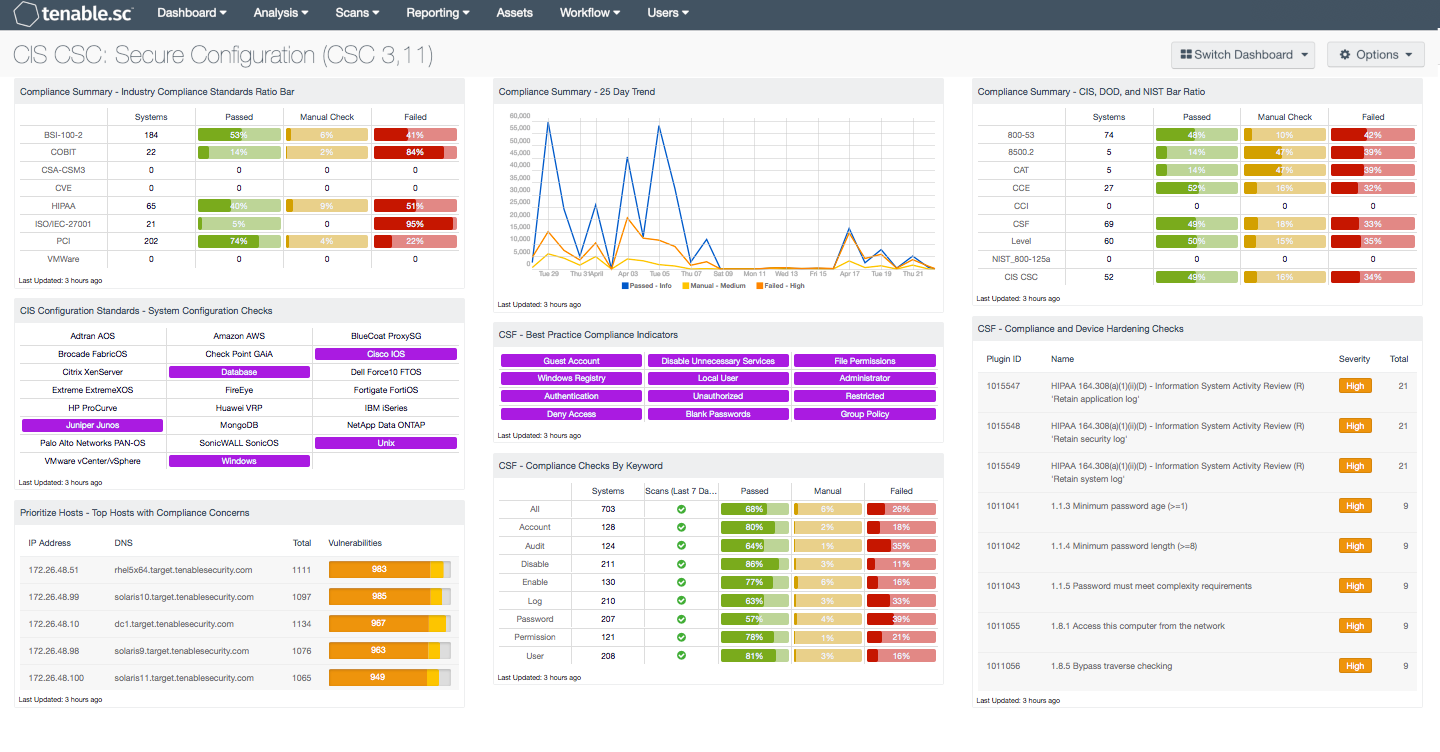
The components on this dashboard present various views into the compliance scan results, providing an analyst with targeted information such as compliance results per standard, per device type, and per keyword. Analysts can easily drill down into the data presented by the dashboard components to gain more detailed information about the compliance checks. The plugin output from audit checks include information about compliance failures, expected vs. actual policy values, and the specific sections of the various standards to which a compliance check relates. The organization can then use this information to apply hardening techniques and reduce the organization's overall attack surface.
This dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Security Industry Trends. The dashboard requirements are:
- Tenable.sc 5.4.0
- Nessus 8.9.0
- Compliance Data
- Compliance Summary - Industry Compliance Standards Ratio Bar: This component displays a summary over of several audit standards, providing a host count, and ratio bars for each severity level. The compliance standards in this component are BSI, COBIT, CCM, CVE, HIPAA, ISO, PCI & VMWare. The three columns with ratio bars provide a ratio of total audit checks to a specified status of the check. Checks that have passed are green, failed are red, and checks which require manual verification are in orange.
- CIS Configuration Standards - System Configuration Checks: This component provides indicators for CIS audits based on the device audited. The indicators search on two fields, the Cross Reference and vulnerability text. The Cross Reference uses the audit file keyword search, while the plugin text searches for “cisecurity.org”. These indicators will show the analysts which type of CIS audits have been run and provide an easy method for accessing CIS audit data. The indicators will turn purple when a match is discovered.
- Prioritize Hosts - Top Hosts with Compliance Concerns: This table displays the top hosts on the network that have either compliance failures or compliance checks that must be performed manually. The list is sorted so that the host with the worst compliance concerns is at the top. A count of compliance concerns and a bar graph indicating the severity of the concerns are given for each host. Use this table to determine the hosts most out of compliance on the network.
- Compliance Summary - 25 Day Trend: This component provides a 25-day trend analysis for all compliance checks. The data points for are calculated using the 'Days Since Observation' set to 'within the last day'. Thus, each data point only calculates the new compliance checks observed daily. The resulting graph more accurately depicts the change in compliance over the period of 25 days.
- CSF - Best Practice Compliance Indicators: This component uses results from the compliance audit to trigger on specific plugin keywords for best practice configuration guidelines. When the keyword or phrase has been detected within the plugin name, the indicator will turn purple. The analyst can click on the indicator and drill down to obtain additional information on hosts affected. This matrix will allow the analyst to readily identify specific compliance best practice keywords, and can be modified to suit organizational needs.
- CSF - Compliance Checks by Keyword: This component uses results from the compliance audit to trigger on specific plugin keywords. Each column includes the respective keyword along with the host count, scans performed in the last 7 days, and whether the checks have passed, failed, or require manual verification. Passed checks are green, failed are red, and checks that require manual verification are in orange. This component will allow the analyst to readily identify specific compliance vulnerabilities. The keywords can be modified to suit organizational needs.
- Compliance Summary - CIS, DOD, and NIST Bar Ratio: This component displays a summary over of several audit standards, providing a host count, and ratio bars for each severity level. The compliance standards in this component are: NIST, DoD, CCE, CCI, CSF, and CSC. The three columns with ratio bars provide a ratio of total audit checks to a specified status of the check. Checks that have passed are green, failed are red, and checks which require manual verification are in orange.
- CSF - Compliance and Device Hardening Checks: This component displays Compliance and Device Hardening Checks from the NIST CSF PR.IP-1 and PR.IP-7 sub-categories. Additional references from other compliance related standards such as NIST CM-2 through CM-7, CM-9, CA-7, PCI DSS 2.1 and 2.2, and the COBIT BAI10 process are also included. Each check will search for vulnerability text that includes each of the respective guidelines and standards noted above. The table will display the plugin name, along with the number of hosts affected, and is sorted by severity level. The analyst can drill down to obtain additional information on specific vulnerabilities, hosts affected, and solutions to mitigate the vulnerability. This information can assist the analyst in patching a large number of hosts at once, which will reduce the overall risk footprint.