by Cody Dumont
October 17, 2016
Perimeter defenses can no longer be solely relied upon to protect an organization's network. There are many ways that perimeter defenses can be circumvented and internal network access obtained by attackers. If there are no internal network defenses, an attacker who merely breaches the perimeter will have unrestricted access to critical systems and information. The internal network itself must have defensive measures in place to protect against attackers who have already breached the perimeter.
The French Network and Information Security Agency (Agence nationale de sécurité des systèmes d’information or ANSSI) developed the "40 Essential Measures for a Healthy Network" to assist organizations in safeguarding the security of information systems within a network. Following these measures, or rules, for a healthy network will provide basic protection for an organization's critical data. ANSSI states that the majority of IT attacks that have involved ANSSI stepping in could have been prevented had the IT measures set out in the guide been applied.
This dashboard aligns with Section VI of the ANSSI 40 Essential Measures for a Healthy Network guide: Secure the Inside of the Network. This section contains four rules:
- Rule 20 focuses on monitoring user access rights within Active Directory or LDAP environments. This rule recommends reviewing the rules set out within the article entitled “Auditing permissions in an Active Directory environment”, which provides a list of safety recommendations for Active Directory.
- Rule 21 emphasizes the need to compartmentalize networks, in order to isolate and protect critical systems on the network. Critical systems should be placed within a sub-network that is protected by an interconnection gateway. This provides an additional layer of protection so that an intruder on a non-critical machine will not have immediate, unrestricted access to those critical systems.
- Rule 22 advises against using wireless infrastructures. However, if the use of wireless technology cannot be avoided, organizations should separate the wireless access network from the rest of the network. In addition, organizations must be able to control access, restrict traffic, and implement secure encryption solutions.
- Rule 23 recommends using secure applications and protocols throughout the network. Insecure protocols contain vulnerabilities that can be easily exploited by attackers; these protocols should be replaced by their secure equivalents. Organizations should take into account security risks when developing applications and make sure any underlying technologies can be updated as required without breaking the applications.
This dashboard enables organizations to effectively monitor and defend the internal network. Organizations will be able to obtain the latest information on product and protocol vulnerabilities, user access control and least privilege issues, and wireless network concerns. This information will assist the organization in protecting assets and safeguarding critical data across the enterprise.
Compliance checks include detailed information related to Active Directory, LDAP services, and user access controls, which can assist in identifying security policies and privileges that need to be modified. Information about new and existing wireless devices can alert analysts for any suspicious wireless activity or rogue wireless devices that can provide attackers with the ability to pivot deeper inside the network. Vulnerabilities detected from web browsers, protocols, and web applications can help to assist in identifying unauthorized and insecure applications currently in use. Leaving these vulnerabilities unpatched may allow for attackers to intercept credentials, obtain confidential information, and gain control over critical systems. In addition, detections of unsupported products, such as unsupported operating systems and applications, can alert analysts to products that need to be upgraded or that may contain zero-day vulnerabilities. Vulnerabilities are also presented by subnet, which can highlight both the internal structure of the network and those sections of the network that are the most vulnerable.
This dashboard is available in the Security Center Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Security Center Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Security Center 5.3.2
- Nessus 6.7.0
- PVS 5.1.0
Tenable Security Center is the market-defining continuous network monitoring solution, and can assist in securing an organization’s internal network. Security Center is continuously updated with information about advanced threats, zero-day vulnerabilities, and new regulatory compliance data. Active scanning periodically examines systems and portable devices to determine vulnerabilities and compliance concerns. Agent scanning enables scanning and detection of vulnerabilities on transient and isolated devices. Passive listening provides real-time discovery of vulnerabilities on operating systems, protocols, network services, wireless devices, web applications, and critical infrastructure. Host data and data from other security products is analyzed to monitor internal network activity. Security Center provides an organization with the most comprehensive view of the network and the intelligence needed to secure the internal network and safeguard critical assets and information.
