by Cesar Navas
October 17, 2019
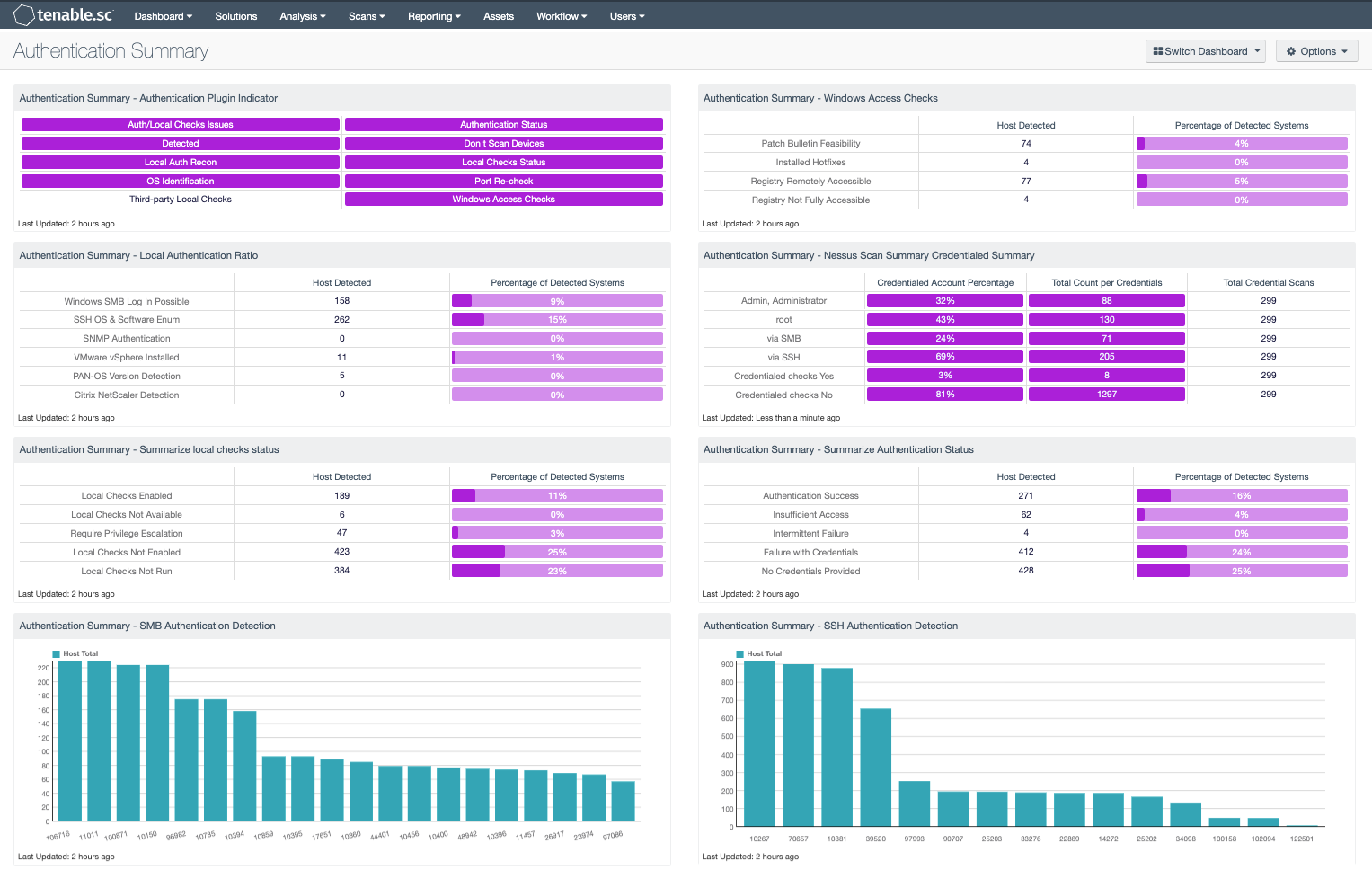
Cyber Exposure requires the data collected by the vulnerability scanner to be trusted and verifiable. Nessus provides several plugins that assist in understanding the scan status and provides a level of trust to risk managers. This dashboard brings together all the plugins used to determine if an asset was successfully authenticated during the vulnerability scan.
