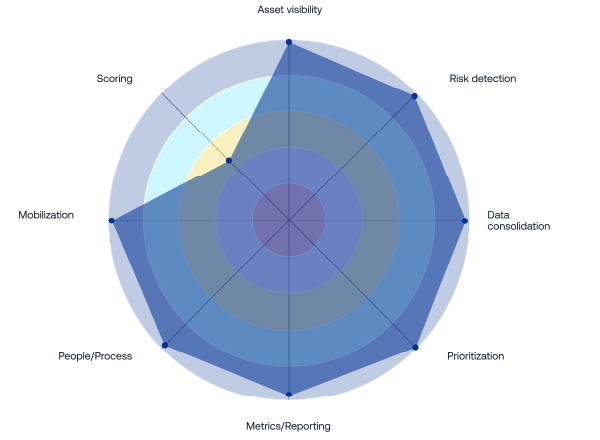
How to chart a path to exposure management maturity
Ready to make exposure management a priority? This quick-start guide will help you pinpoint your current state of exposure management maturity and provide you with powerful people, process and technology changes to help you reach your desired state.

How to Chart a Path to Exposure Management Maturity
14 powerful people, process and technology changes to drive measurable cybersecurity and risk management results