The following components are included in this dashboard:
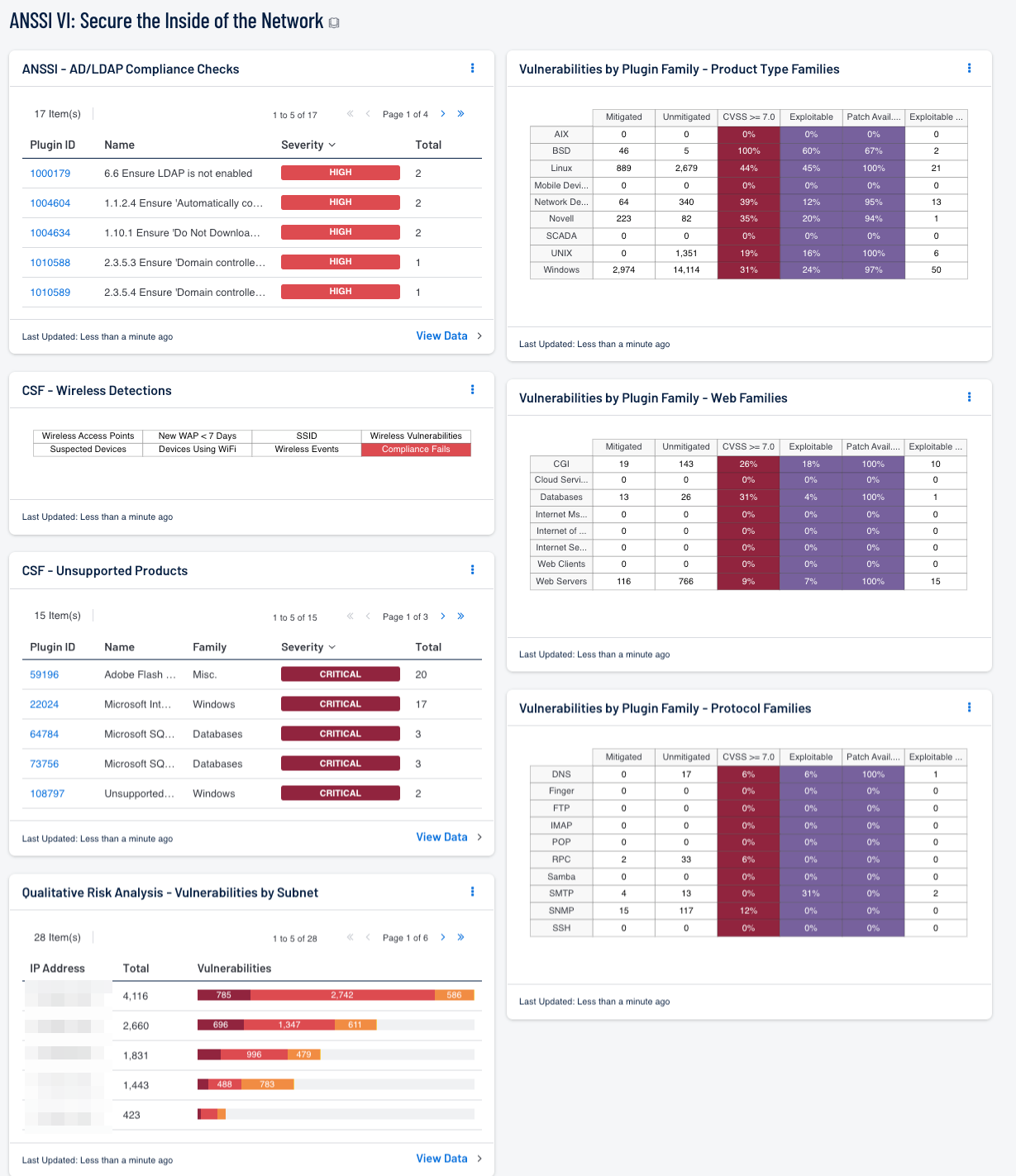
- ANSSI - AD/LDAP Compliance Checks: This table presents a list of Active Directory and LDAP compliance related issues.
- CSF - Wireless Detections: This component presents a breakdown of detected wireless access points, wireless vulnerabilities, and wireless event activity on the network.
- CSF - Unsupported Products: This table displays all unsupported products by name, sorted by severity. This component identifies unsupported products by filtering on the text "unsupported" in the vulnerability plugin name.
- CSF - User Access and Least Privilege Compliance Checks: This component displays user access and least privilege compliance information in areas such as password requirements, lockout policy after failed logins, and controlled use of administrative privileges.
- Vulnerabilities by Plugin Family - Product Type Families: This component presents vulnerabilities discovered in product type plugin family groupings, and can assist an organization in identifying vulnerabilities, prioritizing remediations, and tracking remediation progress.
- Vulnerabilities by Plugin Family - Web Families: This component presents vulnerabilities discovered in web-related plugin family groupings, and can assist an organization in identifying vulnerabilities, prioritizing remediations, and tracking remediation progress.
- Vulnerabilities by Plugin Family - Protocol Families: This component presents vulnerabilities discovered in protocol plugin family groupings, and can assist an organization in identifying vulnerabilities, prioritizing remediations, and tracking remediation progress.