by Cesar Navas
October 21, 2016
Many organizations do not have adequate incident response plans to deal with infected machines and network compromise. Once a host has been compromised, malware can remain on the system for weeks or more, harvesting credentials, stealing data, and causing significant and widespread damage. Without proper detecting and reporting capabilities, organizations will not have a clear picture of the extent of an infection, and will miss critical information on attack vectors being used and points of entry into the network. Lack of proper data backups can also hamper recovery efforts; as critical information may be corrupted or lost completely. Not having a comprehensive plan in place to recover and restore business operations in the event of a natural disaster or network incident may jeopardize an organization's competitiveness and long-term survival.
The French Network and Information Security Agency (Agence nationale de sécurité des systèmes d’information or ANSSI) developed the "40 Essential Measures for a Healthy Network" to assist organizations in safeguarding the security of information systems within a network. Following these measures, or rules, for a healthy network will provide basic protection for an organization's critical data. ANSSI states that the majority of IT attacks that have involved ANSSI stepping in could have been prevented had the IT measures set out in the guide been applied.
This dashboard aligns with Section XI of the ANSSI 40 Essential Measures for a Healthy Network guide: Organise Response in the Event of an Incident. This section contains three rules:
- Rule 36 advises developing and regularly updating at least a basic plan for IT recovery, continuity of operations, and incident response. This plan should specify how the company's sensitive data is backed up.
- Rule 37 emphasizes implementing an alert chain in the event of an incident. All users must be able to contact the designated point of contact easily. Including an on-call or 24-hour component can help to ensure that incidents are dealt with quickly and effectively.
- Rule 38 recommends going beyond simply dealing with the infection of a machine, to establish how malware came to be installed on the machine, whether other machines are infected, and what data has been accessed. This information can improve incident response and aid in dealing with future incidents.
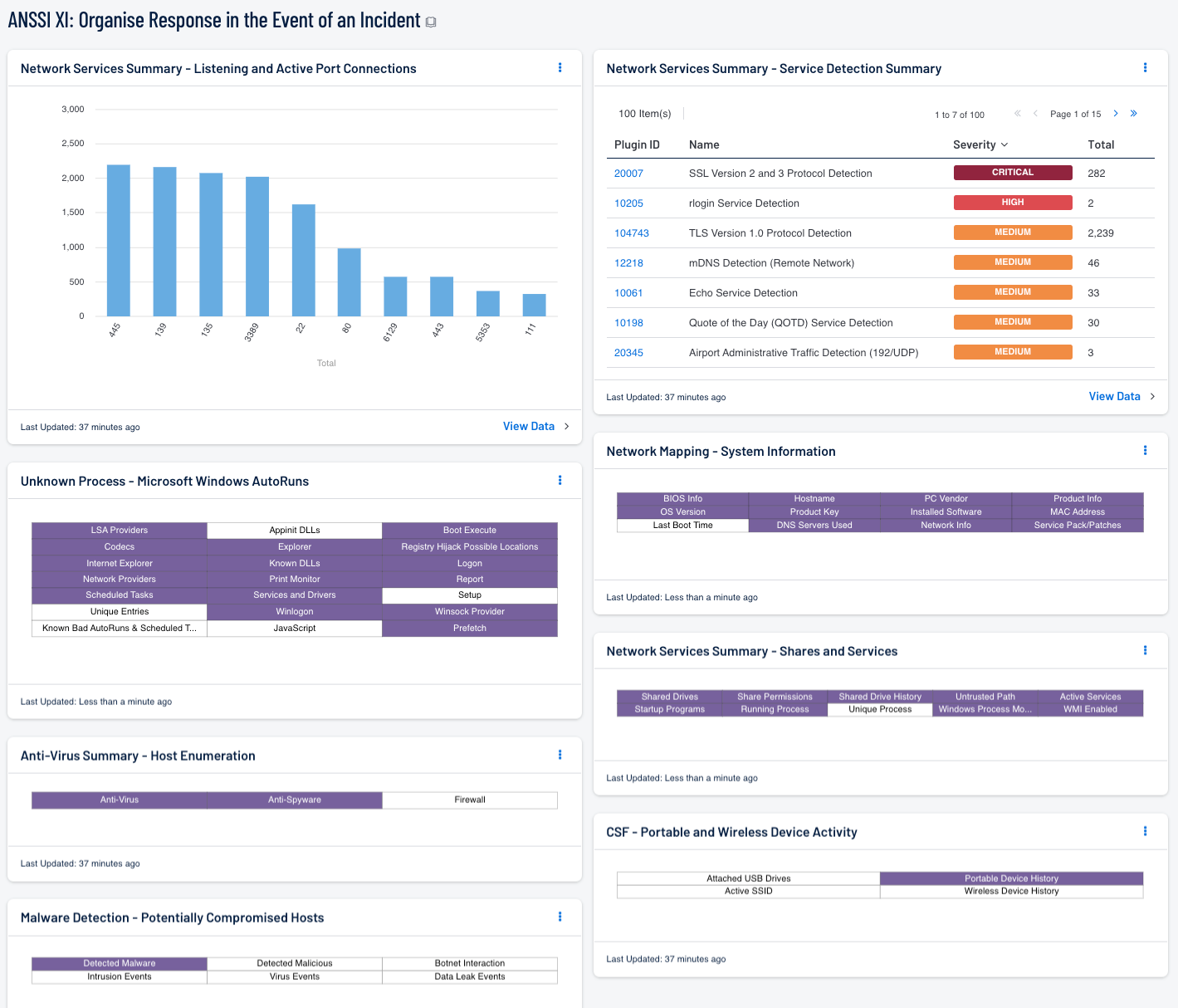
This dashboard will provide system information on listening and active ports connections, which can help to support incident response planning and post-exploitation activity. Security teams can use the data presented to monitor the network for wireless and portable devices that have been connected to the network. Service detection on internal hosts will provide valuable information on any unauthorized or insecure services in use that could be exploited by attackers. Indicators provide a comprehensive look at system information, configurations, shared drives, startup programs, and active processes on internal hosts. This information can be useful in determining an initial point of entry used by an attacker, malicious processes that may be running, what access an attacker could have access to, and other systems that may have been compromised.