Authentication can be defined by connecting to a system and providing credentials in order to gain access to the system. Nessus scans systems by using different network protocols (SSH, SMB, HTTPS, SNMP, etc.) in order to gain access to the remote target asset. For example, logging in to a remote host via SSH using a username and password is a method of authentication. Each remote asset can authenticate using several protocols. Assets with more than one authenticatable protocol, for example Windows server running a SQL server, could report both authentication success and failure. Understanding this fact during analysis is key to understanding is the system was successfully scanned or not. While in many cases the successful authentication of an asset may seem binary, there are many examples of successfully scanned systems with authentication failures. The system administrator should review all the failures and understand the services which are enabled on the asset for a complete analysis.
Local checks are a feature in Nessus scans, which enable the scanner to perform security checks on the target asset. Different authentication protocols may allow for general checks to be performed locally, but when all possible checks are completed, Nessus does a more detailed Local Check. The Local Check always requires authentication and often requires elevated privileges. Local checks for major operating systems with security advisories numbering in the thousands are often grouped into their own plugin family, but local checks plugins also exist in other families such as Firewalls or Misc.
Enabling local checks is much more complex than authentication and occurs after successful authentication has been established. In order to enable local checks, the following criteria must be satisfied:
- The target device or operating system must be identified
- Local checks must be available in Nessus plugins for the identified device or operating system
- The information needed to enable local checks for that particular device or operating system must be obtained from the remote host
- Except in particular circumstances, such as scanning localhost, remote authentication must first be successful before local checks can be enabled - but the threshold to enabling local checks is higher than the threshold for successful authentication.
To ensure the scans report the most complete and accurate information Local Checks are a requirement. Users can enable local checks by providing credentials with elevated privileges and/or administrative access or deploying Nessus Agent. Without elevated access, the ability for Nessus to successfully identify risk on a system is diminished. The more access to a system Nessus has, the more complete the risk analysis is..
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Monitoring.
The dashboard requirements are:
- Tenable.sc 5.12.0
- Nessus 8.7.2
This dashboard provides the organization with a clear and simplified method to track and troubleshoot authentication related problems. By grouping authentication plugins into diagnostic context, the dashboard allows administrators to apply focus to areas of concern. The data helps facilitate the Fix and Measuring steps to the Cyber Exposure Lifecycle. Tenable.sc is the on-prem solution for understanding a comprehensive picture of the network, while keeping the data under the organization’s control. Built on leading Nessus technology, Tenable.sc discovers unknown assets and vulnerabilities, and monitors unexpected network changes before they turn into breaches.
This dashboard contains the following components:
Authentication Summary - Authentication Plugin Indicator: The plugins in this component are used in many environments to understand and troubleshoot authentication problems.
Authentication Summary - Local Authentication Ratio: This matrix provides a summary view of the plugins used to determine if Local Authentication is possible.
Authentication Summary - Summarize local checks status: This matrix provides a summary view of Local Check performance, meaning if the local checks were enabled or not.
Authentication Summary - SMB Authentication Detection: This bar chart provides a summary view of all the Server Message Blocks (SMB) plugins, which are used to understand the success of Windows Asset Scanning.
Authentication Summary - Windows Access Checks: This matrix provides the administrator with a good indication of the scan health of Windows systems.
Authentication Summary - Nessus Scan Summary Credentialed Summary: This component displays a matrix using the “Nessus Scan Summary (19506)” plugin to report on authentication status.
Authentication Summary - Summarize Authentication Status: This matrix provides an overall authentication summary of the systems that have been scanned.
Authentication Summary - SSH Authentication Detection: This bar chart provides a summary view of all the Secure Shell (SSH) plugins, which are used to understand the success of Linux or network device Asset Scanning.