by Cesar Navas
August 26, 2015
Configuration compliance programs continue to expand and increase the requirement for monitoring and management. To assist in this process, the Center for Internet Security has created several configuration benchmarks. Tenable supports a wide variety of configuration audits including NIST, CIS and other technology audits standards. The audit files for CIS include operating systems, SQL databases, routers and much more. Tenable.sc uses the audit files created specifically for CIS configuration guidelines to audit several aspects of the networks.
The CIS guidelines have two security levels. Level 1 settings are generally considered “safe” to apply to most systems. The Level 1 settings are not likely to cause a negative impact unless otherwise noted in the guide. Level 2 settings provide a higher level of security, but implementing these settings could have a negative impact to performance and functionality. For each level, when auditing there are 3 possible results of the audit check. They are Scorable, Not Scorable, and Reportable. Scorable means the system configuration can be determined via automated means. A Not Scoreable system configuration cannot be determined via automated means, thus requiring manual review of the output. Reportable means the setting is not scored but should be reported on.
This dashboard presents the data in a useable manner by both audit configuration type and by the CIS Level settings. The Not Scorable indicators should be manually reviewed after each new scan to determine if a vulnerability is present or not. If the results are acceptable, the organization can decide to accept the risk. For all the Scorable settings, the organization should review their local configuration guidelines and then compare those settings to the ones in the scan results. If needed, the organization can modify the audit files to be aligned with local policies. Should the organization not have configuration guidelines, implementing CIS benchmarks can improve security and operations.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessments.
The dashboard requirements are:
- Tenable.sc 5.0.1
- Nessus 8.5.0
Tenable.sc provides a unique combination of detection, reporting, and pattern recognition utilizing industry recognized algorithms and models. Tenable.sc supports a tight integration and API extensibility with SIEMs, malware defenses, patch management tools, BYOD, firewalls, and virtualization systems. Tenable has the ability to audit more technologies than any other vendor including operating systems, network devices, and critical infrastructure. Because Tenable has the largest installed based and best know-how, we see security and compliance issues before our competitors, and provide a peace of mind to customers.
Components
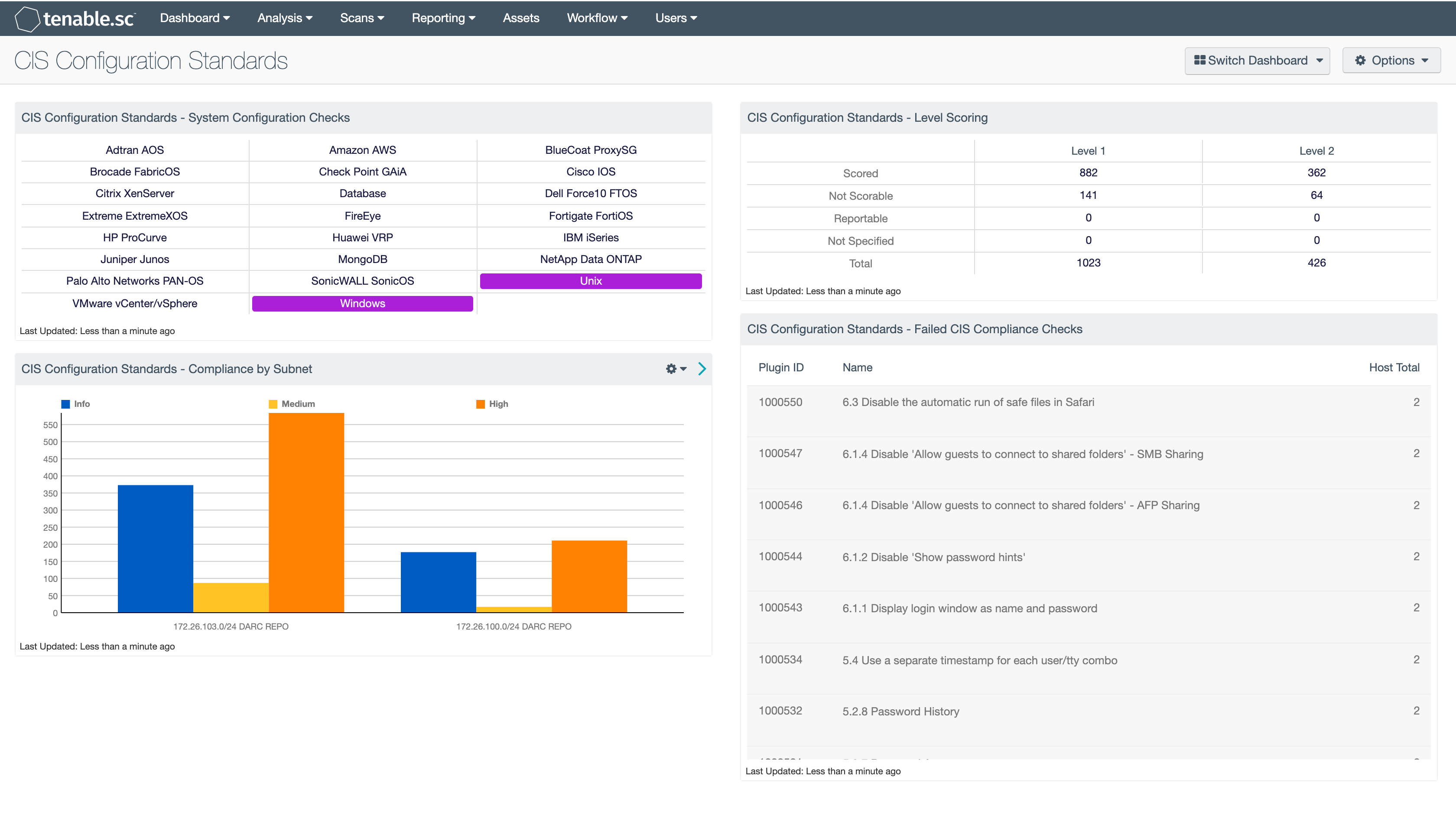
CIS Configuration Standards - System Configuration Checks: This component provides indicators for CIS audits based on the device audited. The indicators search on two fields, the Cross Reference and vulnerability text. The Cross Reference uses the audit file keyword search, while the plugin text searches for “cisecurity.org”. These indicators will show the analysts which type of CIS audits have been run and provide an easy method for accessing CIS audit data. The indicators will turn purple when a match is discovered.
CIS Configuration Standards - Compliance by Subnet: This chart provides the analysts with a subnet level view of CIS audits. The bar chart tracks 3 severity levels: Informational, Medium, and High. When an audit scan finds a setting within compliance, then an informational severity is given to plugin. When a compliance check fails, the plugin is flagged as high severity. Plugins with a medium severity are where a manual review of the plugin output is needed to determine if the check passed or failed. The top 10 subnets with CIS checks will be represented in this chart.
CIS Configuration Standards - Level Scoring: This component provides a detailed view of the Level 1 and 2 audit checks and if the checks are scorable or not.
CIS Configuration Standards - Failed CIS Compliance Checks: This table provides a list of the failed CIS audit checks. The information in this table provides the analysis with a high-level view of the failed audit checks related to CIS benchmarks.