Users most associated with virus events are also presented, providing insight into which users may be engaging in activity that exposes the network to viruses. Additional indicators are displayed that will alert analysts to potentially compromised hosts based on detected malware or suspicious behavior. A ticket activity summary is included that leverages Security Center integrated ticketing system, which can be used to track incident response activities. Indicators about AutoRun and startup services will alert security teams to processes, registry keys, startup programs, and scheduled tasks that could potentially execute malicious programs on hosts. Information about both local and domain users and groups will provide data on group membership changes, highlight issues with password security policies, and help to detect malicious activity associated with local user accounts. Attackers often target local user accounts with administrative access, as some organizations have security controls in place that focus more on domain security, rather than local security. Administrators may also have the same local credentials in place across many systems, so once one system is compromised, an attacker may have control over more systems on the network. This information can be useful for security teams to understand current weaknesses and how to fix them, detect compromised hosts, and track incident response activity. Organizations will be able to use the extensive information presented by components in this dashboard to strengthen security controls, reduce the attack surface, and improve overall incident response procedures.
This dashboard is available in the Security Center Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Security Center Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 5.4.0
- Nessus 8.5.1
- NNM 5.9.1
Tenable Security Center is the market-defining continuous network monitoring solution, and can assist in securing an organization’s internal network. Security Center is continuously updated with information about advanced threats, zero-day vulnerabilities, and new regulatory compliance data. Active scanning periodically examines systems to determine vulnerabilities and compliance concerns. Agent scanning enables scanning and detection of vulnerabilities on transient and isolated devices. Passive listening provides real-time discovery of vulnerabilities on operating systems, protocols, network services, wireless devices, web applications, and critical infrastructure. Host data and data from other security products is analyzed to monitor the network for malware, intrusions, and other forms of malicious activity. Security Center provides an organization with the most comprehensive view of the network and the intelligence needed to support proactive incident response efforts.
This dashboard contains the following components:
- Network Services Summary - Listening and Active Port Connections: The Listening and Active Port Connections component presents a chart of the top 10 ports detected on hosts that are listening or have active port connections
- Network Mapping - System Information: The System Information component presents indicators that will report on system details, network configurations, and installed software detected on network hosts
- CSF - Portable and Wireless Device Activity: The Portable and Wireless Device Activity component presents indicators that will report on Active SSID’s, attached USB Drives, and history of previously detected portable and wireless devices
- Network Services Summary - Service Detection Summary: The Service Detection Summary component presents a list of services detected on internal network hosts
- Network Services Summary - Shares and Services: The Shares and Services component presents indicators that highlight the types of services and shared storage in use on the network
- Ticket Overview – List of Tickets: The List of Tickets component presents a status summary of tickets issued within the Tenable.sc Ticketing and Alert System
- Anti-Virus Summary - Host Enumeration: The Host Enumeration component uses the plugin IDs 16193 (Anti-Virus Enumeration), 45050 (Anti-Malware Enumeration), and 45052 (Firewall Enumeration) to report on the status of anti-virus, anti-malware, and desktop firewalls
- Malware Detection - Potentially Compromised Hosts: This component presents indicators that highlight potentially compromised hosts
- Unknown Process – Microsoft Windows AutoRuns: This component presents 21 indicators that will alert on a variety of Windows AutoRun issues detected on the network
- CSF – Account and Group Information: This table displays detections of account and group information, such as accounts that have never been logged into, disabled accounts, and group user lists